Questions:
How does an #Aadhaar card work?
Is it really possible to Hack #Aadhar System?
How vulnerable is the Aadhaar database to unauthorized access?
Can the system successfully trace unauthorized access?
Does it properly maintain logs? Thread 1/n #AadhaarLeaks #aadharleaks
How does an #Aadhaar card work?
Is it really possible to Hack #Aadhar System?
How vulnerable is the Aadhaar database to unauthorized access?
Can the system successfully trace unauthorized access?
Does it properly maintain logs? Thread 1/n #AadhaarLeaks #aadharleaks
Key Features of #Aadhaar:
• A random number- for lifetime
• All residents
•1 person =1 Aadhaar
• Minimal data collected
• Secured&Privacy of data ensured
• Ubiquitous online authentication
• Enroll&Update from anywhere
• Doesn’t confer citizenship,rights,entitlements 2/n
• A random number- for lifetime
• All residents
•1 person =1 Aadhaar
• Minimal data collected
• Secured&Privacy of data ensured
• Ubiquitous online authentication
• Enroll&Update from anywhere
• Doesn’t confer citizenship,rights,entitlements 2/n
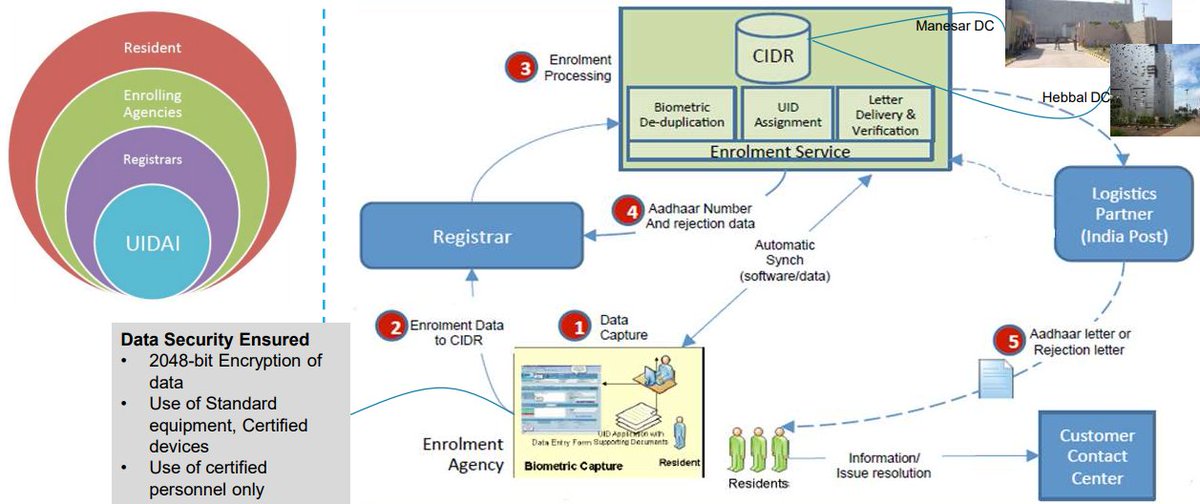
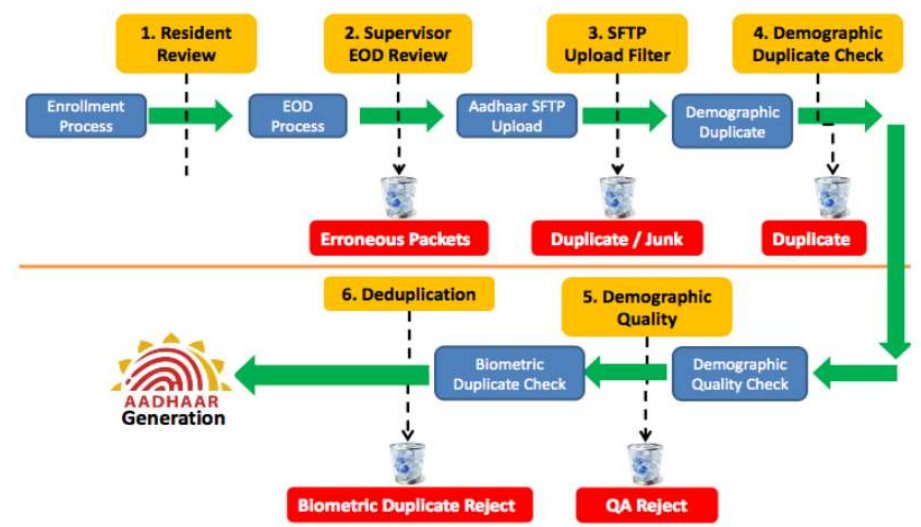
#Aadhaar Enrolment Agencies are entities hired by UIDAI-appointed Registrars, for enrolment of residents during which demographic and biometric data is collected as per the UIDAI enrolment process Enrolment require handling of large binary data for all residents, min 8MB 3/n
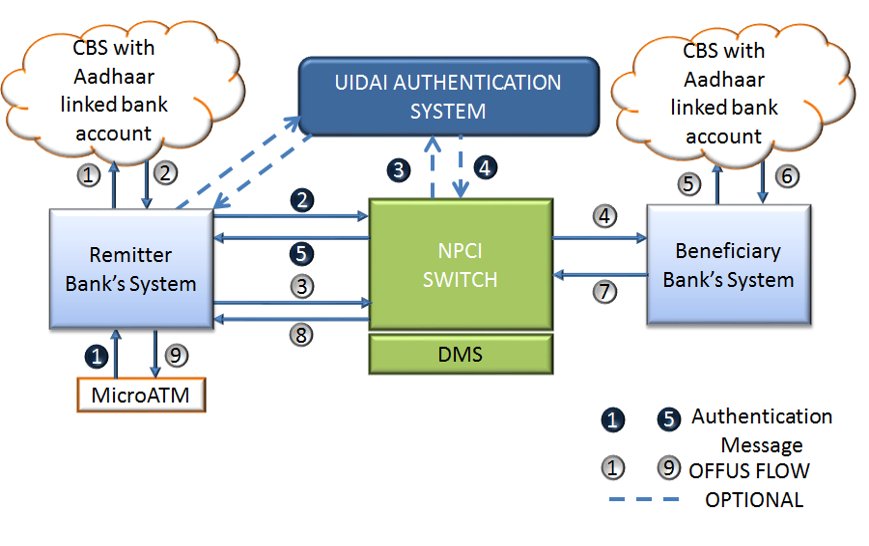
#Aadhaar Payment Bridge
1.Govt. Department prepares an electronic file containing Aadhaar no and amt
2.Govt. Department sends the file to the bank where scheme account is maintained
http://3.Bank"> http://3.Bank sends to Aadhaar Payments Bridge (APB) (owned and operated by NPCI) 4/n
1.Govt. Department prepares an electronic file containing Aadhaar no and amt
2.Govt. Department sends the file to the bank where scheme account is maintained
http://3.Bank"> http://3.Bank sends to Aadhaar Payments Bridge (APB) (owned and operated by NPCI) 4/n
....4.APB routes money to the concerned banks. Banks credit the money in beneficiaries’ accounts
5.Department can send SMS informing the beneficiary about the money being sent. Banks can also send when the money arrives in the accounts
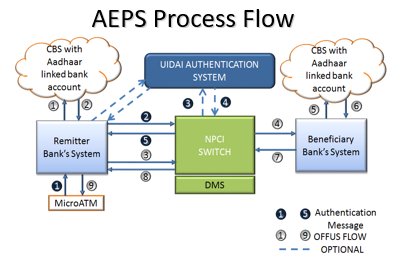
Aadhaar enabled Payment system Process https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">
5.Department can send SMS informing the beneficiary about the money being sent. Banks can also send when the money arrives in the accounts
Aadhaar enabled Payment system Process
Advantages of Aadhaar Payment Bridge System (APBS) to Departments
#Aadhaar linkage in the Government and Bank databases provides end-to-end visibility of subsidy and benefits payments from Government to the beneficiaries 6/n
#Aadhaar linkage in the Government and Bank databases provides end-to-end visibility of subsidy and benefits payments from Government to the beneficiaries 6/n
The entire technology architecture behind Aadhaar is based on principles of openness, linear scalability, strong security, and most importantly vendor neutrality. 7/n
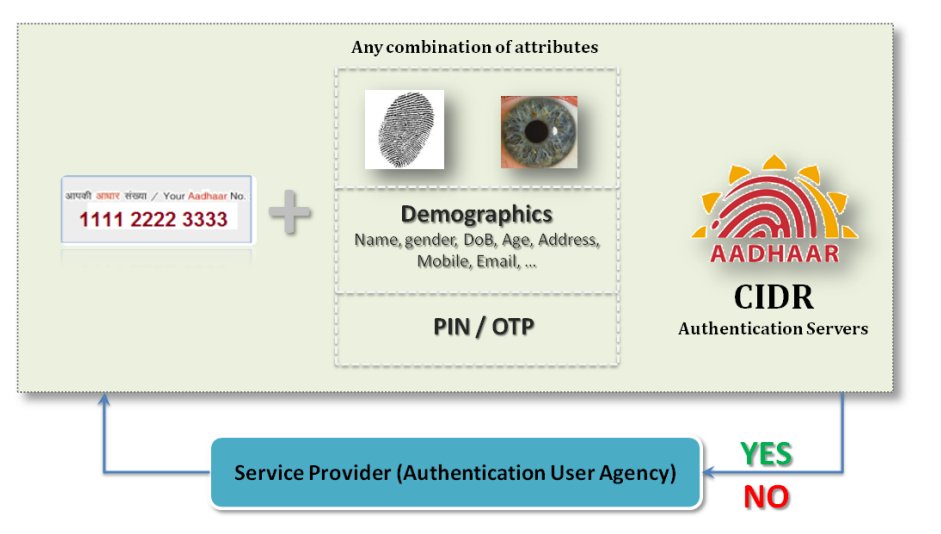
Authentication is matching eligible information provided by an #Aadhaar number holder with the information stored in the Central Identities Data Repository (CIDR). Include the Aadhaar number along with demographic attributes, biometrics, or mobile number 8/n
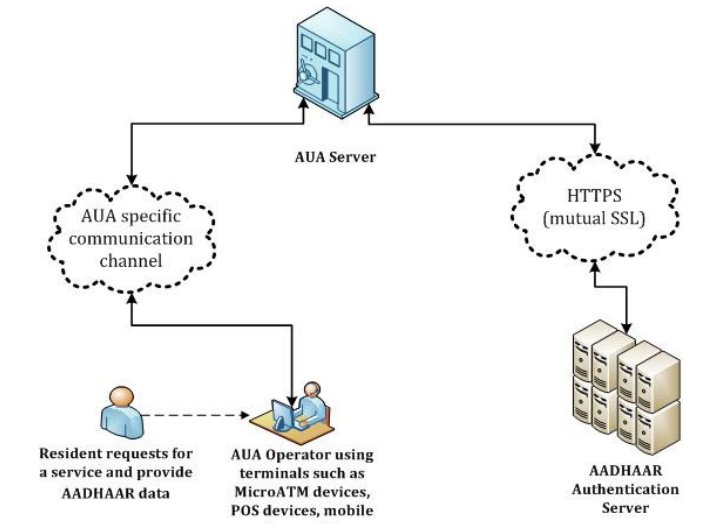
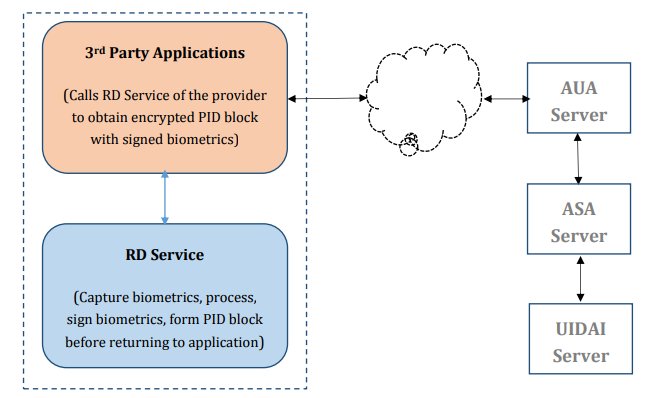
Process: ASAs establish connectivity to the CIDR and transmit authentication requests from AUAs to the CIDR.
AUAs use #Aadhaar authentication to enable their services.To gain access to the Aadhaar authentication facility, AUAs must enter into a formal agreement with the UIDAI 9/n
AUAs use #Aadhaar authentication to enable their services.To gain access to the Aadhaar authentication facility, AUAs must enter into a formal agreement with the UIDAI 9/n
Data Security – The security and privacy of one’s data is a foundation of the #Aadhaar system. The system uses 2048-bit PKI encryption and tamper detection using HMAC in order to ensure that no one can decrypt and misuse the data. 10/n
Resident data and raw biometrics are always kept encrypted, even within UIDAI data centers. In addition, the system does not keep track of any transactional data.11/n
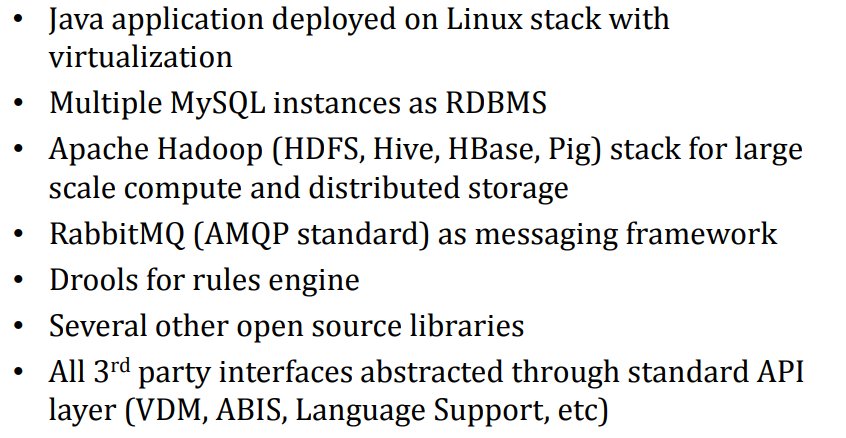
#Aadhaar Technology Stack 12/n
Using Fully distributed compute platform and Data shared across multiple RDBMS instances and DFS
Using Fully distributed compute platform and Data shared across multiple RDBMS instances and DFS
Aadhaar system uses 2048-bit PKI encryption and tamper detection using HMAC in order to ensure that no one can decrypt and misuse the data.Public-key cryptography uses encryption algorithms like RSA and Elliptic Curve Cryptography (ECC) to create the public and pvt keys. 13/n
Public Key Infrastructure (PKI) is the set of hardware, software, people, policies, and procedures that are needed to create, manage, distribute, use, store, and revoke digital certificates. #Aadhaar 14/n
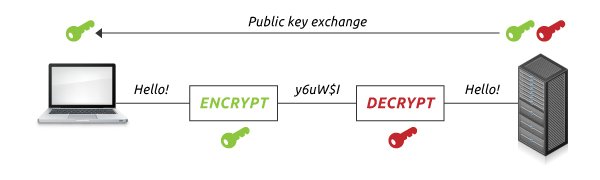
SSL Uses both Asymmetric and Symmetric
SSL communications,the server’s SSL Certificate contains an asymmetric public and private key pair.The session key that the server & the browser create during the SSL Handshake is symmetric
15/n
SSL communications,the server’s SSL Certificate contains an asymmetric public and private key pair.The session key that the server & the browser create during the SSL Handshake is symmetric
15/n
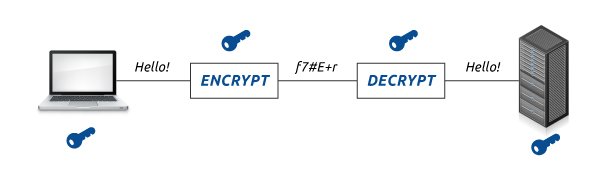
1Server sends a copy of its asymmetric public key
2Browser creates a symmetric session key&encrypts it with the server& #39;s asymmetric public key.den sends it to the server
3Server decrypts the encrypted session key using its asymmetric private key to get the symmetric sess key.16/n
2Browser creates a symmetric session key&encrypts it with the server& #39;s asymmetric public key.den sends it to the server
3Server decrypts the encrypted session key using its asymmetric private key to get the symmetric sess key.16/n
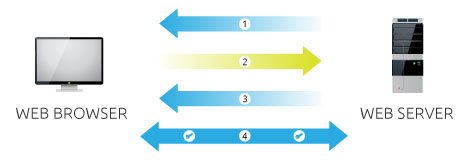
Finally Server and Browser now encrypt and decrypt all transmitted data with the symmetric session key. This allows for a secure channel because only the browser and the server know the symmetric session key, and "the session key is only used for that session"(Imp) 17/n #Aadhaar
In the security world, there is nothing called fully secure and absolute security. Aadhaar use 2048-bit keys in secure SSL certificates. RSA Labs claims that 2048-bit keys are 2^32 times harder to break using NFS, than 1024. almost 4.3 billion #Aadhaar 18/n
..therefore breaking a 2048-bit SSL certificate would take about 4.3 billion times longer than doing it for a 1024-bit key. It is therefore estimated, that standard desktop computing power would take 6.4 quadrillion years to break a 2048-bit SSL certificate. so it& #39;s possible.19/n
Aadhaar authentication data shall be maintained for a period of months and thereafter archived for a period of 5years by the UIDAI.Authentication logs will be maintained by the requesting entity for a period of 2years and archived for a period of 5years. 20/n #AadhaarLeaks
Aadhaar ID is not leaked from the system through unauthorized access.This data is derived from authorized personnel.Remove such criminals from the system and governments please be vigilant, be respectful to the privacy of people. 22/n #AadhaarLeaks https://twitter.com/Rukmini/status/949482118261829632">https://twitter.com/Rukmini/s...
Aadhaar is getting a lot of global attention. World Bank appreciating the Aadhaar architecture and other countries shown keen interest in it. 23/n #AadhaarLeaks
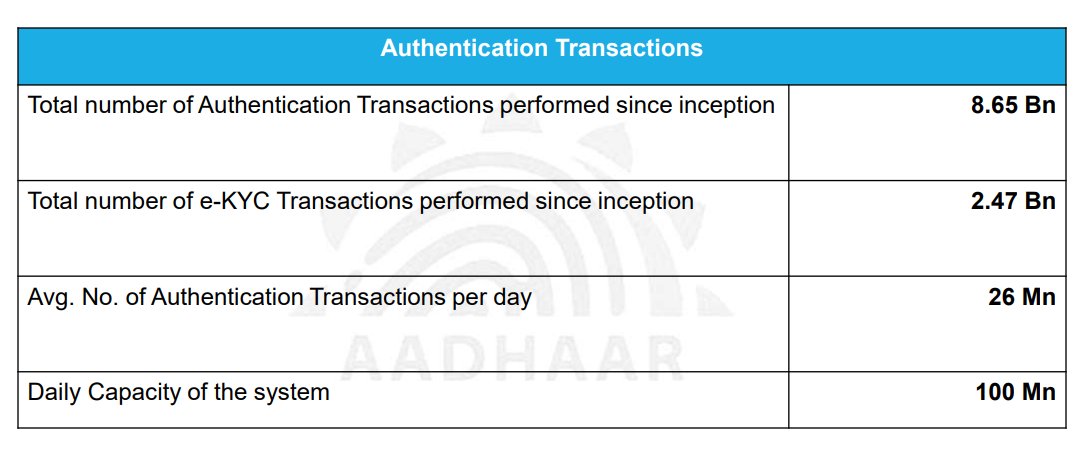
Till now, UIDAI has done more than 500 crores of authentications, more than 100 crores of Aadhaar based e-KYC for various purposes, for opening bank accounts, for getting a SIM card and all these things. #AadharLeaks 24/n
Not a single case of data leak from the UIDAI, data breach from UIDAI was not registered. not a single case of identity theft or financial loss has been reported to @UIDAI . people should make a judgment whether Aadhaar is safe or not. #AadhaarLeaks 25/n
Finally, World Bank estimated that if the government is using Aadhaar in various schemes, will save $11billion annually #AadharLeaks 26/n

 Read on Twitter
Read on Twitter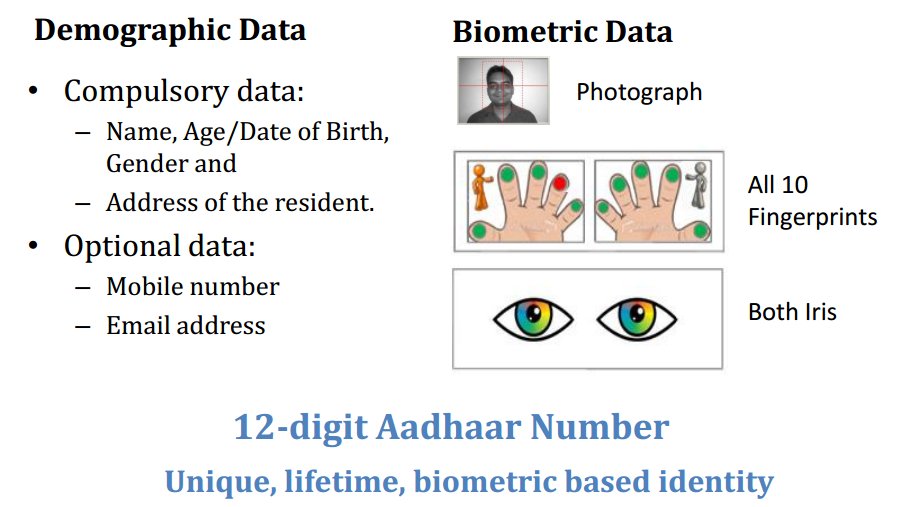
 " title="....4.APB routes money to the concerned banks. Banks credit the money in beneficiaries’ accounts5.Department can send SMS informing the beneficiary about the money being sent. Banks can also send when the money arrives in the accountsAadhaar enabled Payment system Process https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">" class="img-responsive" style="max-width:100%;"/>
" title="....4.APB routes money to the concerned banks. Banks credit the money in beneficiaries’ accounts5.Department can send SMS informing the beneficiary about the money being sent. Banks can also send when the money arrives in the accountsAadhaar enabled Payment system Process https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">" class="img-responsive" style="max-width:100%;"/>