Want to onboard you domain controllers to Microsoft Defender for Identity?
#MDI #MDE #AD #Security https://abs.twimg.com/emoji/v2/... draggable="false" alt="🛡️" title="Schild" aria-label="Emoji: Schild">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🛡️" title="Schild" aria-label="Emoji: Schild">
Out of scope: ADFS, actions accounts and remote SAM.
A thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">
#MDI #MDE #AD #Security
Out of scope: ADFS, actions accounts and remote SAM.
A thread
First create a new group policy or edit your current security baseline GPO.
Enable the following advanced auditing config settings to success and failure.
Enable NTLM auditing for incoming and outgoing traffic.
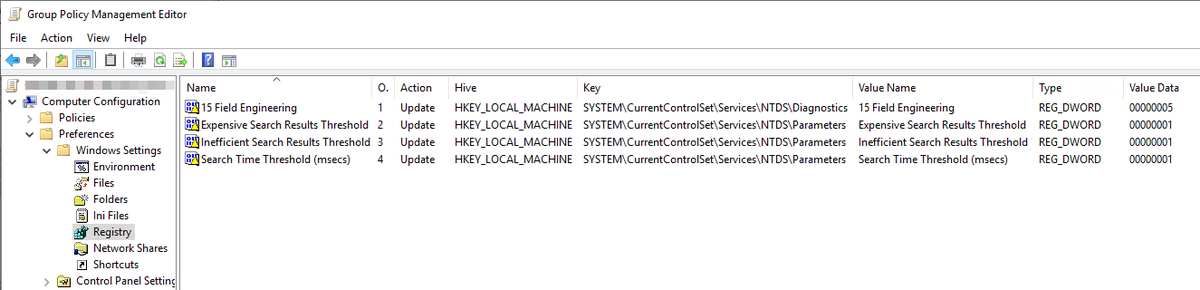
Add registry keys for event ID 1644 using GPP.
Enable the following advanced auditing config settings to success and failure.
Enable NTLM auditing for incoming and outgoing traffic.
Add registry keys for event ID 1644 using GPP.
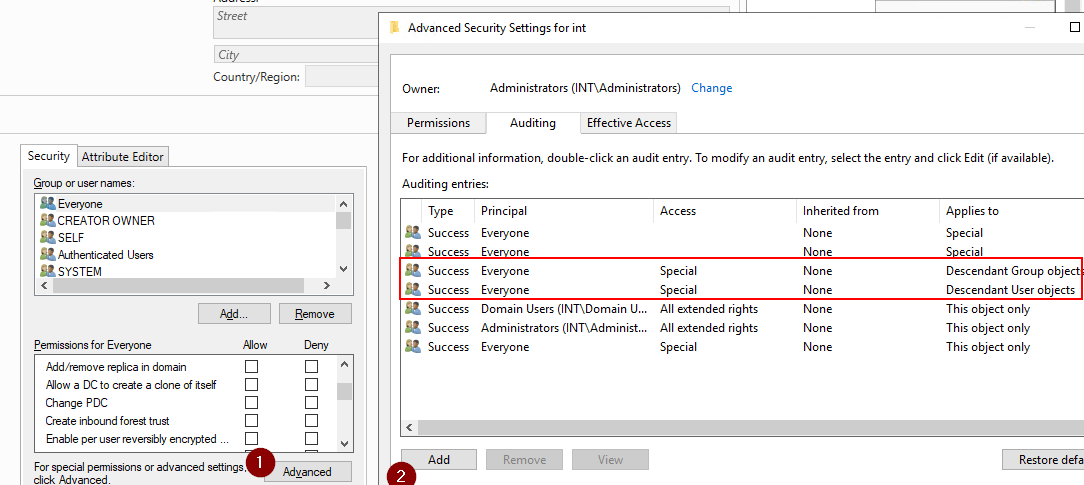
In Active Directory Administrative Center and open the Advanced security dialog for the domain root. Select "Auditing" and "Add"
Principal: Everyone
Type: Success
Applies to: Descendant User/Group objects
Scroll to the bottom and click "Clear all". Change as shown in screenshot
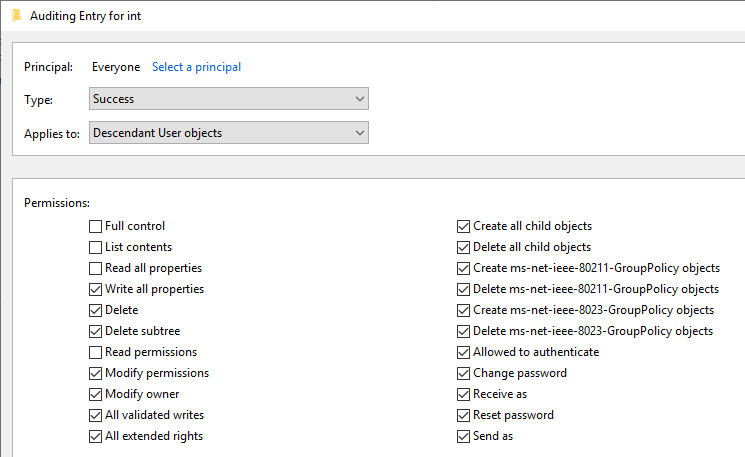
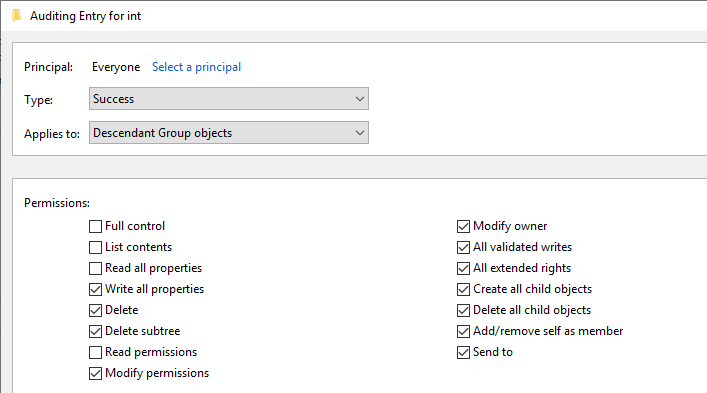
Principal: Everyone
Type: Success
Applies to: Descendant User/Group objects
Scroll to the bottom and click "Clear all". Change as shown in screenshot
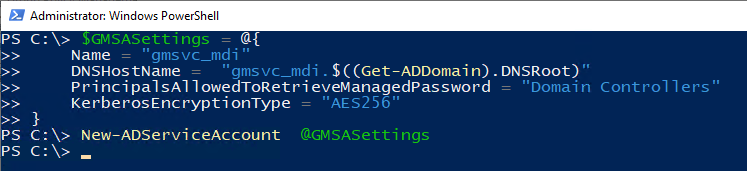
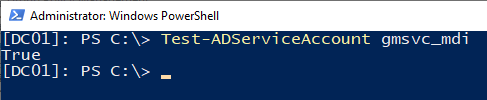
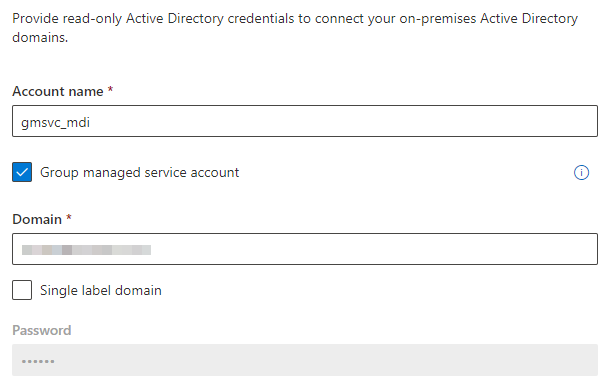
Create a new gMSA account with Kerberos encryption type AES256 and allow the domain controllers to retrieve the password.
Test if the account can be accessed.
Test if the account can be accessed.
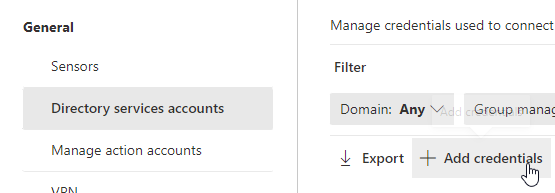
Switch to Defender portal, Settings,
Identities, Directory services accounts.
Add the newly created credentials
https://security.microsoft.com/settings/identities?tabid=directory">https://security.microsoft.com/settings/...
Identities, Directory services accounts.
Add the newly created credentials
https://security.microsoft.com/settings/identities?tabid=directory">https://security.microsoft.com/settings/...
Allow network communication from your domain controllers to the AATP service IPs. See script for current list of IPs.
If you are going to use a proxy server allow connections to and disable TLS inspection
* http://sensorapi.atp.azure.com"> http://sensorapi.atp.azure.com
*.atp.azure.com https://gist.github.com/f-bader/e9a48e1f24df32055d4775b58cb33cdc">https://gist.github.com/f-bader/e...
If you are going to use a proxy server allow connections to and disable TLS inspection
* http://sensorapi.atp.azure.com"> http://sensorapi.atp.azure.com
*.atp.azure.com https://gist.github.com/f-bader/e9a48e1f24df32055d4775b58cb33cdc">https://gist.github.com/f-bader/e...
Also allow you domain controllers to reach out to your servers and clients using the following ports for name resolution:
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">TCP/135 - NTLM over RPC
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">TCP/135 - NTLM over RPC
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">UDP/137 - NetBIOS
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">UDP/137 - NetBIOS
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">TCP/3389 - RDP
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🟢" title="Groene cirkel" aria-label="Emoji: Groene cirkel">TCP/3389 - RDP
As a last resort MDI will use reverse DNS (UDP/53) https://docs.microsoft.com/en-us/defender-for-identity/nnr-policy">https://docs.microsoft.com/en-us/def...
As a last resort MDI will use reverse DNS (UDP/53) https://docs.microsoft.com/en-us/defender-for-identity/nnr-policy">https://docs.microsoft.com/en-us/def...
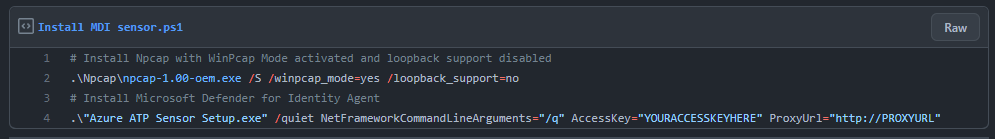
Copy and expand installer package to your DCs
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabled
https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabled
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access key
https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access key
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.
Check onboarding status in the MDE portal
https://gist.github.com/f-bader/d0029bdd0c9c55d9f648eb16baf6341a">https://gist.github.com/f-bader/d...
Check onboarding status in the MDE portal
https://gist.github.com/f-bader/d0029bdd0c9c55d9f648eb16baf6341a">https://gist.github.com/f-bader/d...
If you have Exchange in your environment, you have to add additional auditing on your Configuration container. #enable-auditing-on-an-exchange-object">https://docs.microsoft.com/en-us/defender-for-identity/configure-windows-event-collection #enable-auditing-on-an-exchange-object">https://docs.microsoft.com/en-us/def...
Optional: Regenerate access key through the MDE portal. This will not impact already onboarded DCs but makes sure that the used access key cannot be used anymore.
// End of thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">
// End of thread
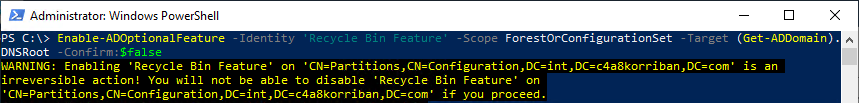
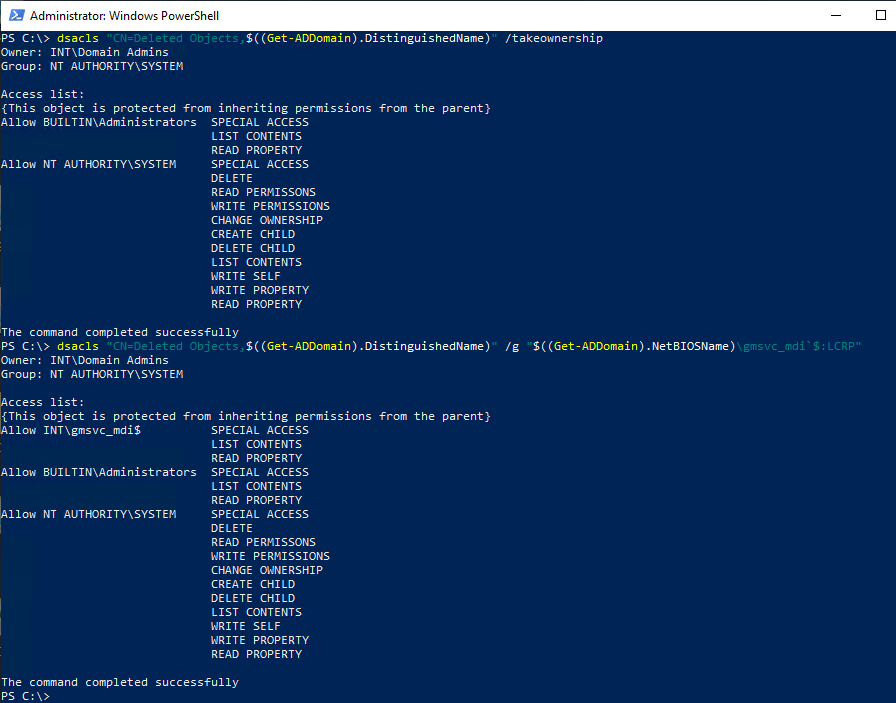
As @dougsbaker mentioned corretly please also enable the Recyle Bin Feautre in you forest and also grant the MDI service account read and list permissions on the Deleted Objects container.
https://gist.github.com/f-bader/06fafab0969f44066d4d0d727a8c2552">https://gist.github.com/f-bader/0...
https://gist.github.com/f-bader/06fafab0969f44066d4d0d727a8c2552">https://gist.github.com/f-bader/0...

 Read on Twitter
Read on Twitter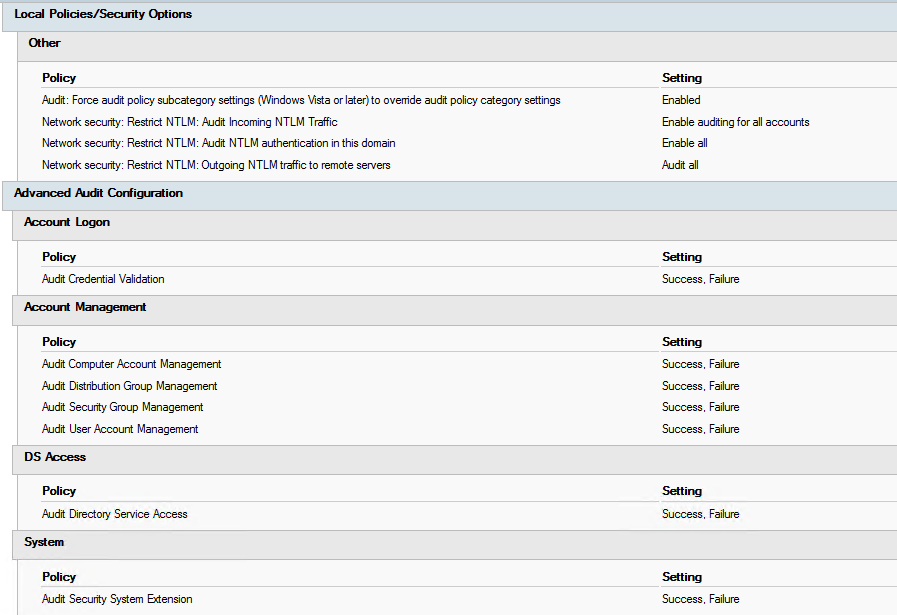

 Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d..." title="Copy and expand installer package to your DCs https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d...">
Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d..." title="Copy and expand installer package to your DCs https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d...">
 Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d..." title="Copy and expand installer package to your DCs https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d...">
Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d..." title="Copy and expand installer package to your DCs https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Nummertoets een" aria-label="Emoji: Nummertoets een"> Install Npcap with WinPCAP mode enabled and loopback disabledhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Nummertoets twee" aria-label="Emoji: Nummertoets twee"> Install the MDI sensor using you access keyhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔁" title="Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan" aria-label="Emoji: Open cirkelende pijlen die met de klok mee naar rechts en naar links gaan">Repeat on all domain controllers in your forest.Check onboarding status in the MDE portal https://gist.github.com/f-bader/d...">
 " title="Optional: Regenerate access key through the MDE portal. This will not impact already onboarded DCs but makes sure that the used access key cannot be used anymore.// End of thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">" class="img-responsive" style="max-width:100%;"/>
" title="Optional: Regenerate access key through the MDE portal. This will not impact already onboarded DCs but makes sure that the used access key cannot be used anymore.// End of thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="collectie" aria-label="Emoji: collectie">" class="img-responsive" style="max-width:100%;"/>