New documents for the Okta breach: I have obtained copies of the Mandiant report detailing the embarrassing Sitel/SYKES breach timeline and the methodology of the LAPSUS$ group. 1/N https://twitter.com/BillDemirkapi/status/1506107157124722690">https://twitter.com/BillDemir...
We can see how LAPSUS$ originally began investigating their compromised host on January 19th, 2022. With little regard for OPSEC, LAPSUS$ searched for a CVE-2021-34484 bypass on their compromised host and downloaded the pre-built version from GitHub. 2/N https://twitter.com/KLINIX5/status/1451558296872173577">https://twitter.com/KLINIX5/s...
LAPSUS$ used off-the-shelf tooling from GitHub for the majority of their attacks. After downloading Process Explorer and Process Hacker, LAPSUS$ bypassed the FireEye endpoint agent by simply terminating it! 3/N
With the endpoint agent disabled, LAPSUS$ simply downloaded the official version of Mimikatz (a popular credential dumping utility) directly from its repository. 4/N
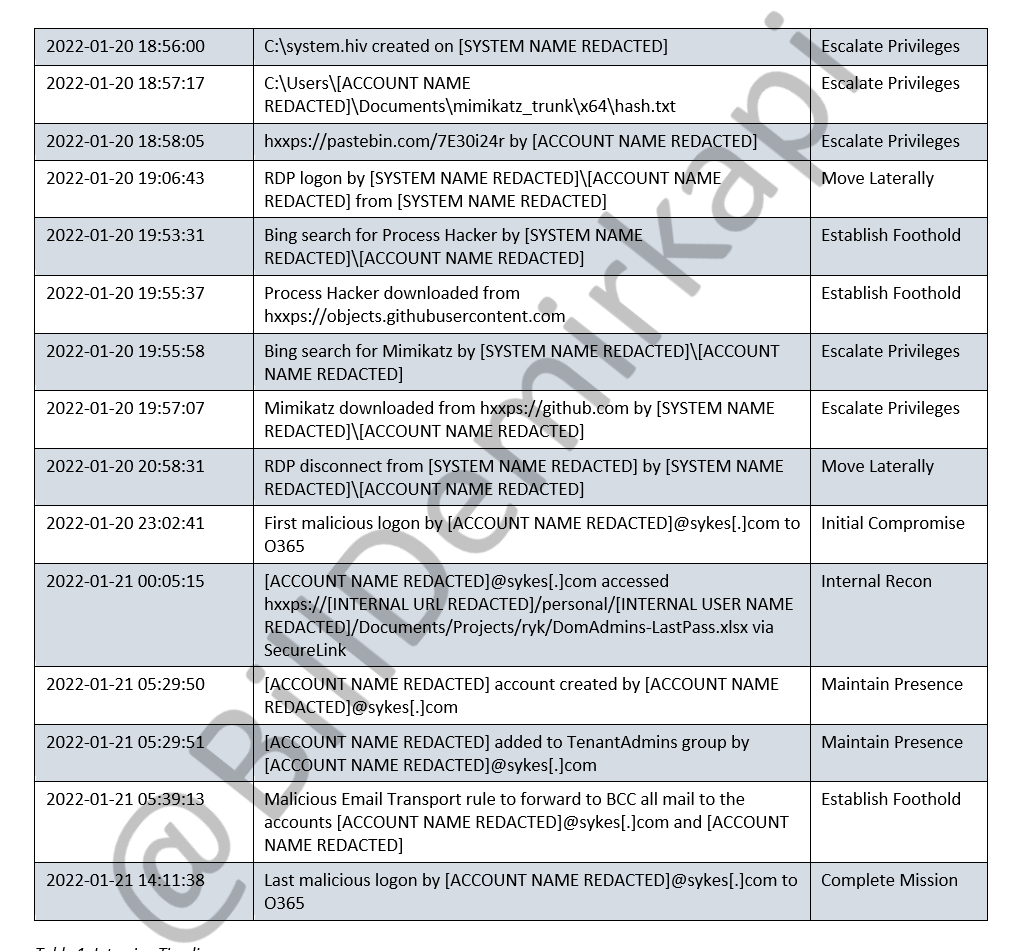
LAPSUS$ was able to create backdoor users in Sitel& #39;s environment after retrieving an Excel document conspicuously titled "DomAdmins-LastPass.xlsx"  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦♂️" title="Facepalmende man" aria-label="Emoji: Facepalmende man">. 5/N
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦♂️" title="Facepalmende man" aria-label="Emoji: Facepalmende man">. 5/N
LAPSUS$ finished off their attack by creating a malicious "email transport rule" to forward all mail within Sitel& #39;s environment to their own accounts. 6/N https://docs.microsoft.com/en-us/exchange/security-and-compliance/mail-flow-rules/mail-flow-rules">https://docs.microsoft.com/en-us/exc...
My questions for Okta: You knew that the machine of one of your customer support members was compromised back in January. Why didn& #39;t you investigate it? Having the capability to detect an attack is useless if you aren& #39;t willing to respond. 7/N
Even when Okta received the Mandiant report in March explicitly detailing the attack, they continued to ignore the obvious signs that their environment was breached until LAPSUS$ shined a spotlight on their inaction. 8/N
For the Sitel Group: Why weren& #39;t your customers immediately informed upon the first sign of compromise? Why did your customers have to wait two months to even hear that you were breached? 9/N
Sitel Group serves many more customers than Okta. Often times, for support staff to perform their jobs, they need Administrative privileges into their customer& #39;s environment. The attack highlights the increased risk of outsourcing access to your org.& #39;s internal environment. 10/N
Good questions to ask include: Who knows how your sub-processors handle their own security? As we saw in this case, Sitel didn& #39;t take the security of their environment very seriously. What can an attacker do if one of your sub-processors becomes compromised? 11/N
Well this didn& #39;t go to plan. 12/N https://twitter.com/BillDemirkapi/status/1508610588200607746">https://twitter.com/BillDemir...

 Read on Twitter
Read on Twitter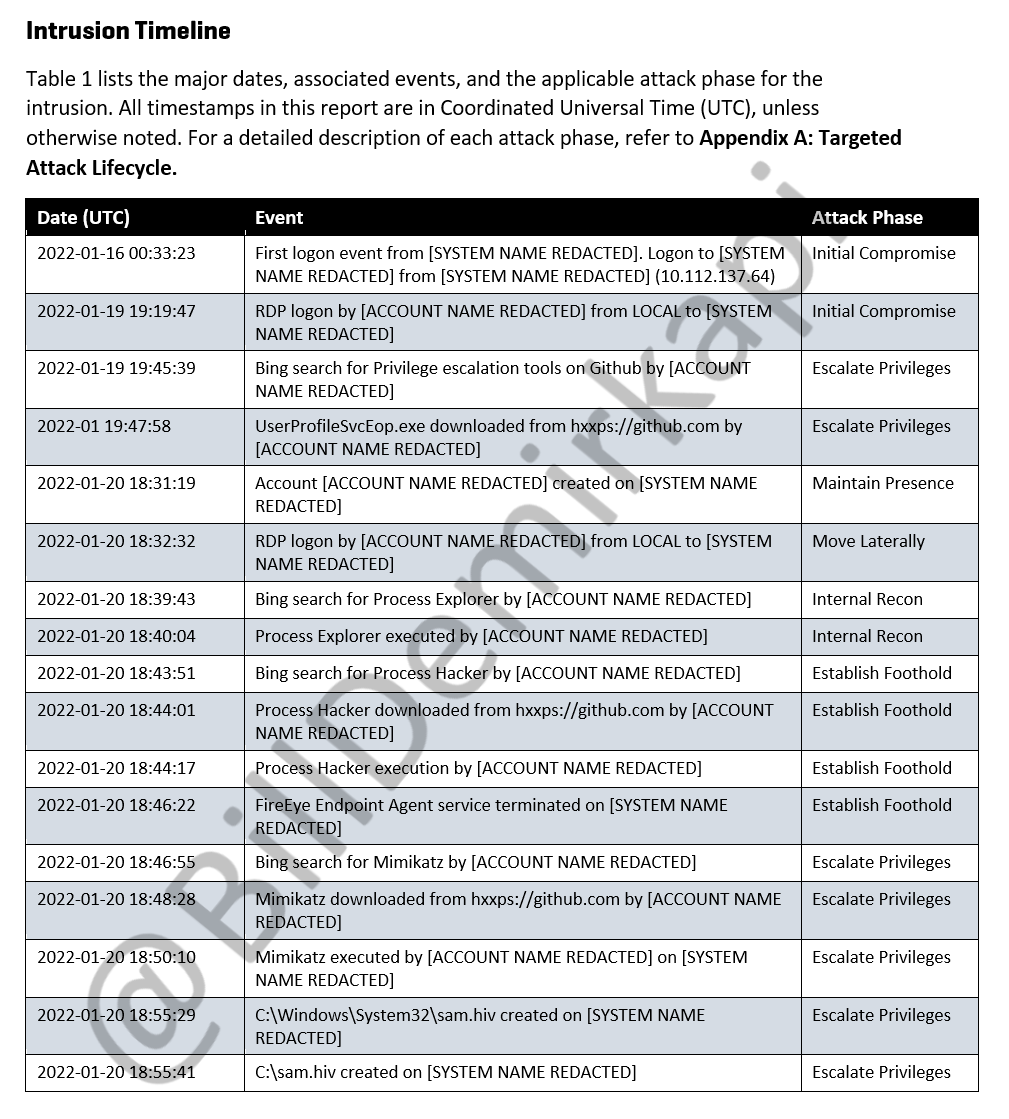




 . 5/N" title="LAPSUS$ was able to create backdoor users in Sitel& #39;s environment after retrieving an Excel document conspicuously titled "DomAdmins-LastPass.xlsx" https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦♂️" title="Facepalmende man" aria-label="Emoji: Facepalmende man">. 5/N" class="img-responsive" style="max-width:100%;"/>
. 5/N" title="LAPSUS$ was able to create backdoor users in Sitel& #39;s environment after retrieving an Excel document conspicuously titled "DomAdmins-LastPass.xlsx" https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦♂️" title="Facepalmende man" aria-label="Emoji: Facepalmende man">. 5/N" class="img-responsive" style="max-width:100%;"/>



