1/8
Another weekend with a DeFi exploit on BSC, and this time the AMM called vSwap from @value_defi is in trouble.
About $11M was stolen today from non 50/50 pools, in addition to $6M already lost this week as a result of contract reinitialization.
Let’s see what happened https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
Another weekend with a DeFi exploit on BSC, and this time the AMM called vSwap from @value_defi is in trouble.
About $11M was stolen today from non 50/50 pools, in addition to $6M already lost this week as a result of contract reinitialization.
Let’s see what happened
2/8
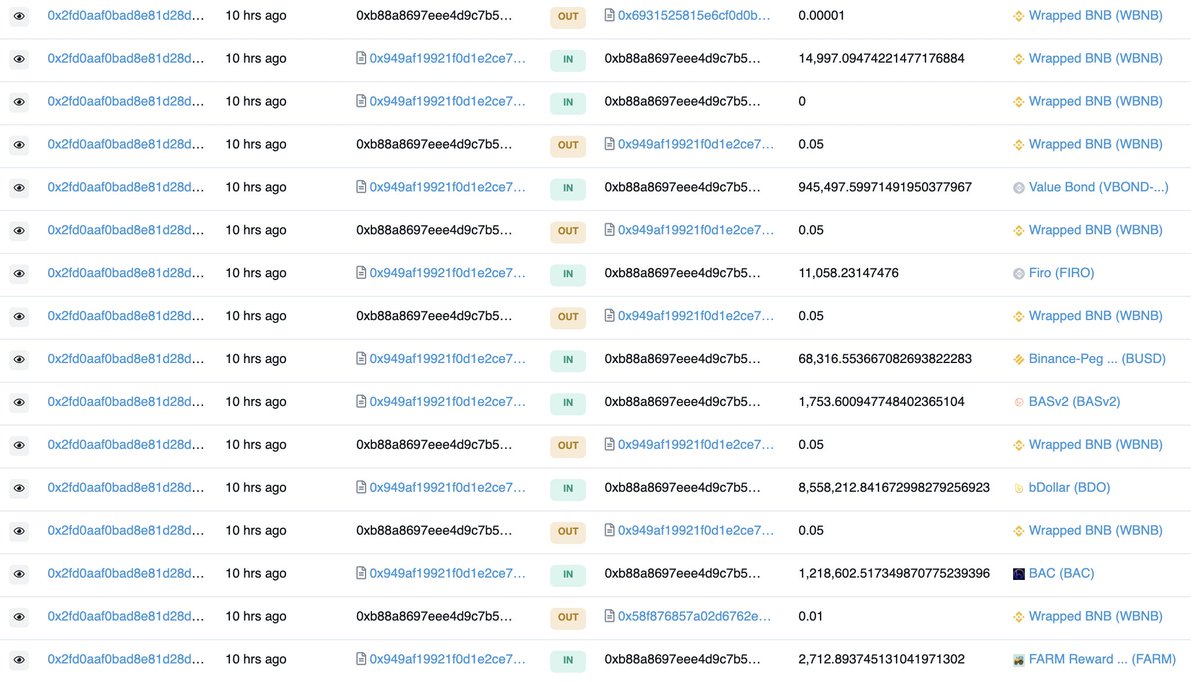
Here are 9 of the 16 pools that were attacked:
- vBSWAP/WBNB (70/30)
- gvVALUE/BUSD (98/2)
- BDO/BUSD (80/20)
- vBSWAP/BUSD (98/2)
- FARM/WBNB (70/30)
- IRON/STEEL (60/40)
- BDO/vBSWAP (70/30)
- BAC/BUSD (80/20)
- BASv2/WBNB (60/40)
Here are 9 of the 16 pools that were attacked:
- vBSWAP/WBNB (70/30)
- gvVALUE/BUSD (98/2)
- BDO/BUSD (80/20)
- vBSWAP/BUSD (98/2)
- FARM/WBNB (70/30)
- IRON/STEEL (60/40)
- BDO/vBSWAP (70/30)
- BAC/BUSD (80/20)
- BASv2/WBNB (60/40)
3/8
Stolen funds:
- 15k BNB
- 2.7k FARM
- 1.7k BASv2
- 8.5M BDO
- 68.3k BUSD
- 41.4k MDG
- 945k VBOND
- 1.2M BAC
- 11k FIRO
These tokens were swapped to 3.24k anyETH and withdrawn to Ethereum.
Stolen funds:
- 15k BNB
- 2.7k FARM
- 1.7k BASv2
- 8.5M BDO
- 68.3k BUSD
- 41.4k MDG
- 945k VBOND
- 1.2M BAC
- 11k FIRO
These tokens were swapped to 3.24k anyETH and withdrawn to Ethereum.
4/8
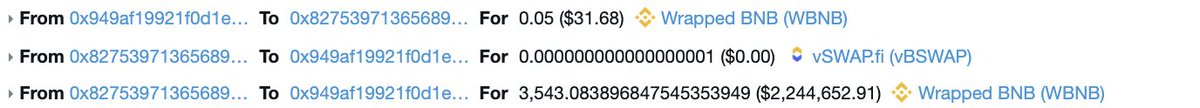
The exploit looked like this:
1. First of all, the attacker sends a small amount of a second token to pair addresses
2. Makes a swap in which they want to withdraw a small amount of the first token and a lot of the second token
The exploit looked like this:
1. First of all, the attacker sends a small amount of a second token to pair addresses
2. Makes a swap in which they want to withdraw a small amount of the first token and a lot of the second token
5/8
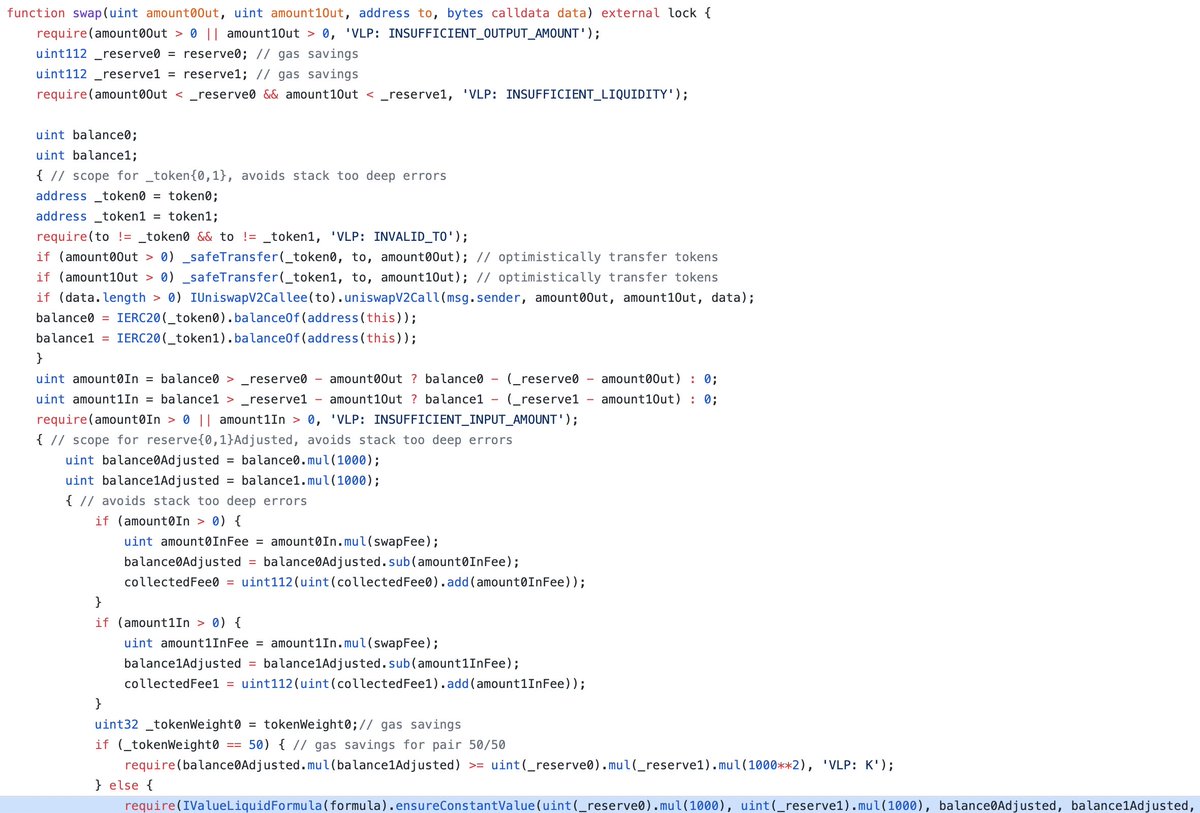
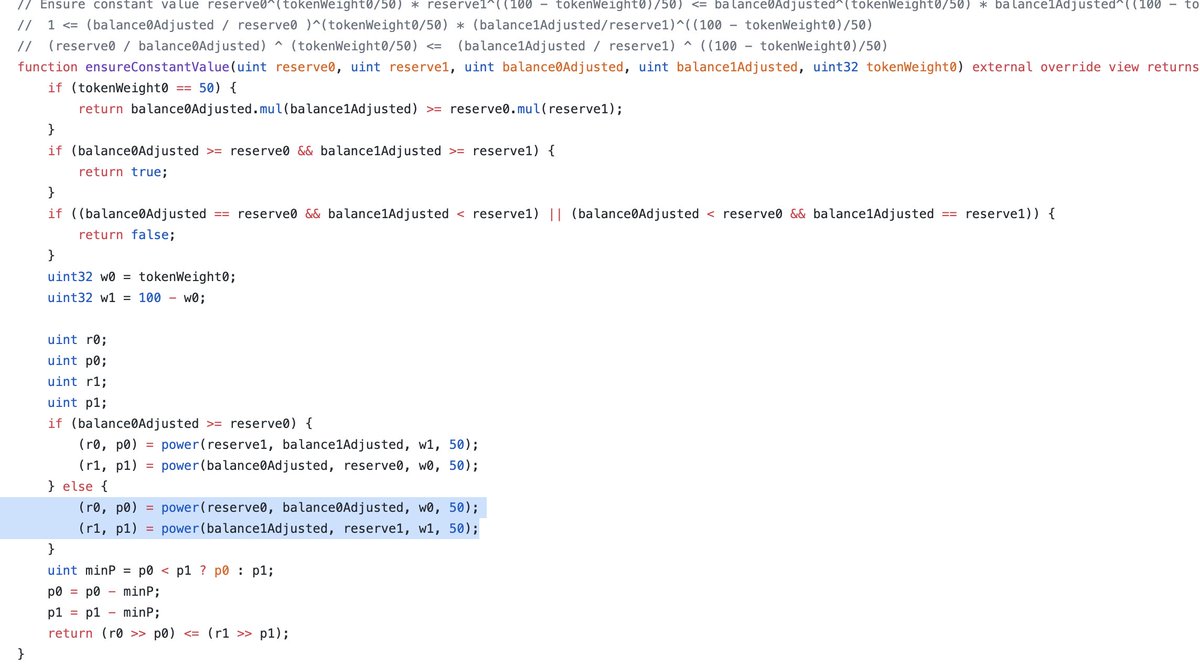
3. Due to incorrect use of the Bancor formula, pair contracts consider a swap to be successful (Exploit part)
4. The attacker swaps the first tokens for the second in the same pool and repeats this operation until the exploit allows it.
3. Due to incorrect use of the Bancor formula, pair contracts consider a swap to be successful (Exploit part)
4. The attacker swaps the first tokens for the second in the same pool and repeats this operation until the exploit allows it.

 Read on Twitter
Read on Twitter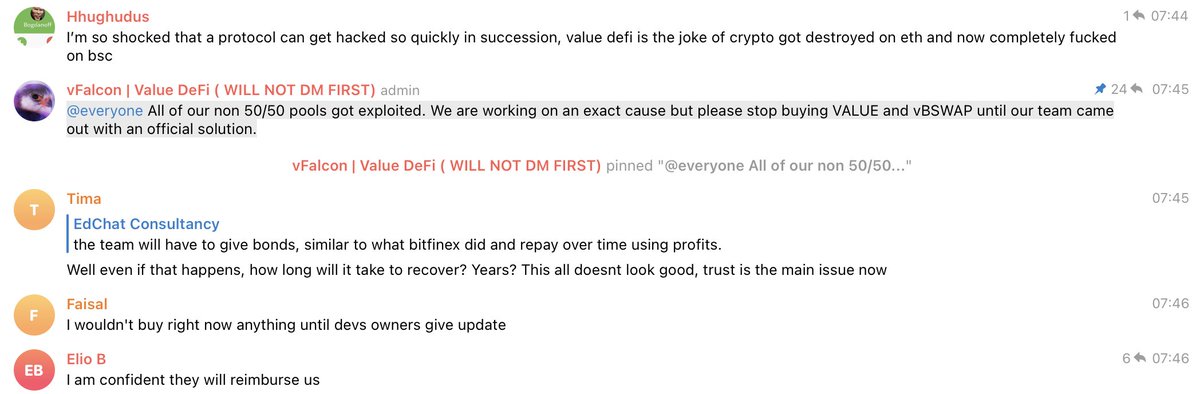 " title="1/8Another weekend with a DeFi exploit on BSC, and this time the AMM called vSwap from @value_defi is in trouble.About $11M was stolen today from non 50/50 pools, in addition to $6M already lost this week as a result of contract reinitialization.Let’s see what happenedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>
" title="1/8Another weekend with a DeFi exploit on BSC, and this time the AMM called vSwap from @value_defi is in trouble.About $11M was stolen today from non 50/50 pools, in addition to $6M already lost this week as a result of contract reinitialization.Let’s see what happenedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>