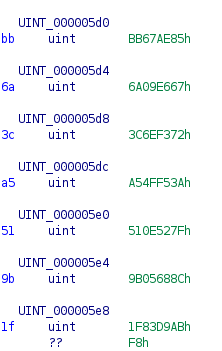
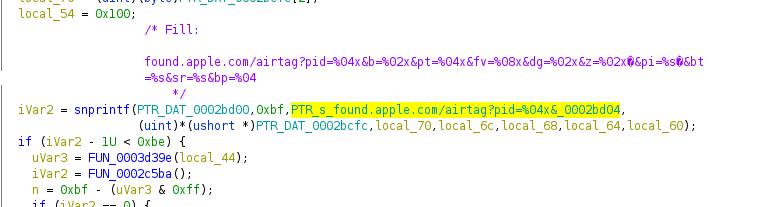
Continuing the tweet-chain of @colinoflynn on AirTag hacking, we will look at the flash contents now! https://twitter.com/colinoflynn/status/1390486554586587139">https://twitter.com/colinofly...
Similar to most Apple embedded devices, the AirTags also seem to run RTKit... And this is where it gets interesting: It& #39;s a DEBUG build - debug builds have more functionality, and sometimes more logs & co - this is good news!
/cc @naehrdine
/cc @naehrdine
Also looks like the firmware for the U1 DSP is on the flash, as you can find a ton of AArch64 instructions
Next step: Dump the rkos images contained in the firmware...
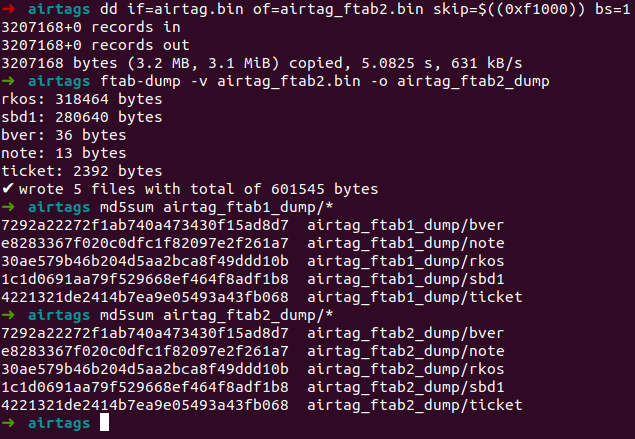
Using ftab-dump ( https://github.com/19h/ftab-dump )">https://github.com/19h/ftab-... it& #39;s as simple as this  https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">
Ohhh, what do we have here? This looks a lot like it might be an nRF52 firmware, which is the microcontroller used on the AirTag!
Hmm too bad, looks like it& #39;s just a reset vector, not actual firmware :)
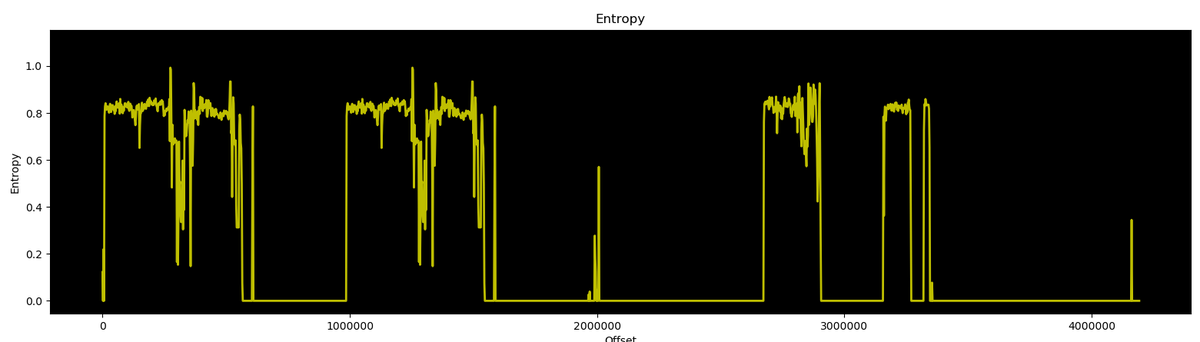
Also here& #39;s the entropy graph of the whole thing, looks like nothing is encrypted :)
I still remember when I first saw this Apple note - in the firmware images of my 3rd generation iPod when I just got started with hardware/firmware reversing  https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">
Well hello there, nRF52 firmware https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥸" title="Disguised face" aria-label="Emoji: Disguised face">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥸" title="Disguised face" aria-label="Emoji: Disguised face">
(If someone close to Stuttgart has too many AirTags and can spare one.. hit me up  https://abs.twimg.com/emoji/v2/... draggable="false" alt="👀" title="Augen" aria-label="Emoji: Augen">)
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👀" title="Augen" aria-label="Emoji: Augen">)
For those playing along at home: Loaded the firmware starting at 0x28D000 into Ghidra, loading offset seems to be 0x1c000 - guessing that there& #39;s a bootloader in front of that?!
Then used SVD-Loader to load an nrf52 SVD I found - it& #39;s not super detailed but gets the job done
Then used SVD-Loader to load an nrf52 SVD I found - it& #39;s not super detailed but gets the job done
Sweet, picking some tags up in an hour, that should be fun https://abs.twimg.com/emoji/v2/... draggable="false" alt="😬" title="Grimasse schneidendes Gesicht" aria-label="Emoji: Grimasse schneidendes Gesicht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😬" title="Grimasse schneidendes Gesicht" aria-label="Emoji: Grimasse schneidendes Gesicht">

 Read on Twitter
Read on Twitter
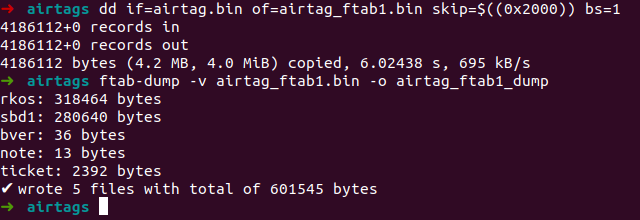 " title="Using ftab-dump ( https://github.com/19h/ftab-... it& #39;s as simple as this https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">" class="img-responsive" style="max-width:100%;"/>
" title="Using ftab-dump ( https://github.com/19h/ftab-... it& #39;s as simple as this https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">" class="img-responsive" style="max-width:100%;"/>
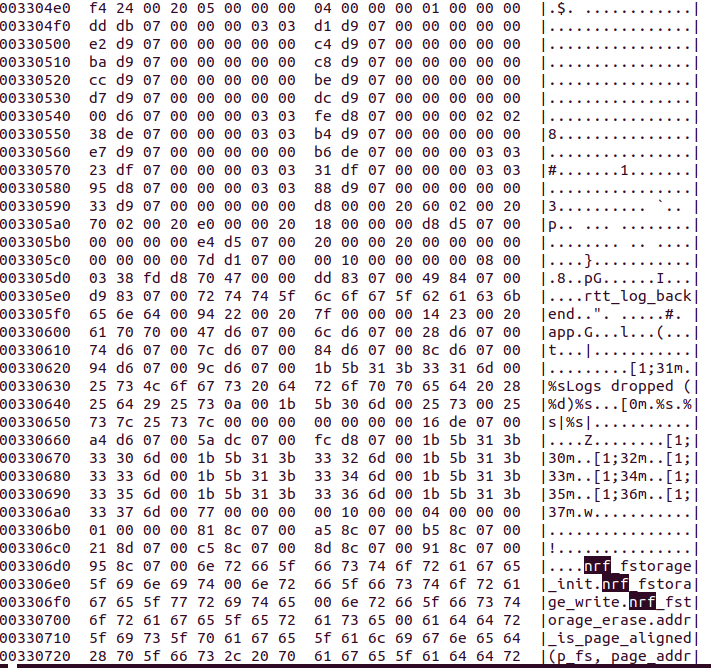
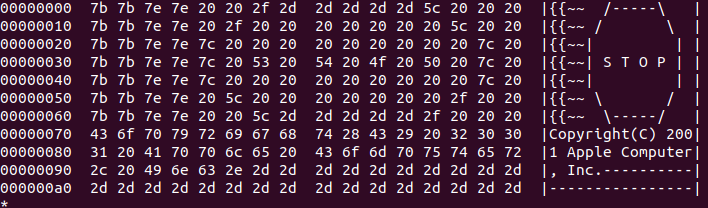 " title="I still remember when I first saw this Apple note - in the firmware images of my 3rd generation iPod when I just got started with hardware/firmware reversing https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">" class="img-responsive" style="max-width:100%;"/>
" title="I still remember when I first saw this Apple note - in the firmware images of my 3rd generation iPod when I just got started with hardware/firmware reversing https://abs.twimg.com/emoji/v2/... draggable="false" alt="😀" title="Grinsendes Gesicht" aria-label="Emoji: Grinsendes Gesicht">" class="img-responsive" style="max-width:100%;"/>
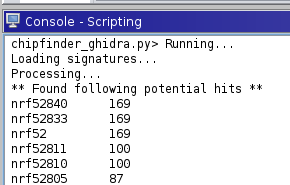 " title="Well hello there, nRF52 firmwarehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥸" title="Disguised face" aria-label="Emoji: Disguised face">" class="img-responsive" style="max-width:100%;"/>
" title="Well hello there, nRF52 firmwarehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥸" title="Disguised face" aria-label="Emoji: Disguised face">" class="img-responsive" style="max-width:100%;"/>