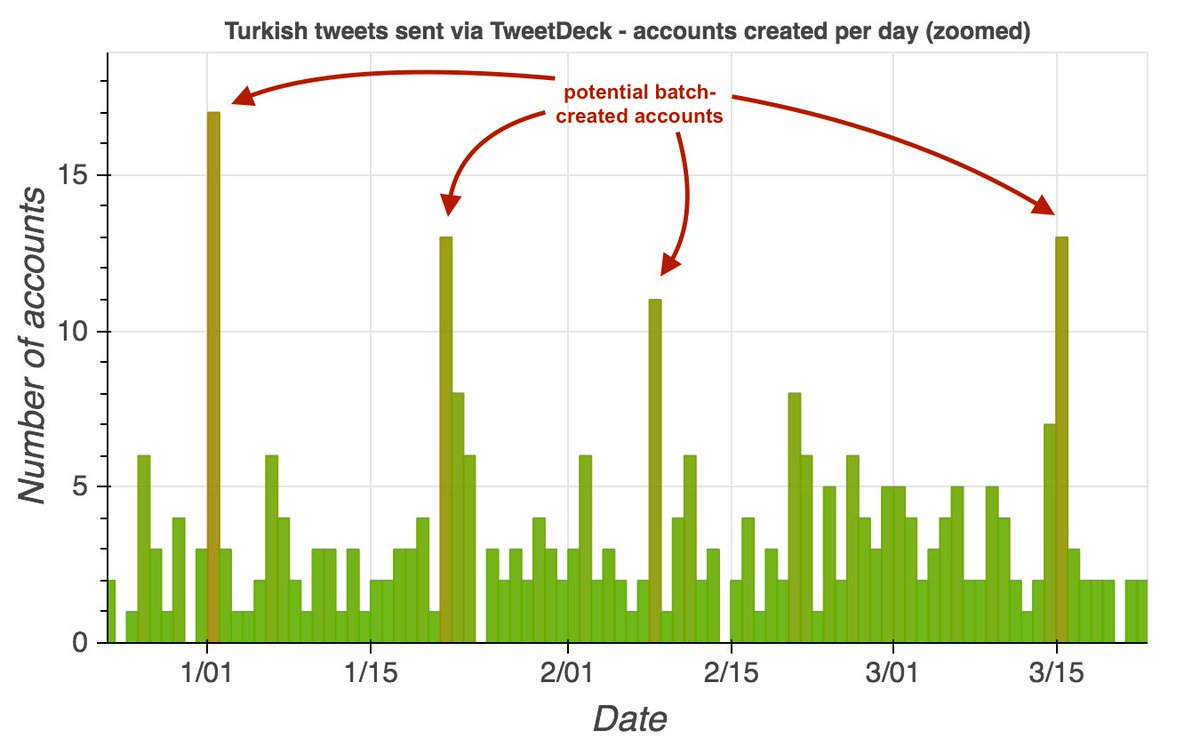
How does one find bot/sock networks? One technique that sometimes bears fruit is to gather a bunch of tweets with some common characteristic (in this example, Turkish tweet sent with TweetDeck), plot the account creation dates, and look for spikes.
cc: @ZellaQuixote
cc: @ZellaQuixote
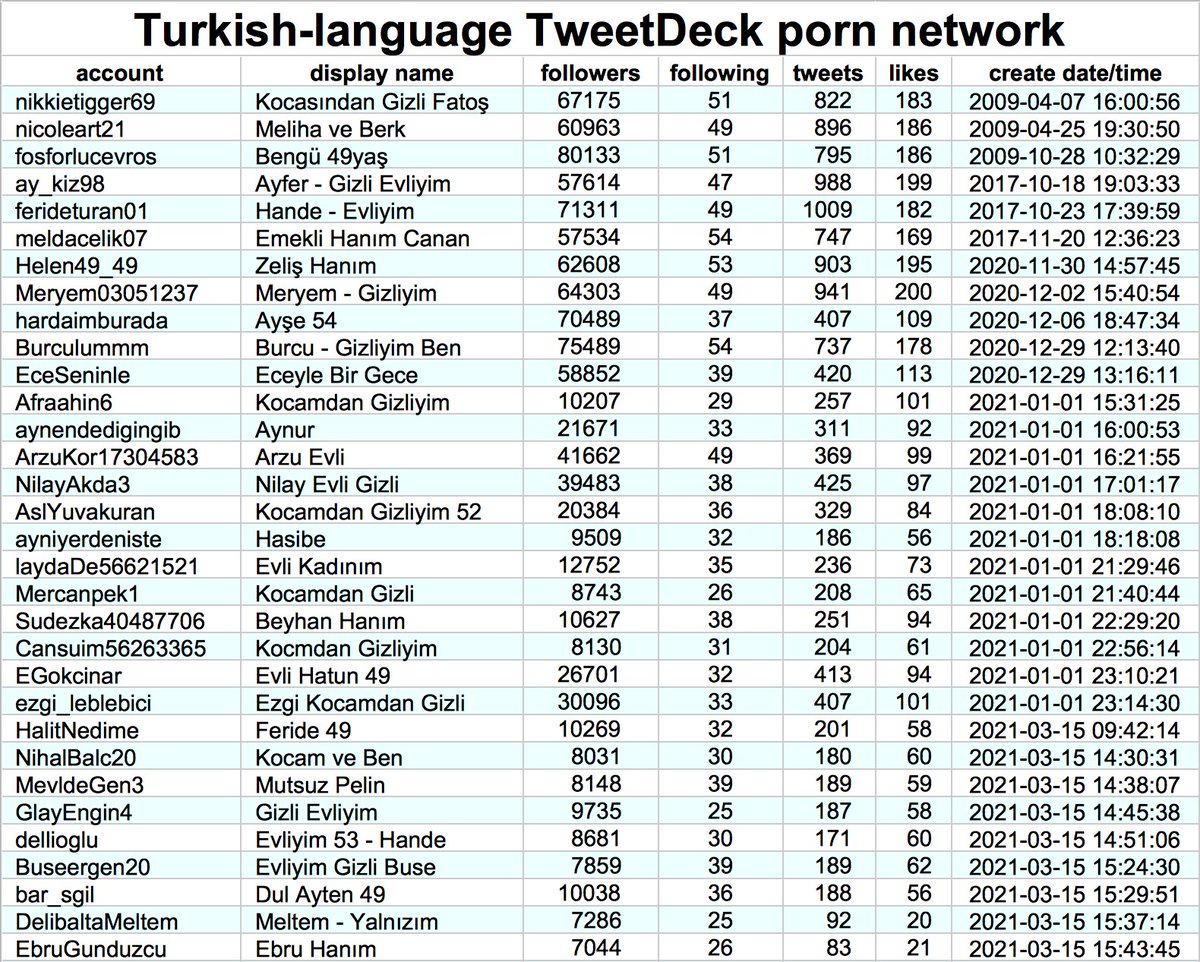
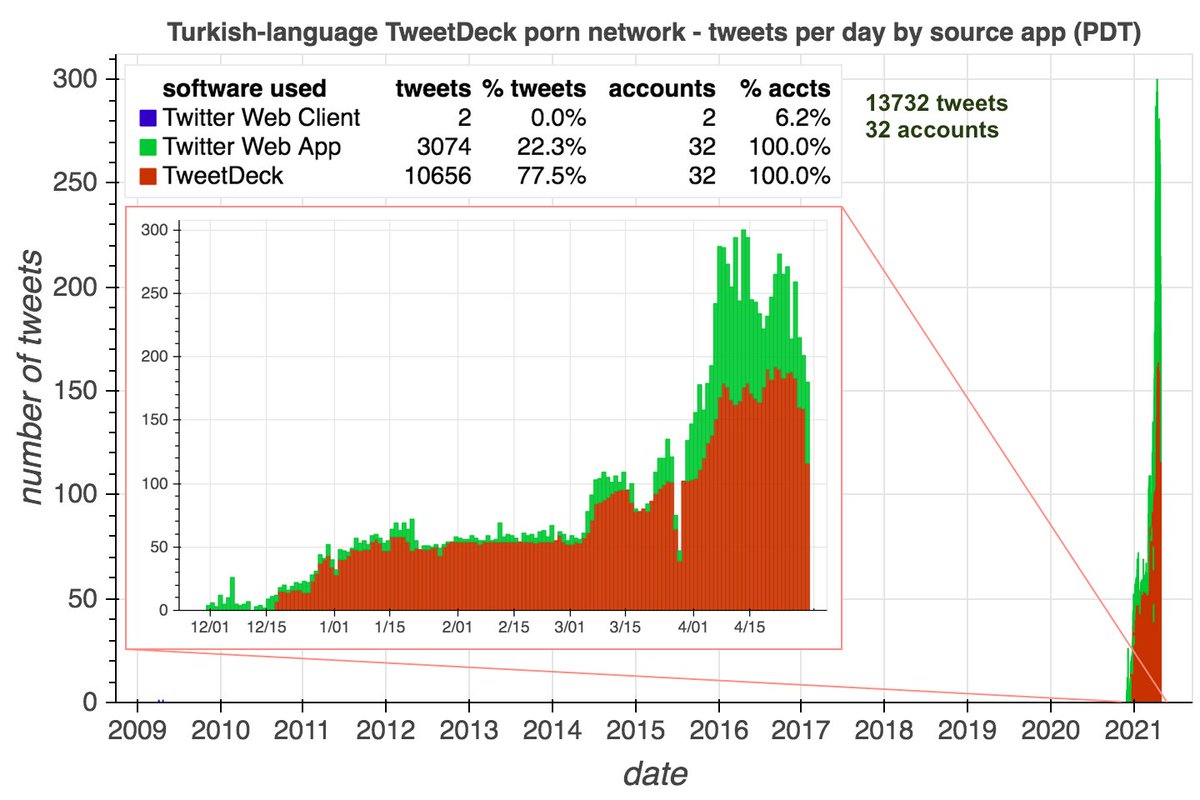
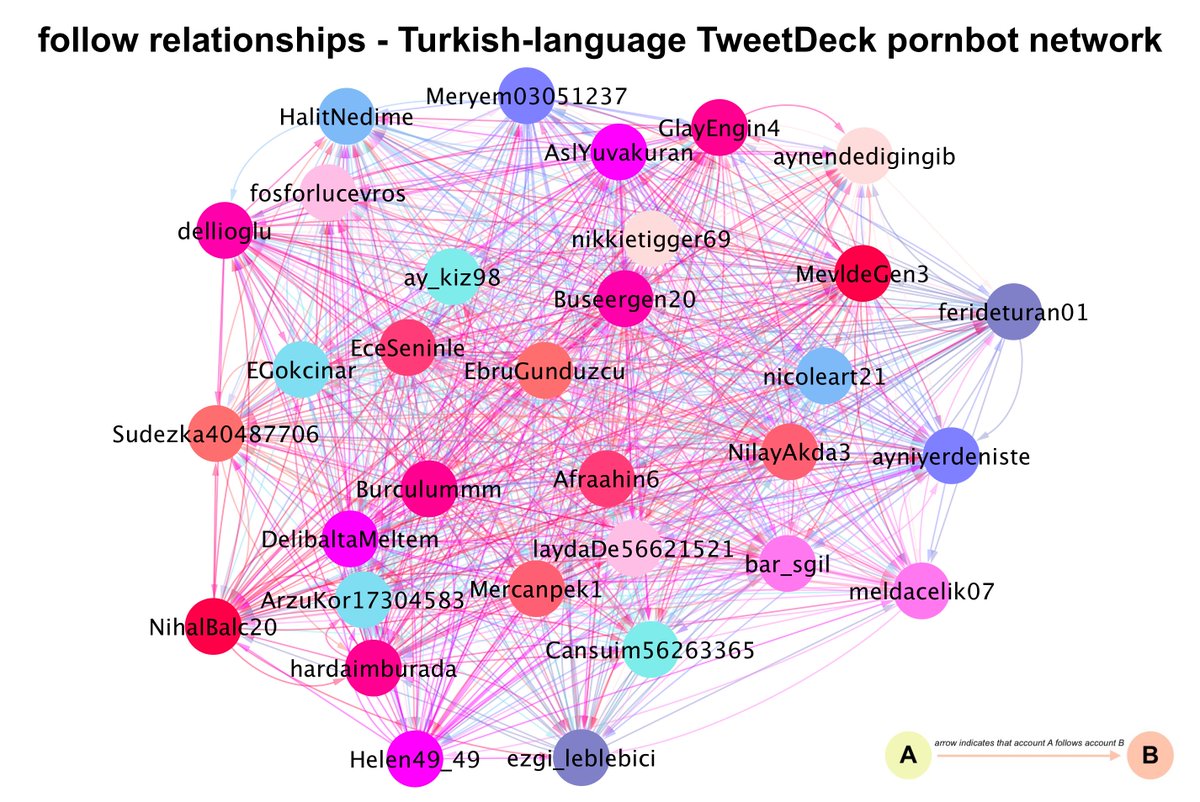
Two of the creation date spikes (Jan 1 and Mar 15, 2021) are batches of accounts that are part of the same botnet: a 32-account porn network whose members tweet at the same times each day via TweetDeck and occasionally via the Twitter Web App. Most were created in 2020 or 2021.
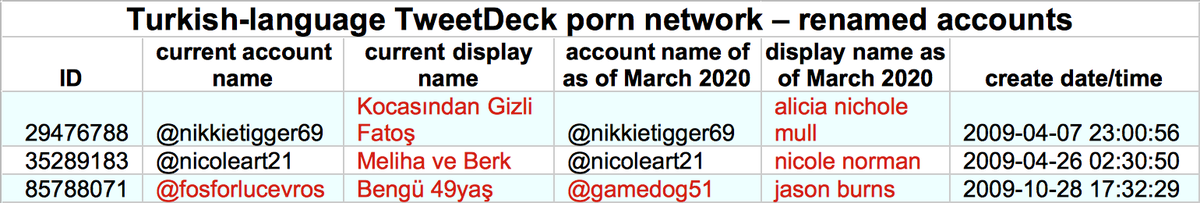
The botnet also contains three accounts created in 2009. It is possible that these were purchased/hacked/otherwise repurposed, as all three have changed their display name significantly and one has changed its @-name as well.
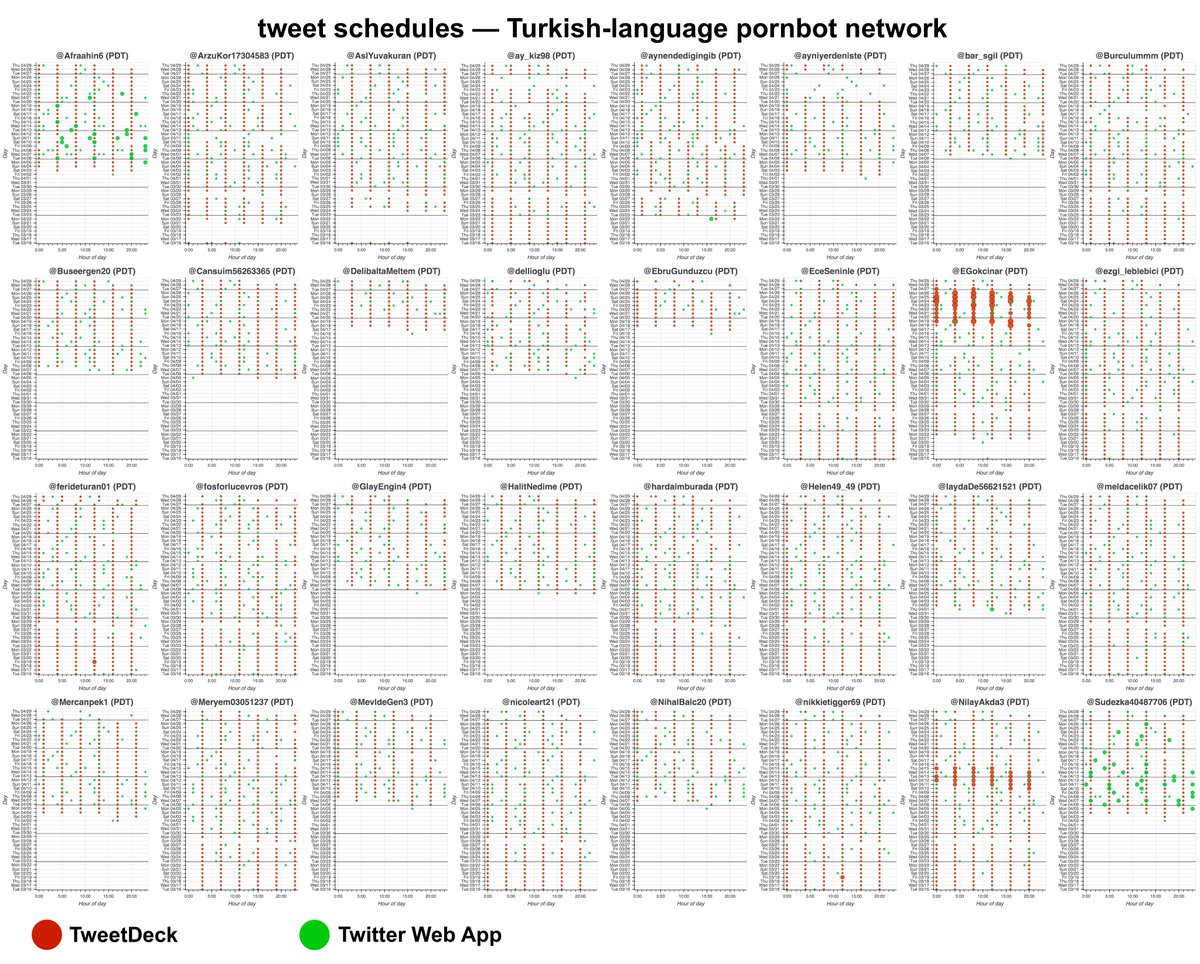
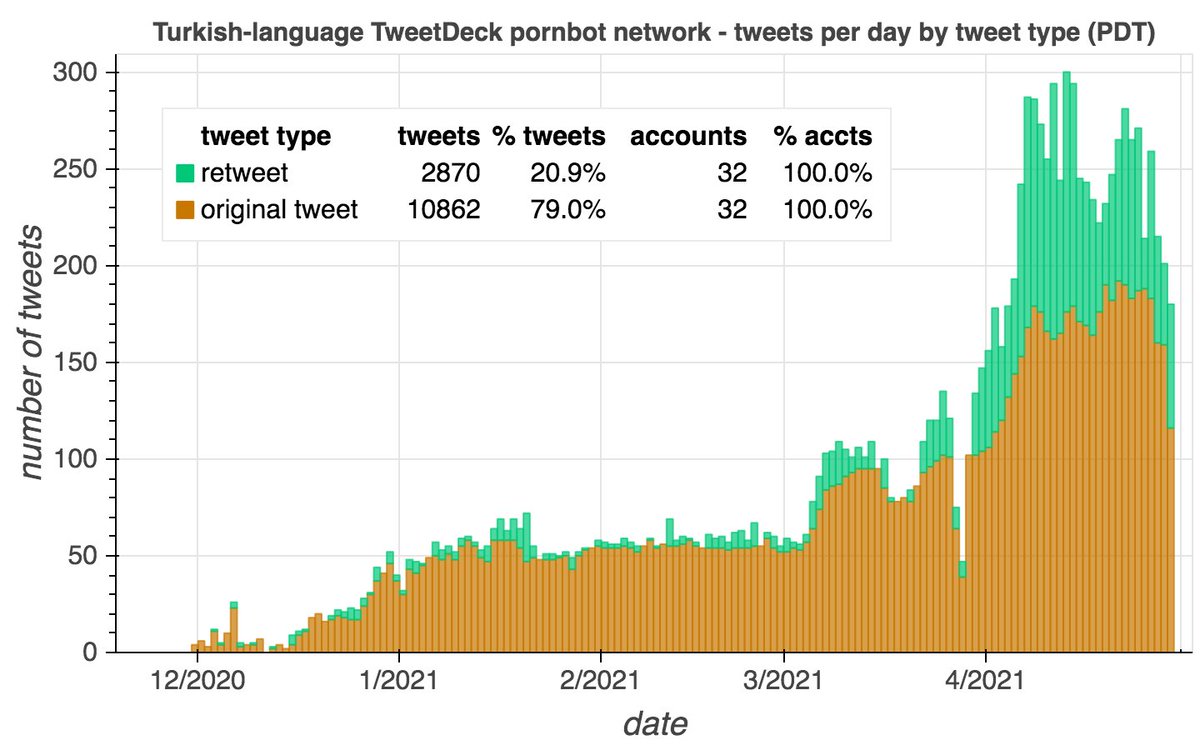
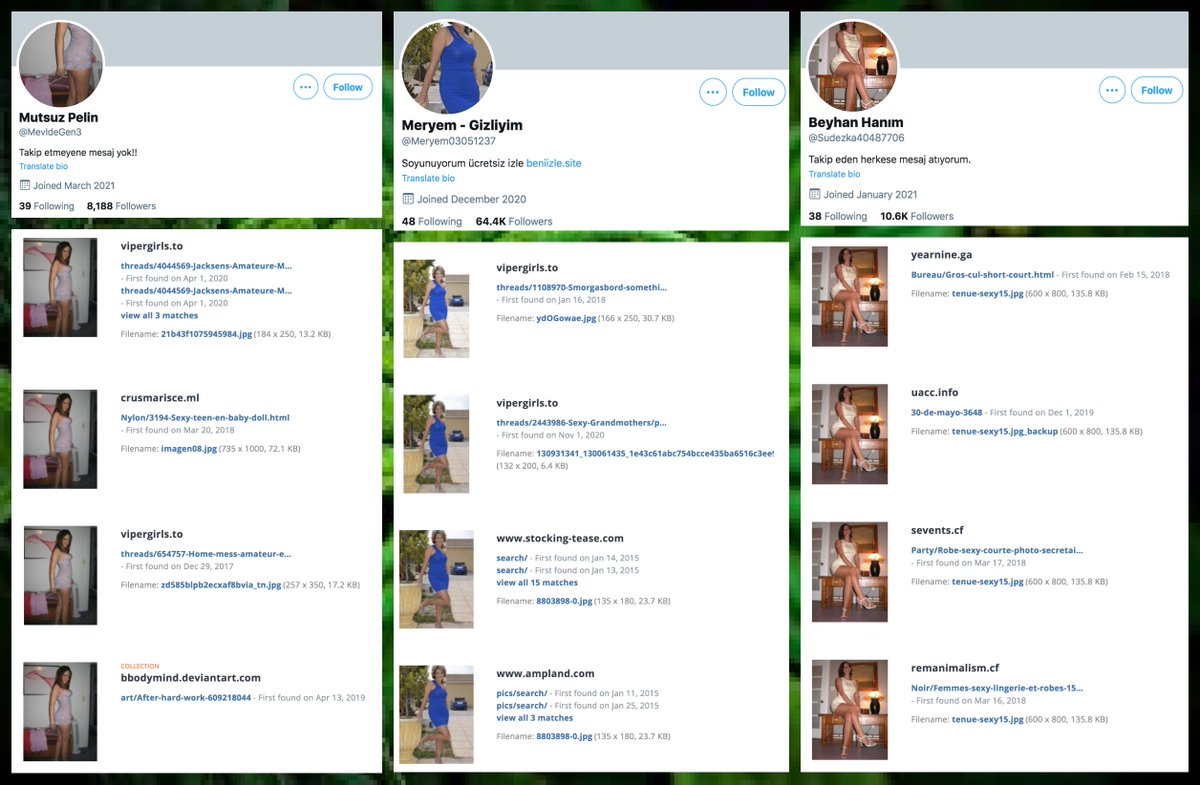
This network posts two types of tweets: original tweets sent mostly via TweetDeck, and retweets sent via the Twitter Web App. The original tweets are repetitive porn tweets with images, while the retweets are mostly of other accounts in the network.
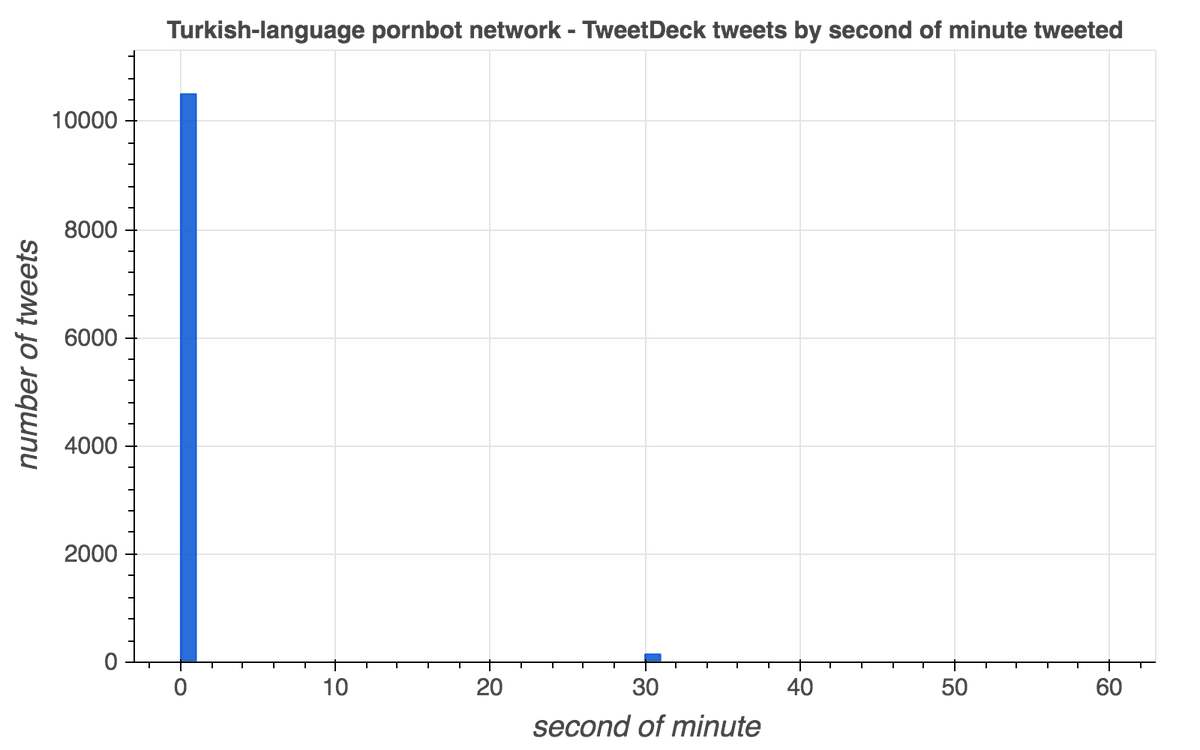
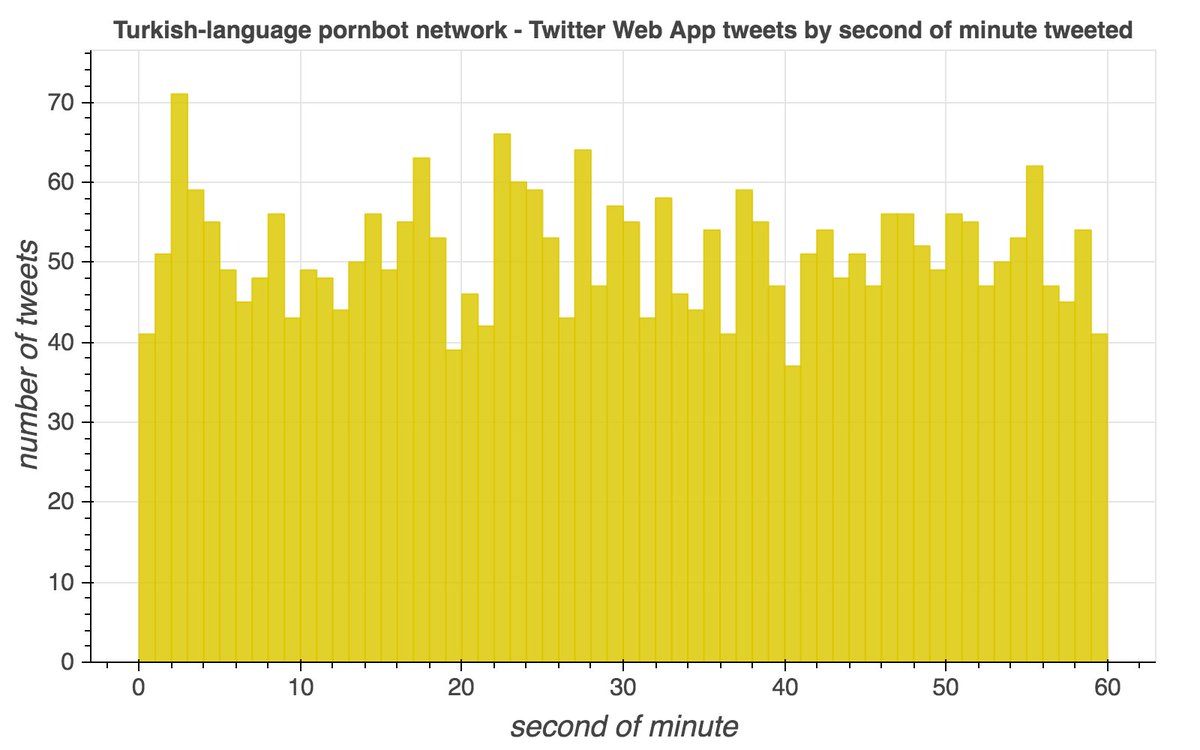
The scheduling features of both TweetDeck and the Twitter website (usually) post scheduled tweets in the first second of the minute for which they are scheduled. Based on this, this pornbot network& #39;s TweetDeck tweets appear to be scheduled, while its web tweets do not.
(thread with more background on the timing of scheduled TweetDeck tweets) https://twitter.com/conspirator0/status/1237193515177857026">https://twitter.com/conspirat...
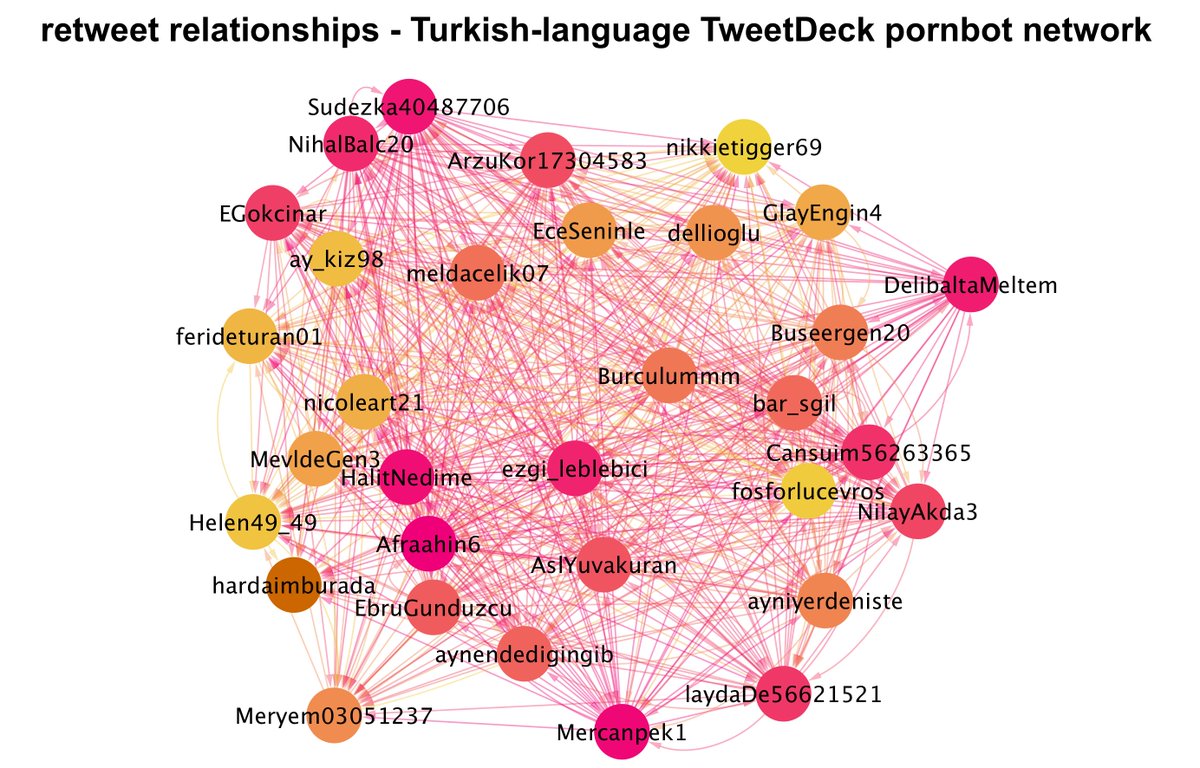
Every account in this botnet follows or is followed by every other account in the botnet. (Some follows are mutual, some are not.) The bots follow very few accounts outside the network, mostly large Turkish accounts and porn accounts.

 Read on Twitter
Read on Twitter