1/  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer">  https://abs.twimg.com/emoji/v2/... draggable="false" alt="📝" title="Memo" aria-label="Emoji: Memo">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="📝" title="Memo" aria-label="Emoji: Memo">  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥞" title="Pfannkuchen" aria-label="Emoji: Pfannkuchen">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥞" title="Pfannkuchen" aria-label="Emoji: Pfannkuchen">  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🆚" title="Quadratisches VS" aria-label="Emoji: Quadratisches VS">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🆚" title="Quadratisches VS" aria-label="Emoji: Quadratisches VS">  https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2">
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Polizeiautos mit drehendem Licht" aria-label="Emoji: Polizeiautos mit drehendem Licht"> Smart Contract Bug found in Pancake V2
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Polizeiautos mit drehendem Licht" aria-label="Emoji: Polizeiautos mit drehendem Licht"> Smart Contract Bug found in Pancake V2  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Polizeiautos mit drehendem Licht" aria-label="Emoji: Polizeiautos mit drehendem Licht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Polizeiautos mit drehendem Licht" aria-label="Emoji: Polizeiautos mit drehendem Licht">
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer">: Pancake new router is incompatible with Pancake LP implementation.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer">: Pancake new router is incompatible with Pancake LP implementation.
Users may get __revert__ txs upon __swaps__ due to the bug.
Vulnerability was reported to @PancakeSwap team asap.
Thread below https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
Users may get __revert__ txs upon __swaps__ due to the bug.
Vulnerability was reported to @PancakeSwap team asap.
Thread below
2/ After @PancakeSwap V2 announcement, we have been working on supporting the new V2 pools.
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen"> As with our security standard, we always perform smart contract review and testing, to ensure our users’ safety.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen"> As with our security standard, we always perform smart contract review and testing, to ensure our users’ safety.
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> We have found and informed the @PancakeSwap team on the issue.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> We have found and informed the @PancakeSwap team on the issue.
3/  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?
The question comes down to: what changes from Pancake V1 to V2?
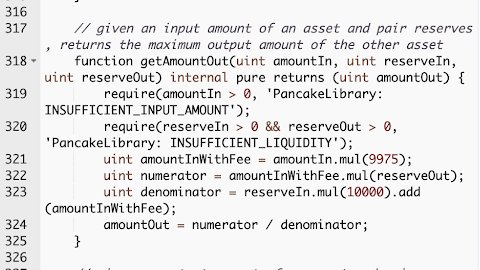
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2%
https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2%  https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%
https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev address
https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev address
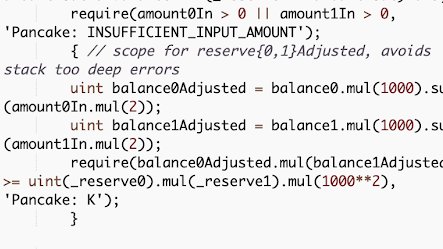
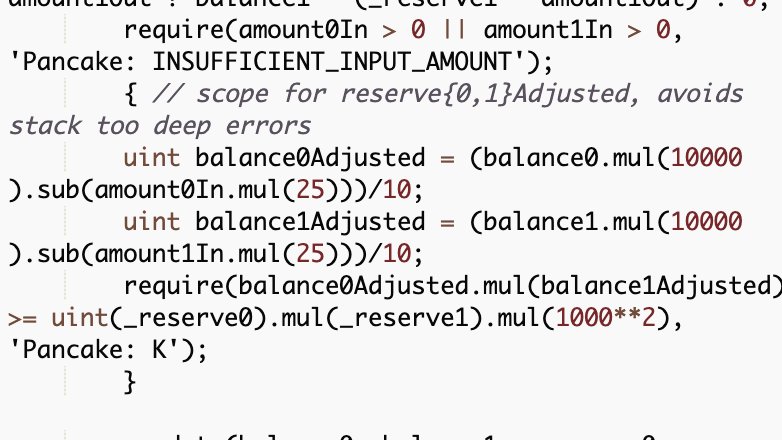
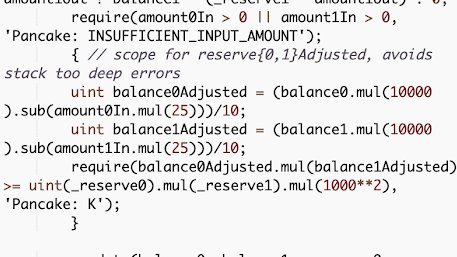
Below are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.
The question comes down to: what changes from Pancake V1 to V2?
Below are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.
4/ On the LP pair side, __swap__ function also encodes the swap fee for constant product calculation. Here are the V1 and V2 implementation:
5/  https://abs.twimg.com/emoji/v2/... draggable="false" alt="👀" title="Augen" aria-label="Emoji: Augen"> At first glance, the implementation seems correct, as the parameters reflect 0.2% and 0.25% in the old and new versions, respectively.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👀" title="Augen" aria-label="Emoji: Augen"> At first glance, the implementation seems correct, as the parameters reflect 0.2% and 0.25% in the old and new versions, respectively.
However, in Solidity, there is no floating-point.
All divisions will be rounded down https://abs.twimg.com/emoji/v2/... draggable="false" alt="⬇️" title="Pfeil nach unten" aria-label="Emoji: Pfeil nach unten">.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="⬇️" title="Pfeil nach unten" aria-label="Emoji: Pfeil nach unten">.
However, in Solidity, there is no floating-point.
All divisions will be rounded down
6/ So, __balance0Adjusted__ and __balance1Adjusted__ can have their actual values truncated, reverting the next __require__ statement when checked for the constant product monovariant.
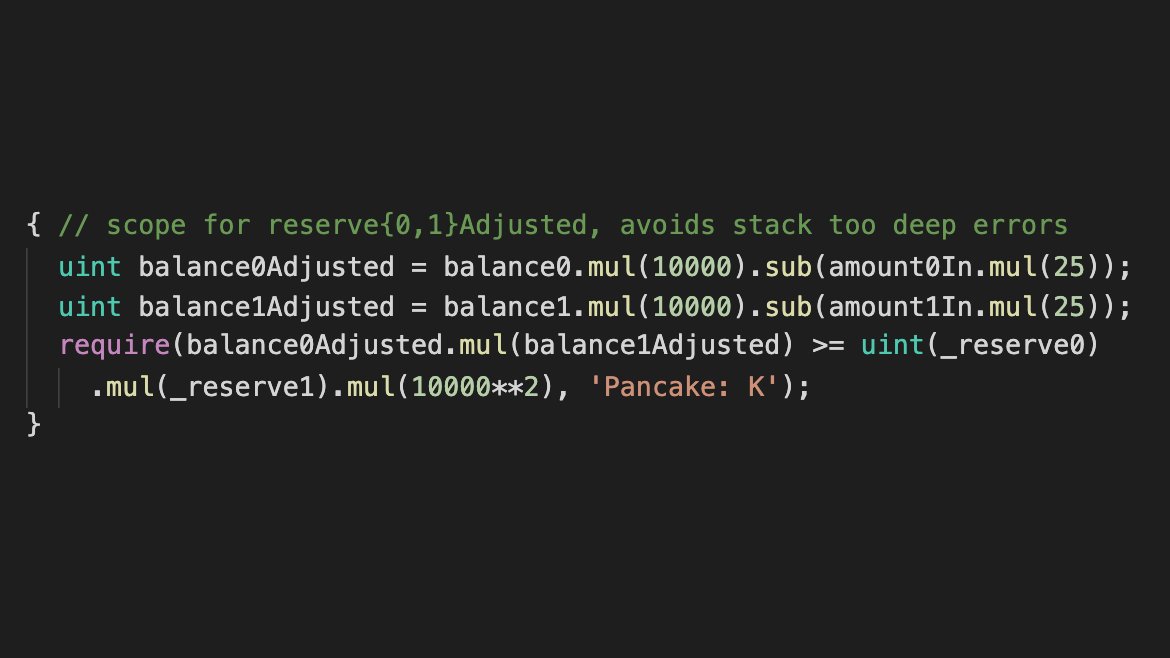
7/ Instead of performing divisions, it’s mostly always better to compare the cross-multiplication. This should be the correct implementation:
9/ So, the next question is: How does this affect #AlphaHomora?
#AlphaHomora performs multiple complex txs into one, including swaps. This means that users who open new positions, refill existing positions, and also liquidations may get revert txs.
#AlphaHomora performs multiple complex txs into one, including swaps. This means that users who open new positions, refill existing positions, and also liquidations may get revert txs.
10/  https://abs.twimg.com/emoji/v2/... draggable="false" alt="💦" title="Schweißtropfen" aria-label="Emoji: Schweißtropfen"> As liquidation is one of the core security features of #AlphaHomora to keep the protocol solvent, this bug can cause security loopholes in our system.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="💦" title="Schweißtropfen" aria-label="Emoji: Schweißtropfen"> As liquidation is one of the core security features of #AlphaHomora to keep the protocol solvent, this bug can cause security loopholes in our system.
Even if the chances of tx reversions are not high, security is one of @AlphaFinanceLab’s top priorities.
Even if the chances of tx reversions are not high, security is one of @AlphaFinanceLab’s top priorities.
11/ After we’ve found the bug and made sure it’s reproducible, we immediately contacted @PancakeSwap team to inform them re:vulnerability.
They immediately responded and confirmed the vulnerability within minutes.
They immediately responded and confirmed the vulnerability within minutes.
12/ To fix the issue, a new factory, router, and LP pairs need to be deployed.
We’ll be working towards supporting these new pools and again performing checks and tests on the new implementation.
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🛄" title="Gepäckausgabe" aria-label="Emoji: Gepäckausgabe"> And so let the new migration begin... https://twitter.com/PancakeSwap/status/1385501978667618304">https://twitter.com/PancakeSw...
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🛄" title="Gepäckausgabe" aria-label="Emoji: Gepäckausgabe"> And so let the new migration begin... https://twitter.com/PancakeSwap/status/1385501978667618304">https://twitter.com/PancakeSw...
We’ll be working towards supporting these new pools and again performing checks and tests on the new implementation.

 Read on Twitter
Read on Twitter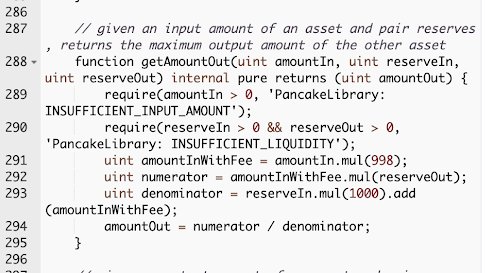 So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers." title="3/ https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.">
So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers." title="3/ https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.">
 So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers." title="3/ https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.">
So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers." title="3/ https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐛" title="Käfer" aria-label="Emoji: Käfer"> So, what is the actual bug?The question comes down to: what changes from Pancake V1 to V2?https://abs.twimg.com/emoji/v2/... draggable="false" alt="1️⃣" title="Tastenkappe Ziffer 1" aria-label="Emoji: Tastenkappe Ziffer 1"> Swap fees: 0.2% https://abs.twimg.com/emoji/v2/... draggable="false" alt="➡️" title="Pfeil nach rechts" aria-label="Emoji: Pfeil nach rechts"> 0.25%https://abs.twimg.com/emoji/v2/... draggable="false" alt="2️⃣" title="Tastenkappe Ziffer 2" aria-label="Emoji: Tastenkappe Ziffer 2"> Fee distribution to LPs, to dev addressBelow are the router __getAmountOut__ implementations (V1 & V2). The difference lies in the numbers.">