The "lawful interception" industry is a hive of scum and villainy: these are powerful, wildly profitable companies who search out defects in widely used software, then weaponize them and sell them to the world& #39;s most brutal dictators and death squads.
1/
1/
Their names are curses: The NSO Group, Palantir, and, of course, Cellebrite, who have pulled publicity stunts like offering $1m bounties for exploitable Iphone defects that can be turned into cyberweapons.
2/
2/
Late last year, Cellebrite announced that they& #39;d added "support" for @signalapp to their top-selling cyberweapons, UFED and Physical Analyzer. The announcement was deliberately misleading, claiming to have "cracked the encryption" (they haven& #39;t and can& #39;t do this).
3/
3/
Now, Signal founder Moxie Marlinspike has turned the tables on Cellebrite in a delicious act of security analysis, which he wrote up in detail on Signal& #39;s corporate blog:
https://signal.org/blog/cellebrite-vulnerabilities/
4/">https://signal.org/blog/cell...
https://signal.org/blog/cellebrite-vulnerabilities/
4/">https://signal.org/blog/cell...
As Marlinspike explains, the job of Cellebrite& #39;s tools is to ingest untrusted input - the files from a seized mobile device - and parse them. This is a very dangerous task: "This is the space in which virtually all security vulnerabilities originate."
5/
5/
Incredibly, Cellebrite& #39;s programmers do no input sanitizing, just trusting all the files they receive and passing them from subroutine to subroutine. What& #39;s more, these subroutines call on wildly out-of-date software with dozens - even hundreds - of known vulnerabilities.
6/
6/
For example, the version of ffmpeg that Cellebrite bundles in its products was last patched in 2012; and more than ONE HUNDRED security updates have been released since then.
7/
7/
Marlinspike& #39;s investigation turned up other sources of shame and liability for Cellebrite, including pirated libraries from Apple& #39;s Itunes software, which he documents in detail.
8/
8/
Marlinspike intimates that he turned up more vulnerabilities than he enumerates in his analysis, but he is not making the kind of "responsible disclosure" to Cellebrite that is common among "white hat" security researchers.
9/
9/
Rather, he& #39;s made an offer to fully disclose his findings to Cellebrite only if they make a binding promise to engage in the same kinds of disclosures with the software they analyze - to pledge to help to patch bugs, rather than weaponizing them.
10/
10/
And in a move of pure petard-hoisting, Marlinspike describes a proof-of-concept attack on Cellebrite, a corrupted file that can execute code on the Cellebrite device that will alter all future AND past reports, "with no detectable timestamp changes or checksum failures."
11/
11/
He says that these doctored files could corrupt Cellebrite data "at random, and would seriously call the data integrity of Cellebrite’s reports into question."
12/
12/
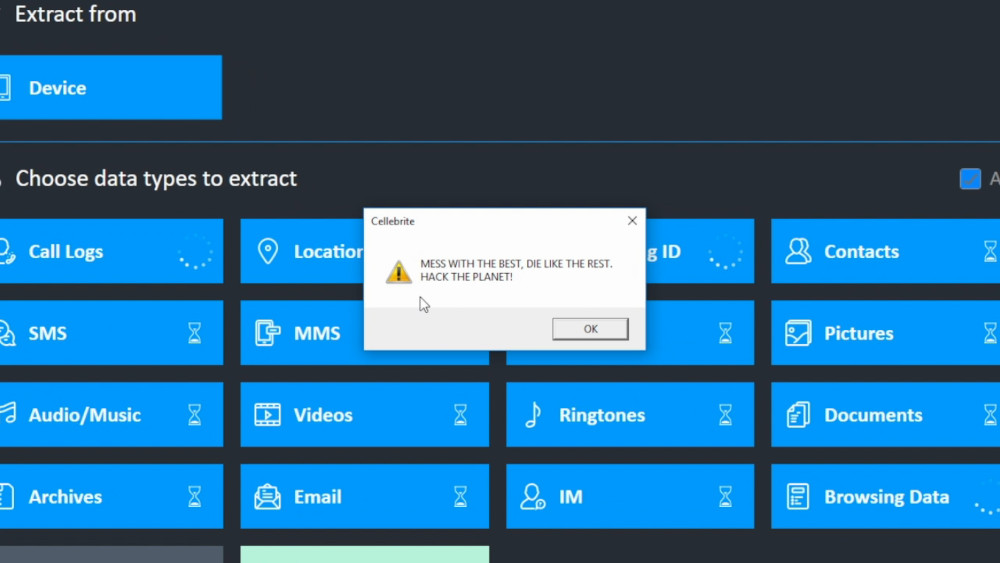
As proof of his proof-of-concept, Marlinspike includes a video (intercut with scenes from the classic movie HACKERS) in which a Cellebrite device slurps up files from an Iphone and then displays his victory message: "MESS WITH THE BEST, DIE LIKE THE REST. HACK THE PLANET!"
13/
13/
Marlinspike closes out the report by announcing some "completely unrelated news," that future versions of Signal will periodically pull functionally useless, "aesthetically pleasing" files and store them, inert, on users& #39; devices.
14/
14/
The implication is that Marlinspike is now in possession of a vast trove of zero-day exploits for Cellebrite products, and he is seeding those exploits in the wild on hundreds of millions of devices, booby-trapping them should they ever be plugged into a Cellebrite device.
15/
15/
The further implication is that any Cellebrite customer who encounters one of these booby-traps in the wild will lose the ability to trust ALL the data they EVER retrieved with a Cellebrite product, and will never be able to trust that product again.
Yum!
eof/
Yum!
eof/
ETA - If you& #39;d like an unrolled version of this thread to read or share, here& #39;s a link to it on http://pluralistic.net"> http://pluralistic.net , my surveillance-free, ad-free, tracker-free blog:
#petard">https://pluralistic.net/2021/04/22/ihor-kolomoisky/ #petard">https://pluralistic.net/2021/04/2...
#petard">https://pluralistic.net/2021/04/22/ihor-kolomoisky/ #petard">https://pluralistic.net/2021/04/2...

 Read on Twitter
Read on Twitter