2/ As far as we know, this is the first public reporting of the PSS activity, mainly targeting people in the Palestinian territories and Syria. They used their own low-sophistication malware disguised as secure chat applications + open-source malware tools.
3/ With our blog post, @Mdvily’s team is also sharing a deep-dive technical report on the Arid Viper activity and how this actor responded to enforcement by us and others in the industry over time https://about.fb.com/wp-content/uploads/2021/04/Technical-threat-report-Arid-Viper-April-2021.pdf">https://about.fb.com/wp-conten...
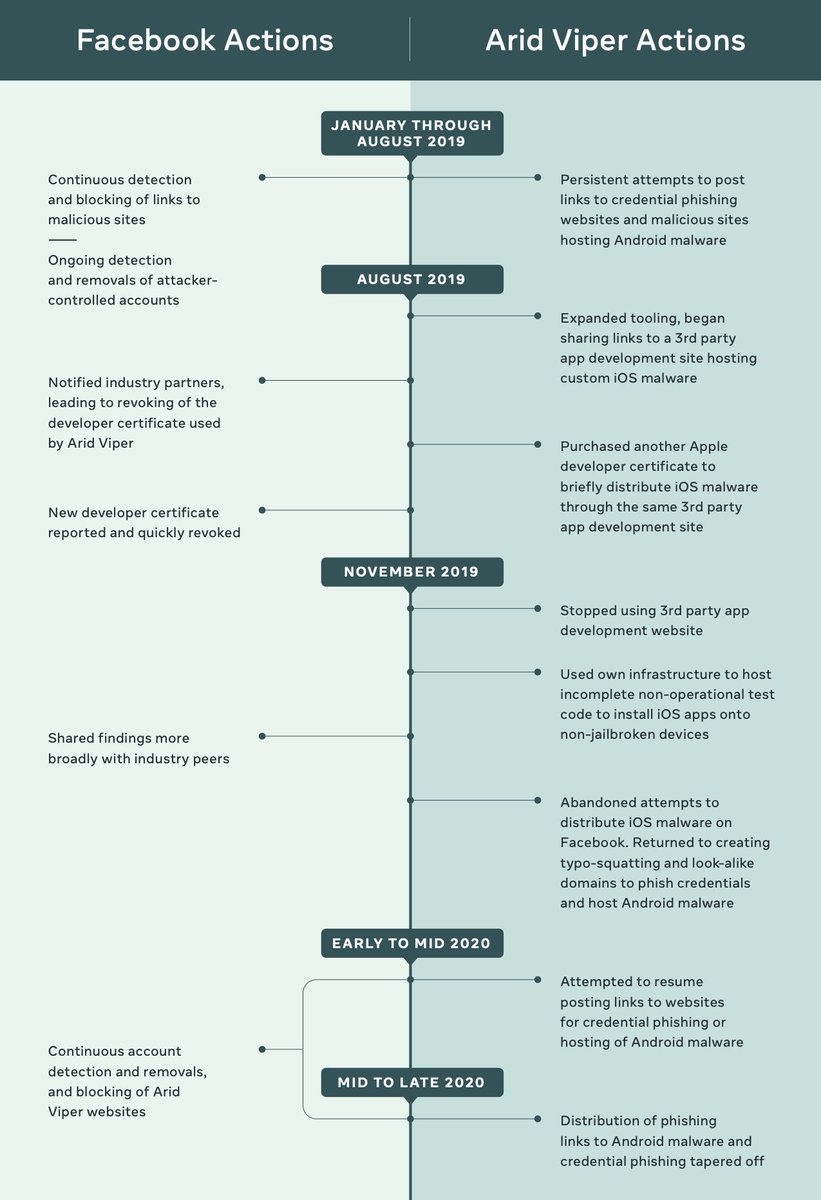
4/ We saw Arid Viper use sprawling infrastructure to support its operations, including over a hundred websites that either hosted iOS and Android malware, attempted to steal credentials through phishing or acted as command and control servers.
5/ This follows on our previous cyber-espionage threat reporting of operations from China last month and from Bangladesh and Vietnam in December. https://about.fb.com/news/2021/03/taking-action-against-hackers-in-china/">https://about.fb.com/news/2021...
6/ We’ve been tracking and disrupting these networks throughout the course of our investigation, and today’s announcement and accompanying threat report are an anthology of the insights we’ve gained which hopefully are helpful to the broader security research community.
7/ In addition to our enforcement, we shared information about this activity with industry peers and the security research community and alerted people who we believe were targeted by both groups. [end thread]

 Read on Twitter
Read on Twitter