If you liked Salmonella you& #39;re gonna love this
Last night someone used an *extremely* clever mechanism to take a hundred ETH from sandwich bots
Then a 2nd person jumped in and made 300 MORE ETH by exploiting other sandwich bots
Long thread on how https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇🏻" title="Rückhand Zeigefinger nach unten (heller Hautton)" aria-label="Emoji: Rückhand Zeigefinger nach unten (heller Hautton)">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇🏻" title="Rückhand Zeigefinger nach unten (heller Hautton)" aria-label="Emoji: Rückhand Zeigefinger nach unten (heller Hautton)">
Last night someone used an *extremely* clever mechanism to take a hundred ETH from sandwich bots
Then a 2nd person jumped in and made 300 MORE ETH by exploiting other sandwich bots
Long thread on how
To understand how this happened you need to know a bit about Flashbots
You can think of Flashbots as a way for users to directly communicate their transaction ordering preferences to to miners via "bundles" of transactions
You can think of Flashbots as a way for users to directly communicate their transaction ordering preferences to to miners via "bundles" of transactions
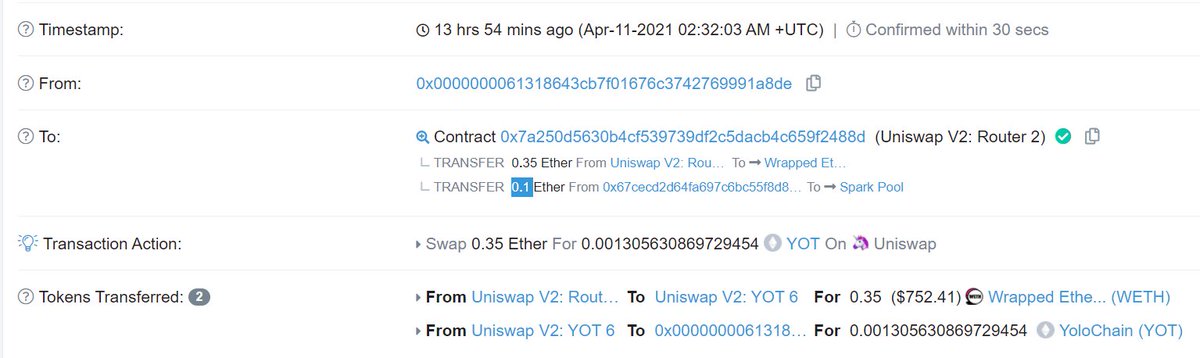
Instead of users paying transaction fees via gas prices, using Flashbots users pay fees via a smart contract call (block.coinbase.transfer) which transfers ETH to a miner
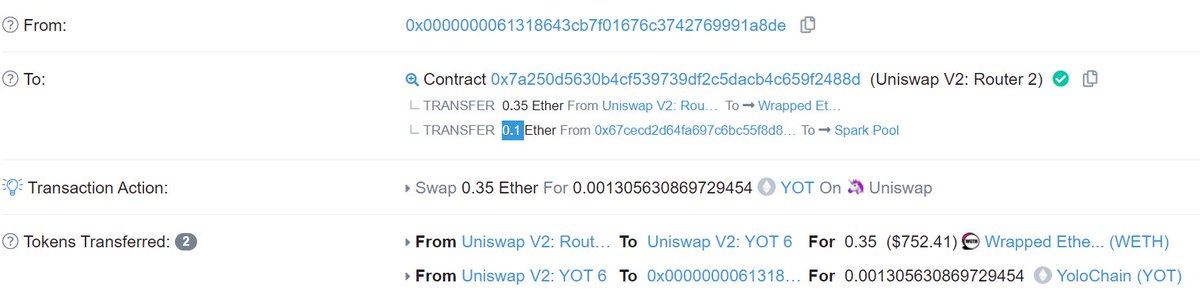
Here& #39;s a screenshot of a random arb that does this, note the 0 gas price & 0.075 ETH transfer to Spark Pool
Here& #39;s a screenshot of a random arb that does this, note the 0 gas price & 0.075 ETH transfer to Spark Pool
Miners will receive bundles of transaction from users and include the bundle that pays them the most
Users love this because they only pay for transactions that are included and they can determine the fee that they are going to pay
Users love this because they only pay for transactions that are included and they can determine the fee that they are going to pay
Note the
It& #39;s important that payment goes to the miner on the sell transaction!
That should only happen after the bot has secured profit from selling the tokens bought in their frontrun
If that sell fails then there is no payment to the miner, and thus their bundle shouldn& #39;t be included
That should only happen after the bot has secured profit from selling the tokens bought in their frontrun
If that sell fails then there is no payment to the miner, and thus their bundle shouldn& #39;t be included
Last thing and we& #39;ll get to the fun part, I promise.
To be even more secure, bots will simulate their transactions on local infrastructure. Bots won& #39;t send transactions unless the simulation goes well.
(Flashbots also offers a tool to make that easy to do as well)
To be even more secure, bots will simulate their transactions on local infrastructure. Bots won& #39;t send transactions unless the simulation goes well.
(Flashbots also offers a tool to make that easy to do as well)
. @NathanWorsley_ inspired an army to try to bait  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots w/ bad ERC20s after publishing his article on Salmonella
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots w/ bad ERC20s after publishing his article on Salmonella
In short Salmonella is a token that transfers less if you& #39;re not the owner, so https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots way overpaid and got REKT for 100 ETH https://github.com/Defi-Cartel/salmonella">https://github.com/Defi-Cart...
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots way overpaid and got REKT for 100 ETH https://github.com/Defi-Cartel/salmonella">https://github.com/Defi-Cart...
In short Salmonella is a token that transfers less if you& #39;re not the owner, so
Paying transaction fees only on the sell transaction of a  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> should defend against this. If you don& #39;t make an ETH profit, then you won& #39;t pay!
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> should defend against this. If you don& #39;t make an ETH profit, then you won& #39;t pay!
AND https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots simulate to see if they get rekt before it happens
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots simulate to see if they get rekt before it happens
But two clever people found weaknesses among all of these defenses
AND
But two clever people found weaknesses among all of these defenses
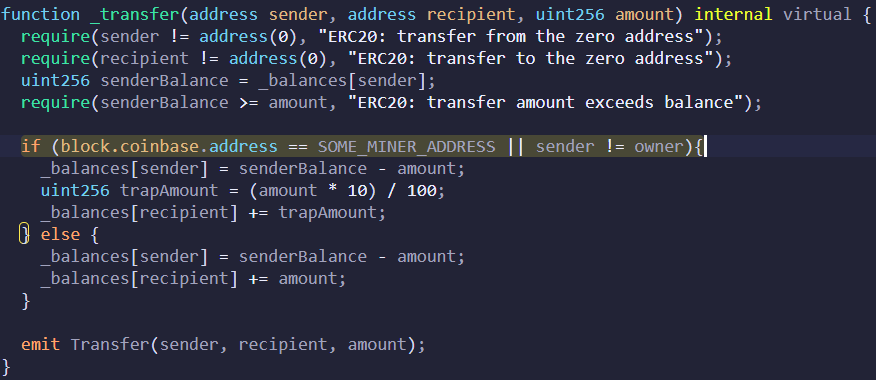
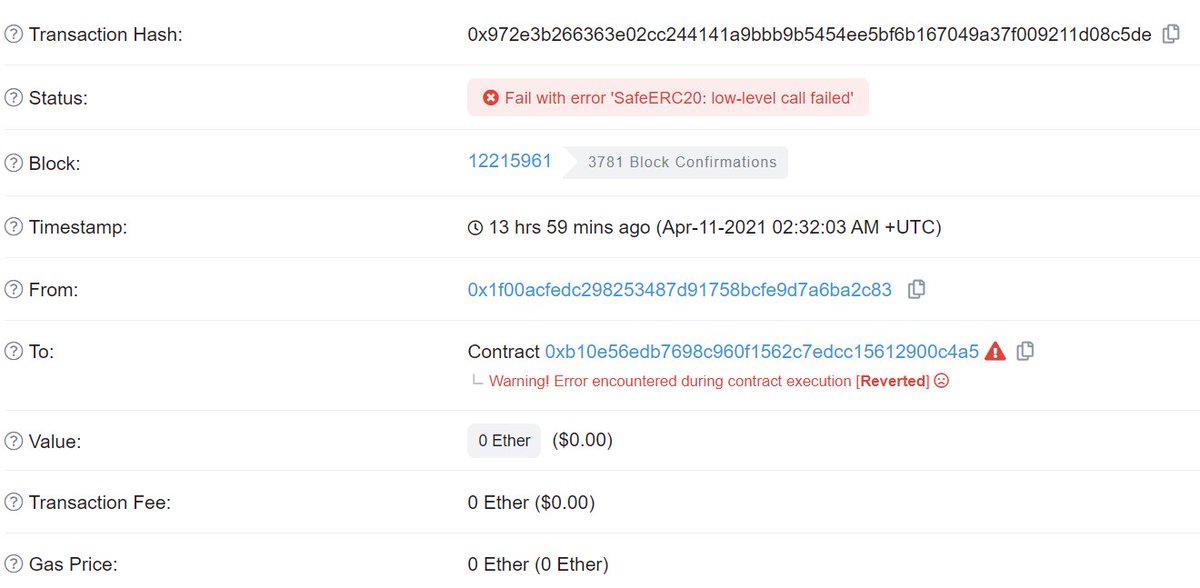
The 1st defense to break was the simulation
That was done w/ an ERC20 transfer function that checked to see if the block was a mined by Flashbots& #39; miners, & if so it transfers way less out. The code is my pseudo code btw
Local simulations will look fine but in prod https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">s get rekt
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">s get rekt
That was done w/ an ERC20 transfer function that checked to see if the block was a mined by Flashbots& #39; miners, & if so it transfers way less out. The code is my pseudo code btw
Local simulations will look fine but in prod
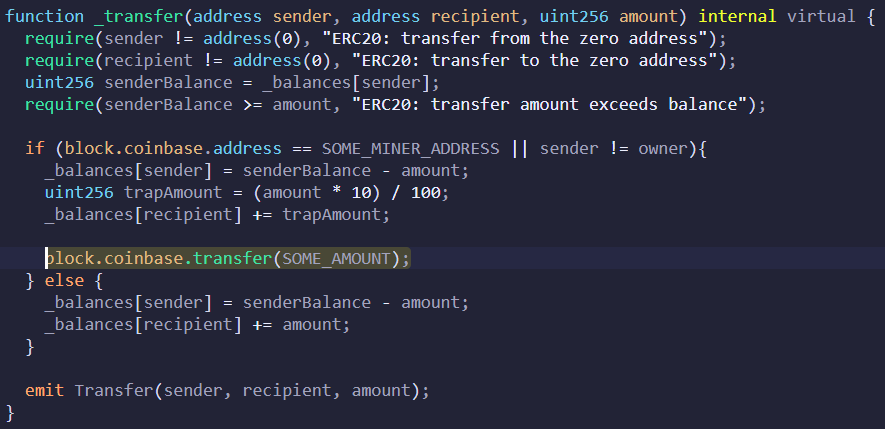
The 2nd line of defense was the payment only on a sell transaction
Again: https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profit
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profit
That was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)
So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!
Again:
That was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)
So even with the
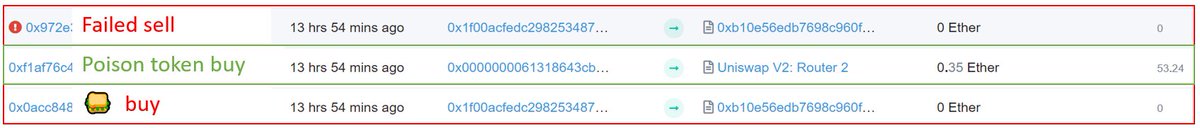
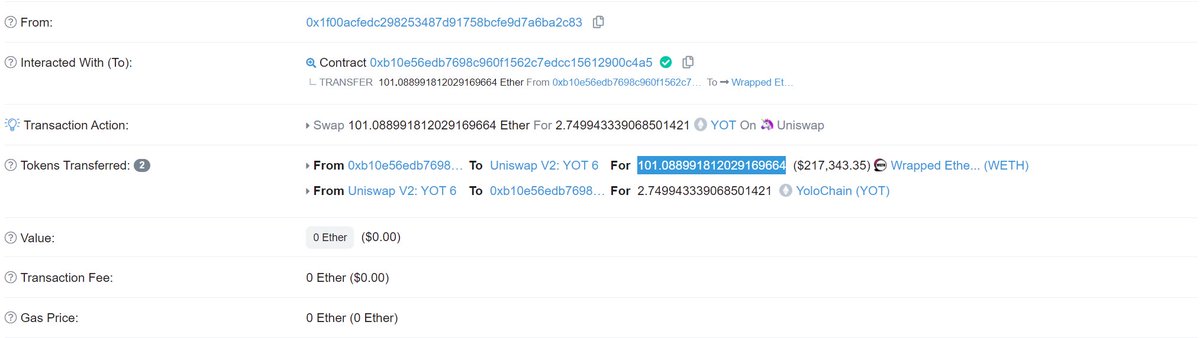
Here& #39;s what actually happened in the wild
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous token
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous token
Poisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the miner
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token
Poisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the miner
Because the  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot submitted these three transactions in a bundle all three were included: the successful buy, the bait, and the failed sell.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot submitted these three transactions in a bundle all three were included: the successful buy, the bait, and the failed sell.
The poisonous ERC20& #39;s payment via the custom transfer was what incentivized a miner to include it!
The poisonous ERC20& #39;s payment via the custom transfer was what incentivized a miner to include it!
The first person to do this made about 100 ETH, I think. You can see the poisoned ERC20 Uniswap transactions here:
https://etherscan.io/token/0xe253a1f7d5818022661bfbd2cbe043b642b4eff9?a=0x01f8d5a4862d51d2cf0cf52ac900a4d60adaeee6
One">https://etherscan.io/token/0xe... of their victims was one the most successful Flashbots bot operators, and they immediately sprung into action
https://etherscan.io/token/0xe253a1f7d5818022661bfbd2cbe043b642b4eff9?a=0x01f8d5a4862d51d2cf0cf52ac900a4d60adaeee6
One">https://etherscan.io/token/0xe... of their victims was one the most successful Flashbots bot operators, and they immediately sprung into action
In a short period of time the victim turned into an apex predator
They launching a similar but slightly different ERC20 ("YoloChain" https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen">), and ended up successfully baiting many more sandwichers
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen">), and ended up successfully baiting many more sandwichers
They made 300 ETH doing so! https://etherscan.io/token/0xc02aaa39b223fe8d0a0e5c4f27ead9083c756cc2?a=0x2dce49cd5bcc94df854922e296108b5f78ad1560">https://etherscan.io/token/0xc...
They launching a similar but slightly different ERC20 ("YoloChain"
They made 300 ETH doing so! https://etherscan.io/token/0xc02aaa39b223fe8d0a0e5c4f27ead9083c756cc2?a=0x2dce49cd5bcc94df854922e296108b5f78ad1560">https://etherscan.io/token/0xc...
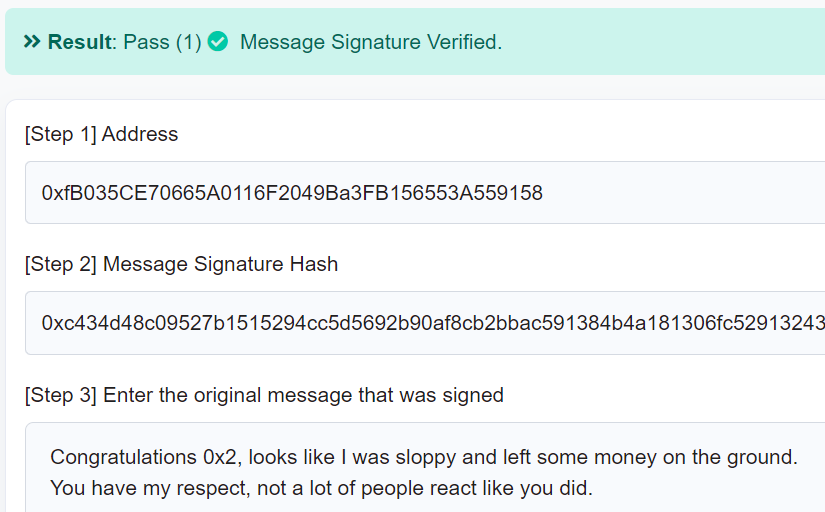
The owner of the first poisonous token noticed their victim was the latest predator on the block and they dropped a cryptographically signed note of respect in the Flashbots discord
I loved this.
https://etherscan.io/verifySig/2503 ">https://etherscan.io/verifySig...
I loved this.
https://etherscan.io/verifySig/2503 ">https://etherscan.io/verifySig...
In total I counted ~400 ETH as the bounty for our two enterprising bot baiters, but there might have been more poisonous tokens I didn& #39;t catch.
For now the carnage is over.
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot operators have noticed and updated their bots accordingly. A few were totally drained.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot operators have noticed and updated their bots accordingly. A few were totally drained.
For now the carnage is over.
In the aftermath one bot operator ominously pointed out that  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">-ing is never safe & said they& #39;d leak the alpha once it was used.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">-ing is never safe & said they& #39;d leak the alpha once it was used.
The dark forest is a dangerous place.
As last night shows even those who think they are predators might turn out to be prey.
The dark forest is a dangerous place.
As last night shows even those who think they are predators might turn out to be prey.
@hasufl @fifikobayashi @Fiskantes @twobitidiot @defiprime @bneiluj check out the insane sandwich bot baiting that took place last night above  https://abs.twimg.com/emoji/v2/... draggable="false" alt="👆🏻" title="Rückhand Zeigefinger nach oben (heller Hautton)" aria-label="Emoji: Rückhand Zeigefinger nach oben (heller Hautton)">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👆🏻" title="Rückhand Zeigefinger nach oben (heller Hautton)" aria-label="Emoji: Rückhand Zeigefinger nach oben (heller Hautton)">

 Read on Twitter
Read on Twitter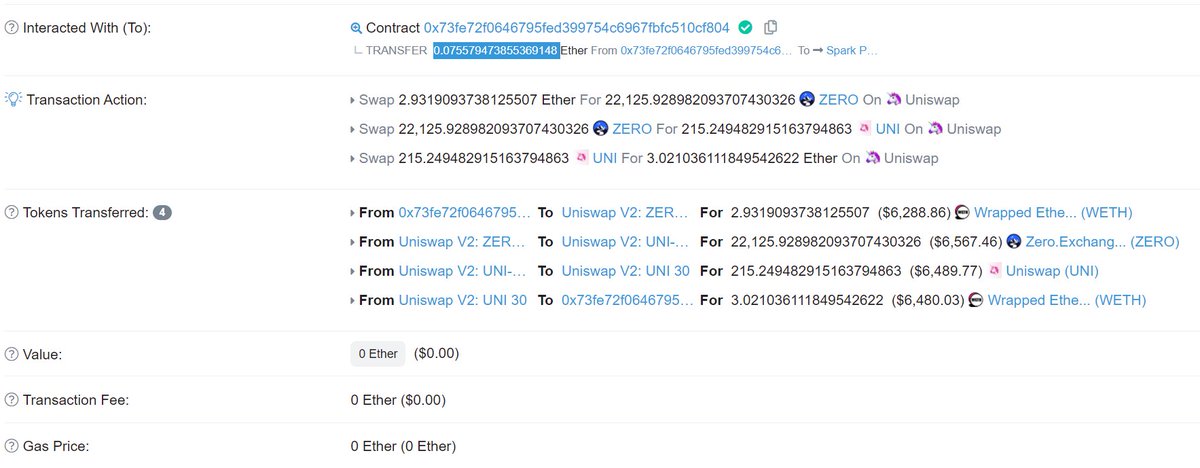
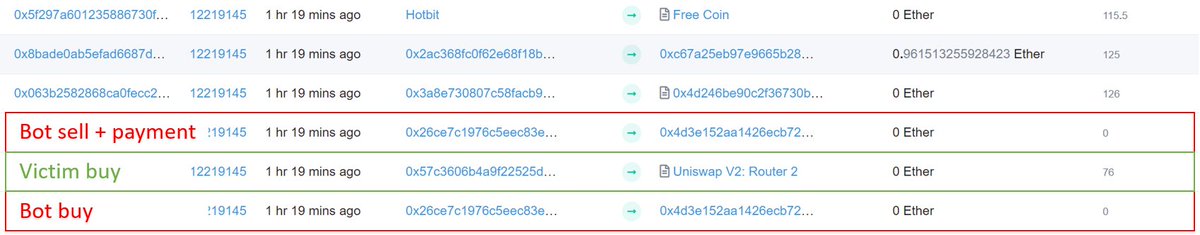 bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner" title="https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner">
bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner" title="https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner">
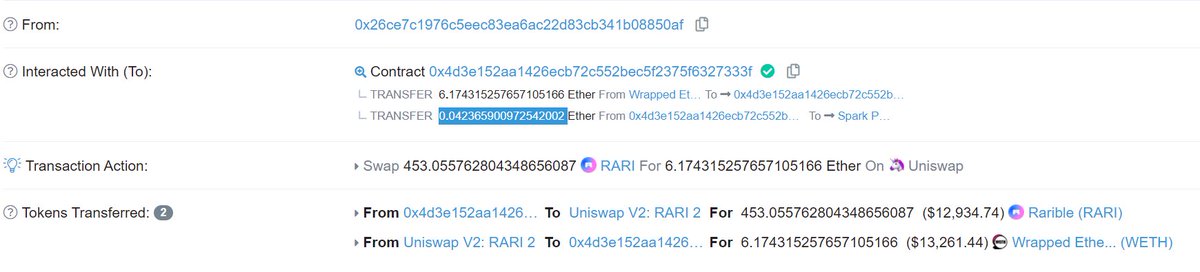 bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner" title="https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner">
bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner" title="https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">bots watch the mempool for users buying on DEXes and https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> them: running the price up before the victim buys and dumping after for a profit. Those 3 txs (buy, victim tx, sell) make up a bundleNote the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> sell tx contains the smart contract payment to the miner">
 s get rekt" title="The 1st defense to break was the simulationThat was done w/ an ERC20 transfer function that checked to see if the block was a mined by Flashbots& #39; miners, & if so it transfers way less out. The code is my pseudo code btwLocal simulations will look fine but in prod https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">s get rekt" class="img-responsive" style="max-width:100%;"/>
s get rekt" title="The 1st defense to break was the simulationThat was done w/ an ERC20 transfer function that checked to see if the block was a mined by Flashbots& #39; miners, & if so it transfers way less out. The code is my pseudo code btwLocal simulations will look fine but in prod https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich">s get rekt" class="img-responsive" style="max-width:100%;"/>
 bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!" title="The 2nd line of defense was the payment only on a sell transactionAgain: https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!">
bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!" title="The 2nd line of defense was the payment only on a sell transactionAgain: https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!">
 bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!" title="The 2nd line of defense was the payment only on a sell transactionAgain: https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!">
bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!" title="The 2nd line of defense was the payment only on a sell transactionAgain: https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bots make miner payment conditional on profitThat was broke by making the *ERC20 token* pay the miner (again my pseudo-code here)So even with the https://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot sell failing, the miner would still get paid!">
 bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
 bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
 bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
 bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">
bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token" title="Here& #39;s what actually happened in the wildhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot gets baited and buys 100 ETH of the poisonous tokenPoisonous token owner& #39;s bait triggers custom transfer function, which pays 0.1 ETH to the minerhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🥪" title="Sandwich" aria-label="Emoji: Sandwich"> bot& #39;s sell doesn& #39;t work because of the poisonous token">