1/ Why does Avalanche $AVAX stand above the rest?
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Security
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Security
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Performance
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Performance
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Decentralisation
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Decentralisation
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Customisability
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Customisability
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Tokenomics
https://abs.twimg.com/emoji/v2/... draggable="false" alt="✅" title="Fettes weißes Häkchen" aria-label="Emoji: Fettes weißes Häkchen">Tokenomics
First, I will cover Security and how Avalanche compares to other platforms and then separate threads for the others later. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="Thread" aria-label="Emoji: Thread">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="Thread" aria-label="Emoji: Thread"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
First, I will cover Security and how Avalanche compares to other platforms and then separate threads for the others later.
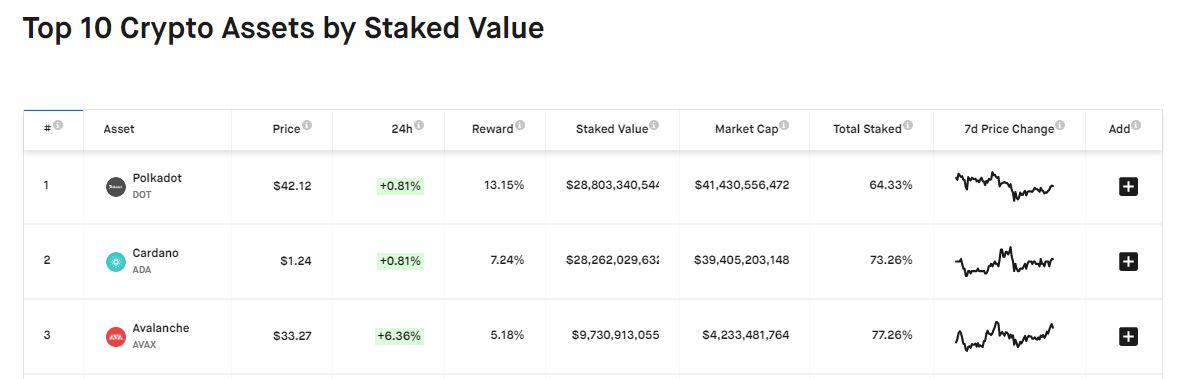
2/ Sybil Resistance - Avalanche uses Proof of Stake instead of Proof of Work, with nearly $10 Billion of staked value securing the network with an impressive 77.26% of the entire supply being staked, just 6 months after mainnet. It is currently the 3rd largest in staked value.
3/ Proof of Stake is not only more secure than Proof of Work as evident by the number of 51% attacks seen against POW Chains due to the ease of renting hash power compared to acquiring stake, but it& #39;s also requires far less energy consumption.
4/ Sharding - For platforms that utilise sharding, validators and staked value are split between the number of shards. If you have 100 shards, then that $10 billion securing the entire network is now divided by 100 leaving just $100 million securing each shard.
5/ Whereas if you assumed up to 1/3 of the stake can be malicious in the entire network, as validators are now randomly split up and assigned to each shard, it& #39;s now possible that an attacker can control more than 1/3 of the stake in a shard, ...
6/ whilst owning significantly less than 1/3 of the stake of the entire network.
The more shards you have also the smaller the number of validators assigned to each shard out of the total validator set securing the network as well.
The more shards you have also the smaller the number of validators assigned to each shard out of the total validator set securing the network as well.
7/ This is the case for heterogenous sharding platforms such as Polkadot where the total number of validators in the relay chain is limited which are then split up so that as little as 14 validators are validating each of the parachains.
Having skin in the game is important to..
Having skin in the game is important to..
8/ deter attacks, but with the combination of a limited number of validators, 0% commission and no min own stake required, then this can lead to potentially dangerous scenarios such as Zug Capital controlling 10% of stake in Polkadot when they themselves own less than $1k of DOT
9/ With Avalanche, all the chains including in the primary network are secured by the full staked value of the network. In additional Avalanche consensus is inclusive and not restricted to a small number of validators like other blockchains and can scale to millions of validators
10/ all securing the network and participating in consensus for every transaction.
Committee Sizes - Other platforms use a very small committee size and to randomly select a sample of the entire validator set, which faces similar issues where it& #39;s possible an attacker can
Committee Sizes - Other platforms use a very small committee size and to randomly select a sample of the entire validator set, which faces similar issues where it& #39;s possible an attacker can
11/ control the majority of the committee size, but actually own significantly less % of the total stake of the entire network.
As well as now relying on just a small number of nodes to validate the transaction compared to reaching consensus across the entire network.
As well as now relying on just a small number of nodes to validate the transaction compared to reaching consensus across the entire network.
12/ Transaction Security - Platforms such as Cardano use a consensus following the longest chain rule, where a leader is chosen that can add a block to the chain without first reaching consensus with other validators on the validity of the block.
13/ Subsequent leaders can then choose to either build on top of the previous block (confirming they believe it& #39;s valid) or choose to fork the network. Transactions therefore start with very weak security backing which increases with the more subsequent blocks that get added.
14/ As leaders are randomly selected based off the stake their own it& #39;s possible that an attacker controlling 10% of the network could be selected to produce 10 blocks in a row and so you have to wait a long time to be sure they are secure and valid.
15/ With 10% malicious nodes, Cardano calculated 15 blocks are required to achieve the same level of security as Bitcoin& #39;s six block rule, which means finality of around 5 minutes. If a larger % is controlled by an attacker, then this increases significantly further.
16/ Other blockchains such as Solana also use a leader and follow longest chain rule, where they can add blocks to the blockchain without first reaching consensus on their validity. So even though it has 400ms block times, they can be reverted and offer weak security initially.
17/ With Finality on Solana lasting around 13 seconds.
With Avalanche the entire network reaches consensus and transactions are irreversible and final within less than a second offering immediate transaction security of the entire network.
With Avalanche the entire network reaches consensus and transactions are irreversible and final within less than a second offering immediate transaction security of the entire network.
18/ Layer 2 solutions such as Optimistic Rollups provide their own security risks. All tokens within a rollup are locked into a smart contract. A smart contract bug / hack could result in those funds getting stolen or frozen.
19/Transactions are added optimistically in batches without having every Ethereum node run the compute and calculate the state and reach consensus, and instead relies on fraud proofs where verifiers run the computation and verify the state output afterwards (needing up to a week)
20/ If the sequencer is malicious and posts an incorrect resulting state root / tries to steal users funds, then as long as there is one verifier who has checked the validity of the transaction they can post a fraud proof and the batch is rolled back and the Sequencer is slashed
21/ Running a verifier costs money checking all the transactions, the higher the number of transactions added to the chain, the more resources they need to check them all = more costs incurred. You may go for long periods without finding any fraud and thus receive no reward
22/ This could then cause verifiers to drop out / reducing the security of the chain and making it more likely fraud would occur. This is a similar issue with fishermen with polkadot as mentioned in this article https://cryptoseq.medium.com/polkadot-an-early-in-depth-analysis-part-three-limitations-and-issues-d8b0a795a3e">https://cryptoseq.medium.com/polkadot-...
23/ Even if a fraud proof is posted, a 51% on Ethereum main chain can censor it from being included on chain for the 7 days and thus able to steal the funds. Therefore, the amount of value locked in the rollup will also depend on how much it costs to 51% attack for 7 days.
24/Likewise, if there is a bug in the protocol used to detect fraud (and instead reports them incorrectly as being fine) then funds can also be lost as the transactions would go undetected. The more value secured in the smart contract the more attractive it becomes to an attacker
25/ Avalanche is not reliant on hoping someone checks every transaction afterwards, the entire network checks the validity of the transaction as part of consensus as it& #39;s added to the chain, with sub second finality that can scale to millions of nodes offering incredible security

 Read on Twitter
Read on Twitter