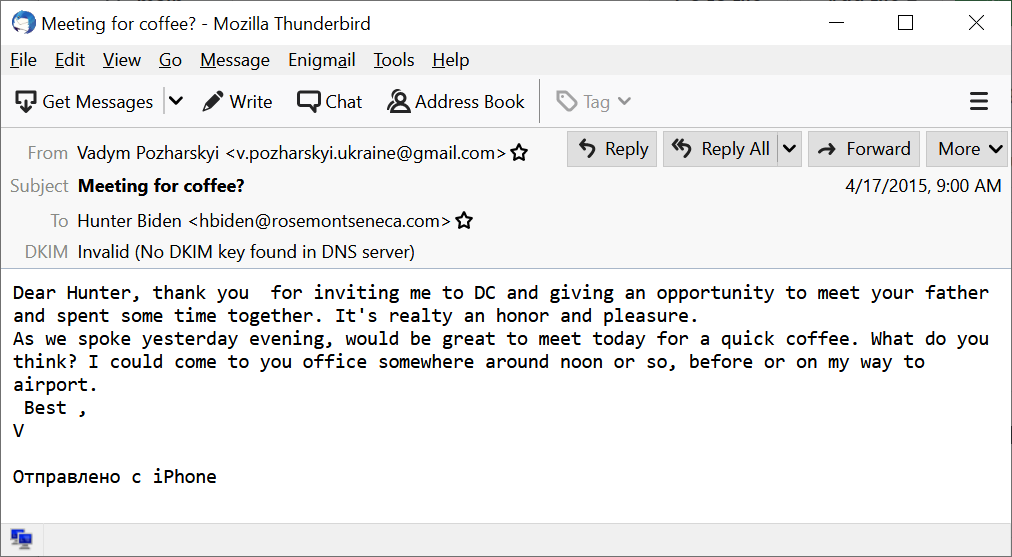
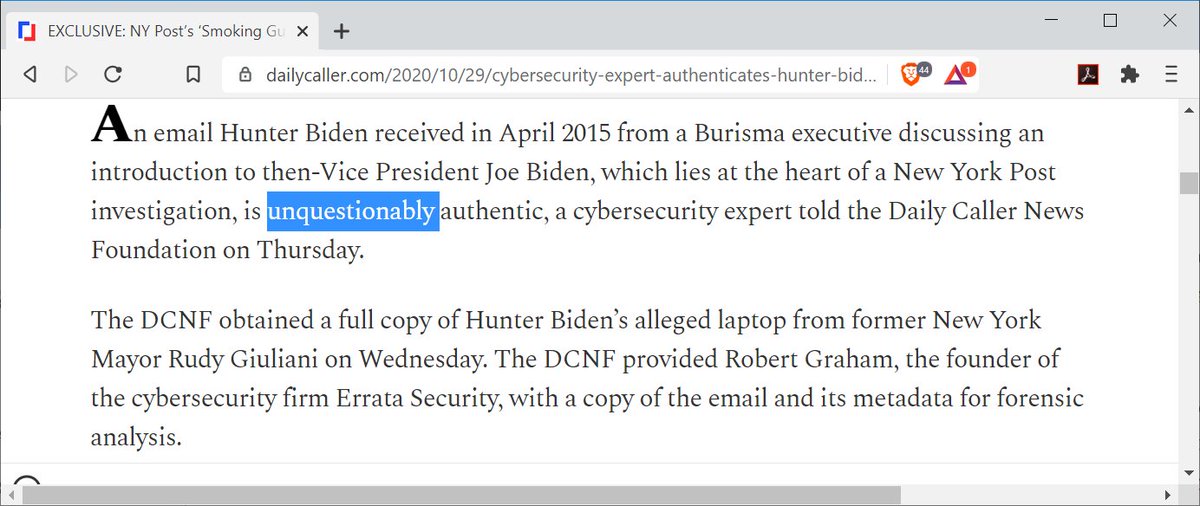
So as I blogged before, the emails contained DKIM information, which the original reporters could and should have verified. So I eventually got a copy of the email and run DKIM verification on it. It passed: https://twitter.com/DailyCaller/status/1322005711837155328">https://twitter.com/DailyCall...
We can still have our fun arguments about whether it& #39;s taken out of context, or the exact provenance (harddrive vs. hacking into his account). But we do know the email is valid -- through the power of crypto!!
When you attempt to use your favorite DKIM checker (such as Thunderbird with DKIM Verifier add-on), it& #39;ll fail at first. That& #39;s because the key is 6 years old and no longer provided by Gmail& #39;s DNS servers.
So you search the Internet for "TXT 20120113._domainkey.gmail.com" and you& #39;ll find lots of answers what the key was 6 years ago: https://github.com/robertdavidgraham/hunter-dkim/blob/main/20120113._domainkey.gmail.com.-TXT.txt">https://github.com/robertdav...
We do have the little problem that we are getting the signing key not from Gmail, but from other sources on the Internet. But there are so many MANY sources all in agreement.
I created a Github project so that YOU TOO can do the verification. It would be awesome if you were to prove me wrong, that I& #39;ve made some sort of mistake. https://github.com/robertdavidgraham/hunter-dkim">https://github.com/robertdav...

 Read on Twitter
Read on Twitter