ok gang! i know @ZephrFish has made some awesome content on CVE-2020-1472 but i think its time to get some more focus on this shizzle! to the @pwnDefend LAB! *plays batman sounds*
lab hypervisors go bRRRRRRRRRRRRRRR (if u know what i& #39;m talking about patch ur shit people)
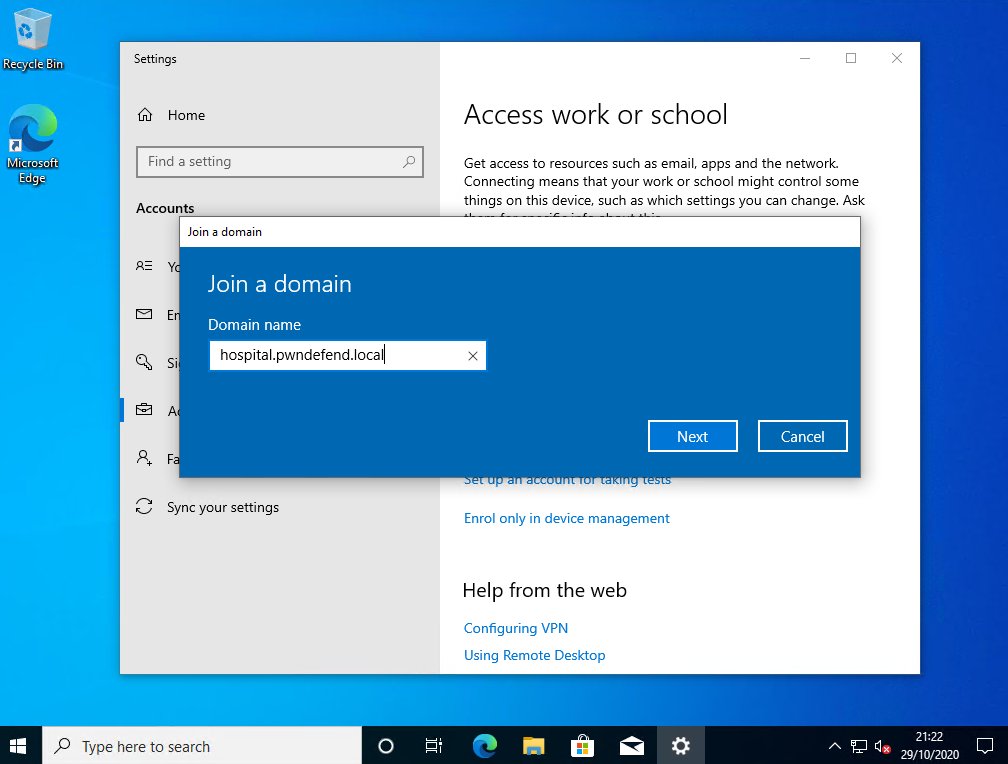
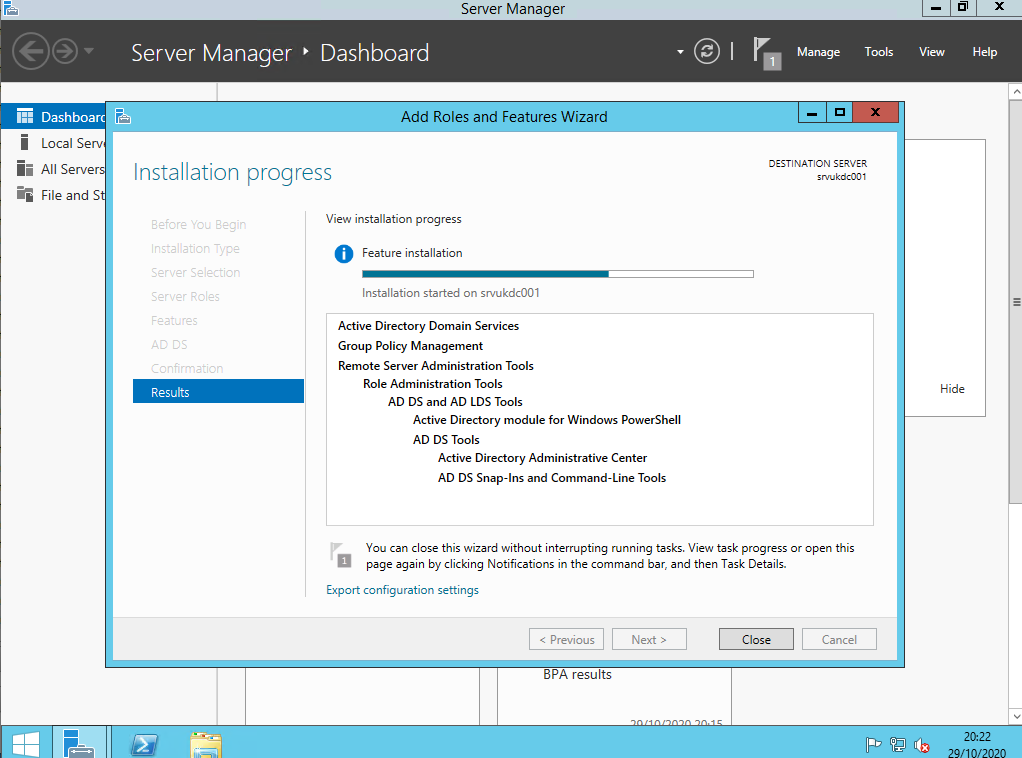
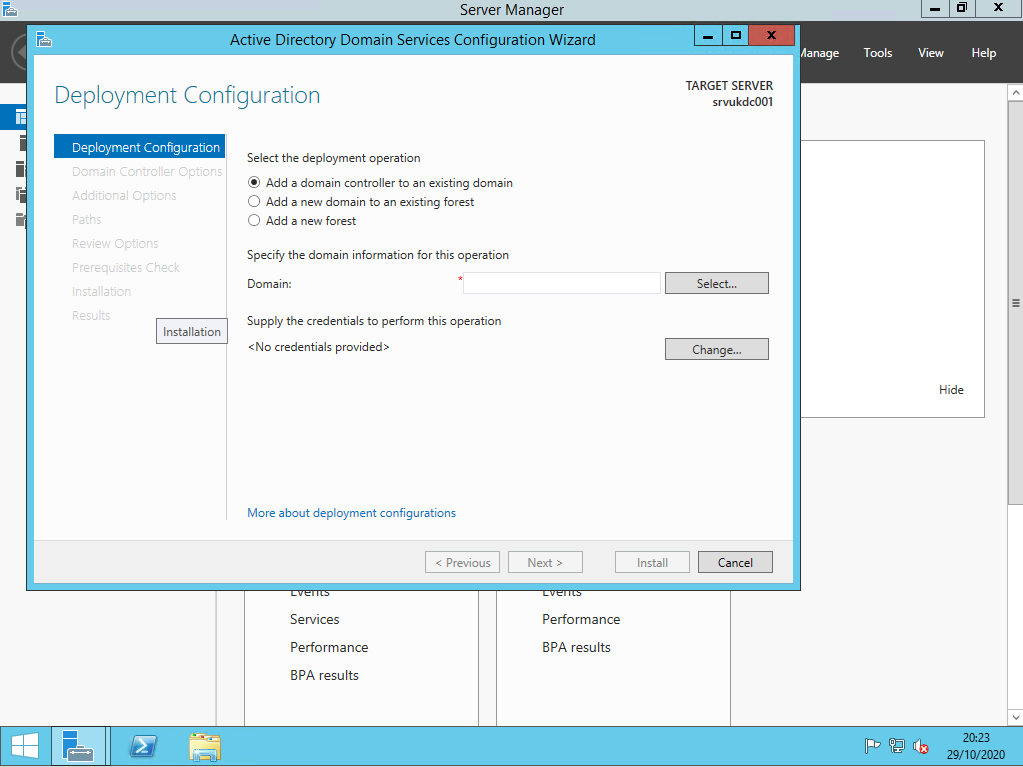
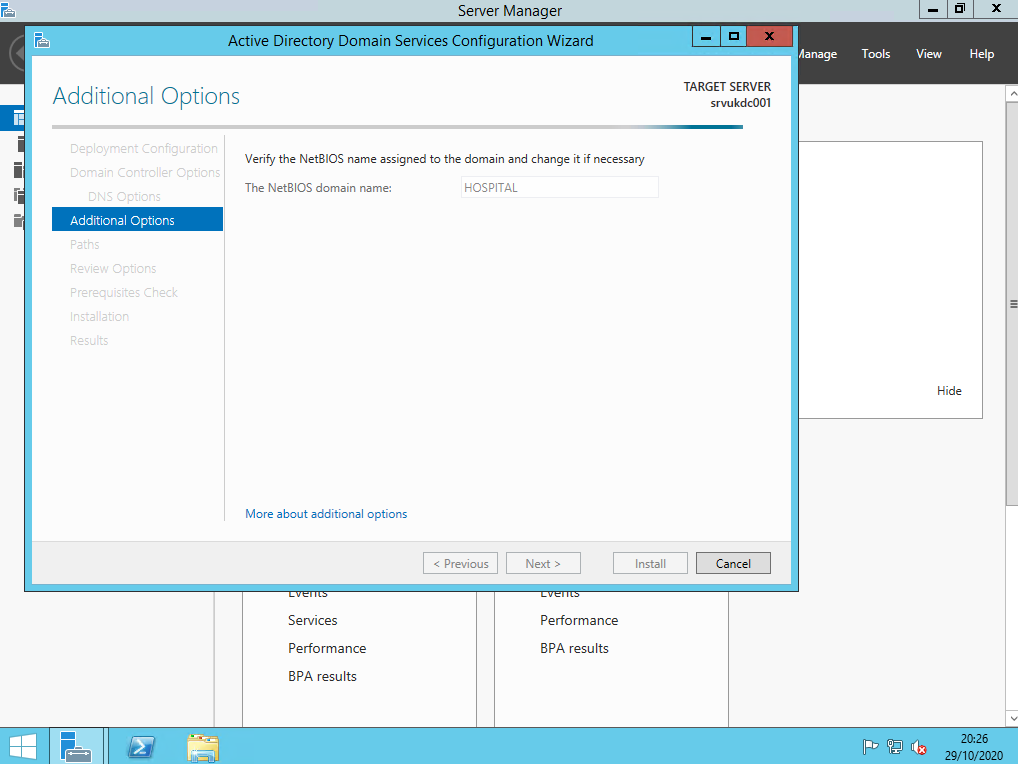
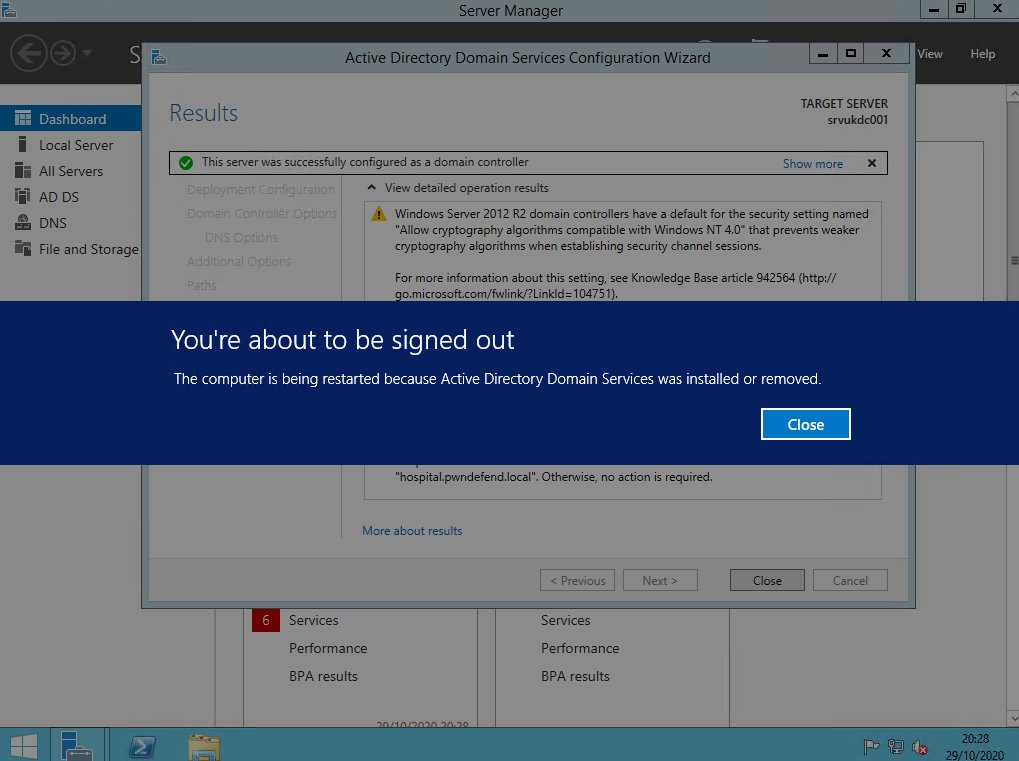
ok so we& #39;re are installing ADDS and we are going to promote this vm to be a domain controller!
ok so here& #39;s our hospital lab domain controller :(
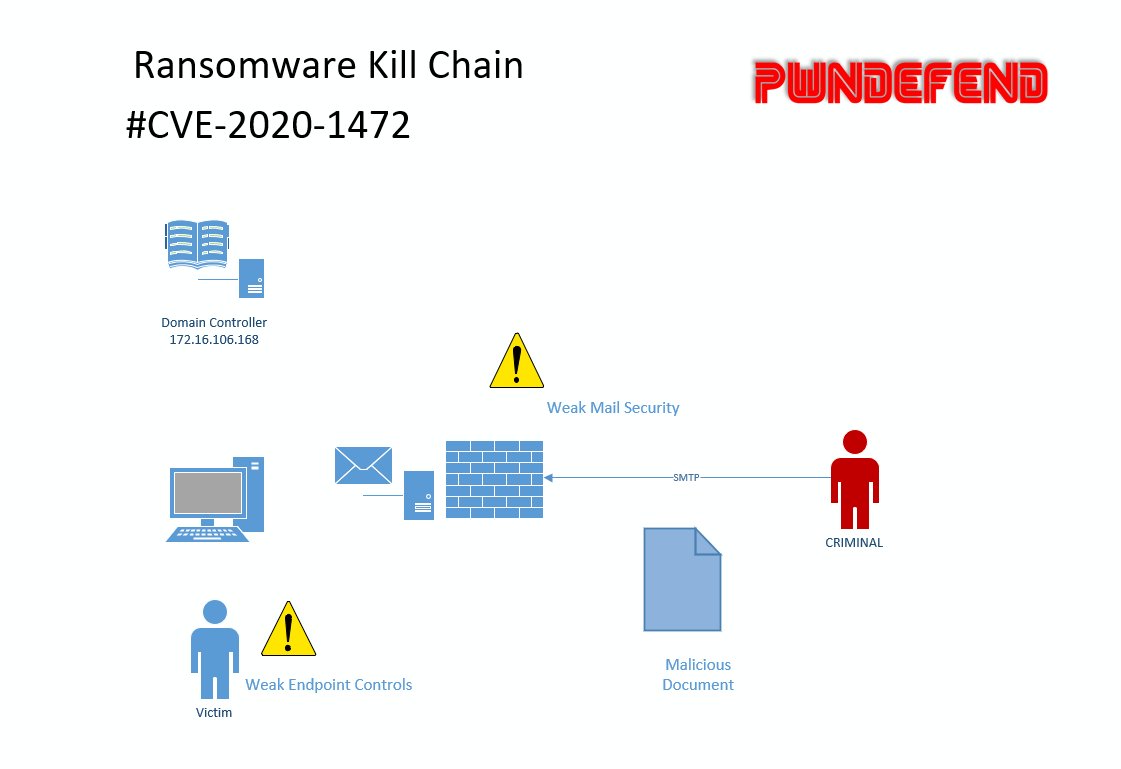
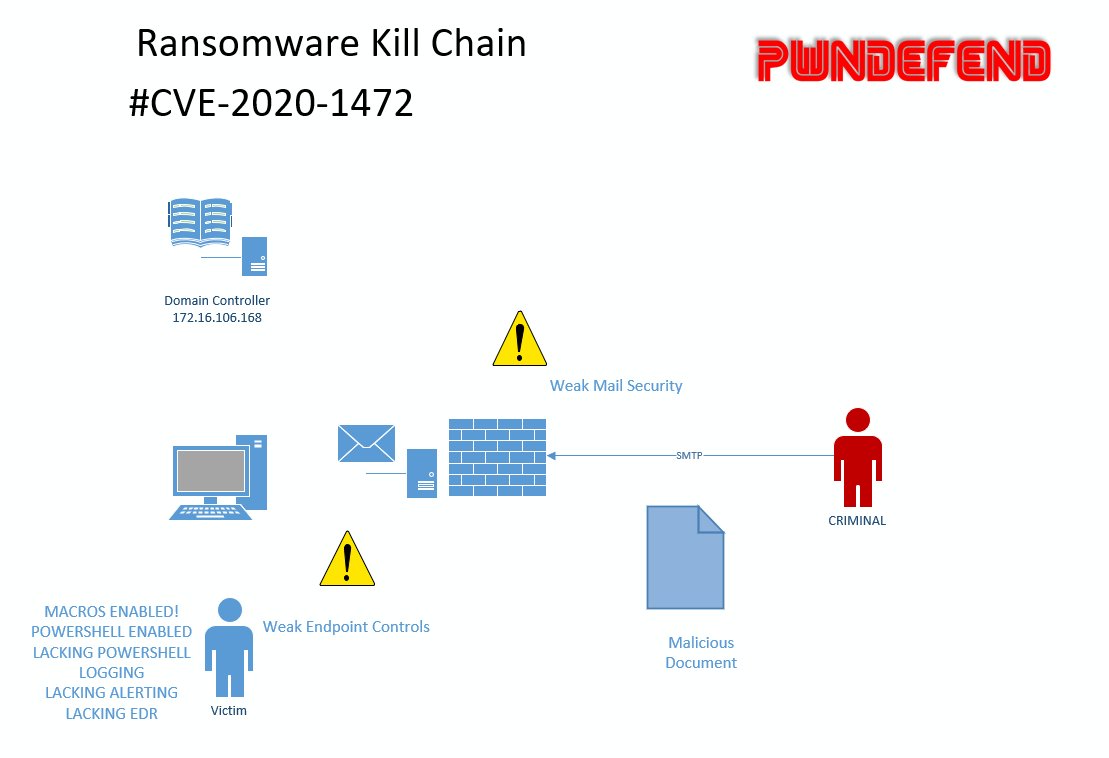
we are gonna protect the fuck out of this place but we need to show how to detect the vuln first! #FuckRansomware
Nothing more Kermie Hax likes than protecting all the things! He hates crims who hit hospitals!  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐸" title="Froschgesicht" aria-label="Emoji: Froschgesicht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐸" title="Froschgesicht" aria-label="Emoji: Froschgesicht"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">
ok kettle on, we are just gonna deploy a windows 10 vm as a sysadmin machine. Then we are going to get the AMAZING tool PINGCASTLE so we can discover all the things!
whilst we sort that out let& #39;s talk about intial access quickly! now you all know i love/hate RDP initial access vectors! but for a change I& #39;m going to talk about phishing! its about 50/50 these days on ransomware vector RDP vs PHISH!
now we& #39;ve already got a range of fuckup, our SPF isn& #39;t configured, DMARC missing and our mail filters/security is weak (not to say a nicely encrypted zip won& #39;t get us in etc.)
ok we& #39;ve got a windows 10 enterprise latest build deploying.
now looking at RYUK IOCs etc. your gonna see lure& #39;s with PDFs possible hosted on google docs. so again more defence prep with awareness training (but that& #39;s no silver bullet)
ok i& #39;m nearly ready for the main event :)
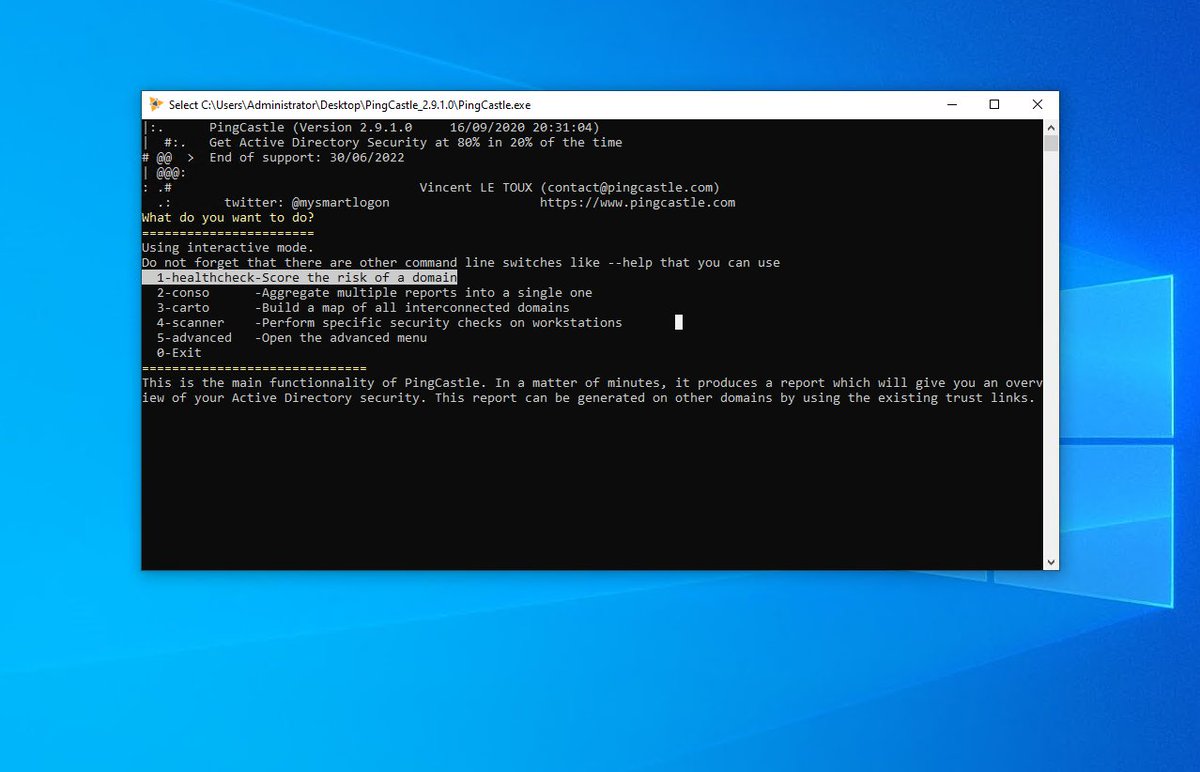
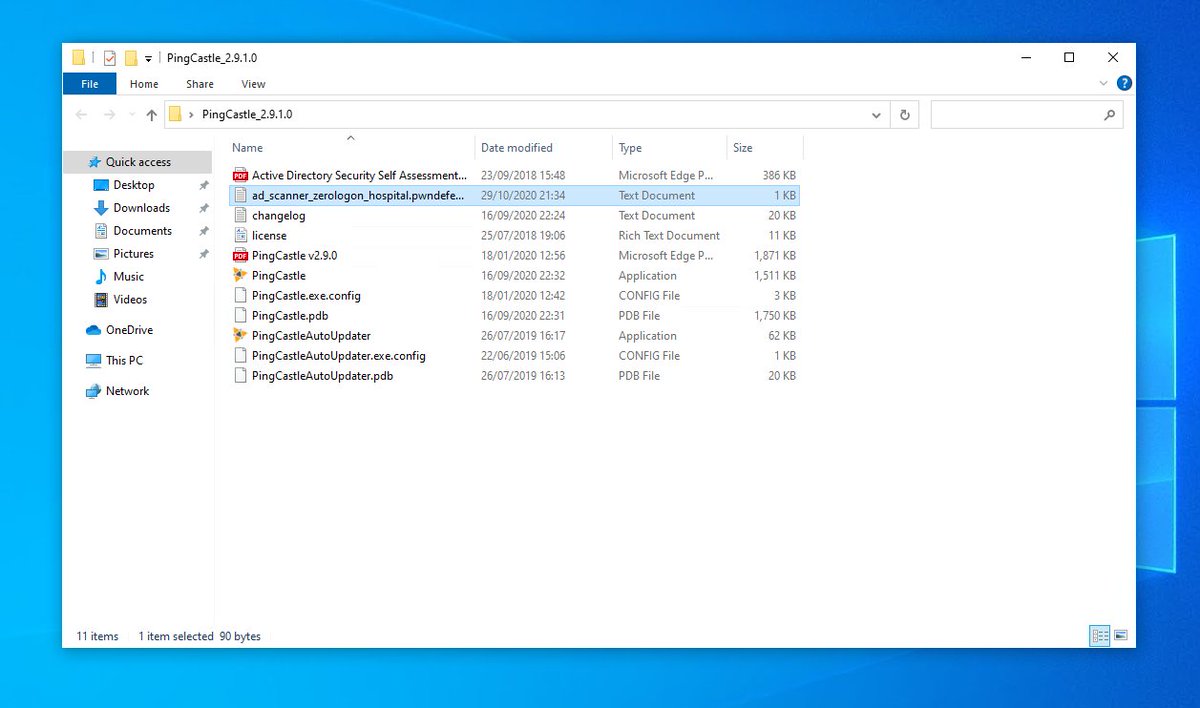
ok now this is where the magic from @mysmartlogon comes in! PINGCASTLE is fucking amazing! if you havne& #39;t used it go to https://www.pingcastle.com/ ">https://www.pingcastle.com/">... and download it! it& #39;s awesome!
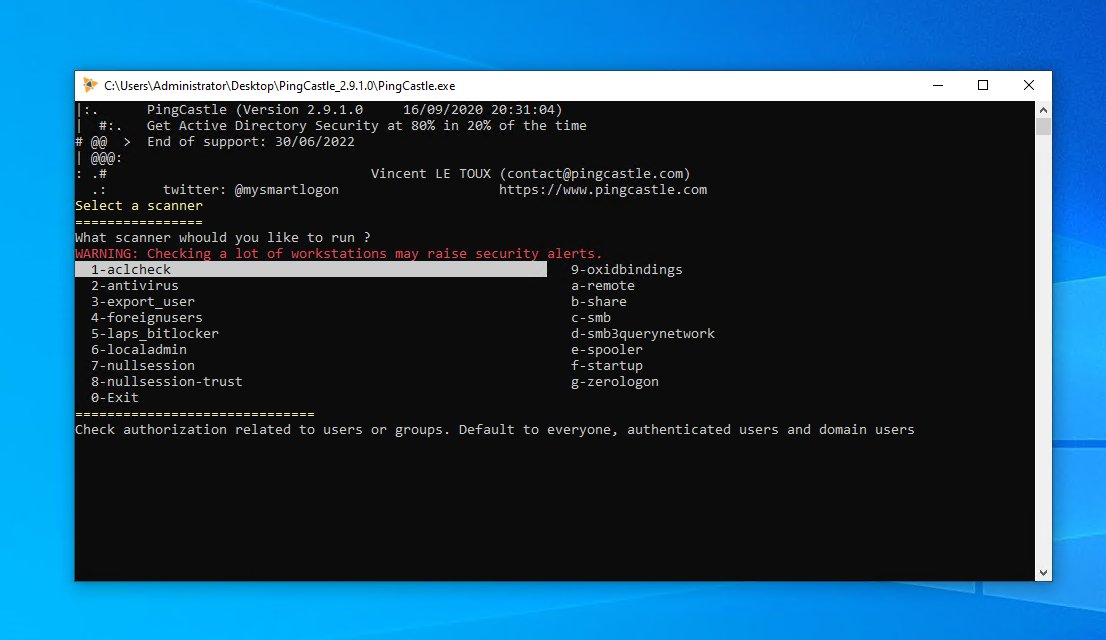
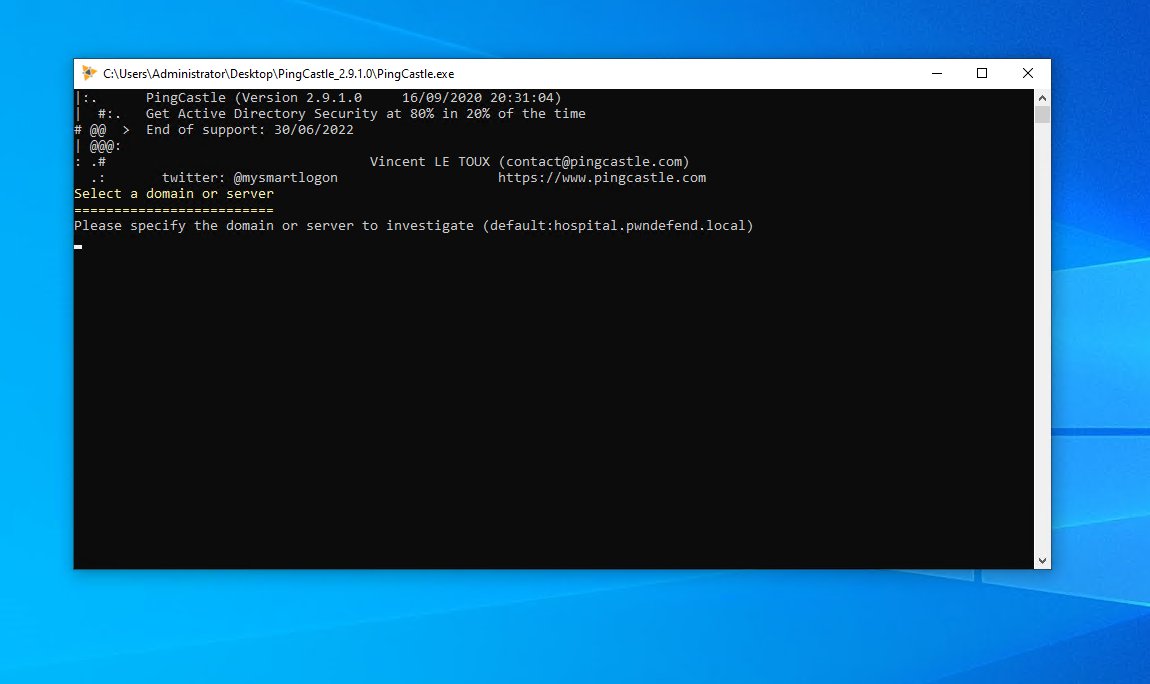
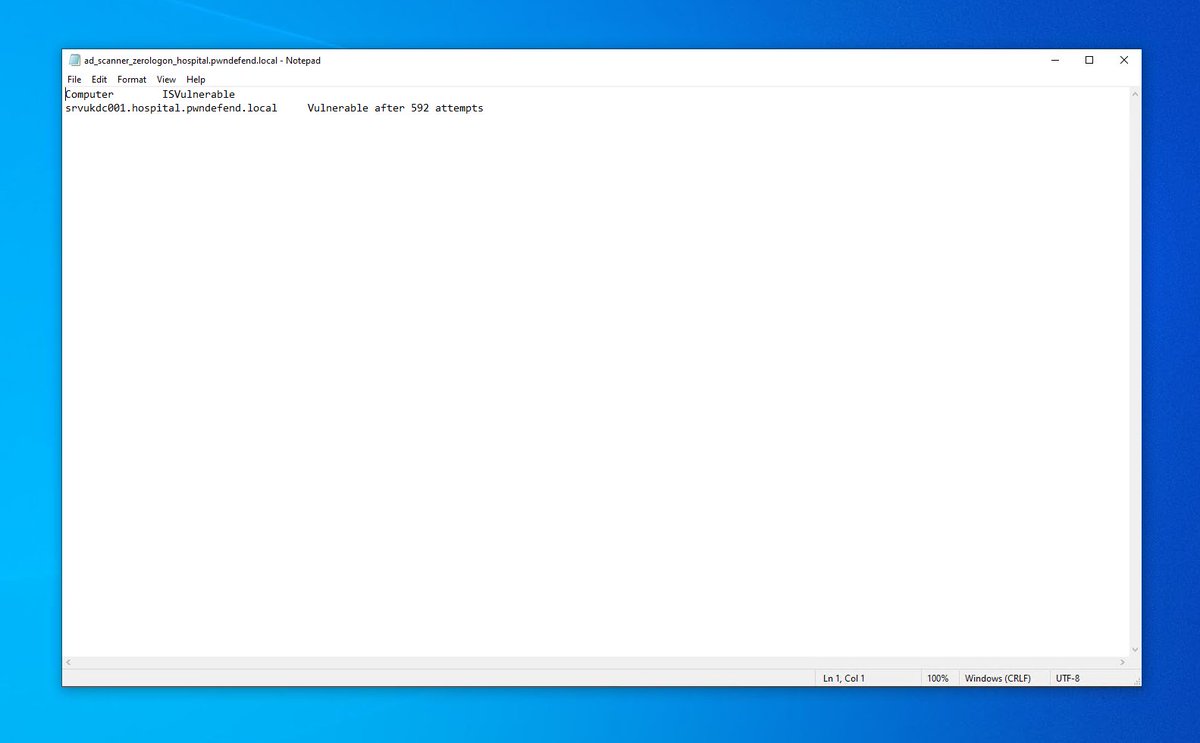
so from out domain joined workstation (might work non domain joined as well but not got time to check) we are going to run PINGCASTLE and on the main menu we can see OPTION 4 - Scanner
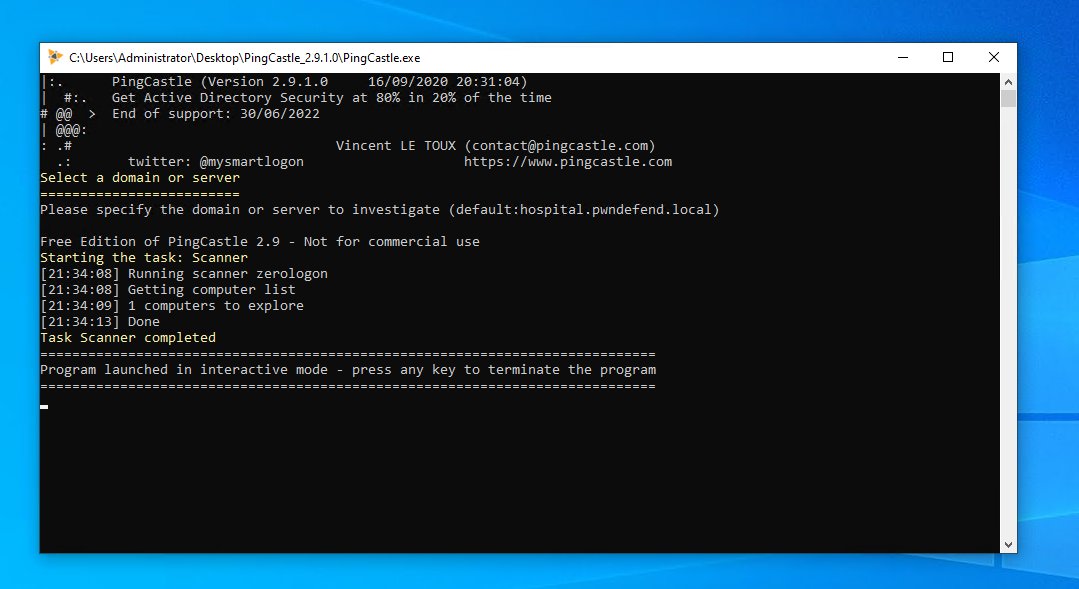
and pew pew! now remember this might be picked up by an IPS/IDS/HIDS or AV so only run this if you have AUTHORISATION.
So get your assess over to https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472">https://portal.msrc.microsoft.com/en-US/sec... and get the patches! remember you need to raise a change request/follow process but when i used to manage a large estate I would have phoned the responsible director and this would be getting rolled out fast as fuck (test first)
I can& #39;t stress this enough! I& #39;m going to do more on AD security and protecting against ransomware! hopefully @Shadow0pz are going to find time to film/steam some stuff! we can watch John pwn me in the lab then me go all blue and try stop his ass from breaching my servers :P

 Read on Twitter
Read on Twitter

 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">" title="Nothing more Kermie Hax likes than protecting all the things! He hates crims who hit hospitals! https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐸" title="Froschgesicht" aria-label="Emoji: Froschgesicht">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">" class="img-responsive" style="max-width:100%;"/>
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">" title="Nothing more Kermie Hax likes than protecting all the things! He hates crims who hit hospitals! https://abs.twimg.com/emoji/v2/... draggable="false" alt="🐸" title="Froschgesicht" aria-label="Emoji: Froschgesicht">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤬" title="Gesicht mit Symbolen über dem Mund" aria-label="Emoji: Gesicht mit Symbolen über dem Mund">" class="img-responsive" style="max-width:100%;"/>