I& #39;m excited to share the work of my student @bhangu_kaur, co-supervised with Aiman Hanna @GinaCodySchool:
"An Analysis of Security Vulnerabilities in Container Images for Scientific Data Analysis"
https://arxiv.org/abs/2010.13970
1/n">https://arxiv.org/abs/2010....
"An Analysis of Security Vulnerabilities in Container Images for Scientific Data Analysis"
https://arxiv.org/abs/2010.13970
1/n">https://arxiv.org/abs/2010....
Containers are great tools to run data analyses on HPC clusters, but they contain a lot of software that might be exploited to attack systems. We certainly don& #39;t want our containers to be entry points for bitcoin miners or data thieves!
2/n
2/n
This pre-print looks at security vulnerabilities present in container images available in @BIDSstandard apps and @BoutiquesTools, using 4 different vulnerability scanners: @vuls_en @anchore, Clair @containerlinux and @SingularityApp tools.
3/n
3/n
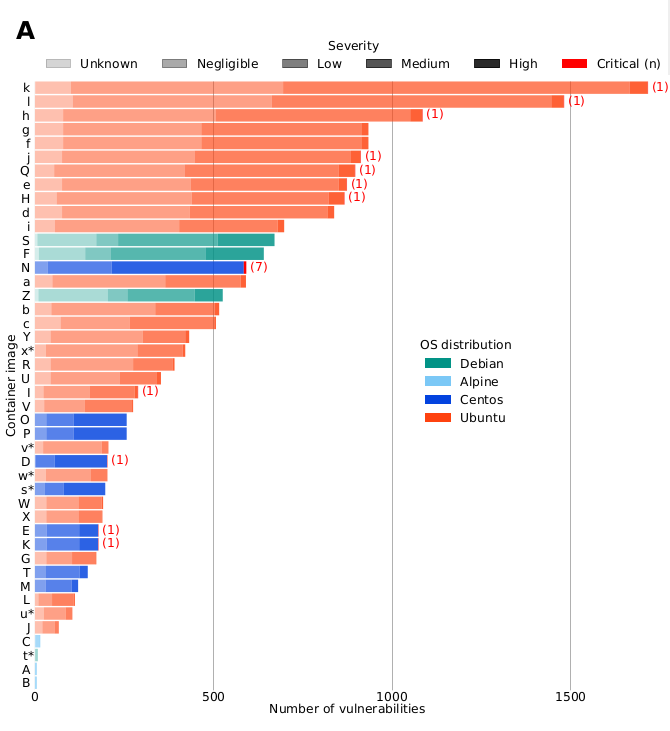
We found an average of 460 vulnerabilities per image, including many of high severity and a few of critical severity. That& #39;s a lot of possible security breaches!
4/n
4/n
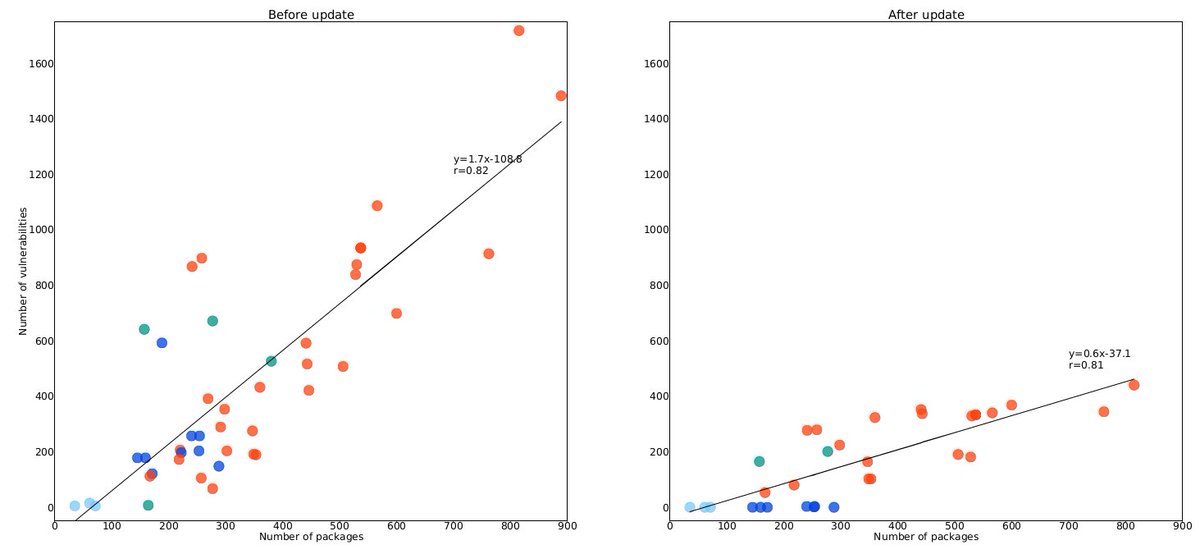
Removing unused packages is also quite useful. We used ReproZip to identify such packages, but it requires running actual analyses in the image. So not very convenient or scalable.
6/n
6/n
Surprisingly, different scanners report different vulnerability sets, with Jaccard coefficients as low as 0.6. This is due to different interpretations of vulnerability types and statuses. For instance, should we care about vulnerabilities in library headers?
7/n
7/n
One thing is for sure: images based on Alpine Linux contain less vulnerabilities than images based on CentOS, Debian or Ubuntu. This is simply because Alpine Linux comes with fewer packages than other distributions. Well done @alpinelinux!
8/n
8/n
A few recommendations to build more secure container images:
* Introduce software dependencies cautiously
* Use lightweight base images such as @alpinelinux
* Use OS releases with long-term support
* Run vulnerability scanners during continuous integration
9/n
* Introduce software dependencies cautiously
* Use lightweight base images such as @alpinelinux
* Use OS releases with long-term support
* Run vulnerability scanners during continuous integration
9/n
Also, update images regularly... but wait, isn& #39;t it going to break reproducibility? Yes, it might (sigh). Follow @g_kiar& #39;s and @ASalar007& #39;s work for more updates on that front.
10/n
10/n
The amount of security vulnerabilities found in containers is worrying. As a community, we should make our analyses robust to software updates, and use the latest security fixes. Let& #39;s not panic though: good old password cracking is probably still more dangerous!
11/n
11/n
Congrats to @bhangu_kaur for putting that work together! And thanks to Aiman Hanna, for providing all the background on security, to @mathdugre, for helping out with the experiments, and to you, for reading this thread to the end!
12/12
12/12

 Read on Twitter
Read on Twitter