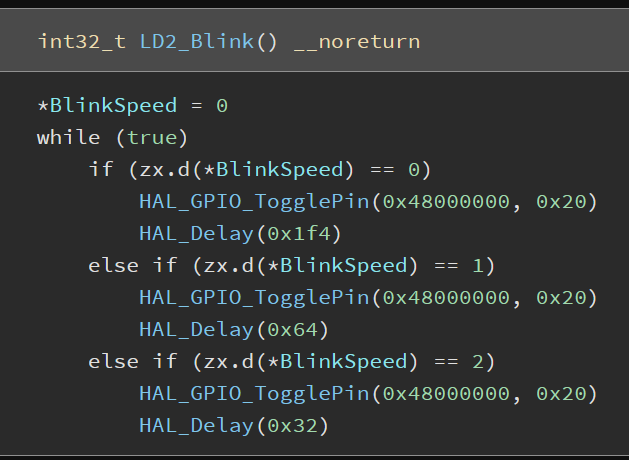
A very simple LED blinky for the STM32-F030R8.
It& #39;s just the relevant bits of the standard code on the device.
Let& #39;s see what this looks like in various disassemblers/decompilers!
It& #39;s just the relevant bits of the standard code on the device.
Let& #39;s see what this looks like in various disassemblers/decompilers!
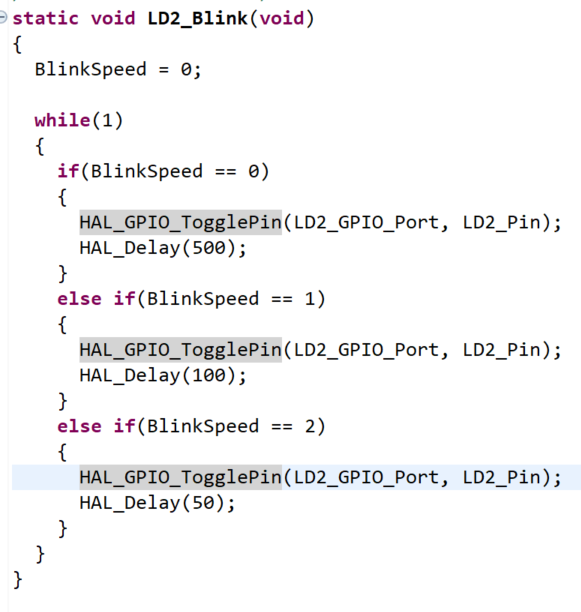
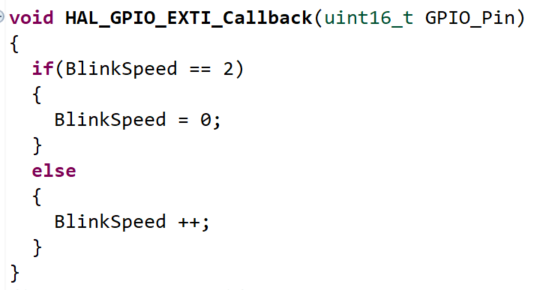
This is all it does!
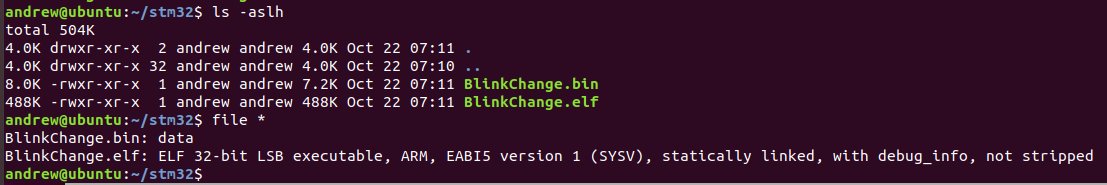
STM32Cube (and any other toolchain, really) make both an .elf and a .bin.
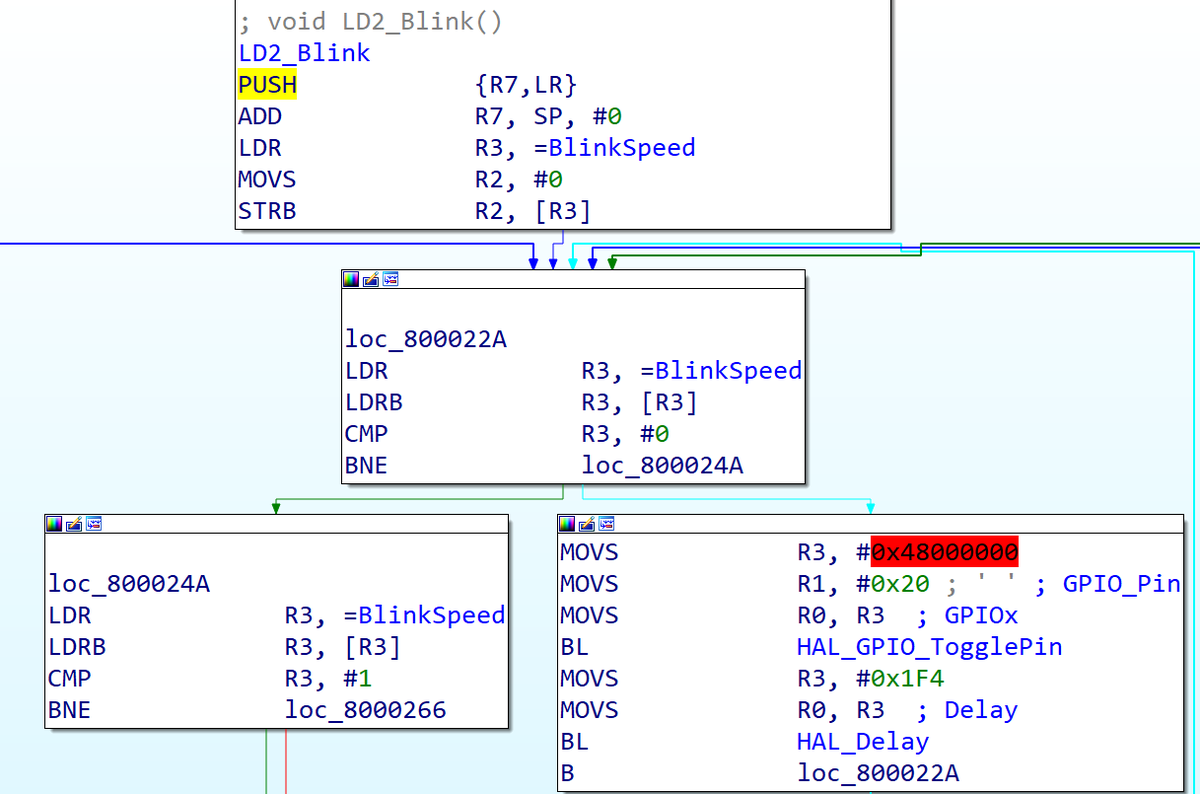
Let& #39;s see what the .elf looks like in IDA. We don& #39;t need to tell it that it& #39;s ARM etc. as this is in the ELF.
Let& #39;s see what the .elf looks like in IDA. We don& #39;t need to tell it that it& #39;s ARM etc. as this is in the ELF.
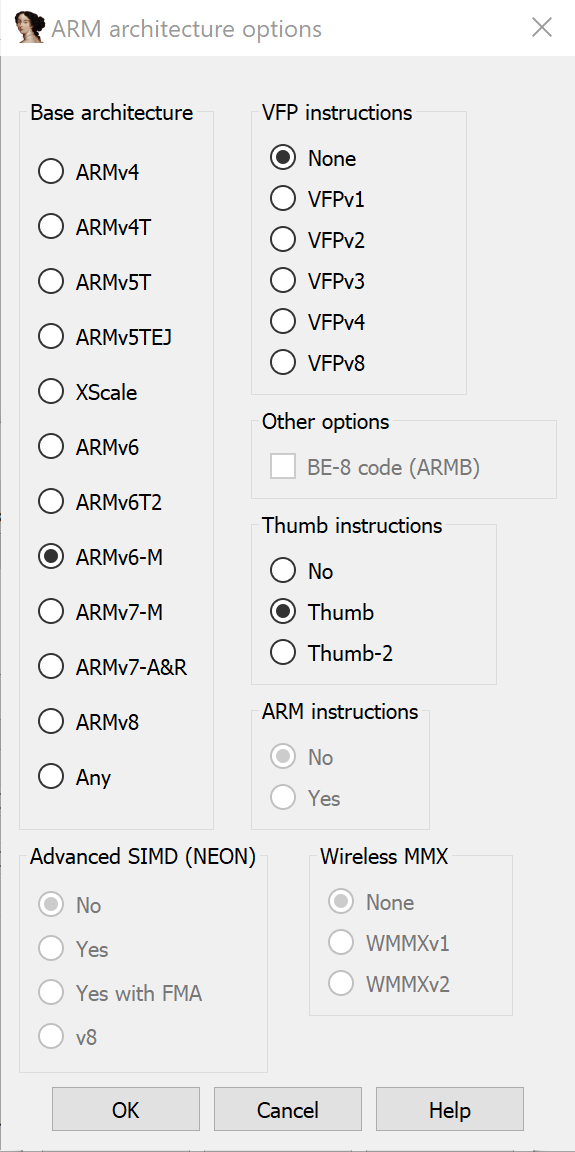
We could tell it something about the processor (Cortex M0, so ARMv6-M), but ELF shouldn& #39;t need this so much.
Ghidra is much the same - .elf loads straight away.
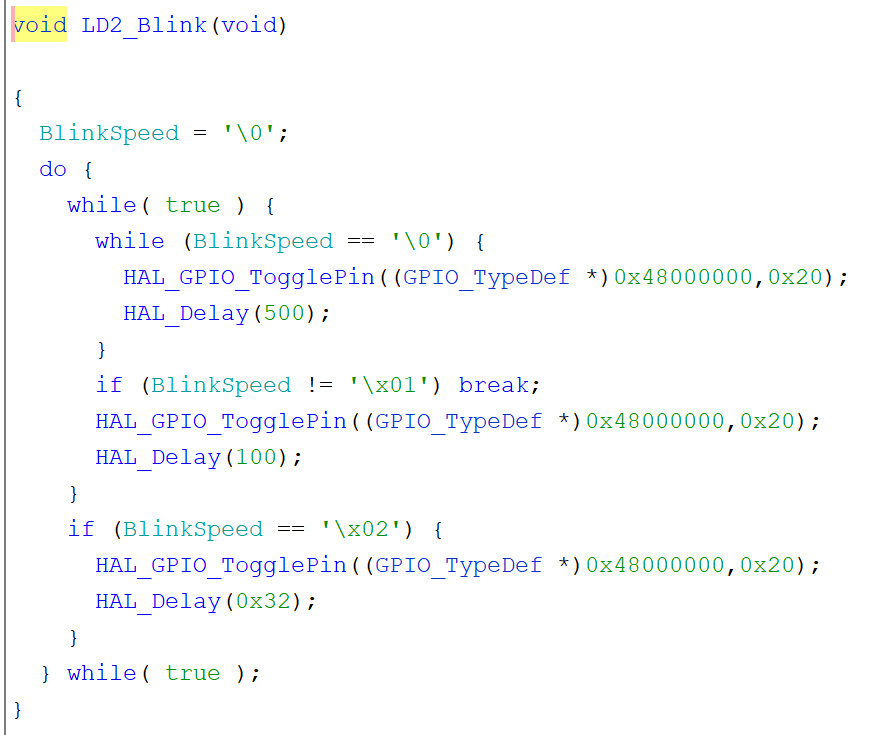
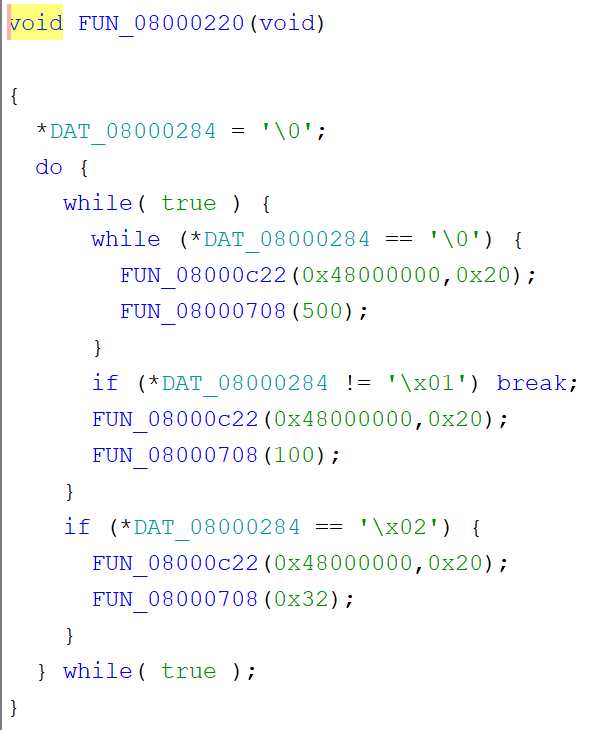
The decompiled function is not bad at all!
The speed has been interpreted as a string, and the loops are... interesting. But very easy to infer what is going on.
The decompiled function is not bad at all!
The speed has been interpreted as a string, and the loops are... interesting. But very easy to infer what is going on.
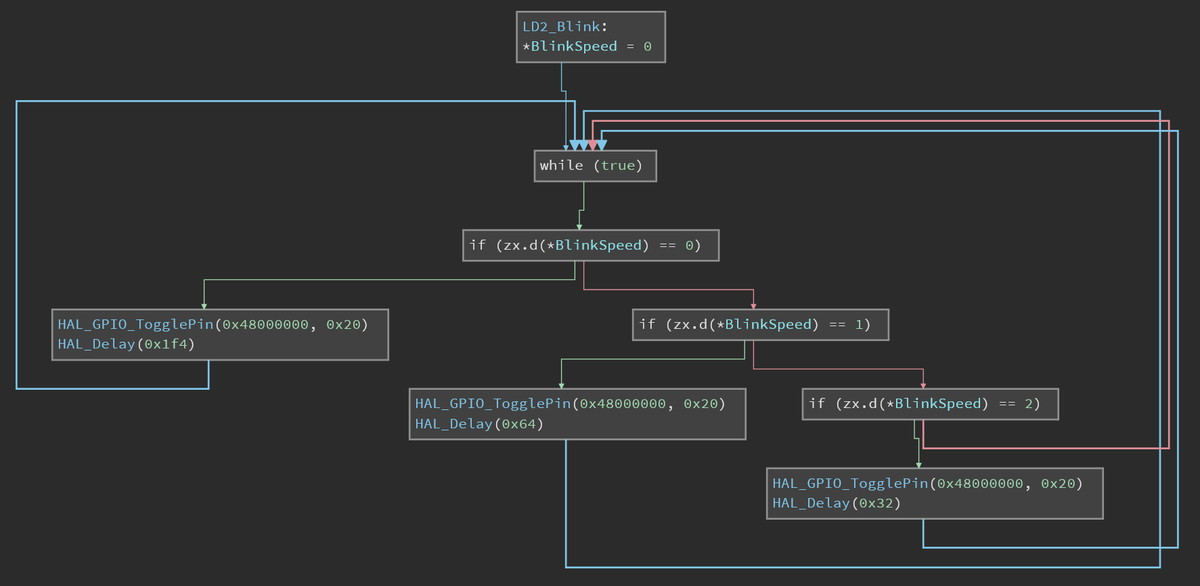
Binary Ninja Cloud has really clean high level decompiled code. I don& #39;t think this could be more obvious IMHO
That& #39;s practically what I wrote, so really not bad!
Now, the problem is that we wouldn& #39;t have that .elf if we had pulled the firmware from a device. We have a .bin - which is going to be devoid of all the symbols and other information.
The .bin?
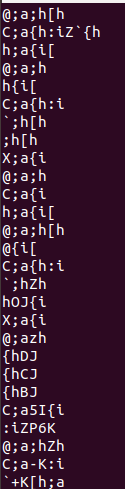
No actual ASCII strings!
This is one of the issues with baremetal firmware - unless it logs or interacts with external systems, it might not have any strings at all!
No actual ASCII strings!
This is one of the issues with baremetal firmware - unless it logs or interacts with external systems, it might not have any strings at all!
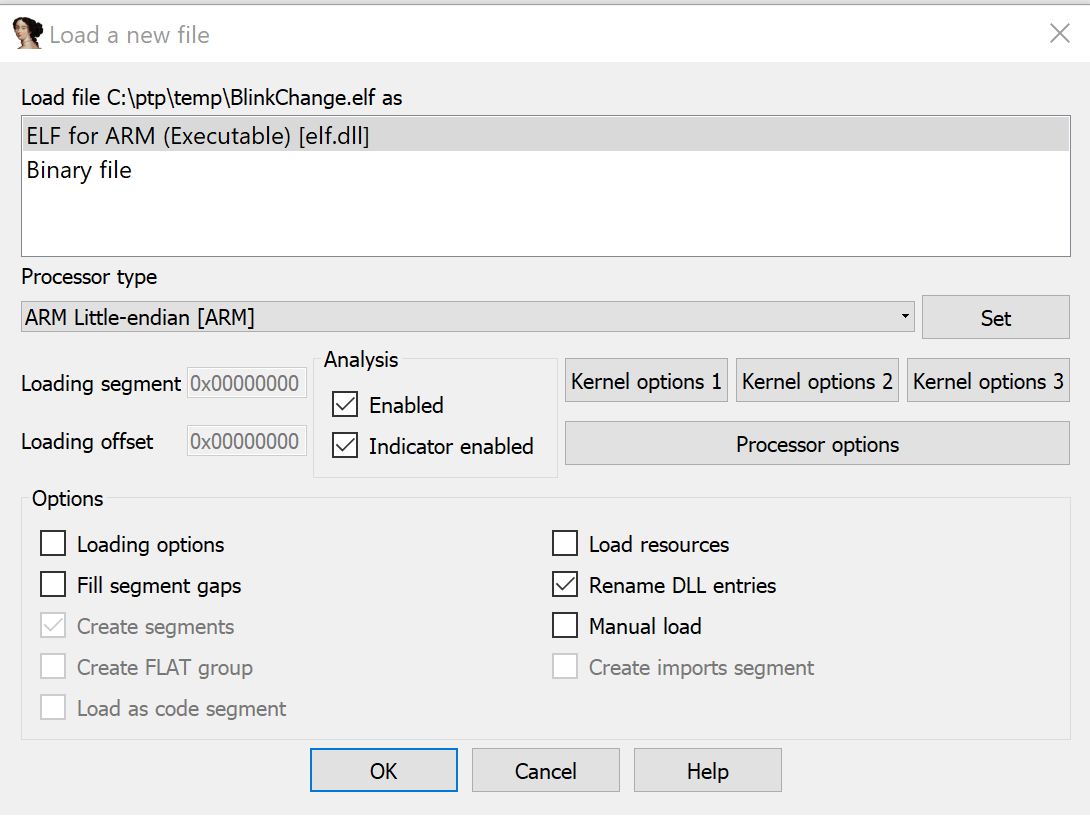
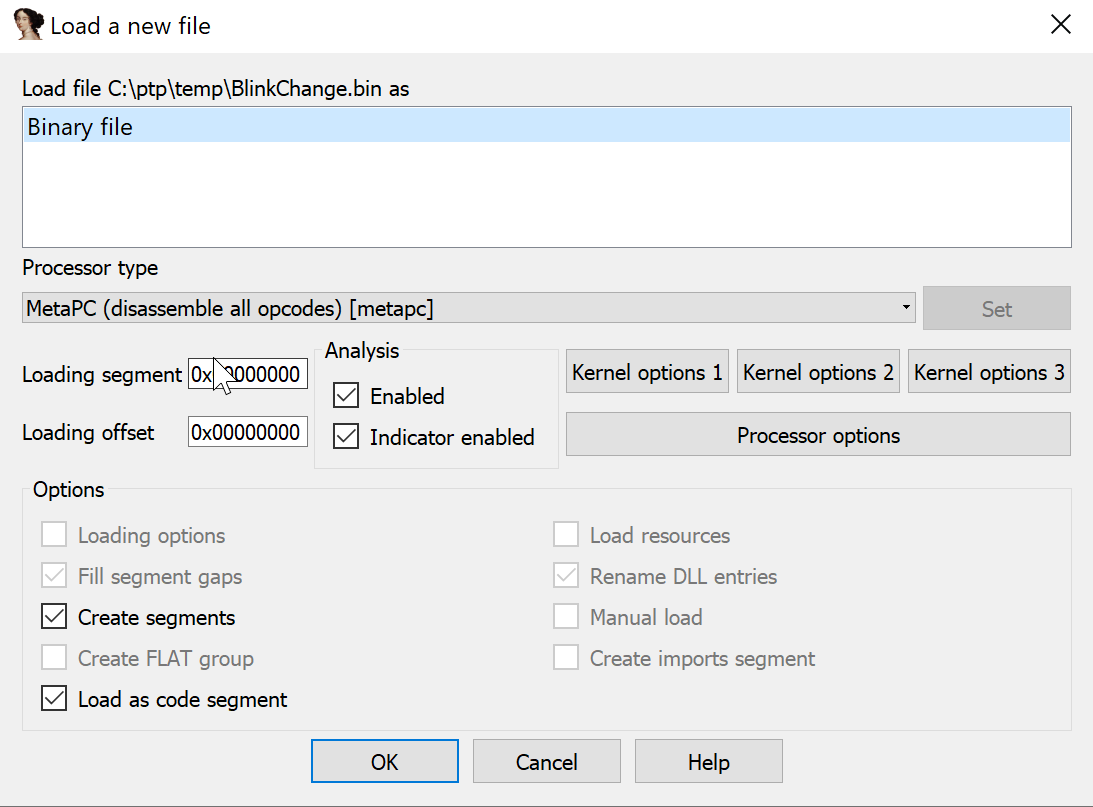
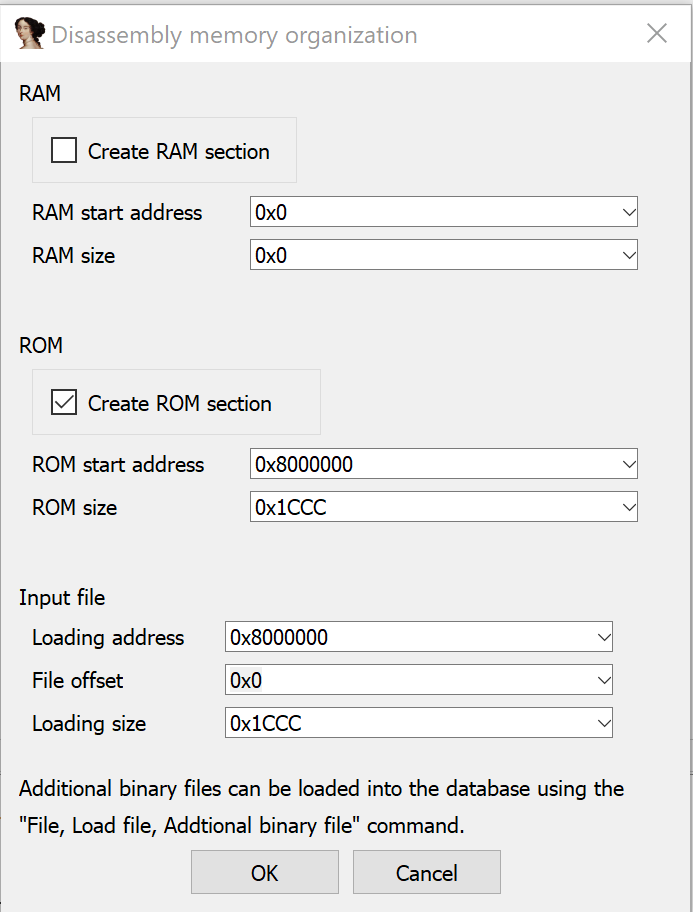
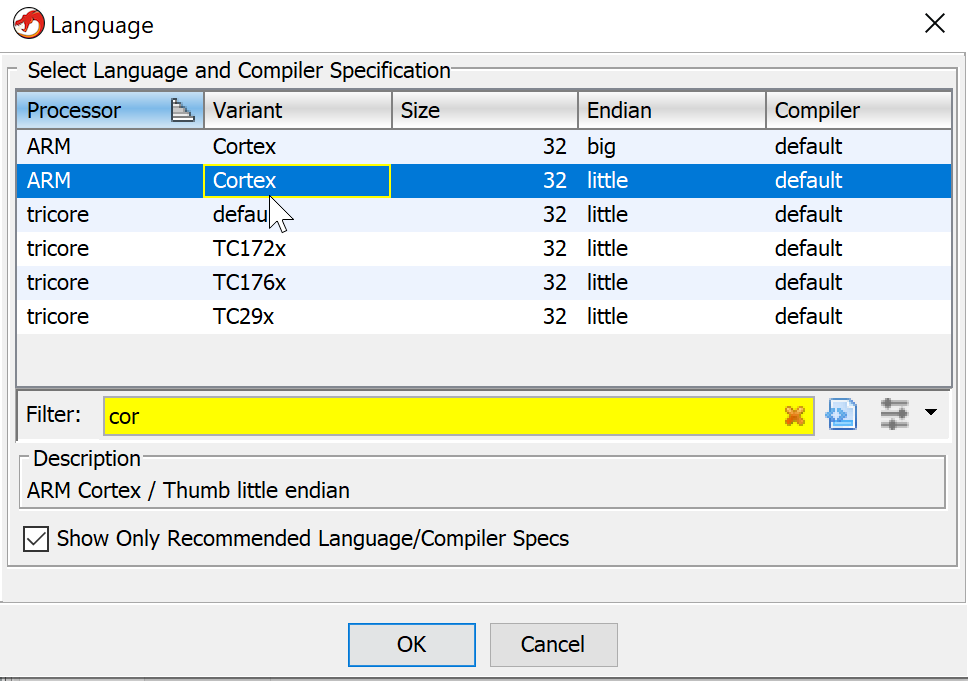
So we open the .bin in IDA and it doesn& #39;t know anything about it. We need to tell it.
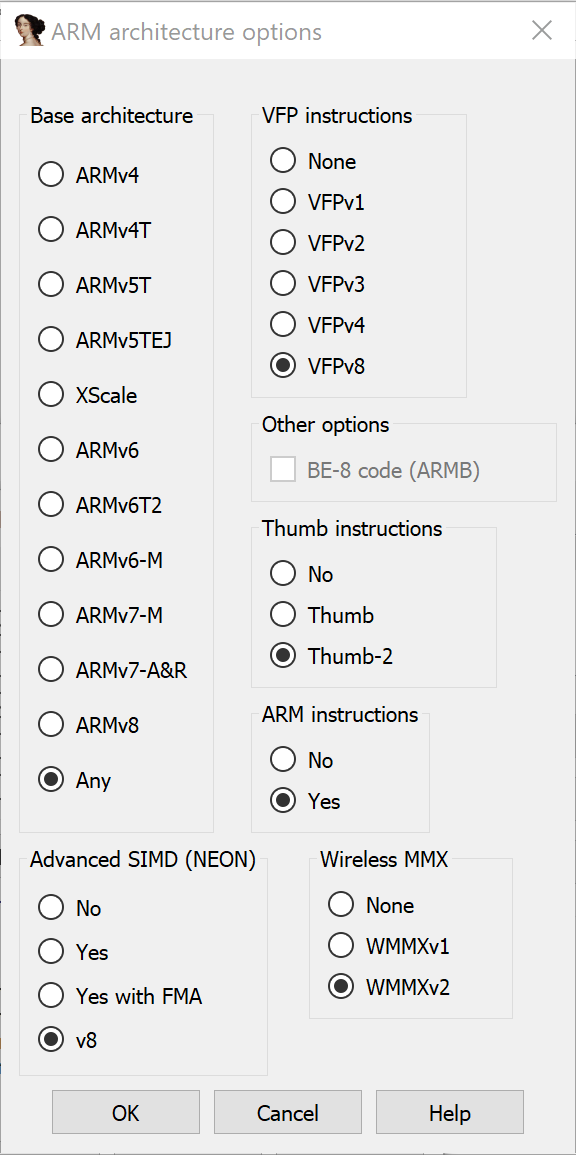
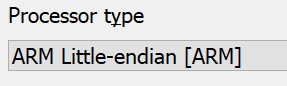
It& #39;s ARM little-endian.
And it& #39;s ARMv6-M. That means no full ARM instructions, only original thumb. It makes the disassemblers work far easier.
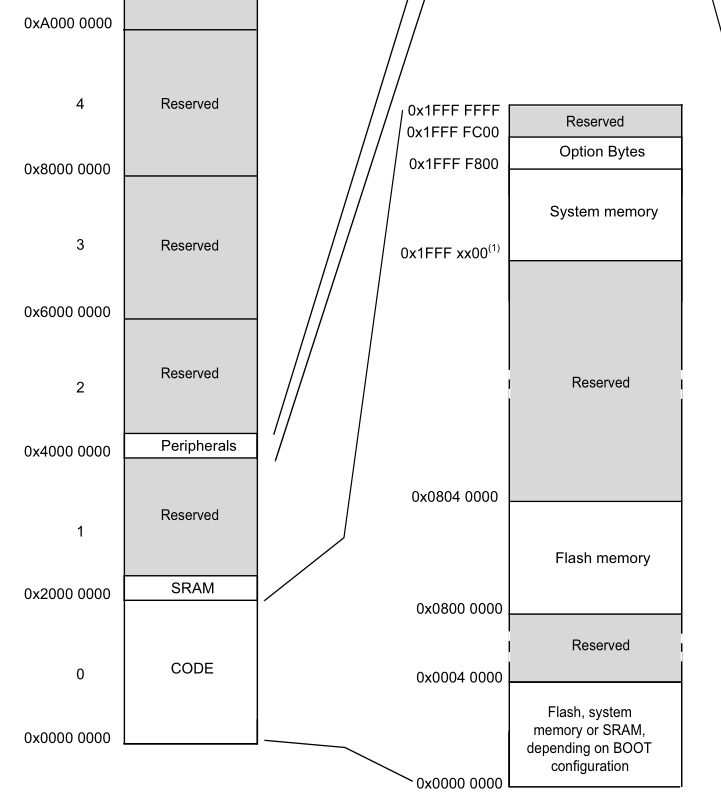
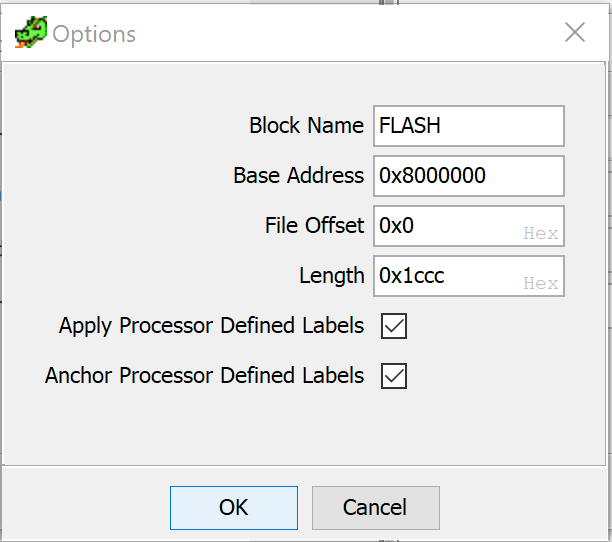
We need to tell IDA where to load the file. Look to the datasheet, and we can see that flash is at 0x8000000 on these chips.
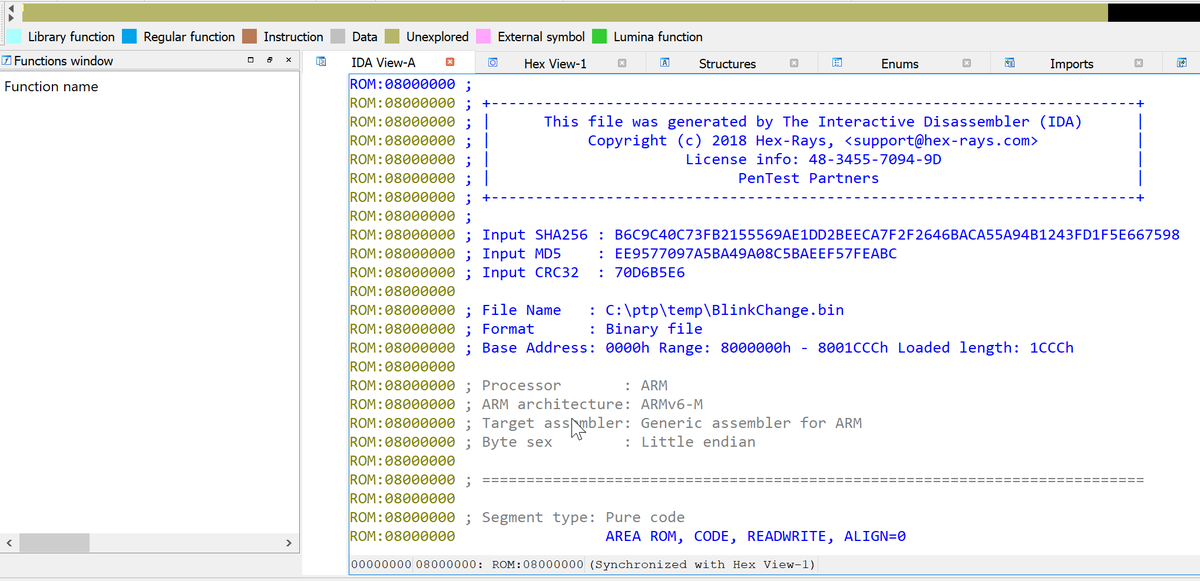
Oh. No IDA magic?
That& #39;s because there is no way for IDA to know where to start looking for code. We need to tell it!
That& #39;s because there is no way for IDA to know where to start looking for code. We need to tell it!
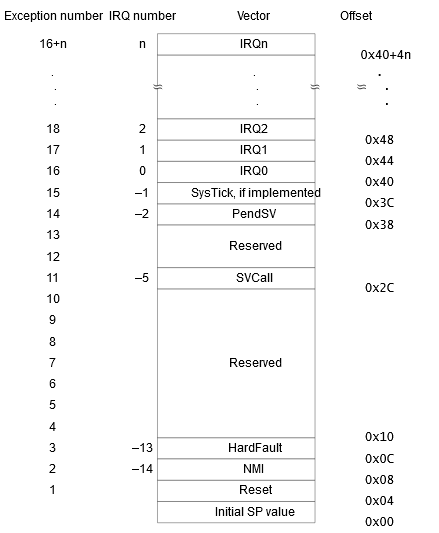
ARM Cortex-M0 (and many other ARM Cortex) use something called a vector table, right at the start of flash.
The word is the initial stack pointer. The next is the reset vector - where to run code from! This tells us where to start.
The word is the initial stack pointer. The next is the reset vector - where to run code from! This tells us where to start.
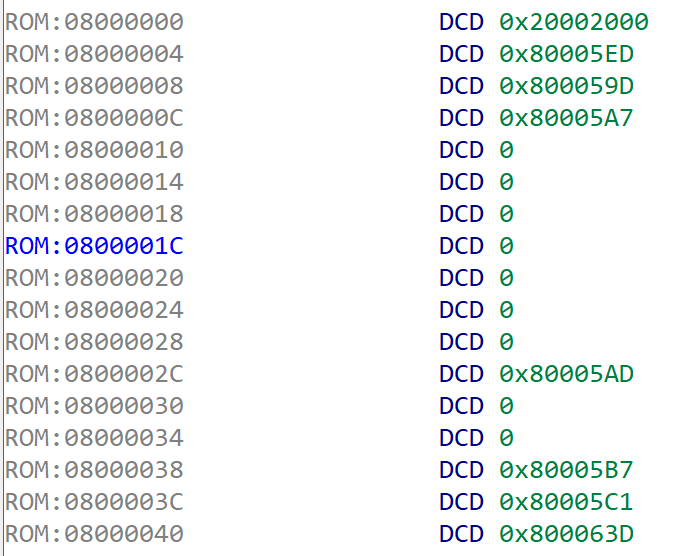
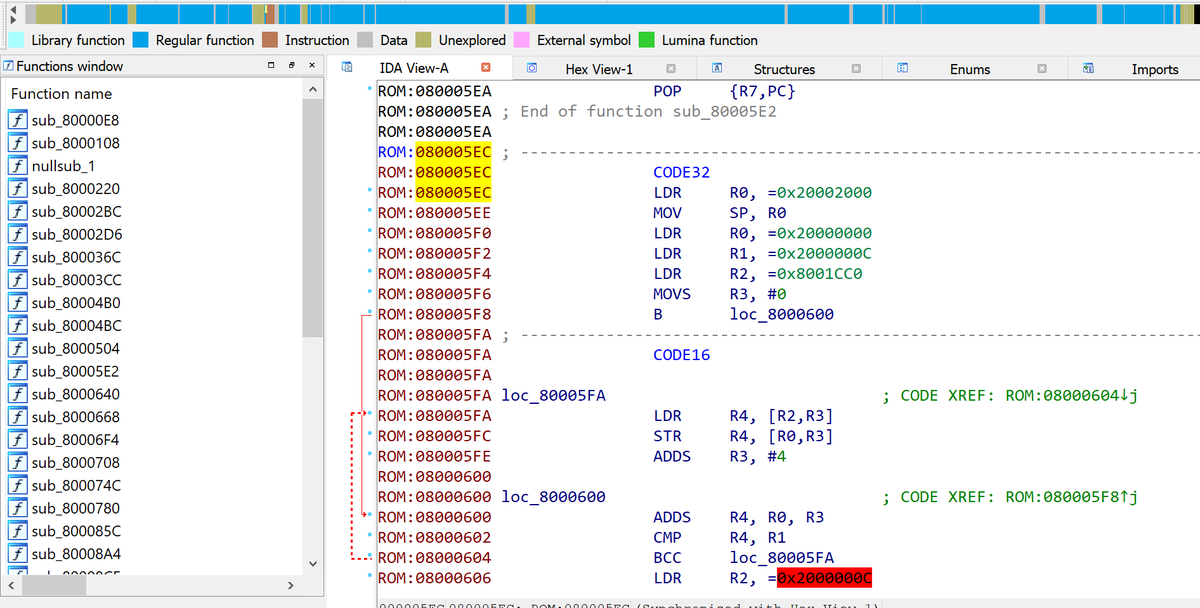
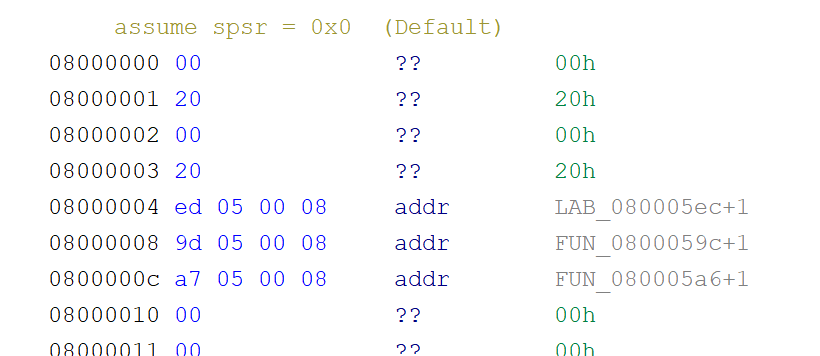
A few taps of the "D" key to change bytes into words, and we can see these vectors.
Reset is 0x80005ED. Lets& #39;s jump there by double clicking on it!
Reset is 0x80005ED. Lets& #39;s jump there by double clicking on it!
Well, a strange quirk of ARM is that the least significant bit of an called address says if it is in Thumb mode or ARM mode. We know we are in Thumb mode... as it can only run in Thumb mode. We need to subtract 1 from the address to get 0x80005EC.
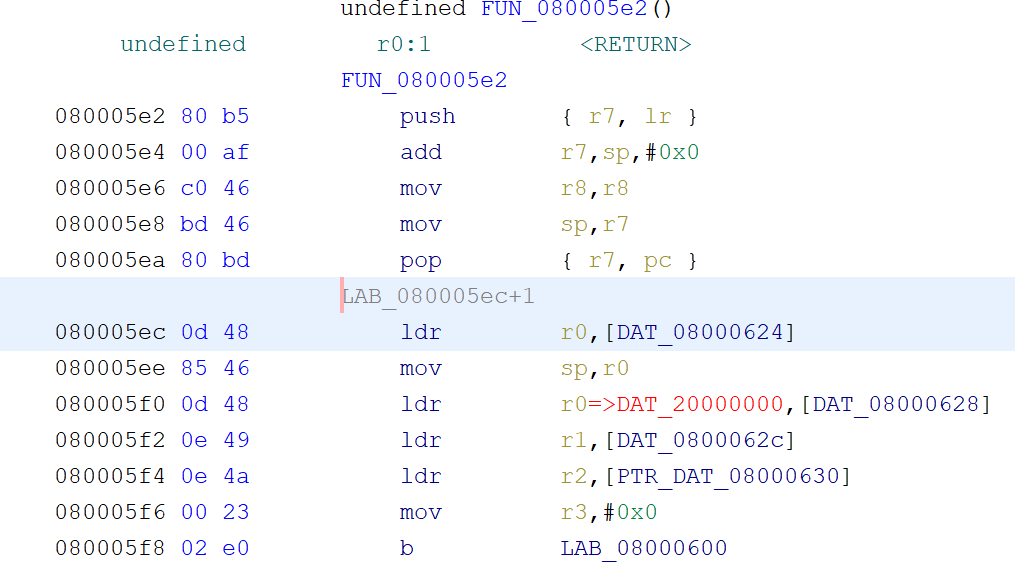
Bang!
Bang!
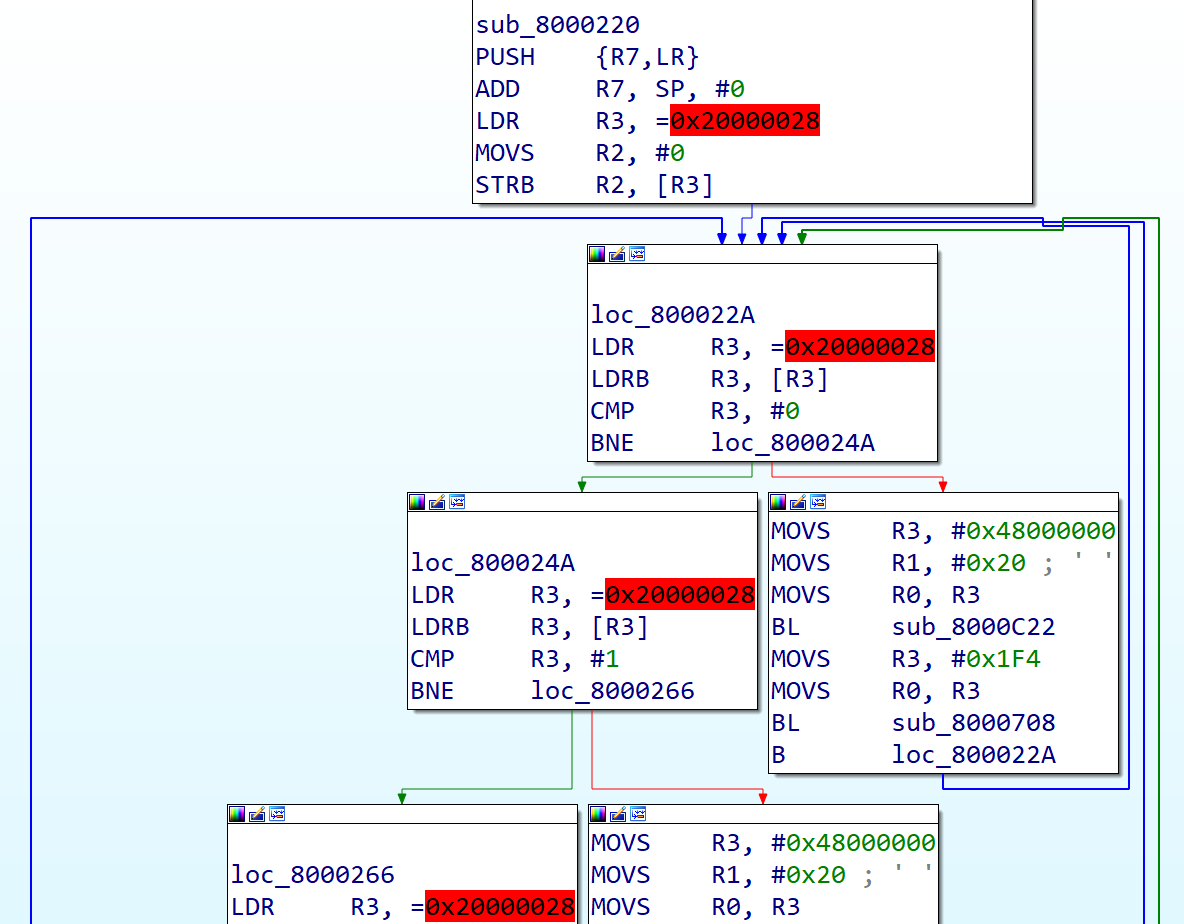
Let& #39;s head to our LD2_Blink() function.
It still looks nice, a good structure. But now the variable names have gone, the functions it calls have gone. This is much harder work to reverse.
It still looks nice, a good structure. But now the variable names have gone, the functions it calls have gone. This is much harder work to reverse.
Now, Ghidra sometimes sets up the ARM vector table automatically (when it& #39;s at 0x0). It hasn& #39;t done it here.
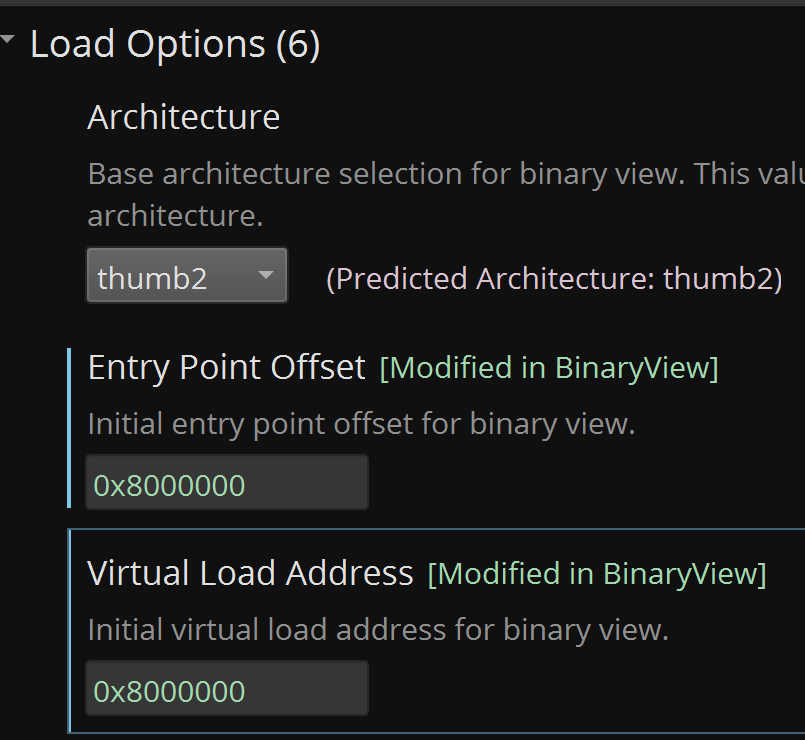
Now, I can& #39;t do this in Binary Ninja Cloud to show you what it does, but I can try the trial.
It& #39;s guessed that it& #39;s thumb2 - although the chip is only thumb, this should not present an issue.
I found these offsets very confusingly named compared to IDA and Ghidra.
It& #39;s guessed that it& #39;s thumb2 - although the chip is only thumb, this should not present an issue.
I found these offsets very confusingly named compared to IDA and Ghidra.
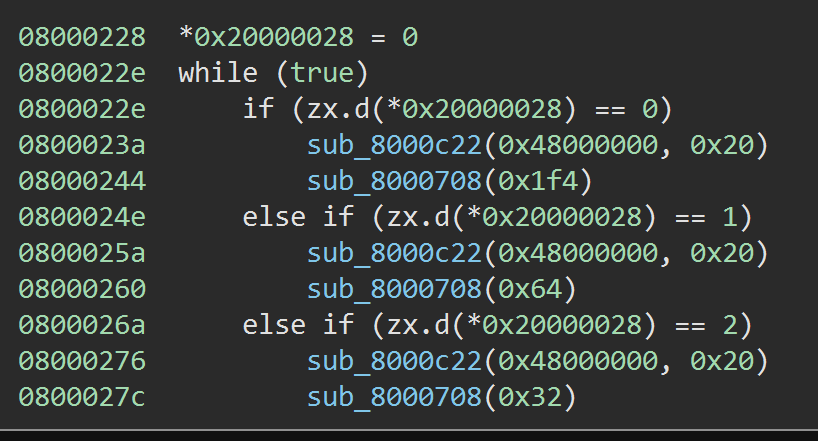
And it& #39;s done an admirable job here, finding the function.
As people have pointed out, there are ways and means to make a lot of this automated. But I hope it illustrates how much harder it can be to work with bare metal firmware.
Sometimes we don& #39;t even know *what* the processor is, or have a memory map.
Sometimes we don& #39;t even know *what* the processor is, or have a memory map.

 Read on Twitter
Read on Twitter