This shouldn’t be news to anyone,but human operated ransomware is a problem that has gotten completely out of control
The reasons are relatively straightforward:
The reasons are relatively straightforward:
The cost to pay is often significantly less than cost to business impact from downtime
The “supply” of possible targets is significantly higher than traditional financial crime which have to target payment/gift cards, banks (or related orgs)
Monetization is also wayyyyy easier
The “supply” of possible targets is significantly higher than traditional financial crime which have to target payment/gift cards, banks (or related orgs)
Monetization is also wayyyyy easier
I don’t think you will see a material change in % of orgs who pay ransom unless governments make payment of ransoms illegal (which will have a lot of other unintended consequences).
Do you think governments should outlaw payment of cyber ransoms?
Do you think governments should outlaw payment of cyber ransoms?
If governments banning payment of ransoms isn’t feasible/reasonable - what other actions be take to materially impact frequency of human operated ransomware campaigns causing significant disruption?
And don’t tell me orgs just need better security or more security staff. Many of orgs being hit have no dedicated security resources (just IT personnel).
I remember a 300 person manufacturing org hit with a 6 figure ransom payment. Most 300 person orgs have no security staff
I remember a 300 person manufacturing org hit with a 6 figure ransom payment. Most 300 person orgs have no security staff
Maybe MSPs can help fill the gap?
Let’s pretend MSP detects breach in progress. Most MSP’s I’ve seen report intrusions but don’t take recovery steps
If attacker obtains domain admin rights & you were notified by MSP - what could you realistically do to prevent the ransomware
Let’s pretend MSP detects breach in progress. Most MSP’s I’ve seen report intrusions but don’t take recovery steps
If attacker obtains domain admin rights & you were notified by MSP - what could you realistically do to prevent the ransomware
Even relatively simple things like password changes (in a windows environment) take several hours (180 hours is default on DCs for replication).
If you are in this situation - you aren’t left w/many good options
1) shut off internet (most orgs won’t do this)
2) block workstation to workstation comms (not trivial to implement quickly). What happens if attacker pushes ransomware from DC logon script (quite common)?
1) shut off internet (most orgs won’t do this)
2) block workstation to workstation comms (not trivial to implement quickly). What happens if attacker pushes ransomware from DC logon script (quite common)?
3) One of more successful approaches I’ve seen implemented while working w/ @MsftSecIntel is deployment of Attack Surface Reduction rules that limit files that can run (length of time or system prevalence) combined w/ AV detection using cloud lookups https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/configure-machines-asr">https://docs.microsoft.com/en-us/win...
The threat actors are often operating from countries that won’t cooperate with foreign law enforcement (or have enough corruption to nullify international law enforcement cooperation)
And advent of crypto currency enables criminals to largely bypass the regulated banking system
And advent of crypto currency enables criminals to largely bypass the regulated banking system
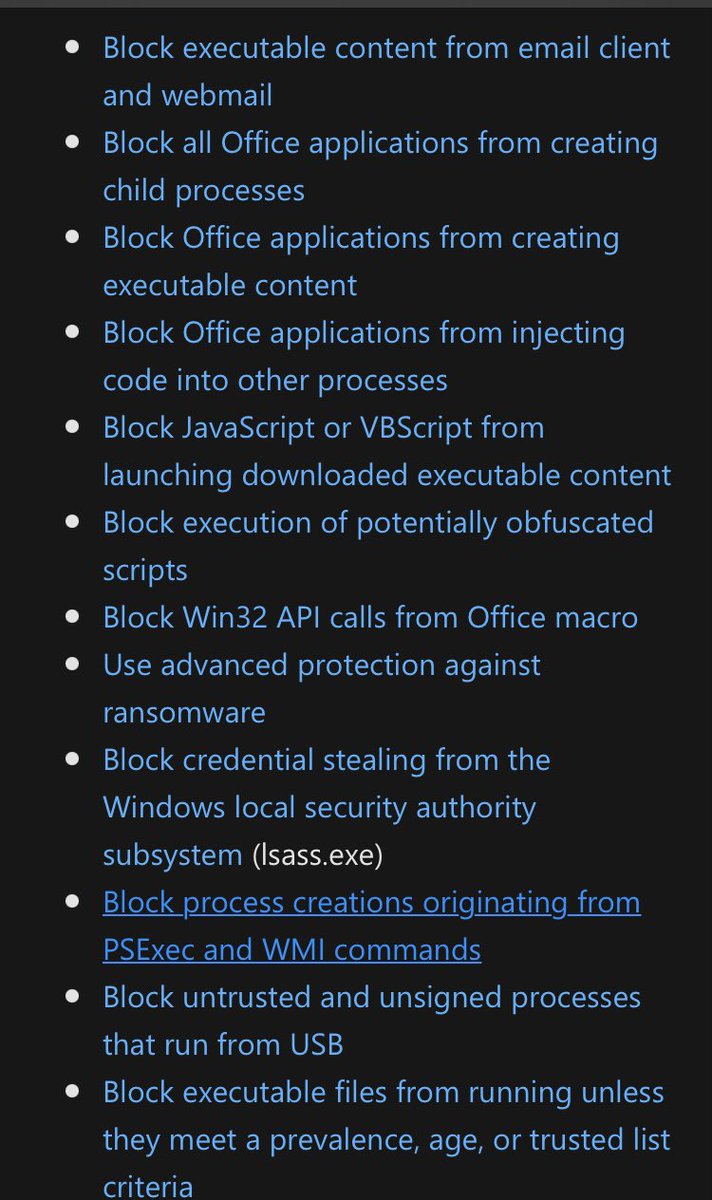
If you aren’t familiar with (or haven’t implemented) Attack Surface Reduction rules - there are a ton of really useful ones that can limit chance of initial compromise, privilege escalation and some forms of lateral movement/remote execution

 Read on Twitter
Read on Twitter