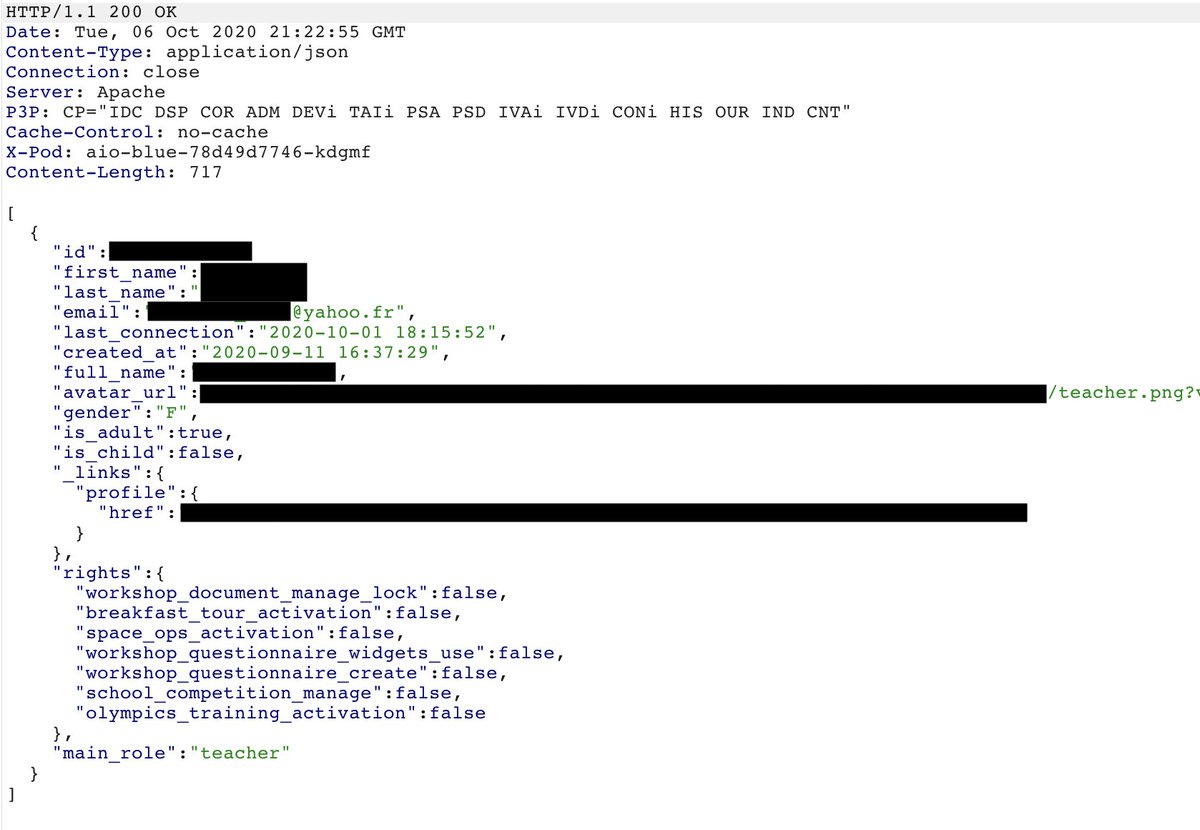
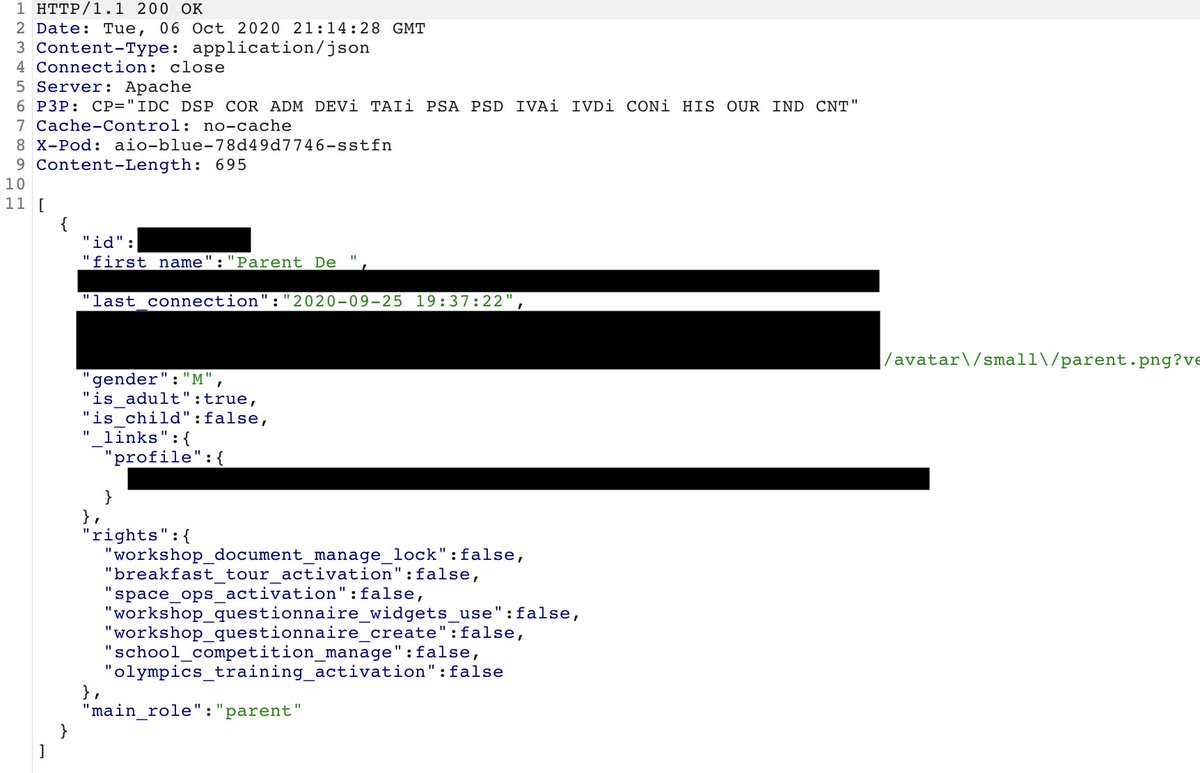
My kid school gave me the account credentials to access « the secure website » where the teacher will post homework, news, ... Are you ready for some fun?
Nothing obvious or crazy at the moment. A lot of checks are done on the server side which is a good thing  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Leicht lächelndes Gesicht" aria-label="Emoji: Leicht lächelndes Gesicht">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Leicht lächelndes Gesicht" aria-label="Emoji: Leicht lächelndes Gesicht">
Angular is still a thing in 2020?
2 wordpress websites on their server:
- WordPress version 4.9.5: released on 2018-04-03
- WordPress version 4.4.2: released on 2016-02-02
- WordPress version 4.9.5: released on 2018-04-03
- WordPress version 4.4.2: released on 2016-02-02
When you reset your password, the website gives you a temporary password. The issue is that password has always the same format: 6 letters + 3 numbers
So, *in theory*, this email address disclosure allows an attacker to:
- spam the teacher inbox email by resetting his password again and again
- brute force the temporary password to takeover the teacher account
- spam the teacher inbox email by resetting his password again and again
- brute force the temporary password to takeover the teacher account
Yes I know, you really need to be bored and/or motivated to brute force the password  https://abs.twimg.com/emoji/v2/... draggable="false" alt="😅" title="Lächelndes Gesicht mit offenem Mund und Angstschweiß" aria-label="Emoji: Lächelndes Gesicht mit offenem Mund und Angstschweiß">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😅" title="Lächelndes Gesicht mit offenem Mund und Angstschweiß" aria-label="Emoji: Lächelndes Gesicht mit offenem Mund und Angstschweiß">
In the directory tab, you can get the names of the pupils and so their IDs (which is a feature). The pupil ID + 1 is the ID of their parents.
If you use the "users lookup" endpoint I used to get the teacher email address, you can get the last connected time of the parents and also their avatars.
I will stop here. I didn& #39;t test the document upload and because this is the begining, the workspace is empty (no news, no homeworks, etc).
Also they have some interesting subdomains but I clearly don& #39;t have time to look at it tonight
Last year the same assessment on a different website was... different https://twitter.com/fs0c131y/status/1174046477594873856">https://twitter.com/fs0c131y/...

 Read on Twitter
Read on Twitter " title="Nothing obvious or crazy at the moment. A lot of checks are done on the server side which is a good thing https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Leicht lächelndes Gesicht" aria-label="Emoji: Leicht lächelndes Gesicht">" class="img-responsive" style="max-width:100%;"/>
" title="Nothing obvious or crazy at the moment. A lot of checks are done on the server side which is a good thing https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Leicht lächelndes Gesicht" aria-label="Emoji: Leicht lächelndes Gesicht">" class="img-responsive" style="max-width:100%;"/>