Yesterday @jc_stubbs published an article about a Russian backed fake news site and @VickerySec found that the Wordpress back end was wide open. This means the underlying folders that hold the raw photos displayed on the site were viewable showing when the photos were uploaded https://twitter.com/VickerySec/status/1311682344051380226">https://twitter.com/VickerySe...
Many photo formats contain what is known as metadata, information included in the file that is extra data about the file. For photos this is known as EXIF, Exchangeable Image File Format, which can include time, location, focal length, lens type, creation date, modification date
and other data fields that can help a photographer edit and catalog their photos. See here for more information https://photographylife.com/what-is-exif-data
As">https://photographylife.com/what-is-e... Chris pointed out the site had a first logo with a different name and second logo with the name they eventually went with
As">https://photographylife.com/what-is-e... Chris pointed out the site had a first logo with a different name and second logo with the name they eventually went with
I& #39;ve archived that file here https://web.archive.org/web/20201002145531/https://naebc.com/wp-content/uploads/2020/08/ava_fbgab_400x400.jpg
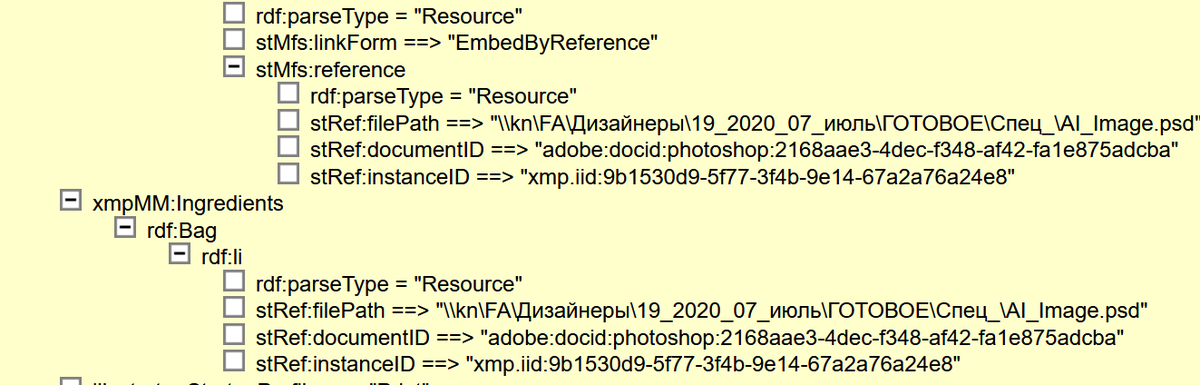
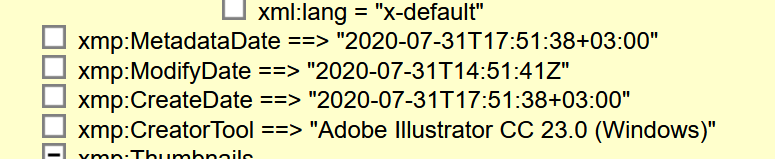
The">https://web.archive.org/web/20201... file didn& #39;t have the normal metadata from a photo but a subset that shows up on files generated with an Adobe program, in this case illustrator
The">https://web.archive.org/web/20201... file didn& #39;t have the normal metadata from a photo but a subset that shows up on files generated with an Adobe program, in this case illustrator
From the metadata we can tell it was created on a Windows Computer on 7/31/2020 that used Russian as the default operating language
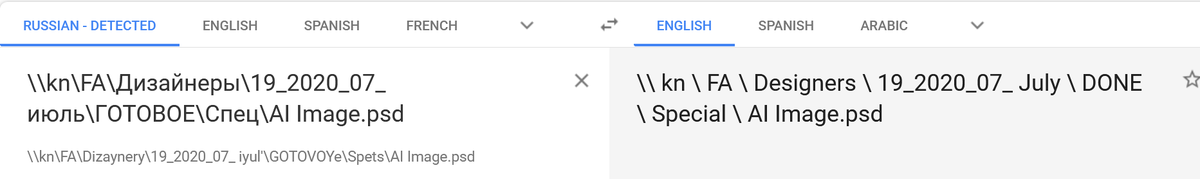
The actual file path name isn& #39;t exciting from Google Translate and verified by 2 Russian speakers
The actual file path name isn& #39;t exciting from Google Translate and verified by 2 Russian speakers
Metadata can be faked but most images uploaded didn& #39;t have any. A few of the images from filename can be identified as having come from someone& #39;s facebook, which uses a unique file naming scheme.
@razhael has a good article with a longer breakdown of how EXIF can be used for news stories. (Note I assisted with that story) https://www.bellingcat.com/news/americas/2018/10/26/joseph-mifsud-rush-exif/">https://www.bellingcat.com/news/amer...

 Read on Twitter
Read on Twitter