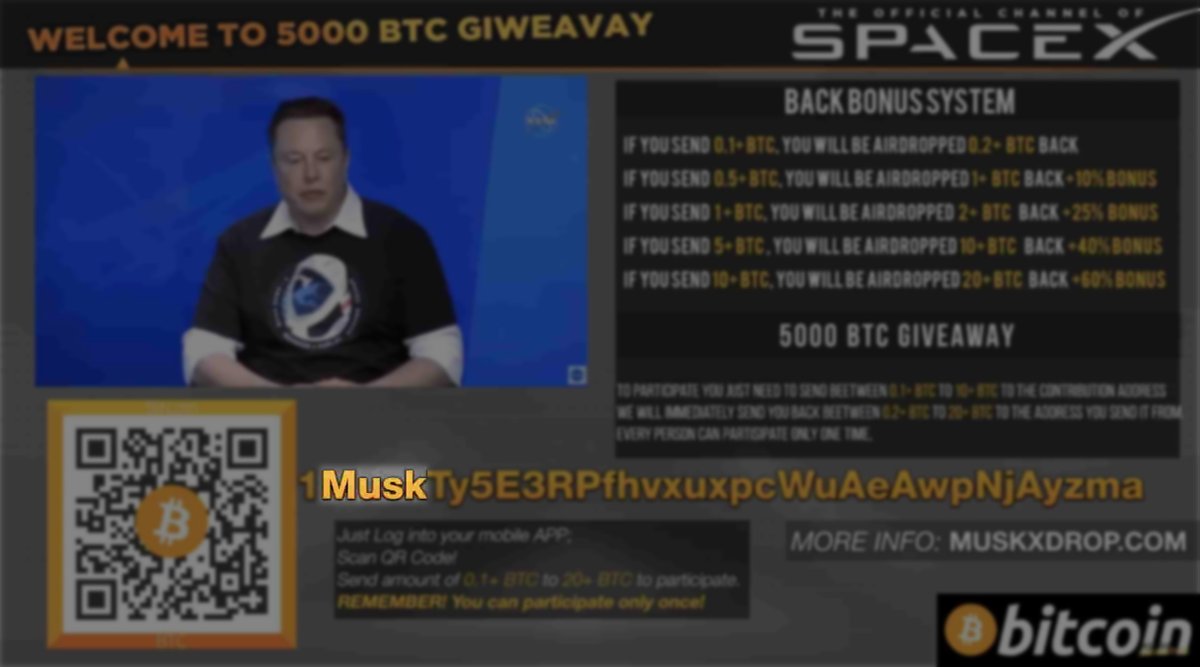
Something fascinating about the @YouTube bitcoin scams is that they often use addresses containing specific keywords. Bitcoin addresses are generated by cryptographic hash functions, and it is practically impossible to find the matching private key for a given address.
This means that the scammers must be using a brute force method to find these addresses by running random private keys through the hash function until they find one that generates an address containing the desired word.
Bitcoin uses SHA-256 encryption and there are 2²⁵⁶ (1.2 x 10⁷⁷) possible addresses, so the computational power required to find just 1 address containing a specific word must be insane. They& #39;d probably have to run billions or even trillions of keys through the hash function.
All of this is in addition to hacking hundreds of YouTube accounts and bypassing 2FA undetected, hosting dozens of livestreams with thousands of view bots, and tumbling bitcoins between addresses without a trace.
To date, the scammers have stolen more than $10 million USD from YouTube viewers and they are still active on the platform. This is clearly a large-scale operation that is being carried out by professional criminals.
@samsheffer You may be interested in this thread as well. I don& #39;t understand why @TeamYouTube has let this go on for so long, and why creators and viewers aren& #39;t putting more pressure on them to do something about it.

 Read on Twitter
Read on Twitter