oh wow.
so this DOS game (name hidden for Reasons) uses encryption, probably for anti-piracy reasons, right?
But here& #39;s the thing: the encryption is the kind where applying it to an encrypted file decrypts it, and applying it to a decrypted file encrypts it
so this DOS game (name hidden for Reasons) uses encryption, probably for anti-piracy reasons, right?
But here& #39;s the thing: the encryption is the kind where applying it to an encrypted file decrypts it, and applying it to a decrypted file encrypts it
so how do they use this? so there& #39;s a .BAT file called "run.bat& #39; that comes with it, which does the following:
ENCRYPT game.exe KEYHERE
game.exe
ENCRYPT game.exe KEYHERE
ENCRYPT game.exe KEYHERE
game.exe
ENCRYPT game.exe KEYHERE
so when you try to load the game, it decrypts it, plays it, then when you exit, it decrypts it.
ok, so... wow. so many problems here
ok, so... wow. so many problems here
the first one is that THE KEY IS IN THE BATCH FILE.
WHO IS THIS STOPPING? THE WORLD& #39;S LAZIEST PIRATE?
WHO IS THIS STOPPING? THE WORLD& #39;S LAZIEST PIRATE?
secondly, what if the game doesn& #39;t exit properly? what if the computer is just turned off, rebooted, or the game just crashes?
well, when the game tries to decode itself before playing, it& #39;ll actually... encrypt itself.
and then try to run an encrypted file, which& #39;ll fail badly.
and then try to run an encrypted file, which& #39;ll fail badly.
although amusingly this is self-fixing:
once you try to run the encrypted file and fail, your computer will crash and you& #39;ll have to reboot.
but now the file is encrypted again, like it& #39;s supposed to be, so when you load it again, it& #39;ll decrypt itself and then run
once you try to run the encrypted file and fail, your computer will crash and you& #39;ll have to reboot.
but now the file is encrypted again, like it& #39;s supposed to be, so when you load it again, it& #39;ll decrypt itself and then run
so, let& #39;s hack the encryption. why? no reason. we can avoid it just by running it once and then removing the encryption calls from the batch file, but I& #39;m feeling up to it.
We could reverse engineer the encrypt binary, but that sounds hard (it& #39;s almost a thousand bytes of 16bit x86 code!)
so let& #39;s crack the encryption without even looking at a single byte of encrypt .com
so let& #39;s crack the encryption without even looking at a single byte of encrypt .com
now we open up our 256 bytes of 00 file and oh look
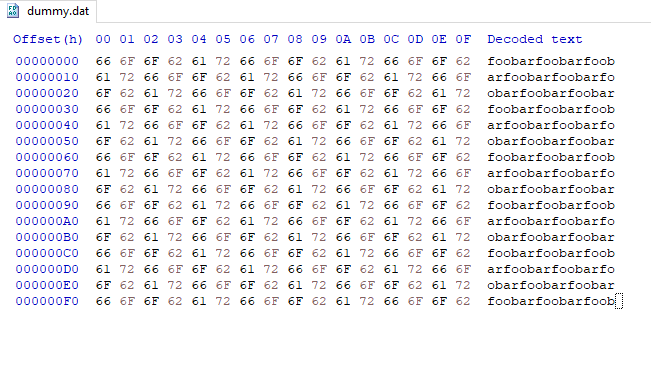
it& #39;s now become "foobar" repeated over and over.
why is that?
it& #39;s now become "foobar" repeated over and over.
why is that?
The answer is it& #39;s the laziest kind of encryption with a key:
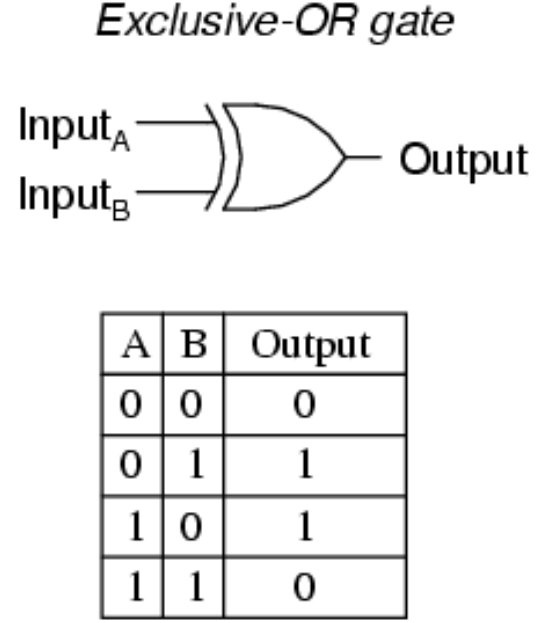
it& #39;s XOR.
So XOR is an operation where the output is 1 if one of the inputs is 1, and 0 otherwise.
it& #39;s XOR.
So XOR is an operation where the output is 1 if one of the inputs is 1, and 0 otherwise.
the fun thing about xor is that you can apply it to a sourcetext and a key, and you generate some scrambled output, but if you apply the key again, it reverts back to the original value. So you don& #39;t need separate "encryption" and "decryption" code, you just apply XOR every time
the simple way to think about how XOR encryption works is that it basically toggles bits, but only sometimes.
if the bit in the key is 0, the corresponding bit in the source is not flipped (0 stays 0, 1 stays 1)
if the bit in the key is 0, the corresponding bit in the source is not flipped (0 stays 0, 1 stays 1)
and if the bit in the key is 1, you do flip the bit.
a 0 becomes a 1, and a 1 becomes a 0.
You just need to do this for every bit in the source, repeating the key as many times as needed.
a 0 becomes a 1, and a 1 becomes a 0.
You just need to do this for every bit in the source, repeating the key as many times as needed.
In theory XOR would be perfectly secure if your key was the same length as your sourcetext... but it& #39;s usually not. usually it& #39;s like kilobytes or megabytes of source and a key like "foobar"
and here& #39;s the big problem with short keys and applying xor on executable files: THEY TEND TO HAVE LOTS OF ZEROS IN THEM.
And remember how I said XOR doesn& #39;t flip the bit if the key is 0?
well, it& #39;s symmetric. if the source is 0, it doesn& #39;t flip the key...
And remember how I said XOR doesn& #39;t flip the bit if the key is 0?
well, it& #39;s symmetric. if the source is 0, it doesn& #39;t flip the key...
meaning that any parts of your input file that are zeros just turn into your key in the output.
that& #39;s why our dummy file turned into foobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobar
that& #39;s why our dummy file turned into foobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobarfoobar
so yeah, right now the batch file pointlessly leaks the key to us, but imagine it didn& #39;t? maybe it instead queries the key from a dongle or a server or god knows what.
would that be secure, assuming it& #39;s still short? NOPE!
would that be secure, assuming it& #39;s still short? NOPE!
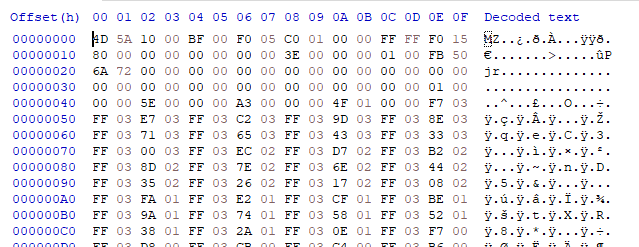
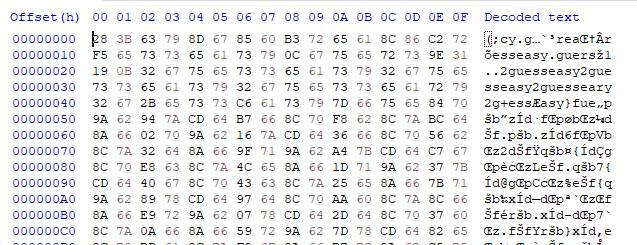
Here& #39;s the header of our EXE, unencrypted.
Now the magic encryption process is going to run on it, and turn it into unbreakable code, and we& #39;ll never guess the key...
Now the magic encryption process is going to run on it, and turn it into unbreakable code, and we& #39;ll never guess the key...
and now, it& #39;s encrypted! no one will ever figure out our highly secure password... what? how did you figure out it& #39;s "easy2guess"?
I think the designers of this game maybe heard about encryption but didn& #39;t really understand how it worked or how to apply it
BTW, I slightly lied about how the batch file worked.
there& #39;s actually TWO exe files that get encrypted and decrypted.
So you can actually manage to glitch your way into a situation where one is encrypted and the other isn& #39;t.
there& #39;s actually TWO exe files that get encrypted and decrypted.
So you can actually manage to glitch your way into a situation where one is encrypted and the other isn& #39;t.
which means every time you run the batch script it& #39;ll encrypt one and decrypt the other.
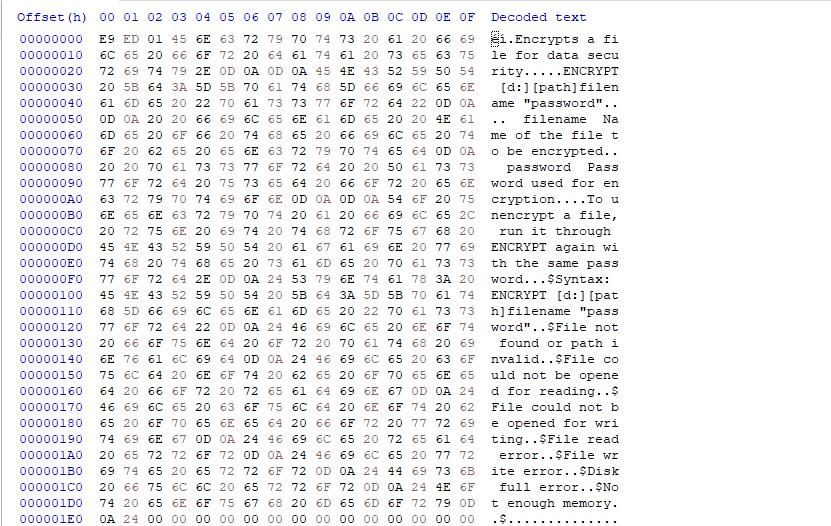
I suspect they got Encrypt from somewhere else, and also it turns out that like half of it is just help text.

 Read on Twitter
Read on Twitter