2021 Roadmap for Back-End Developers https://abs.twimg.com/emoji/v2/... draggable="false" alt="💕" title="Zwei Herzen" aria-label="Emoji: Zwei Herzen">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="💕" title="Zwei Herzen" aria-label="Emoji: Zwei Herzen">
This https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="Thread" aria-label="Emoji: Thread"> is for you
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🧵" title="Thread" aria-label="Emoji: Thread"> is for you https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
This
Internet
1. How does the internet work?
2. What is HTTP?
3. Browsers and how they work?
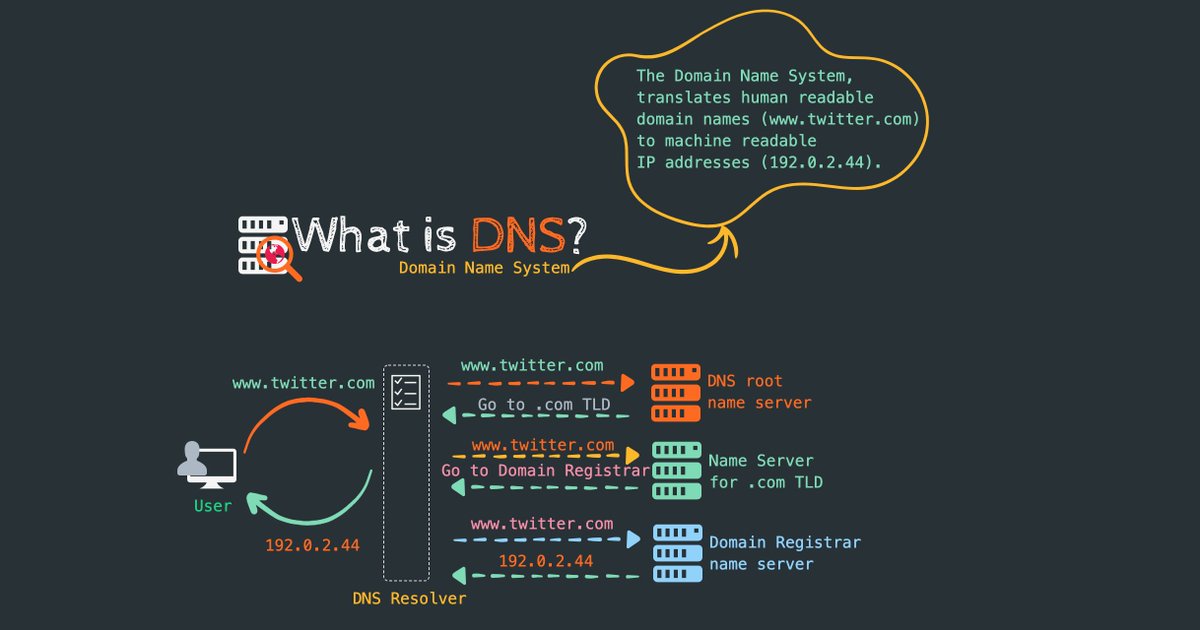
5. DNS and how it works?
6. What is Domain Name?
7. What is hosting?
1. How does the internet work?
2. What is HTTP?
3. Browsers and how they work?
5. DNS and how it works?
6. What is Domain Name?
7. What is hosting?
OS and General Knowledge
1. Terminal usage
2. How OSs work in general
3. Process Mgt.
4. Threads & concurrency
5. Basic terminal commands
6. Memory mgt.
7. Interprocess comm.
8. I/O mgt.
9. POSIX basics
10. Basic networking concepts
1. Terminal usage
2. How OSs work in general
3. Process Mgt.
4. Threads & concurrency
5. Basic terminal commands
6. Memory mgt.
7. Interprocess comm.
8. I/O mgt.
9. POSIX basics
10. Basic networking concepts
Learn a Language
Make sure to learn it& #39;s quirks. Core details about its runtime e.g concurrency, memory model etc.
1. Java
2. Python
3. PHP
4. C#
5. Javascript
6. Ruby
7. Rust
8. Go
9. ?
Make sure to learn it& #39;s quirks. Core details about its runtime e.g concurrency, memory model etc.
1. Java
2. Python
3. PHP
4. C#
5. Javascript
6. Ruby
7. Rust
8. Go
9. ?
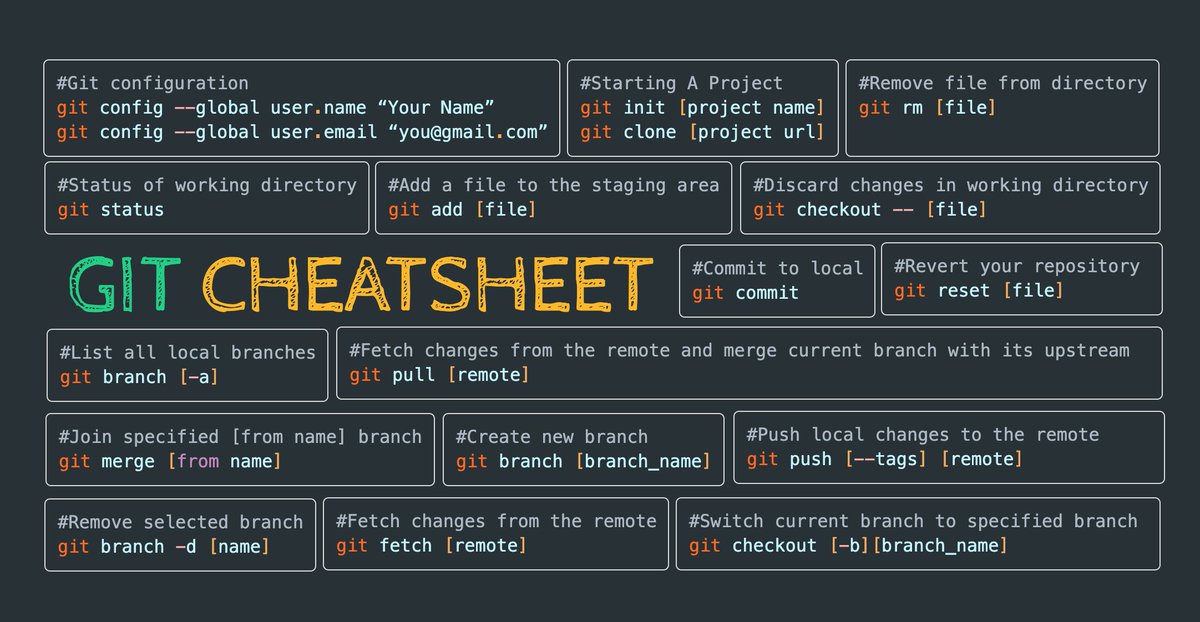
Version Control System
1. Basic usage of Git
2. Repo hosting services
I. GitHub
II. Gitlab
III. Bitbucket
1. Basic usage of Git
2. Repo hosting services
I. GitHub
II. Gitlab
III. Bitbucket
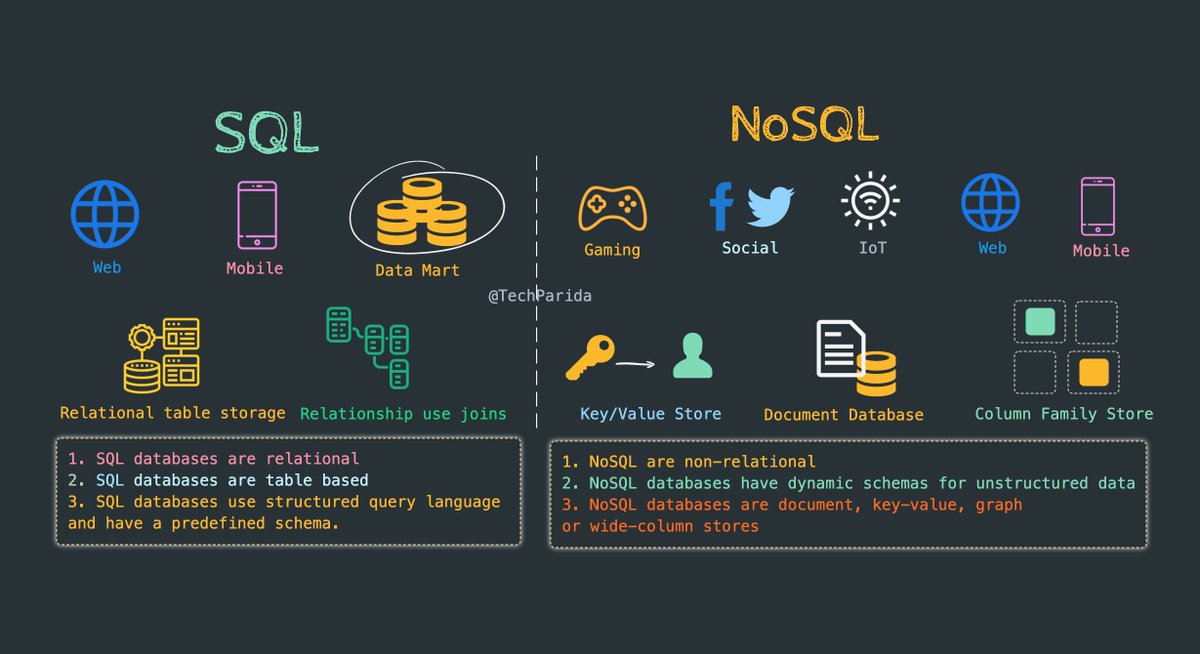
Relational Databases
1. MySQL
2. PostgreSQL
3. MariaDB
4. MS SQL
5. Oracle
1. MySQL
2. PostgreSQL
3. MariaDB
4. MS SQL
5. Oracle
More About Databases
1. ORMs
2. ACID
3. Transactions
4. N+1 Problem
5. Data Replication
6. Sharding Strategies
7. CAP Theorem
8. Database Normalisation
9. Indexes and how they work
1. ORMs
2. ACID
3. Transactions
4. N+1 Problem
5. Data Replication
6. Sharding Strategies
7. CAP Theorem
8. Database Normalisation
9. Indexes and how they work
Web Security Knowledge
1. Hashing Algorithm
I. MD5 and why not to use it
II. SHA Family
III. Scrypt
IV. Bcrypt
2. HTTPS
3. Content Security Policy
4. CORS
5. SSL/TLS
6. OWASP Security Risk
1. Hashing Algorithm
I. MD5 and why not to use it
II. SHA Family
III. Scrypt
IV. Bcrypt
2. HTTPS
3. Content Security Policy
4. CORS
5. SSL/TLS
6. OWASP Security Risk
Testing
1. Integration Testing
2. Unit Testing
3. Functional Testing
1. Integration Testing
2. Unit Testing
3. Functional Testing
CI/CD
1. Jenkins
2. GitLab
3. CircleCI
4. Bamboo
5. TeamCity
6. Travis CI
7. Buddy
1. Jenkins
2. GitLab
3. CircleCI
4. Bamboo
5. TeamCity
6. Travis CI
7. Buddy
Design and Development Principles
1. SOLID
2. KISS
3. YAGNI
4. DRY
5. GOF Design Patterns
6. Domain-Driven Design
7. Test-Driven Development
1. SOLID
2. KISS
3. YAGNI
4. DRY
5. GOF Design Patterns
6. Domain-Driven Design
7. Test-Driven Development
Architectural Patterns
1. Monolithic
2. Microservices
3. SOA
4. CQRS and Event Sourcing
5. Serverless
1. Monolithic
2. Microservices
3. SOA
4. CQRS and Event Sourcing
5. Serverless
Message Brokers
1. RabbitMQ
2. Kafka
1. RabbitMQ
2. Kafka
Containerization
1. Docker
2. rkt
3. LXC
1. Docker
2. rkt
3. LXC
Web Servers
1. Nginx
2. Apache
3. Caddy
4. MS IIS
1. Nginx
2. Apache
3. Caddy
4. MS IIS
Building For Scale
1. Migration Strategies
2. Horizontal vs Vertical Scaling
.
.
.
.
All the above topics will be covered in my YT Channel, many topics are already discussed and many coming. Subscribe and Keep Learning https://abs.twimg.com/emoji/v2/... draggable="false" alt="💕" title="Zwei Herzen" aria-label="Emoji: Zwei Herzen">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="💕" title="Zwei Herzen" aria-label="Emoji: Zwei Herzen">
1. Migration Strategies
2. Horizontal vs Vertical Scaling
.
.
.
.
All the above topics will be covered in my YT Channel, many topics are already discussed and many coming. Subscribe and Keep Learning
And for more details, you can visit the website
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="👉" title="Rückhand Zeigefinger nach rechts" aria-label="Emoji: Rückhand Zeigefinger nach rechts"> https://roadmap.sh/backend ">https://roadmap.sh/backend&q...
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👉" title="Rückhand Zeigefinger nach rechts" aria-label="Emoji: Rückhand Zeigefinger nach rechts"> https://roadmap.sh/backend ">https://roadmap.sh/backend&q...

 Read on Twitter
Read on Twitter