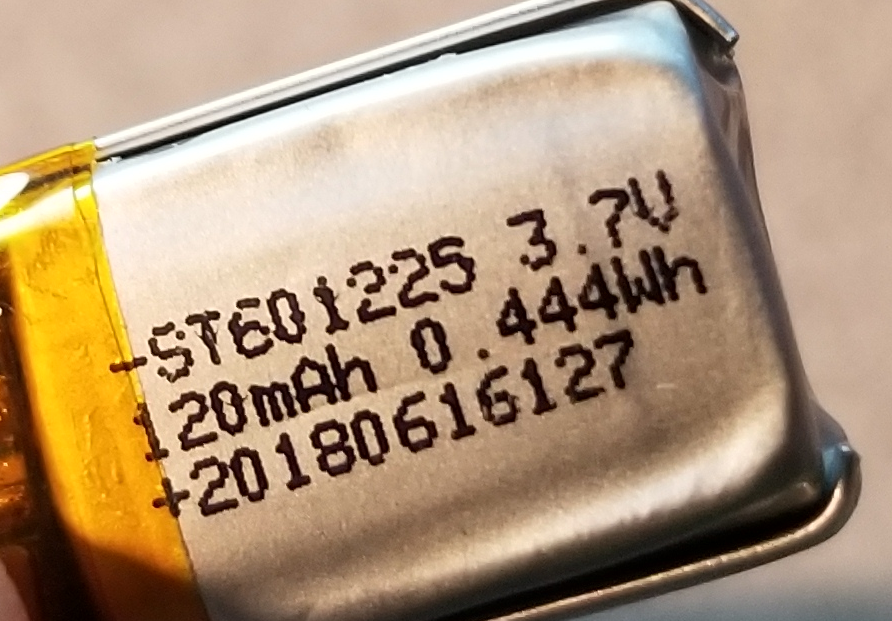Wanna see something you& #39;re NEVER SUPPOSED TO POST ON THE INTERNET? Really, the manual warns you like 5 times not to do this... but I& #39;m gonna.
So this is a Tzumi Klic padlock... cover your eyes.
So this is a Tzumi Klic padlock... cover your eyes.
DUN DUN DUN! I have violated all the warrantees and now Tzumi is crying.
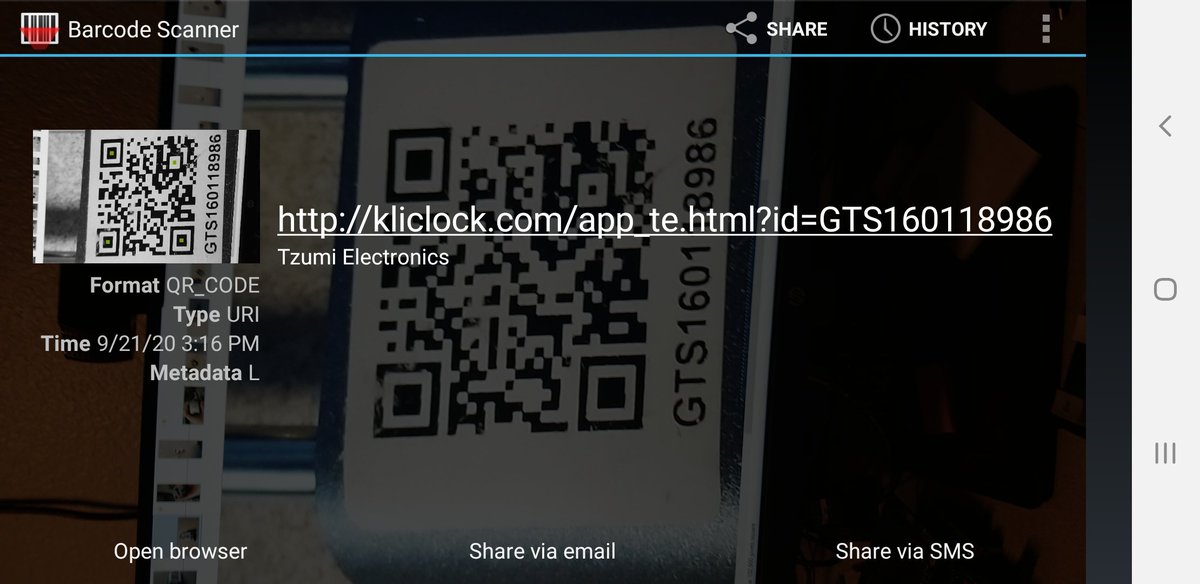
It& #39;s the QR code for this lock!
And yes, this lock has a FCC ID. That& #39;s a bad sign.
It& #39;s the QR code for this lock!
And yes, this lock has a FCC ID. That& #39;s a bad sign.
So the bottom of this padlock shows that there& #39;s no key slot.
Instead there& #39;s a power button, 4 digits, and... a USB port!?
Instead there& #39;s a power button, 4 digits, and... a USB port!?
Yeah, that& #39;s a microUSB port, because you can charge this lock.
So here& #39;s how this lock works: You scan that QR code, then the app can pair your phone with the lock, and it can send an unlock message.
Unfortunately my secondary camera fucked up when I recorded this, so... yeah. 2 frames per second.
Unfortunately my secondary camera fucked up when I recorded this, so... yeah. 2 frames per second.
So obviously there& #39;s two things to do with this lock:
1. figure out how the app works and hack the bluetooth
2. take it apart with some screwdrivers and hammers and spudgers
I went with #2, because it& #39;s easier to do while waiting on other stuff to complete.
1. figure out how the app works and hack the bluetooth
2. take it apart with some screwdrivers and hammers and spudgers
I went with #2, because it& #39;s easier to do while waiting on other stuff to complete.
So first the bottom part is a sticker (a SECURE sticker)
Then it& #39;s plastic (SECURE PLASTIC!) and some secure one-way screws.
Fun fact: with enough force and a properly sized flathead screwdriver, you can just back these out.
Then it& #39;s plastic (SECURE PLASTIC!) and some secure one-way screws.
Fun fact: with enough force and a properly sized flathead screwdriver, you can just back these out.
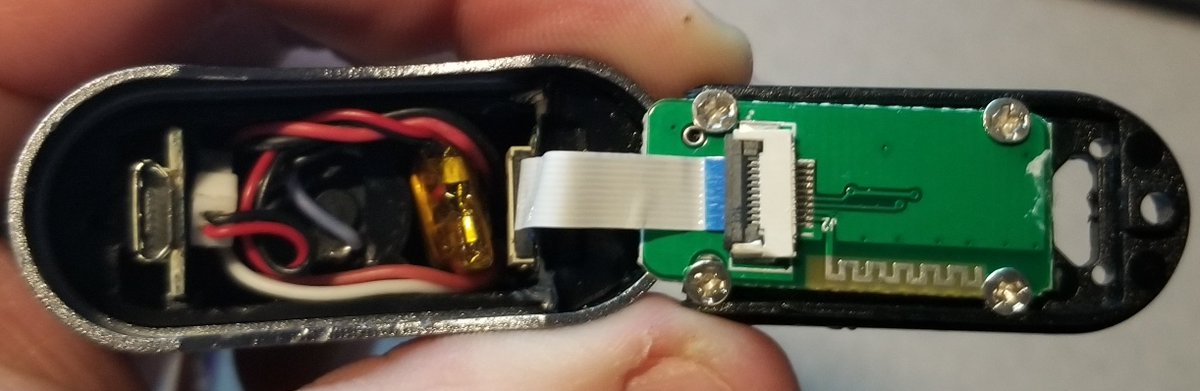
oh look we& #39;re in.
Unfortunately one of the screws got wedged and worn out so I had to break it.
Boy, everything seems shoved in there.
Unfortunately one of the screws got wedged and worn out so I had to break it.
Boy, everything seems shoved in there.
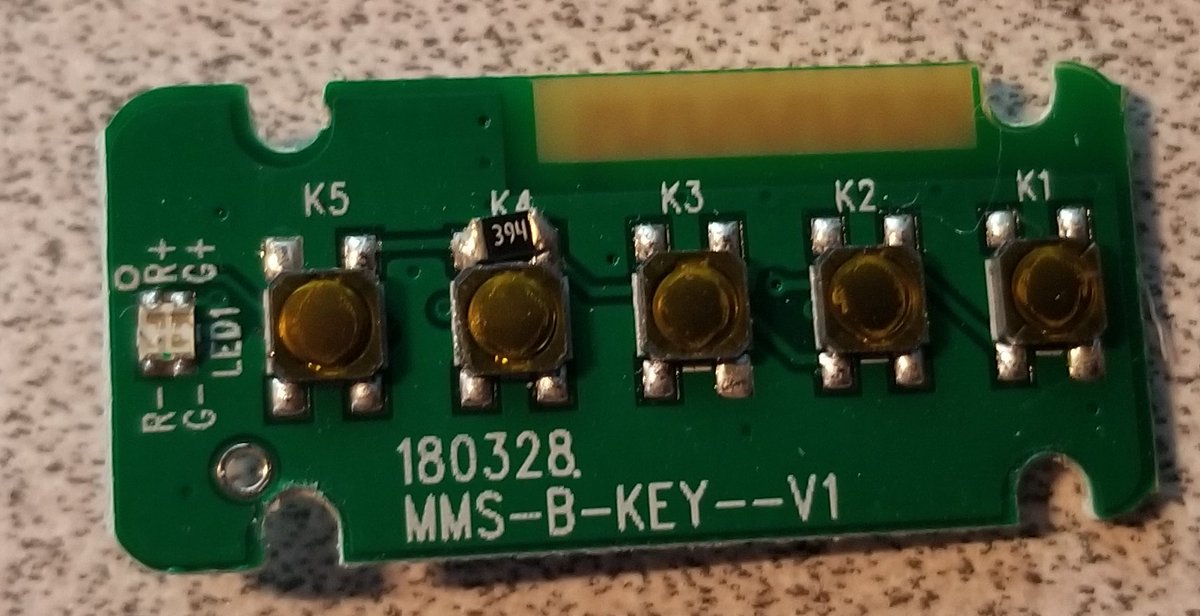
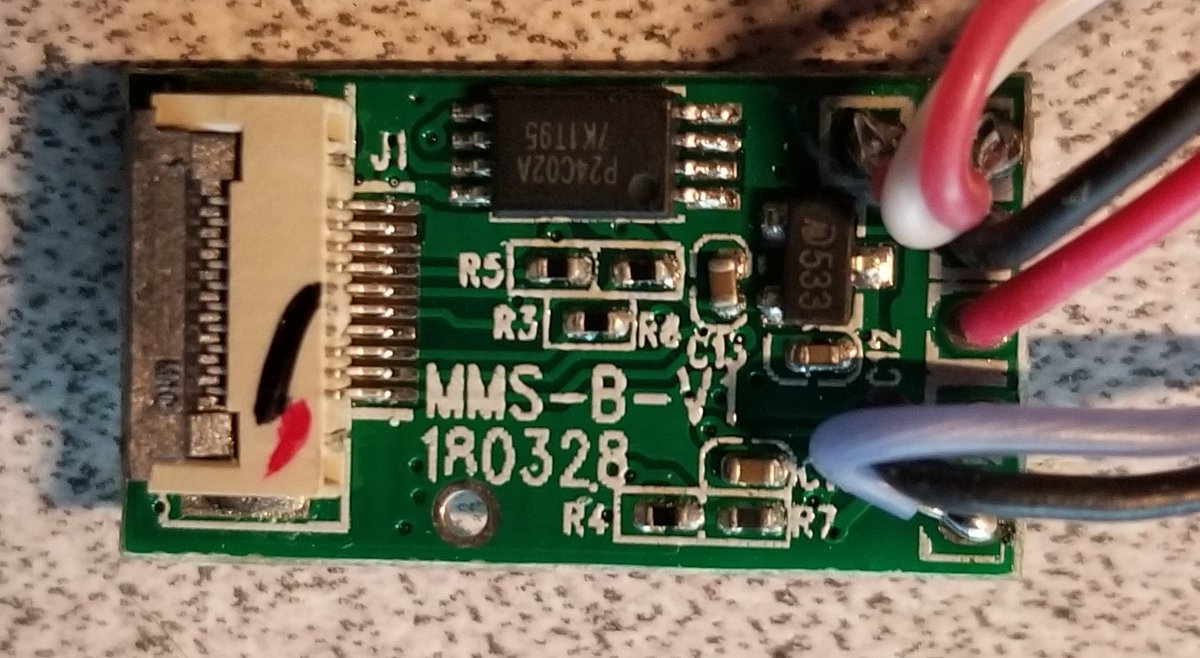
So that top PCB (the one you can access from the bottom of the lock) is actually designed according to proper security design! It& #39;s just buttons, no smarts. So you can& #39;t hack your way in from here.
It& #39;s called an MMS-B-Key--V1, it& #39;s got 5 buttons and an red/green LED.
It& #39;s called an MMS-B-Key--V1, it& #39;s got 5 buttons and an red/green LED.
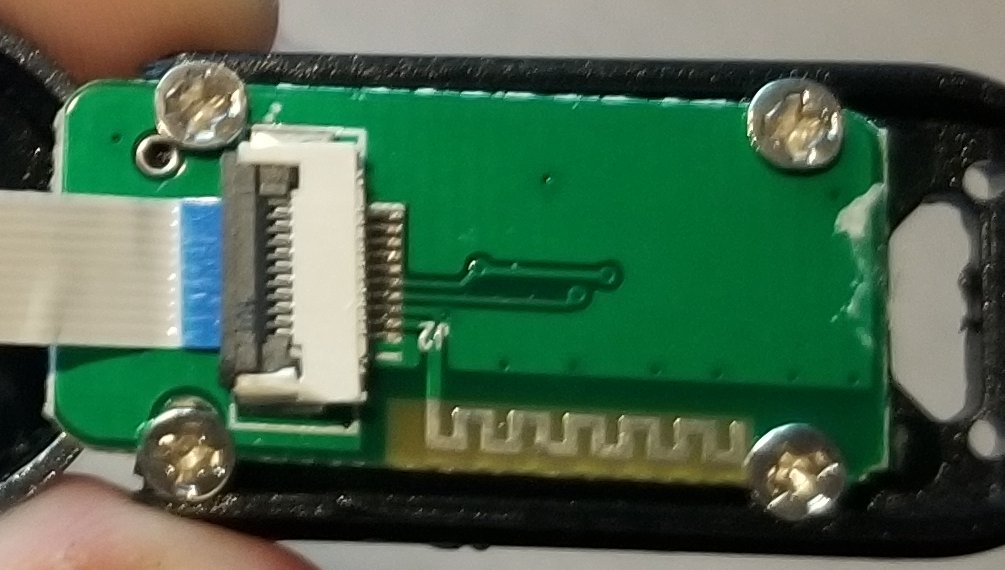
The other side shows that there& #39;s one more feature on this PCB: the bluetooth antenna! You don& #39;t usually see those on the end of a ribbon cable, but it works I guess.
The USB connector is here, on its own PCB (expensive!)
it& #39;s labeled MMS-B-USB--V1, and good news: it only has the power connectors wired up.
So you can& #39;t do any kind of USB hacking on this thing.
it& #39;s labeled MMS-B-USB--V1, and good news: it only has the power connectors wired up.
So you can& #39;t do any kind of USB hacking on this thing.
That PCB is even DOUBLE SIDED for NO REASON because apparently the designers didn& #39;t feel like saving money.
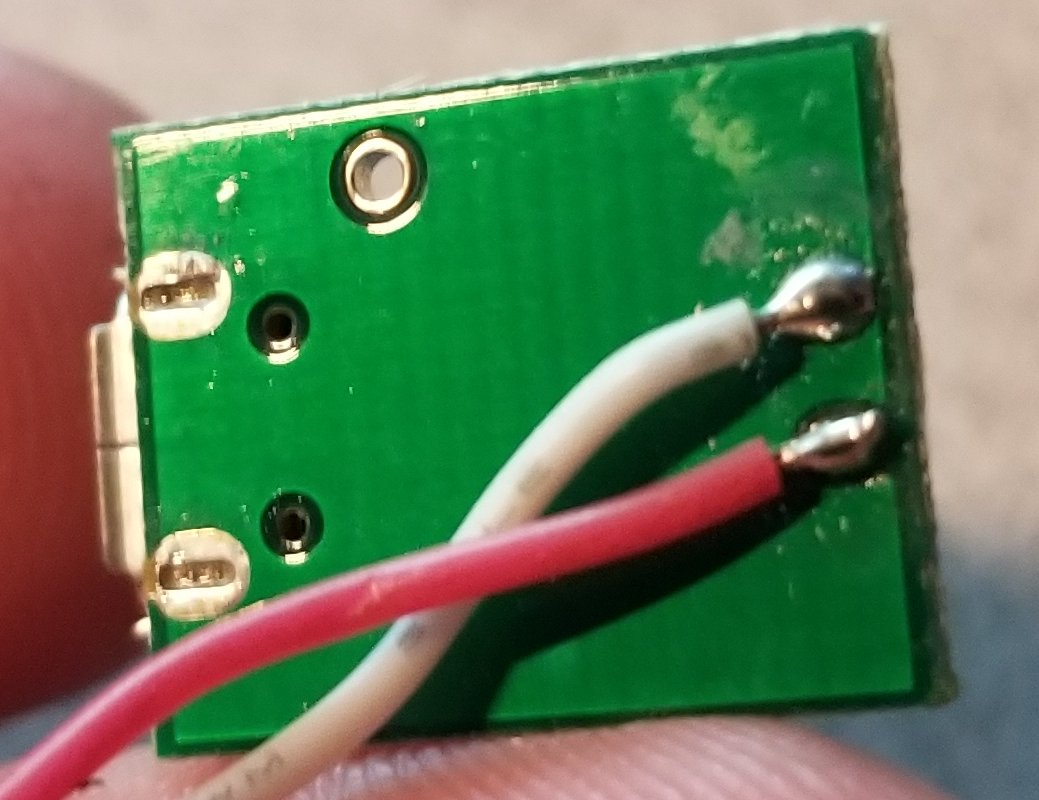
And yes, two wires: only power.
And yes, two wires: only power.
So, the main PCB is here.
It& #39;s the MMS-B-V1.
It& #39;s got 6 wires and a ribbon cable coming off it:
Ribbon cable goes to button/antenna-board, the wires go to the motor, battery, and USB board.
It& #39;s the MMS-B-V1.
It& #39;s got 6 wires and a ribbon cable coming off it:
Ribbon cable goes to button/antenna-board, the wires go to the motor, battery, and USB board.
This chip here is a Puya Semiconductor P24C02A:
That& #39;s a 256 ENTIRE BYTES i²c serial eeprom.
This has gotta be for storing shit like the key combination unlock and bluetooth pairing info, it& #39;s too tiny for anything else.
That& #39;s a 256 ENTIRE BYTES i²c serial eeprom.
This has gotta be for storing shit like the key combination unlock and bluetooth pairing info, it& #39;s too tiny for anything else.
I& #39;m not 100% sure because it has so little markings, but I think this is an HM533 voltage regulator.
It takes in the voltage from the battery or USB power and turns it into 3.3v, for the microcontroller.
It takes in the voltage from the battery or USB power and turns it into 3.3v, for the microcontroller.
Speaking of which, let& #39;s flip that PCB!
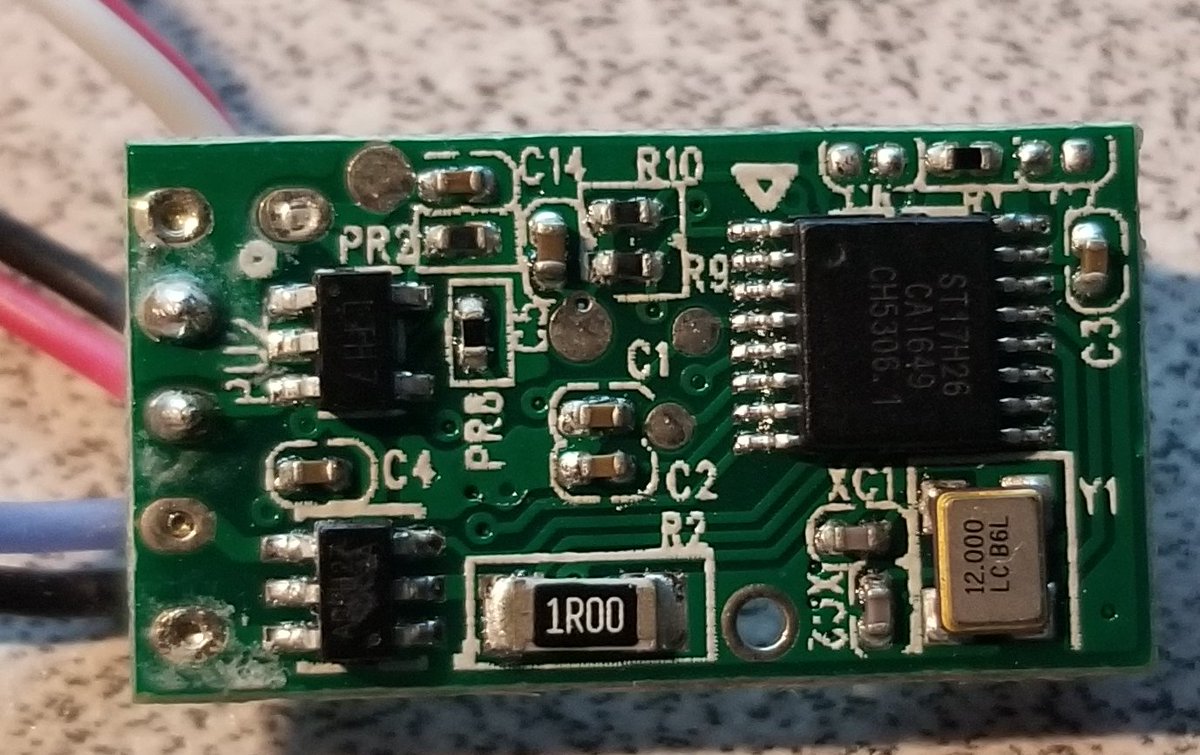
We& #39;ve got one big chip, two smaller chips, and a 12mhz oscillator/crystal.
We& #39;ve got one big chip, two smaller chips, and a 12mhz oscillator/crystal.
That chip is a ST17H26. It& #39;s a bluetooth microcontroller, with a 32bit core, 6 kilobytes of on chip ram, and 16 kilobytes of one-time-programmable program ROM.
It& #39;s got built in support for BLE and power management, so it& #39;s ideal for this sort of application.
It& #39;s got built in support for BLE and power management, so it& #39;s ideal for this sort of application.
This chip was apparently designed by Lenze, who have some weird pictures on their website
http://lenzetech.com/us/ ">https://lenzetech.com/us/"...
http://lenzetech.com/us/ ">https://lenzetech.com/us/"...
They& #39;ve also got some docs up on github, which is nice: https://github.com/17HXX/ ">https://github.com/17HXX/&qu...
I& #39;ve not been able to figure out what core they& #39;re building this on. possibly something proprietary that they designed?
seems unlikely, but there& #39;s no references to any other cores.
seems unlikely, but there& #39;s no references to any other cores.
ANYWAY back to the teardown.
Here we& #39;ve got an LTH7: that& #39;s a Linear Technology LTC4054, a Li-Ion battery charger.
You feed in up to 10v and it& #39;ll charge the battery up to full capacity (at a max current of 800mA), with optional thermal protection.
Here we& #39;ve got an LTH7: that& #39;s a Linear Technology LTC4054, a Li-Ion battery charger.
You feed in up to 10v and it& #39;ll charge the battery up to full capacity (at a max current of 800mA), with optional thermal protection.
This over here... I& #39;m not really sure.
It& #39;s an AD5?27, but I& #39;m guessing just by how this is hooked up that it& #39;s a motor driver.
It& #39;s an AD5?27, but I& #39;m guessing just by how this is hooked up that it& #39;s a motor driver.
Well, that& #39;s all the electronics parts. What& #39;s left? The motor and the mechanical parts.
This here is the padlock core.
This here is the padlock core.
So it& #39;s got a 2 wire device in the middle. It& #39;s either a small motor or a solenoid. (spoiler alert: it& #39;s a motor)
That fits into this part which holds all the PCBs and such, and yes it& #39;s entirely plastic. This is not a secure device, by any stretch of the imagination.
A battery powered drill will get you through this in like 30 seconds.
A battery powered drill will get you through this in like 30 seconds.
So, that tape on the mechanical parts was to hold two pins in, before you slide on the rest of the case that keeps them in place.
Here& #39;s the main shackle pulled out.
It& #39;s got a spring to try to push it out, and a little cut into it that& #39;s used with the locking part.
It& #39;s got a spring to try to push it out, and a little cut into it that& #39;s used with the locking part.
The two pins are not really special, they& #39;re not like cylinders of a lock, they& #39;re just pins.
And yes, the motor/solenoid is, in fact, a motor! like I said.
It& #39;s got a tiny gearbox on top, hooked up to a little peg sticking out. The peg has a metal ring around it to keep it from wearing down
It& #39;s got a tiny gearbox on top, hooked up to a little peg sticking out. The peg has a metal ring around it to keep it from wearing down
The gearbox is surprisingly complex, but I guess it has to be to be this small.
So the top bit (with the peg) has an internal set of gears, then there& #39;s the motorized part that fits inside it, right?
So the top bit (with the peg) has an internal set of gears, then there& #39;s the motorized part that fits inside it, right?
You can see from the top that there is a space between all 3 gears, they& #39;re not actually in contact with each other
Then the part the motor& #39;s shaft goes into fits in between the 3 gears, and rotates them from the middle.
So, when you trigger it to unlock, the MCU tells it to run the motor 5 rotations clockwise, then 5 rotations counterclockwise.
It& #39;s not actually going to rotate that much in practice: I suspect part of this gearing system is to let it slip once it hits too much resistance.
So what does the motor do?
Well, look down the hole where the motor goes.
See that little bit in the middle? that can slide back and forth. The motor fits in there, and can shove it to the left.
Well, look down the hole where the motor goes.
See that little bit in the middle? that can slide back and forth. The motor fits in there, and can shove it to the left.
Here& #39;s how that works: There& #39;s a spring on the right that shoves this little cylinder into the cutout on the shackle, keeping it from opening.
The motor can then rotate and push it right, allowing the (shackle) spring to push out the shackle.
The motor can then rotate and push it right, allowing the (shackle) spring to push out the shackle.
The two pins? They go here and here.
One keeps the slide from sliding too far back or two far in, and the other keeps the shackle from popping out when the motor ejects it.
One keeps the slide from sliding too far back or two far in, and the other keeps the shackle from popping out when the motor ejects it.
So, is this a good lock? No. This is a terrible lock. Even if it wasn& #39;t bluetooth, it& #39;d be a terrible lock.
But if you have to bypass one of these and you don& #39;t have the digit code or QRcode, how would you bypass it?
But if you have to bypass one of these and you don& #39;t have the digit code or QRcode, how would you bypass it?
well the obvious option would be to hack the bluetooth messages.
That sounds hard though, and it& #39;s definitely not the easiest way... they could have made it hard to do that. I didn& #39;t check.
That sounds hard though, and it& #39;s definitely not the easiest way... they could have made it hard to do that. I didn& #39;t check.
Here& #39;s the really obvious easy way:
These two secure screws under the plastic sticker.
Unscrew them or drill them out, then push down on all the mechanism. Or heck, just take a hammer to this and break the plastic.
These two secure screws under the plastic sticker.
Unscrew them or drill them out, then push down on all the mechanism. Or heck, just take a hammer to this and break the plastic.
The whole thing will just slide right out.
Once you do that, you have access to all the pins. pull them out and the whole thing falls apart. Whack it with a hammer here if it& #39;s stuck.
Once you do that, you have access to all the pins. pull them out and the whole thing falls apart. Whack it with a hammer here if it& #39;s stuck.
Alternatively, here& #39;s the thing: outer case and the parts that hold the motor in place are not magnetic. The motor (of course), IS.
So if you have a way to produce a rotating magnetic field, you could probably shove the motor into rotating from outside the case.
So if you have a way to produce a rotating magnetic field, you could probably shove the motor into rotating from outside the case.
the @LockPickingLwyr used that attack on this fingerprint padlock: https://www.youtube.com/watch?v=hQTz1OmmHYo">https://www.youtube.com/watch...
Another magnet based attack that might work if you have a big enough magnet: the slider bit isn& #39;t attracted to magnets, but the spring that holds it in place IS.
Put a big enough magnet on the side of the case and you may pull the magnet down enough that you can open the shackle
Put a big enough magnet on the side of the case and you may pull the magnet down enough that you can open the shackle
Interestingly, the QRCode is printed with a thermal printer, so after a little while of screwing around with this thing... it got warm enough to erase itself.
If you want to get into more esoteric computery hacks, along with the QRCode (that& #39;s explicitly the same as knowing the combination), there& #39;s also a permanently etched serial number.
Is the QRCode linked to the serial number? quite possibly.
Is the QRCode linked to the serial number? quite possibly.
so you might be able to figure out the unlocking code from the serial number with enough reverse engineering.
BTW that QR code just resolves to a URL containing the unlock code listed below (the GTS160118986 one, not the serial number)
they did at least obfuscate the java code used in the app.
that& #39;s not gonna stop people from hacking it, but it makes it not instantly easy.
that& #39;s not gonna stop people from hacking it, but it makes it not instantly easy.
and it does seem to use some actual encryption. There& #39;s RSA key functions and such!
unfortunately it seems there& #39;s also a lot of keys/passwords embedded in the app, so... yeah.
unfortunately it seems there& #39;s also a lot of keys/passwords embedded in the app, so... yeah.
BTW this thing DOES have to talk to the remote Klic server.
I think you can still unlock a lock without talking to the server, IF you have it already added onto your phone?
but that just delays when your lock will get bricked.
I think you can still unlock a lock without talking to the server, IF you have it already added onto your phone?
but that just delays when your lock will get bricked.
so keep good track of the back-up number. That& #39;ll still work if the servers die, since you can always recharge it from the USB port and then type in the code.
well, until the battery dies.
well, until the battery dies.
I really don& #39;t know and I& #39;m not sure I want to know why the app has game code from Tencent, creators of WeChat and co-owners of Fortnite
anyway the app is surprisingly complicated and I didn& #39;t do any bluetooth capturing while I had this thing in a working condition, so I& #39;m probably not gonna hack the protocol today.
I got this thing at walmart for 20$ a while back, and just recently got around to tearing it down to figure out how it worked.
If you want one: https://www.walmart.com/ip/tzumi-Klic-Smart-Lock-Bluetooth-App-Driven-Padlock/634382287">https://www.walmart.com/ip/tzumi-...
If you want one: https://www.walmart.com/ip/tzumi-Klic-Smart-Lock-Bluetooth-App-Driven-Padlock/634382287">https://www.walmart.com/ip/tzumi-...
and if you liked this thread and would like to donate a dollar or two to future teardowns, my ko-fi is here: https://ko-fi.com/fooneturing ">https://ko-fi.com/fooneturi...
and if you want more, my (not actually complete, but it& #39;s a good start) list of teardown threads is over here on my wiki:
#Teardown_Threads">https://floppy.foone.org/w/Reverse_Engineering_documentation #Teardown_Threads">https://floppy.foone.org/w/Reverse...
#Teardown_Threads">https://floppy.foone.org/w/Reverse_Engineering_documentation #Teardown_Threads">https://floppy.foone.org/w/Reverse...
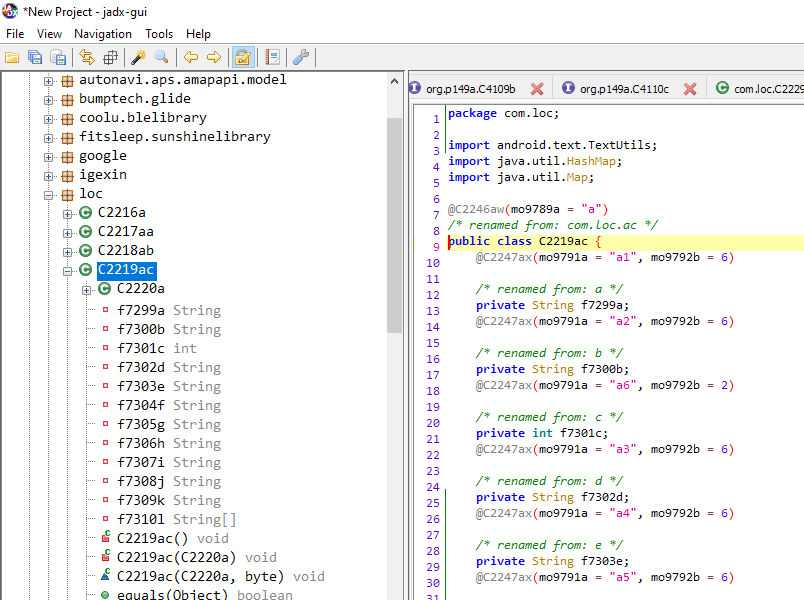
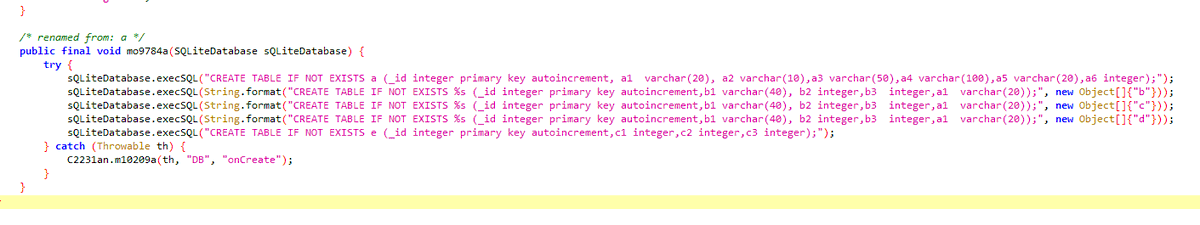
do you ever think back about the old days, when your padlock didn& #39;t need an SQL database?
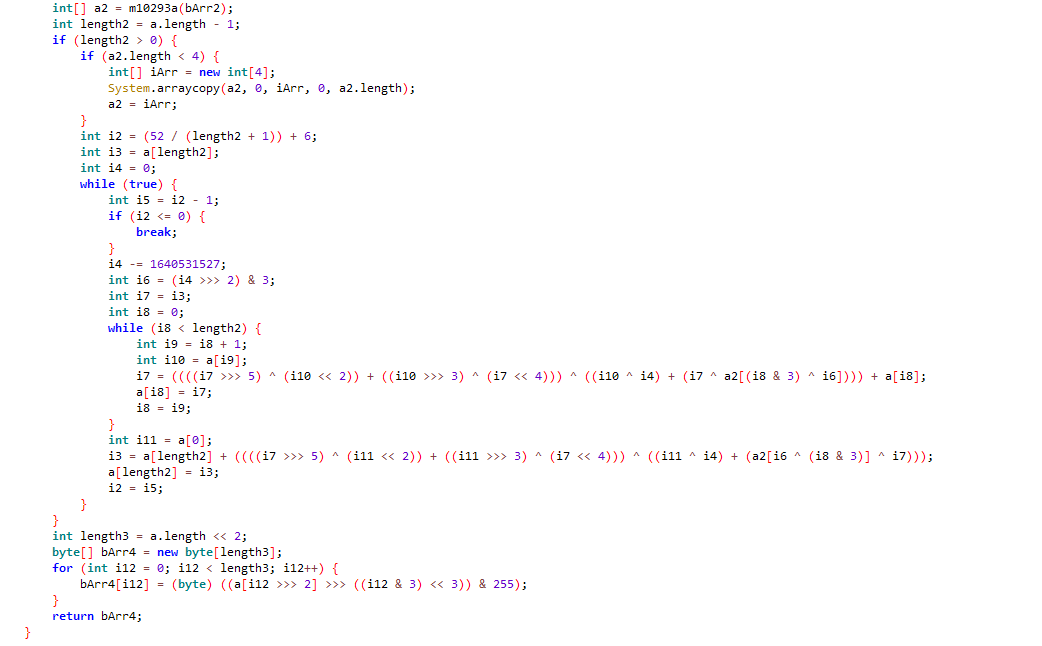
looks like it& #39;s a form of TEA (hopefully XTEA):
https://en.wikipedia.org/wiki/Tiny_Encryption_Algorithm">https://en.wikipedia.org/wiki/Tiny...
https://en.wikipedia.org/wiki/Tiny_Encryption_Algorithm">https://en.wikipedia.org/wiki/Tiny...
TEA would make sense for this kind of application. You can run TEA into a very small microcontroller, like the one that powers this thing.
Also @rdzien alerted me that @thelocklab has done a video on this lock! https://www.youtube.com/watch?v=k6ra0yPlY4k">https://www.youtube.com/watch...
and it turns out @intrd already hacked this lock over bluetooth: https://twitter.com/intrd/status/1308161954524082176">https://twitter.com/intrd/sta...
I love this shit.
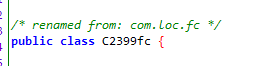
This class is totally obfuscated! I& #39;ll never be able to find out what it was originally called! Damn you!
This class is totally obfuscated! I& #39;ll never be able to find out what it was originally called! Damn you!

 Read on Twitter
Read on Twitter