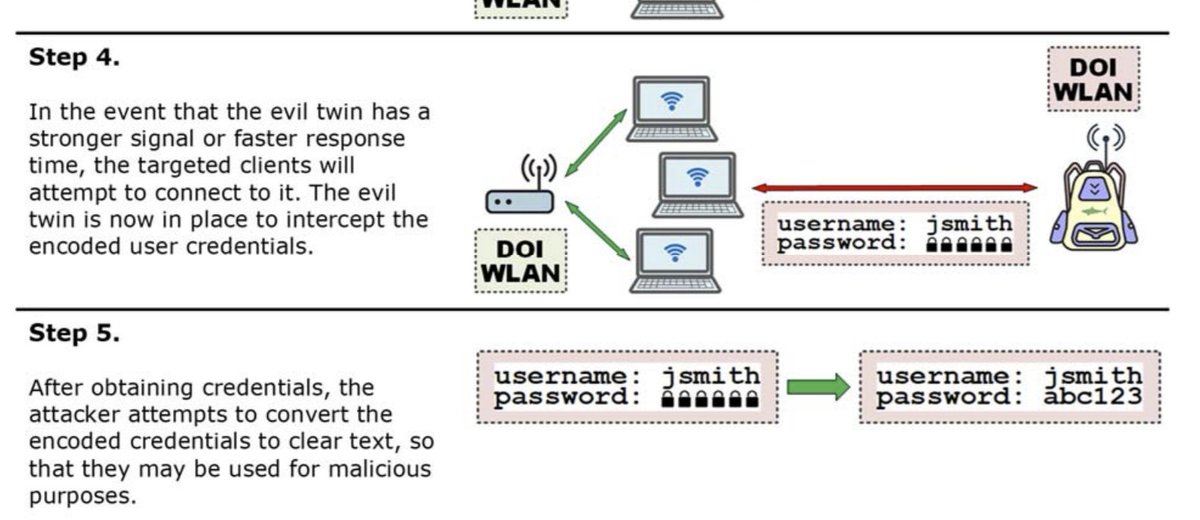
The IG for the Department of the Interior went around the agency cracking their weak WiFi: https://www.doioig.gov/sites/doioig.gov/files/FinalAudit_WirelessNetworkSecurity_Public.pdf
It& #39;s">https://www.doioig.gov/sites/doi... fantastic to see a technically competent IG focus on empirical security over compliance. But it& #39;s also an example of the USG& #39;s misplaced focus on networks. 1/5
It& #39;s">https://www.doioig.gov/sites/doi... fantastic to see a technically competent IG focus on empirical security over compliance. But it& #39;s also an example of the USG& #39;s misplaced focus on networks. 1/5
A core finding in the report is that the DOI& #39;s IG was able to decrypt employee credentials. That& #39;s bad! In response, the IG recommends tightening up WiFi security.
But the real problem is that WiFi security is even important to protect credentials in the first place! 2/5
But the real problem is that WiFi security is even important to protect credentials in the first place! 2/5
Organizations can use WiFi and enterprise single sign-on (SSO) without exposing credentials to attackers who can see wireless traffic.
It means having people sign in at the application layer (using HTTPS), rather than tightly coupling login to the network. It& #39;s very common. 3/5
It means having people sign in at the application layer (using HTTPS), rather than tightly coupling login to the network. It& #39;s very common. 3/5
The @DOIOIG wisely references the principle of least privilege, but focuses on network segmentation rather than an unprivileged network.
It& #39;s a missed opportunity by a tech-savvy IG - but consistent with the USG& #39;s overwhelming, misplaced policy focus on network security. 4/5
It& #39;s a missed opportunity by a tech-savvy IG - but consistent with the USG& #39;s overwhelming, misplaced policy focus on network security. 4/5
You can securely run an organization whose services can be safely accessed from any network - including open WiFi! We Have The Technology.
But in the USG, in 2020, an IG would still appear radical for asking an agency to *rely less* on secure WiFi. So the cycle continues. 5/5
But in the USG, in 2020, an IG would still appear radical for asking an agency to *rely less* on secure WiFi. So the cycle continues. 5/5
Also, shoutout to @Federal_IT at @Nextgov for taking the time to cover such a wonky IG report:
https://nextgov.com/cybersecurity/2020/09/interior-ig-team-used-evil-twins-and-200-tech-hack-department-wi-fi-networks/168521/
Sometimes">https://nextgov.com/cybersecu... I think I& #39;m the only one out there reading through IG reports for fun and dysfunctional tales. ;) IG reports are great and need more coverage!
https://nextgov.com/cybersecurity/2020/09/interior-ig-team-used-evil-twins-and-200-tech-hack-department-wi-fi-networks/168521/
Sometimes">https://nextgov.com/cybersecu... I think I& #39;m the only one out there reading through IG reports for fun and dysfunctional tales. ;) IG reports are great and need more coverage!

 Read on Twitter
Read on Twitter