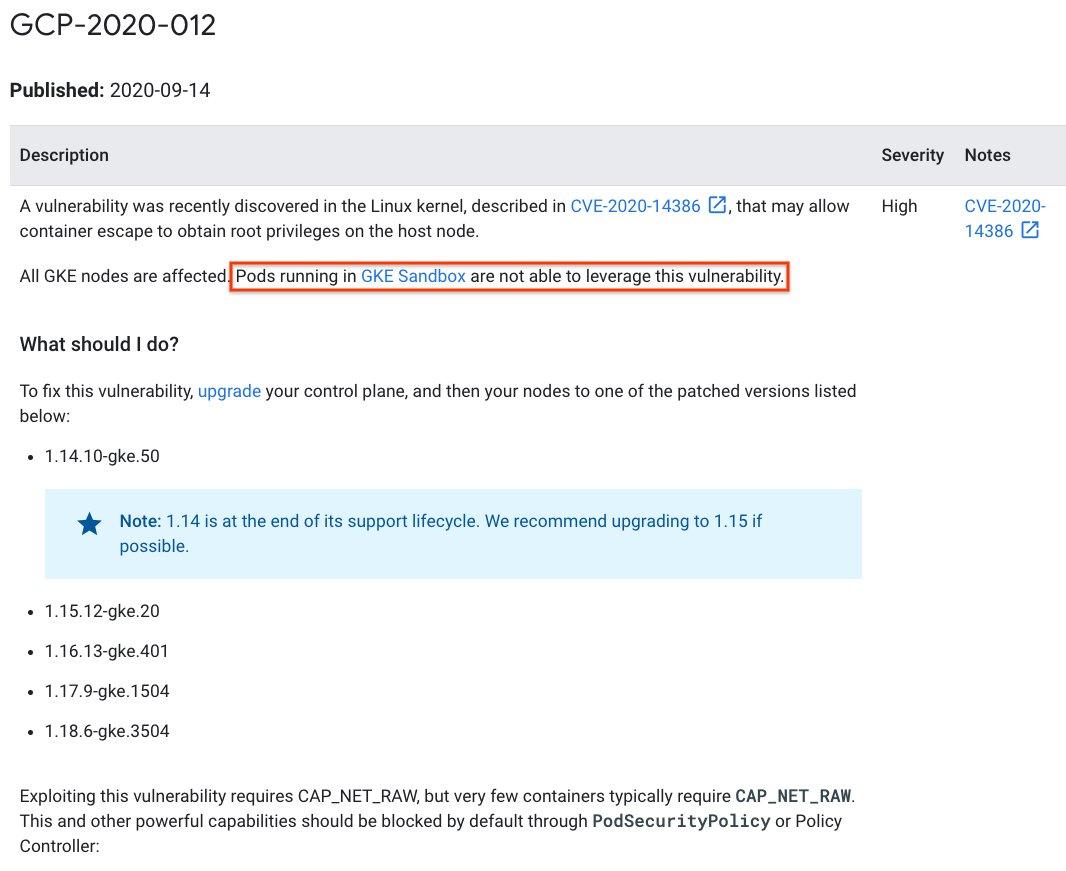
Hard work gets paid off. #gVisor successfully protected #GKE users from CVE-2020-14386. This is the first case GKE Sandbox after going in production preventing attackers from leveraging a vulnerability in the Linux kernel for container escape to get root privileges. (1/3)
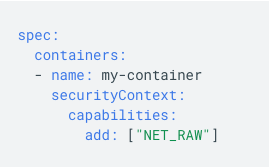
The team did two things. 1) At product design level, we dropped CAP_NET_RAW to reduce the attack surface. GKE Sandbox users need to explicitly add the NET_RAW capability to the container& #39;s security context to create raw sockets. Least privilege. (2/3)
https://cloud.google.com/kubernetes-engine/docs/concepts/sandbox-pods">https://cloud.google.com/kubernete...
https://cloud.google.com/kubernetes-engine/docs/concepts/sandbox-pods">https://cloud.google.com/kubernete...
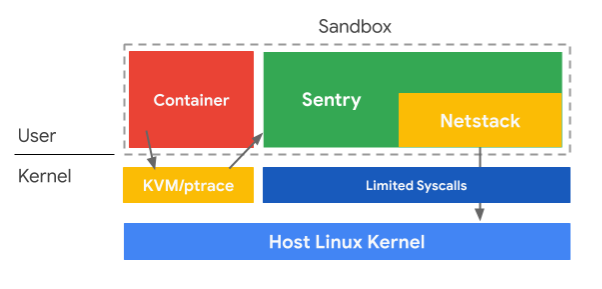
2) Even if users enabled CAP_NET_RAW, the requests go through Sentry (Linux) & Netstack (TCP/IP) both written in Go & run in userland on top of tight seccomp filters. Multiple layers of defense. Details on gVisor& #39;s security design at below. (3/3)
https://gvisor.dev/blog/2019/11/18/gvisor-security-basics-part-1/">https://gvisor.dev/blog/2019...
https://gvisor.dev/blog/2019/11/18/gvisor-security-basics-part-1/">https://gvisor.dev/blog/2019...

 Read on Twitter
Read on Twitter