Initial phish comes from an already compromised user they send you a DM along the lines of "{victim} this is probably you here... {phishing_website} take it down because it is a shame".
So I decided to investigate
Phishing URL: hxxps://smieszne-pl.eu
SSL from @letsencrypt issued on the 7th September at 5:23pm, serial number is 0420a48f9224c934cfc5a950665992b7c15c.
Domain appears to be clean on VT, so does the server& #39;s IP
91.212.150.51 ( https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇷🇺" title="Flagge von Russland" aria-label="Emoji: Flagge von Russland">) appears to sub-rented servers from NForce B.V.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇷🇺" title="Flagge von Russland" aria-label="Emoji: Flagge von Russland">) appears to sub-rented servers from NForce B.V.
SSL from @letsencrypt issued on the 7th September at 5:23pm, serial number is 0420a48f9224c934cfc5a950665992b7c15c.
Domain appears to be clean on VT, so does the server& #39;s IP
91.212.150.51 (
Under the name of "Private Internet Hosting LTD" according to @BgpView the company in question is based in Belize by Alexx Person.
When you visit the URL you get sent to a facebook-like login page (very poorly made and looks like the old version). Posts the form data to /new.php
When you visit the URL you get sent to a facebook-like login page (very poorly made and looks like the old version). Posts the form data to /new.php
After putting their credentials in the victim gets redirected to hxxps://o2-online.pl/?miasta=biedy hosted on the same server. SSL issued by @letsencrypt on 5th of August at 8:51pm, with the serial number 047b19837f1dfd85792a97804f4f196192b8. This is where it gets interesting
Using @urlscanio to scan this URL shows us that there is an outbound link to hxxps://whos.amung.us/stats/mr5cvu849y/, turns out its the statistics for the website& #39;s clicks  https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="😅" title="Lächelndes Gesicht mit offenem Mund und Angstschweiß" aria-label="Emoji: Lächelndes Gesicht mit offenem Mund und Angstschweiß">, note scammer don& #39;t include the stats url in plaintext in your src code for the site.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😅" title="Lächelndes Gesicht mit offenem Mund und Angstschweiß" aria-label="Emoji: Lächelndes Gesicht mit offenem Mund und Angstschweiß">, note scammer don& #39;t include the stats url in plaintext in your src code for the site.
You can bypass the login "verification" bypass entering an invalid login and then entering random email & password.
Looking at the stats page it appears this scam has been up for a couple of days, around 100 clicks at the peaks
Looking at the stats page it appears this scam has been up for a couple of days, around 100 clicks at the peaks
And uses scripts from hxxp://waust.at/d.js for click monetization and audience discovery, and pings information back to whos[.]amung[.]us
Domain: waust[.]at
Registrar: GoDaddy
Domain: o2-online[.]pl
Registrar: AZ[.]pl Sp. z.o.o.
Domain: waust[.]at
Registrar: GoDaddy
Domain: o2-online[.]pl
Registrar: AZ[.]pl Sp. z.o.o.
Domain: smieszne-pl[.]eu
Registrar: AZ[.]pl Sp. z.o.o.
Looking further into the server hosting this phishing
scam [91.212.150.51], 14 phishing domains hosted on this server seen via @securitytrails
Registrar: AZ[.]pl Sp. z.o.o.
Looking further into the server hosting this phishing
scam [91.212.150.51], 14 phishing domains hosted on this server seen via @securitytrails

 Read on Twitter
Read on Twitter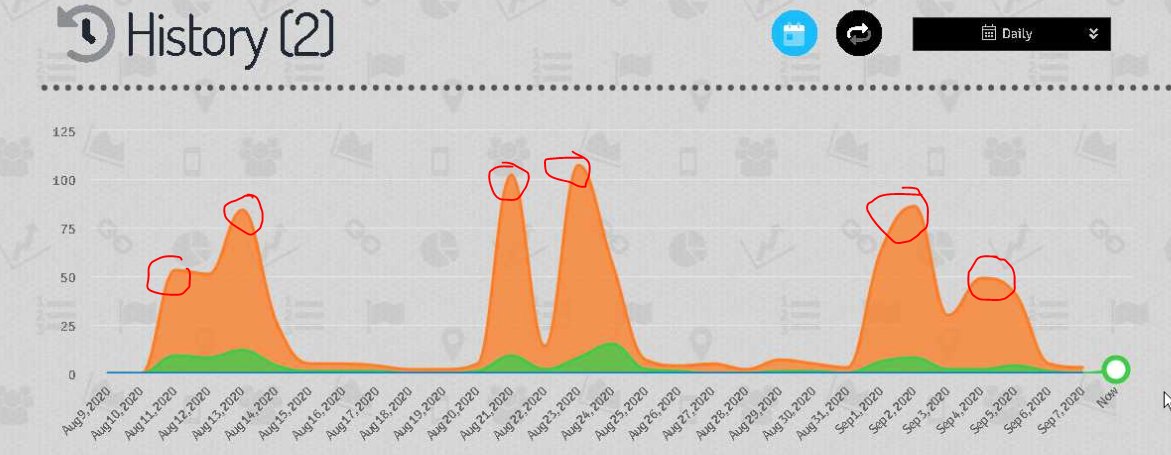
![And uses scripts from hxxp://waust.at/d.js for click monetization and audience discovery, and pings information back to whos[.]amung[.]us Domain: waust[.]atRegistrar: GoDaddyDomain: o2-online[.]plRegistrar: AZ[.]pl Sp. z.o.o. And uses scripts from hxxp://waust.at/d.js for click monetization and audience discovery, and pings information back to whos[.]amung[.]us Domain: waust[.]atRegistrar: GoDaddyDomain: o2-online[.]plRegistrar: AZ[.]pl Sp. z.o.o.](https://pbs.twimg.com/media/EhaLLYuXYAkEFZv.jpg)


