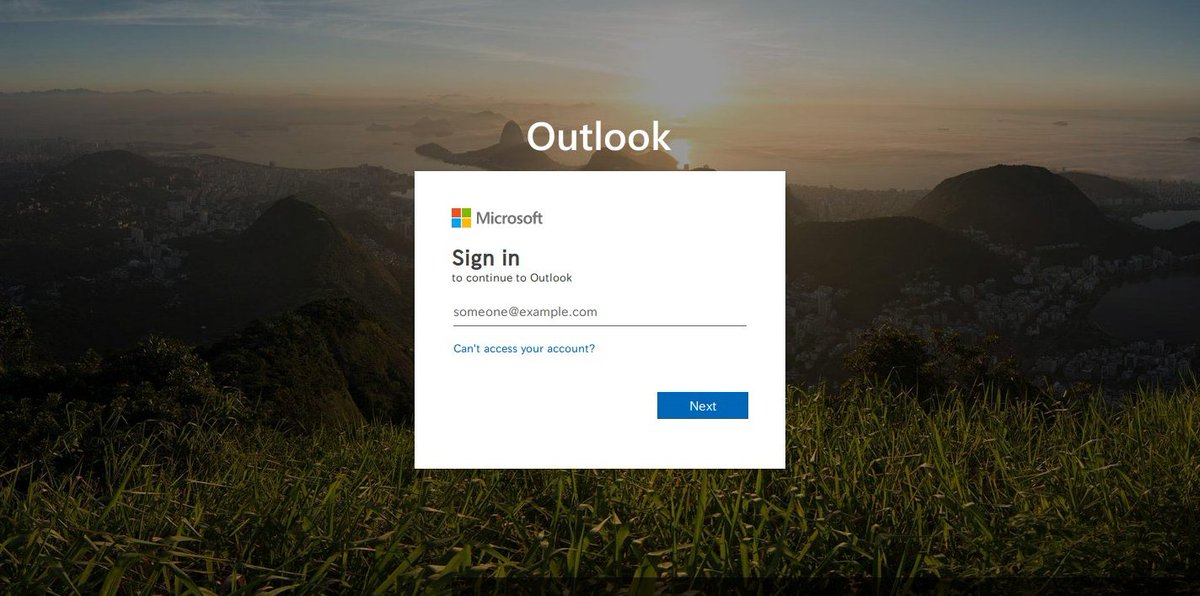
Outlook phishing page hosted by Microsoft: https://sharepointmxrecordpos1.z13.web.core...\.windows.net/
And even "sharepoint" is in the subdomain...
Clear example of how much MS dgaf about not only "random" phishing pages they host, but even ones likes this...
cc @SwiftOnSecurity
And even "sharepoint" is in the subdomain...
Clear example of how much MS dgaf about not only "random" phishing pages they host, but even ones likes this...
cc @SwiftOnSecurity
After entering the credentials, the victim will get redirected to this file: https://whitehouse.gov/wp-content/uploads/2020/02/2020-Economic-Report-of-the-President-WHCEA.pdf">https://whitehouse.gov/wp-conten...
The entered credentials are sent to: https://zankouchlcken[.]com/img/new/pos1/process.php
Just go one level up...
Hey @Namecheap, what about finally nuking this?
cc @olihough86
Just go one level up...
Hey @Namecheap, what about finally nuking this?
cc @olihough86
https://twitter.com/invirtutedei/status/1298747226542481408
Still">https://twitter.com/invirtute... online... Soon 3 months.
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="😂" title="Gesicht mit Freudentränen" aria-label="Emoji: Gesicht mit Freudentränen">
Still">https://twitter.com/invirtute... online... Soon 3 months.
Another one: https://sharepointmxrecxdrroy2.z13.web.core...\.windows.net/
Online for more than 50 hours already...
Online for more than 50 hours already...

 Read on Twitter
Read on Twitter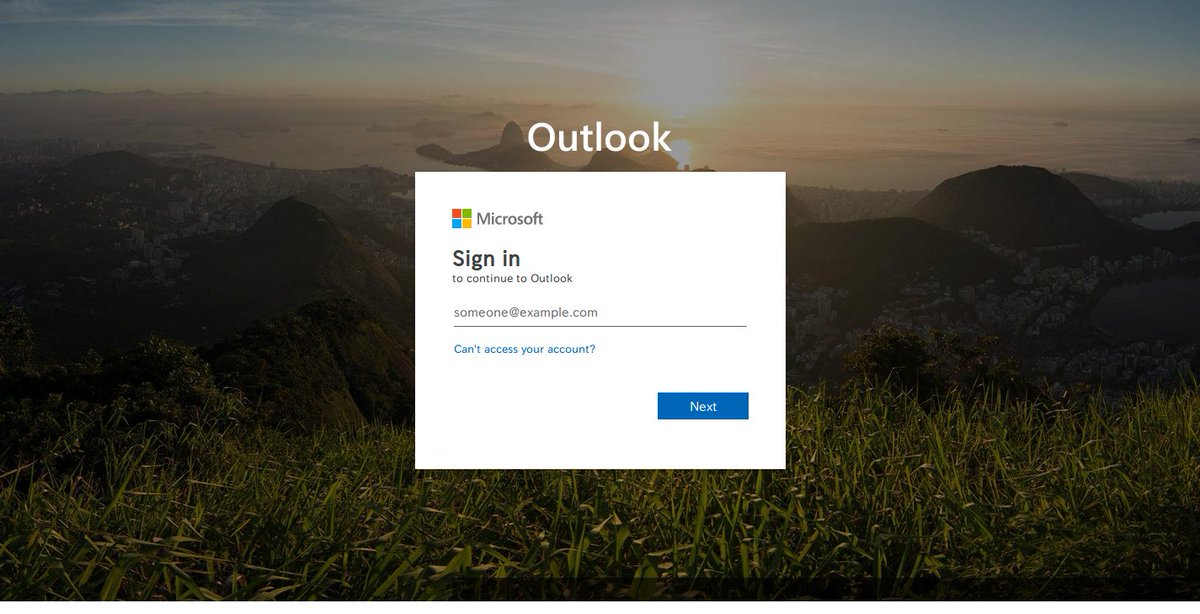

![The entered credentials are sent to: https://zankouchlcken[.]com/img/new/pos1/process.phpJust go one level up...Hey @Namecheap, what about finally nuking this?cc @olihough86 The entered credentials are sent to: https://zankouchlcken[.]com/img/new/pos1/process.phpJust go one level up...Hey @Namecheap, what about finally nuking this?cc @olihough86](https://pbs.twimg.com/media/EgXtvkjXsAU1DCB.png)