OK Kids, I’m finally going to read the Dept of Home Affairs’ “Protecting Critical Infrastructure and Systems of National Significance Consultation Paper” that was released yesterday, and maybe tweet a few bits. https://www.homeaffairs.gov.au/reports-and-publications/submissions-and-discussion-papers/protecting-critical-infrastructure-systems">https://www.homeaffairs.gov.au/reports-a...
Some background: This stuff is intended to build upon last week’s new Cyber Security Strategy, which I wrote about here: “The disappointment of Australia’s new cybersecurity strategy” https://www.zdnet.com/article/the-disappointment-of-australias-new-cybersecurity-strategy/">https://www.zdnet.com/article/t...
But first I’ll read @dobes’ new story from yesterday: “Home Affairs proposes cyber regulations and legal immunities to respond to threats” https://www.zdnet.com/article/home-affairs-proposes-cyber-regulations-and-legal-immunities-to-respond-to-threats/">https://www.zdnet.com/article/h...
Snerk. “The closing date for submissions is 5pm AEDT September 16, the paper said, however, daylight savings does not begin until October 4.”
The term is “daylight saving” but I’ll take that up with the Relevant People at a later date.
The term is “daylight saving” but I’ll take that up with the Relevant People at a later date.
A key part of this is some sort of near real time threat intelligence sharing, something that has supposedly been “coming soon” for approximately a billion years now.
Right. On to the actual document. “Protecting Critical Infrastructure and Systems of National Significance Consultation Paper”. It has a nice cover and goes for 34 pages including all the fluff.
“All Australians rely on critical infrastructure to deliver essential services that are crucial to our way of life, such as electricity, communications, transport and banking.” And here’s a picture.
“Accordingly, Government will introduce an enhanced regulatory framework, building on existing requirements under the Security of Critical Infrastructure Act 2018 (the Act).”
To read later, here’s the Security of Critical Infrastructure Act 2018. http://www.austlii.edu.au/cgi-bin/viewdb/au/legis/cth/num_act/socia2018398/">https://www.austlii.edu.au/cgi-bin/v...
“The Government’s commitment to the continued prosperity of our economy and businesses is unwavering,” the discussion paper says, not quite sure if it’s a policy proposal or an election brochure.
Right, on page 7 we’re finally getting to some substance, summarising what people told Home Affairs during the development of the Cyber Security Strategy. (From now on, just “the strategy”).
“Government heard that Australia’s critical systems are facing a worsening threat environment and the nation needs to address vulnerabilities in supply chain security, control systems and operational technology.”
The Act currently covers the electricity, gas, water, and ports sectors. The discussion paper notes that this should be expanded to some other things, though what they are isn’t specified yet. I read on...
On page 9 we finally get a statement of the objective. “The primary objective of the proposed enhanced framework is to protect Australia’s critical infrastructure from all hazards, including the dynamic and potentially catastrophic cascading threats enabled by cyber attacks.”
IT AIN’T JUST ABOUT THE CYBERS, KIDS!
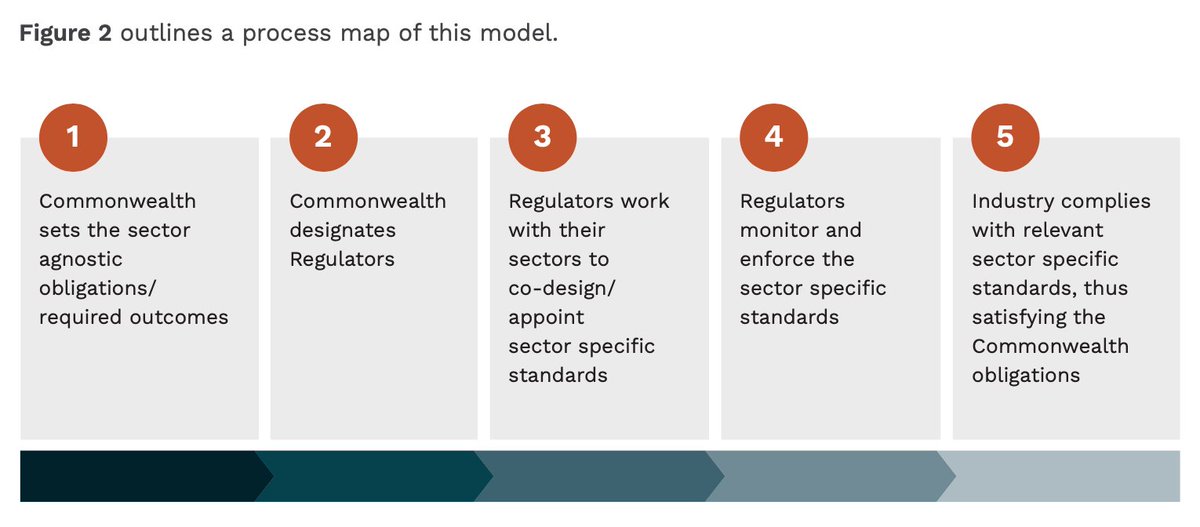
“Government has agreed that the proposed enhanced framework will apply to an expanded set of critical infrastructure sectors, comprising of three key elements,” which are in the screenshot.
For mine, number 2 looks like the fun bit. “Enhanced cyber security obligations” include “the ability for Government to request information to contribute to a near real-time national threat picture”. So what information, and in what circumstances? Many questions there.
At least it says “request”.
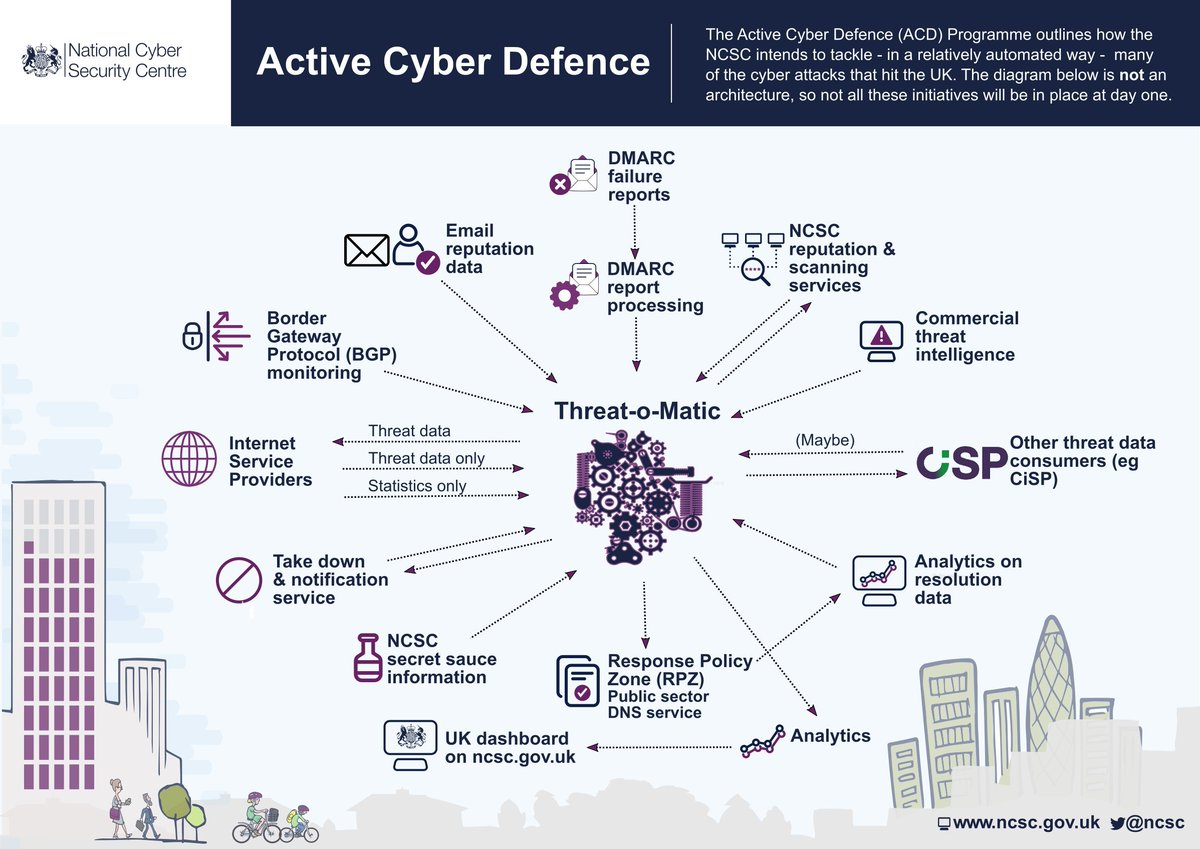
I should mention that the UK’s active cyber defence program includes the idea of building a magic real time Threat-o-Matic — yes that’s what they’re calling it — and I’m imagining this will be Australia’s version. This is very much “a work in progress”.
I also hear on the grapevine* that while NCSC has had enormous success with their DNS work and DMARC and route sanitisation, building the Threat-o-Matic is proving to be more complicatederplex than you might think.
* Note weasel words.
* Note weasel words.
Seriously, who wouldn’t want a Cyber Threat-o-Matic? https://twitter.com/JackAubrey/status/1293721132277698561">https://twitter.com/JackAubre...
Anyway, from page 11 onwards we have an exposition of what the government wants our views on. The fun bit of these is working out what they’ve already decided and therefore won’t ask us about. That requires some decoding. Anyway, here’s the questions...
“Who will the enhanced framework apply to?” They’re looking at including:
• Banking and finance
• Communications
• Data and the Cloud
• Defence industry
• Education, research and innovation
• Energy
• Food and grocery
• Health
• Space
• Transport
• Water.
• Banking and finance
• Communications
• Data and the Cloud
• Defence industry
• Education, research and innovation
• Energy
• Food and grocery
• Health
• Space
• Transport
• Water.
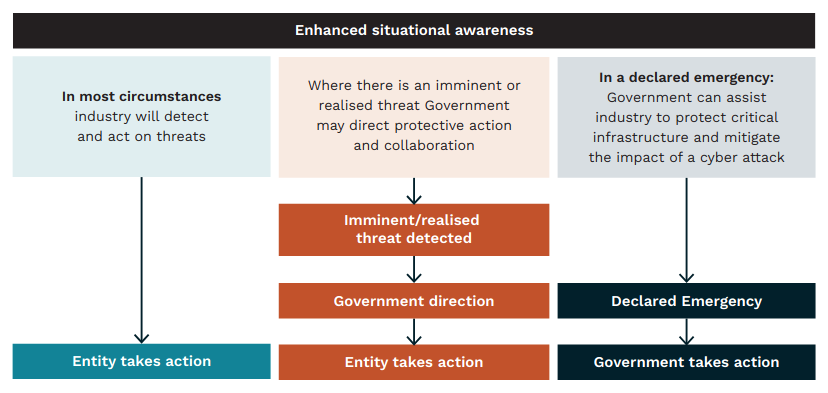
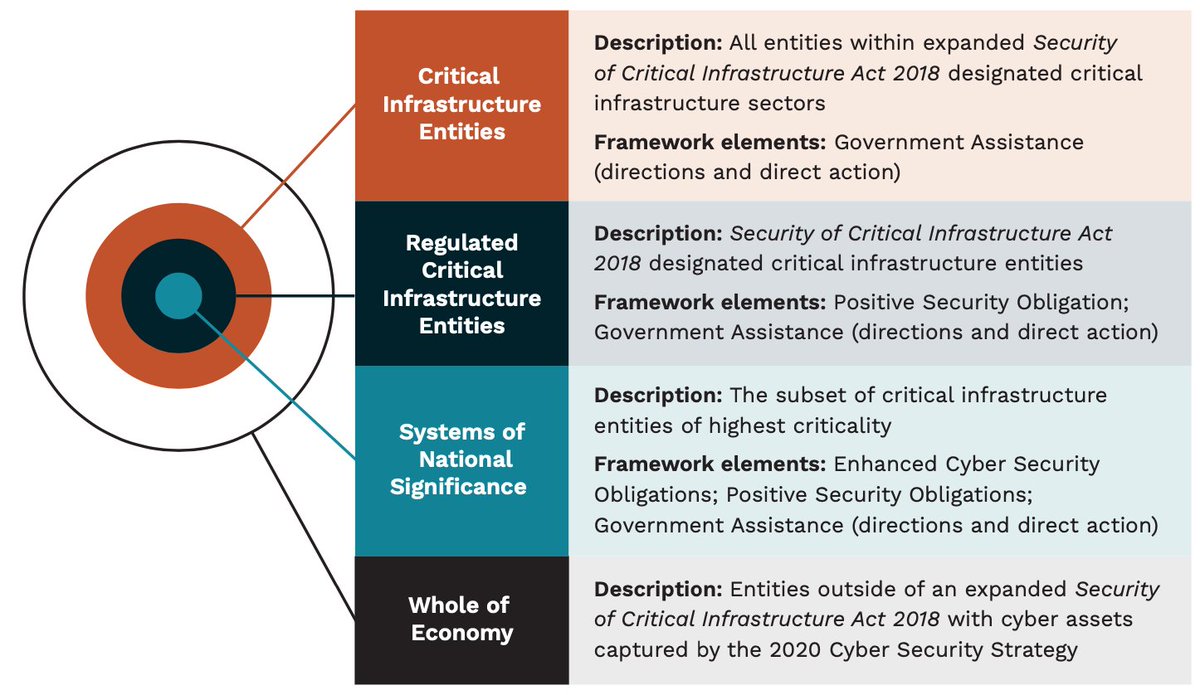
“Which entities will be covered?” There will be four entity levels, and there’s a handy diagram which already has a target on it.
“We need to work with you to map and identify what should become a ‘critical infrastructure entity’, a ‘regulated critical infrastructure entity’ subject to the Positive Security Obligation and the small subset of entities that are the most important to the nation.”
“In developing the criteria for assessing which entities will be covered by the reforms we will be guided by the principles of simplicity, transparency, accuracy and stability,” so it’s a novel approach.
Hahahaha democracy yeah right are you new here? :) https://twitter.com/TimWattsMP/status/1293722886151184385">https://twitter.com/TimWattsM...
“Government-Critical Infrastructure collaboration to support uplift” is certainly a series of words. It seems to be about how this threat info sharing will work, and how it connects to the existing Trusted Information Sharing Network (TISN, not TISM).
Now the discussion paper goes into more detail on what those three initiatives might entail, and asks whether they cover the right things, and how much of this stuff is already a thing in your sector. Quite a few pages on each one, so I’ll tweet the heading and then a few notes.
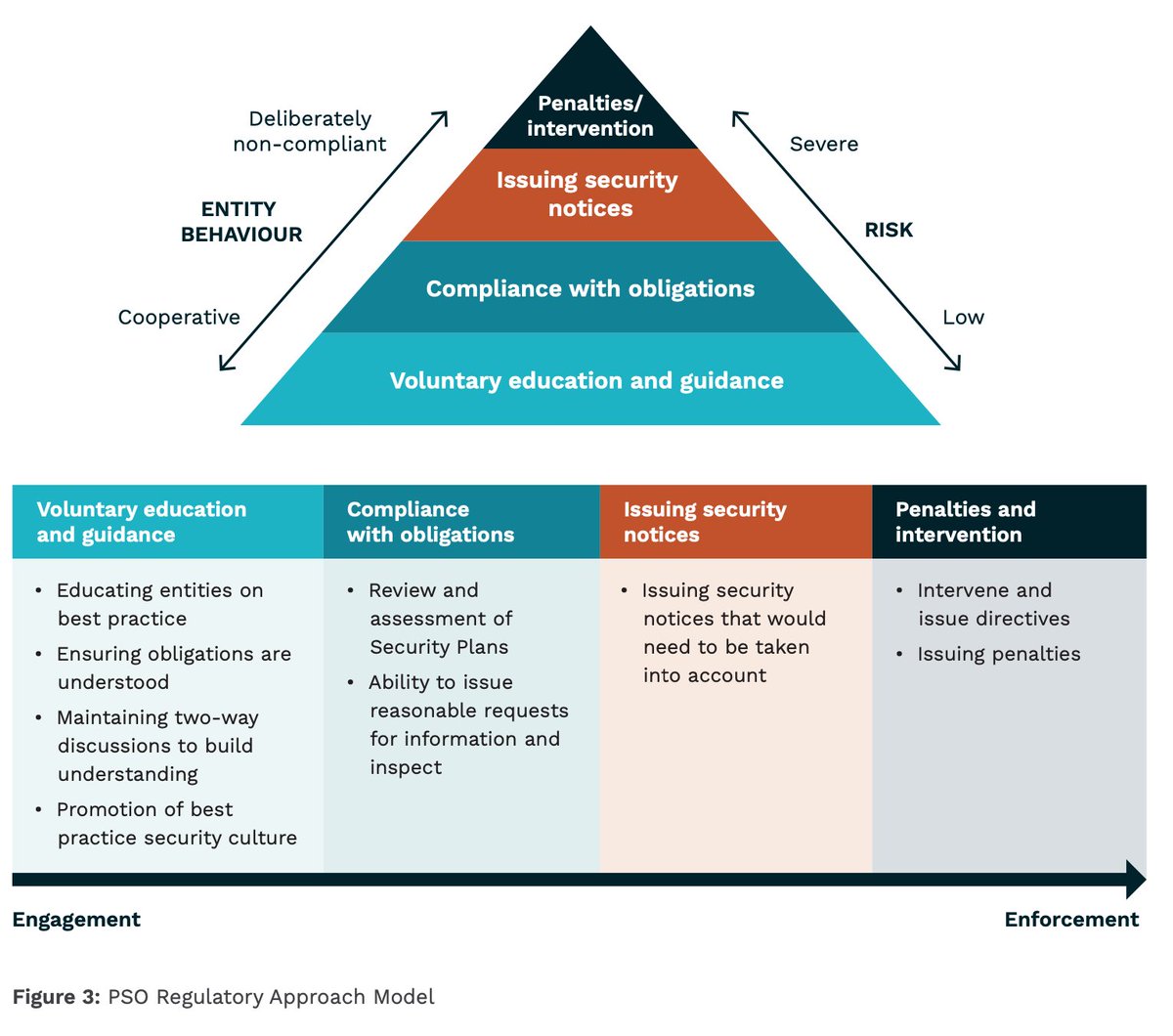
Initiative 1: Positive Security Obligation (PSO)
“A a minimum, owners and operators of critical infrastructure should be legally obliged to manage risks that may impact business continuity and Australia’s economy, security and sovereignty.”
“A a minimum, owners and operators of critical infrastructure should be legally obliged to manage risks that may impact business continuity and Australia’s economy, security and sovereignty.”
“We consider that the new framework should clearly set out in legislation the high-level security obligations that critical infrastructure entities should meet.”
This isn’t just cybers, but also physical security, personnel security, and supply chain security. They keep mentioning an “all-hazards” approach.
(This law will be very difficult to write, but odds-on they’ll want it by Christmas. Before Dutton is sacked, anyway.)
(This law will be very difficult to write, but odds-on they’ll want it by Christmas. Before Dutton is sacked, anyway.)
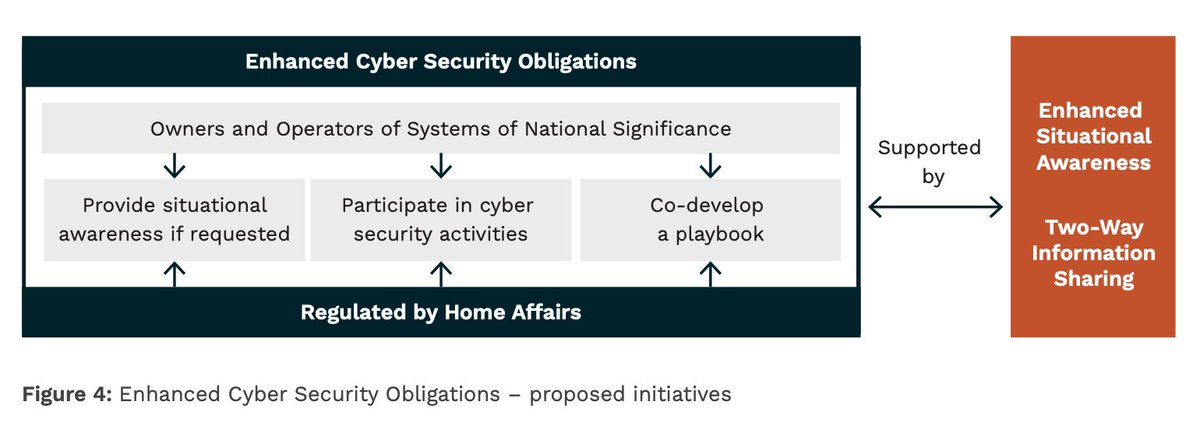
“Initiative 2: Enhanced Cyber Security Obligations”
Yes, this sounds more and more like the Threat-o-Matic, but with very little programmatic specificity. That’s fine, this is a policy document not an implementation plan.
Yes, this sounds more and more like the Threat-o-Matic, but with very little programmatic specificity. That’s fine, this is a policy document not an implementation plan.
Not straight away, anyway.
“Some entities will already have a mature capability allowing them to voluntarily provide Government with the information required and receive actionable, aggregated information in return.”
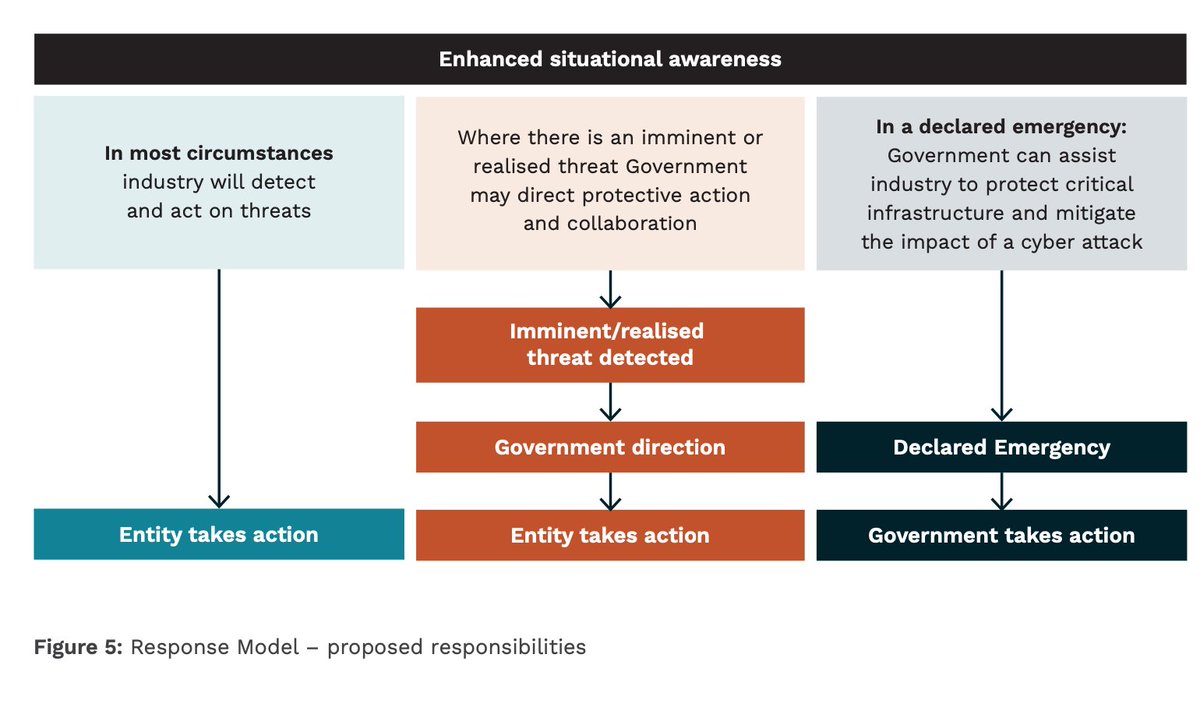
“Initiative 3: Cyber assistance for entities”
This is the bit about “the capability to disrupt and respond to threats” and distinguished between a “significant impact” and a “declared emergency”.
This is the bit about “the capability to disrupt and respond to threats” and distinguished between a “significant impact” and a “declared emergency”.
As mentioned before, the government directs the entities in the first level, and in emergencies the government takes direct action. Lots and lots of scope for having fun with definitions there!
And the rest is just to say that submissions close on 16 Sep, and then there’s a timeline — which conveniently leaves out the legislative timetable. But then we don’t do Parliament these days.
“Prompt action is required to ensure Australia is in a strong position to address all threats to our critical infrastructure. Legislative amendments to the Act will be developed, informed by cross- sectoral consultation on the reforms.”
Yes, everything always has to be done quickly quickly quickly quickly quickly because it took 11 months to deliver the strategy in the first place.
People have noted the gaps in the BLACK BORDER but that just reflects the logo on the Critical Infrastructure Centre. https://twitter.com/stilgherrian/status/1293727144703483904">https://twitter.com/stilgherr...
My #purpletrain is soon to arrive at Sydney, so I’ll just say that I’ll come back to this thread later, and that @jpwarren also tweeted some bits about this yesterday. Not sure if they’re in a blog post yet. https://twitter.com/jpwarren/status/1293307602785320962">https://twitter.com/jpwarren/...

 Read on Twitter
Read on Twitter