My mom: I got the monthly bill from the mobile provider. But I can& #39;t open it.
Me: Why not?
Mom: It& #39;s in a ZIP file protected with a password.
Me *confidently*: Oh, this is a common trick. Scammers send malware like this to bypass e-mail gateway scanners.
Mom: Take a look.
Me: Why not?
Mom: It& #39;s in a ZIP file protected with a password.
Me *confidently*: Oh, this is a common trick. Scammers send malware like this to bypass e-mail gateway scanners.
Mom: Take a look.
So, I do. E-mail headers look perfectly OK. It really does seem to come from the mobile provider. Is this some trick I don& #39;t know?
The message addresses me correctly by name. OK, maybe they got it from somewhere.
Message says ZIP& #39;s encrypted with a password to protect data.
The message addresses me correctly by name. OK, maybe they got it from somewhere.
Message says ZIP& #39;s encrypted with a password to protect data.
Password is my date of birth, YYMMDD. OK, that& #39;s not hard to find, either. But if this is an attack, it& #39;s a hell of a targeted one...
But you can see what& #39;s in the ZIP archive without entering a password; archive directory is not encrypted. It& #39;s a PDF file.
Hmm...
But you can see what& #39;s in the ZIP archive without entering a password; archive directory is not encrypted. It& #39;s a PDF file.
Hmm...
So, taking all precautions, I open the PDF file in the virtual machine with no Internet connection.
IT& #39;S THE FUCKING MONTHLY BILL!!!
It& #39;s not an attack. The idiots have sent the bill exactly as the scammers do!
*That* is why we can& #39;t end phishing...
IT& #39;S THE FUCKING MONTHLY BILL!!!
It& #39;s not an attack. The idiots have sent the bill exactly as the scammers do!
*That* is why we can& #39;t end phishing...
Wait, there is an update!
I sent an e-mail to their customer service, basically explaining them what idiots they are and why, and how to do this stuff properly.
I sent an e-mail to their customer service, basically explaining them what idiots they are and why, and how to do this stuff properly.
They basically answered that "this is how we& #39;re doing it now", which is not surprising; customer service has no authority to make such decisions.
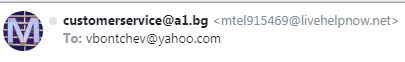
But look at the sender address.
ARE YOU FUCKING KIDDING ME?!
But look at the sender address.
ARE YOU FUCKING KIDDING ME?!
I mean, this thing - the "name" part of the address specifying one (seemingly valid) address and the actual e-mail address being completely unrelated shit is PRECISELY what we tell people to look for in phishing e-mails!!!

 Read on Twitter
Read on Twitter