~ Tor and the Dark Web ~
What is Tor? Why do people use it? How does it work to protect privacy?
Thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
What is Tor? Why do people use it? How does it work to protect privacy?
Thread
2/ The Internet might feel like magic, but computers need to know how to find each other
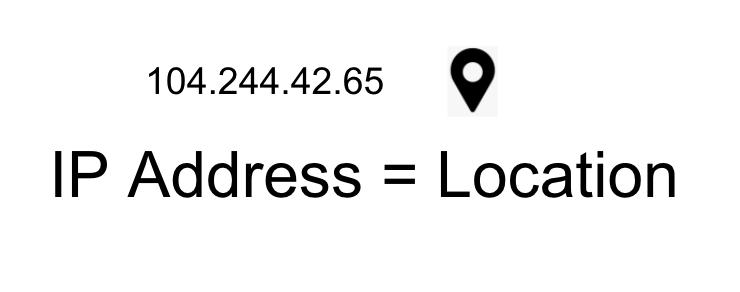
They do this by sharing their IP Addresses, which are similar to mailing addresses in the physical world
An IP Address encodes the location of a machine& #39;s WIFI connection
They do this by sharing their IP Addresses, which are similar to mailing addresses in the physical world
An IP Address encodes the location of a machine& #39;s WIFI connection
3/ This results in some privacy concerns
A website can know the general location of its users
And people can know the general location of the website& #39;s servers
This makes it easy to shut down websites and survey a user& #39;s Internet activity
A website can know the general location of its users
And people can know the general location of the website& #39;s servers
This makes it easy to shut down websites and survey a user& #39;s Internet activity
4/ In a previous thread I discussed VPNs and how they can help, but then they become a trusted third party and single point of failure https://twitter.com/dannydiekroeger/status/1287427727998332928?s=20">https://twitter.com/dannydiek...
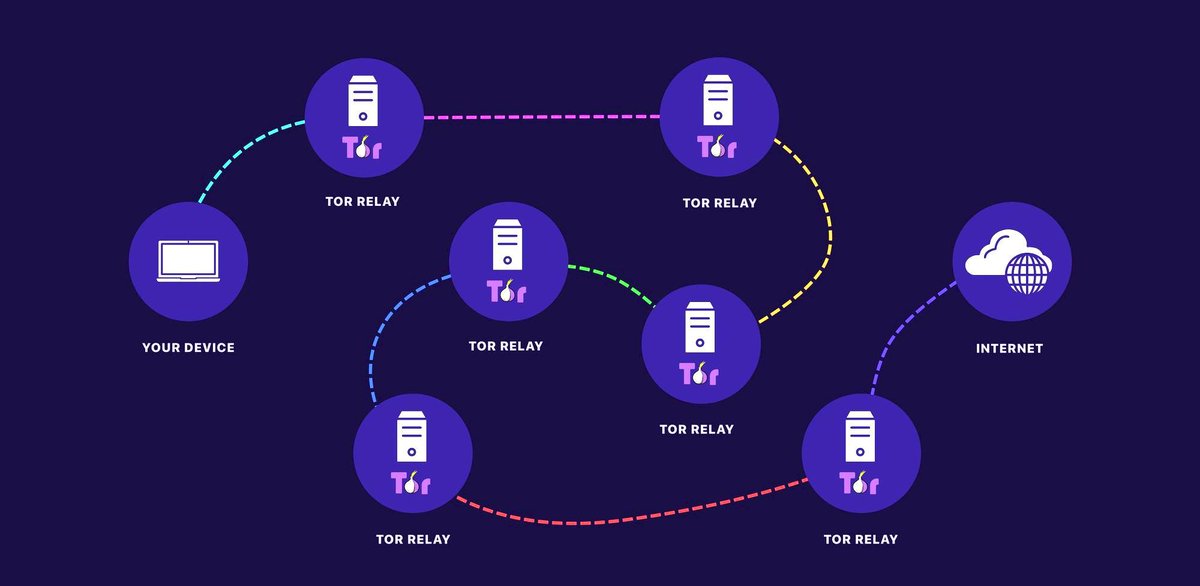
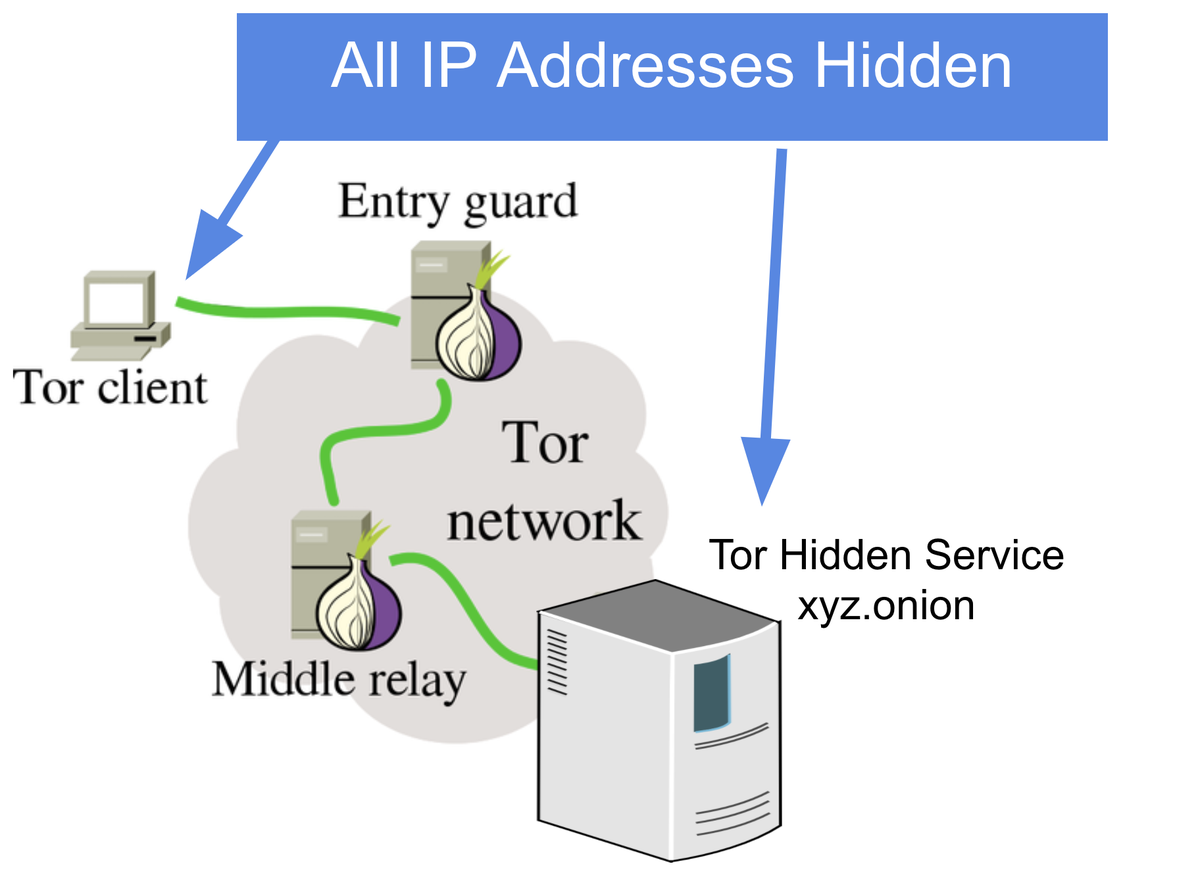
5/ For maximum privacy and censorship resistance, the best tool we have is called Tor
Tor stands for "The Onion Routing" project, and it& #39;s run by volunteers all around the world
These volunteers run Tor Relay Nodes, which assist in routing Internet traffic around secretly
Tor stands for "The Onion Routing" project, and it& #39;s run by volunteers all around the world
These volunteers run Tor Relay Nodes, which assist in routing Internet traffic around secretly
6/ On the regular Internet, requests from a user to a website will pass through multiple machines with each intermediate machine knowing the IP Addresses of both sides
7/ But Tor relay nodes are different
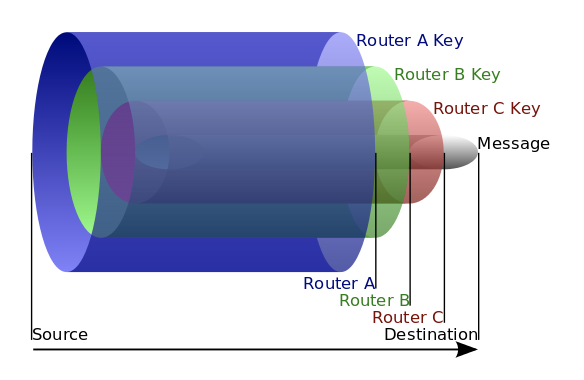
Request across relay nodes are encrypted in a series of layers, like an Onion, and passed around several times before reaching their destinations
Request across relay nodes are encrypted in a series of layers, like an Onion, and passed around several times before reaching their destinations
8/ The Onion-style multi-layered encryption guarantees that no nodes can know the sender or the destination
Each node can only know the previous and next steps in the chain
Each node can only know the previous and next steps in the chain
9/ As an analogy imagine there& #39;s a babushka doll, but each layer has a mail address on it, and requires a specific key to unlock it
And say you& #39;re a relay node for some message inside this babushka doll
You get it in the mail, unlock your layer, then send it to the next address
And say you& #39;re a relay node for some message inside this babushka doll
You get it in the mail, unlock your layer, then send it to the next address
10/ You don& #39;t know how many more layers there are inside the doll, and you don& #39;t know how many layers there were before it
This is kind of how the Onion multi-layered encryption works for Tor traffic
This is kind of how the Onion multi-layered encryption works for Tor traffic
11/ That& #39;s a simplified analogy and there& #39;s a bit more nuance in reality, but the babushka doll is a good way to begin thinking about it
The wikipedia page goes into a bit more detail if you& #39;re interested
https://en.wikipedia.org/wiki/Onion_routing">https://en.wikipedia.org/wiki/Onio...
The wikipedia page goes into a bit more detail if you& #39;re interested
https://en.wikipedia.org/wiki/Onion_routing">https://en.wikipedia.org/wiki/Onio...
12/ So what are the ways that people can use Tor?
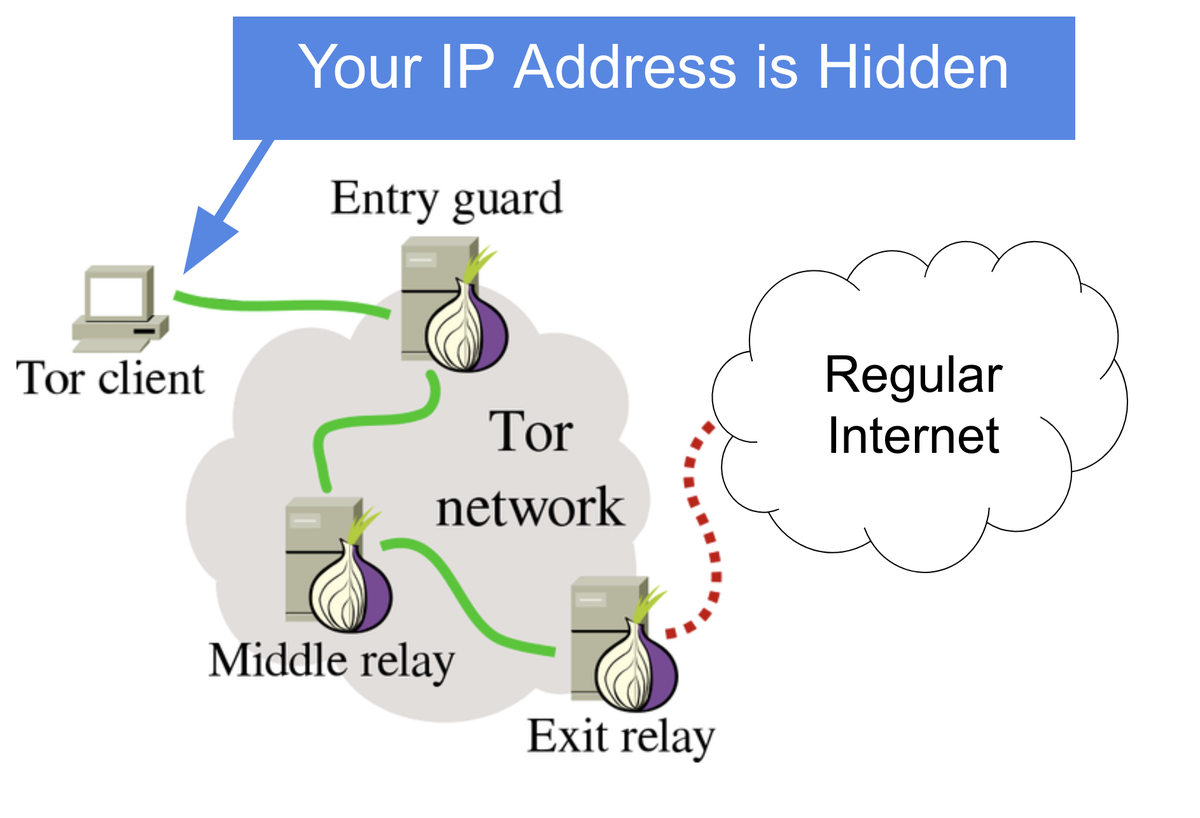
The first way is to use it as a privacy tool to browse the regular Internet
By using the Tor browser, your traffic will get routed through the Tor network before reaching the regular Internet
This conceals your IP Address
The first way is to use it as a privacy tool to browse the regular Internet
By using the Tor browser, your traffic will get routed through the Tor network before reaching the regular Internet
This conceals your IP Address
13/ The other way you can use Tor is to visit or run what& #39;s called a Hidden Service
These are websites that end in ".onion", and they hide the IP Address of the website owner
Sites like these make up what people call the "Dark Web"
These are websites that end in ".onion", and they hide the IP Address of the website owner
Sites like these make up what people call the "Dark Web"
14/ Plenty of illegal activity happens on the Dark Web, but it& #39;s also a really powerful tool for controversial journalists or people living under oppressive government regimes
The Tor website provides a deeper technical dive on how these sites work
https://2019.www.torproject.org/docs/onion-services">https://2019.www.torproject.org/docs/onio...
The Tor website provides a deeper technical dive on how these sites work
https://2019.www.torproject.org/docs/onion-services">https://2019.www.torproject.org/docs/onio...
15/ However remember that nothing is perfect, and there are still complex ways for your activity to be tracked in some cases, but these are the best tools we have
Some weaknesses are outlined here:
#Weaknesses">https://en.wikipedia.org/wiki/Tor_(anonymity_network) #Weaknesses">https://en.wikipedia.org/wiki/Tor_...
Some weaknesses are outlined here:
#Weaknesses">https://en.wikipedia.org/wiki/Tor_(anonymity_network) #Weaknesses">https://en.wikipedia.org/wiki/Tor_...
16/ Well there you have it, those are the basics of Tor
The recommended way to use Tor is to use it along with a VPN
To start using Tor, you can download the Tor browser here https://www.torproject.org/download/ ">https://www.torproject.org/download/...
The recommended way to use Tor is to use it along with a VPN
To start using Tor, you can download the Tor browser here https://www.torproject.org/download/ ">https://www.torproject.org/download/...
17/ As always, please ask questions in the comments, and if you know the answer to someone else& #39;s question please answer!
If you liked this thread, check out my other educational threads, which I always link on this mega-thread here: https://twitter.com/dannydiekroeger/status/1282000262782042117?s=20">https://twitter.com/dannydiek...
If you liked this thread, check out my other educational threads, which I always link on this mega-thread here: https://twitter.com/dannydiekroeger/status/1282000262782042117?s=20">https://twitter.com/dannydiek...
18/ And to stay in touch with me if I get unexpectedly suspended from Twitter again, join my email list here https://dannydiekroeger.substack.com/p/coming-soon ">https://dannydiekroeger.substack.com/p/coming-...

 Read on Twitter
Read on Twitter " title="~ Tor and the Dark Web ~What is Tor? Why do people use it? How does it work to protect privacy?Thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>
" title="~ Tor and the Dark Web ~What is Tor? Why do people use it? How does it work to protect privacy?Thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>