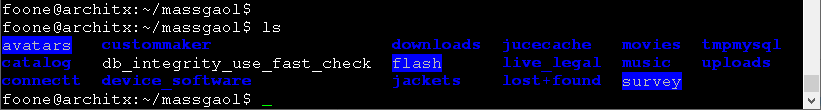
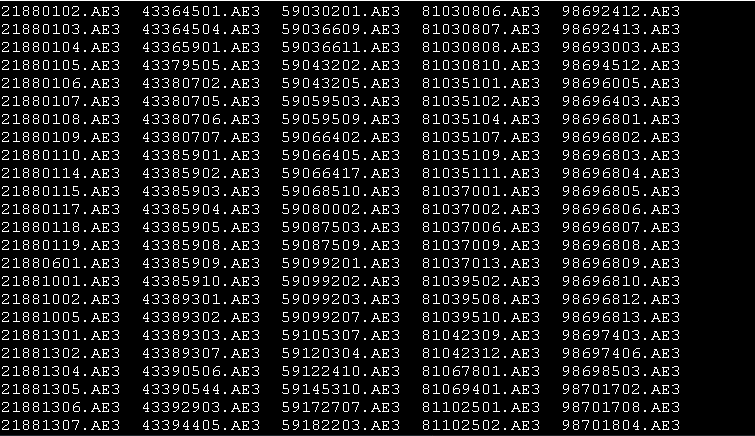
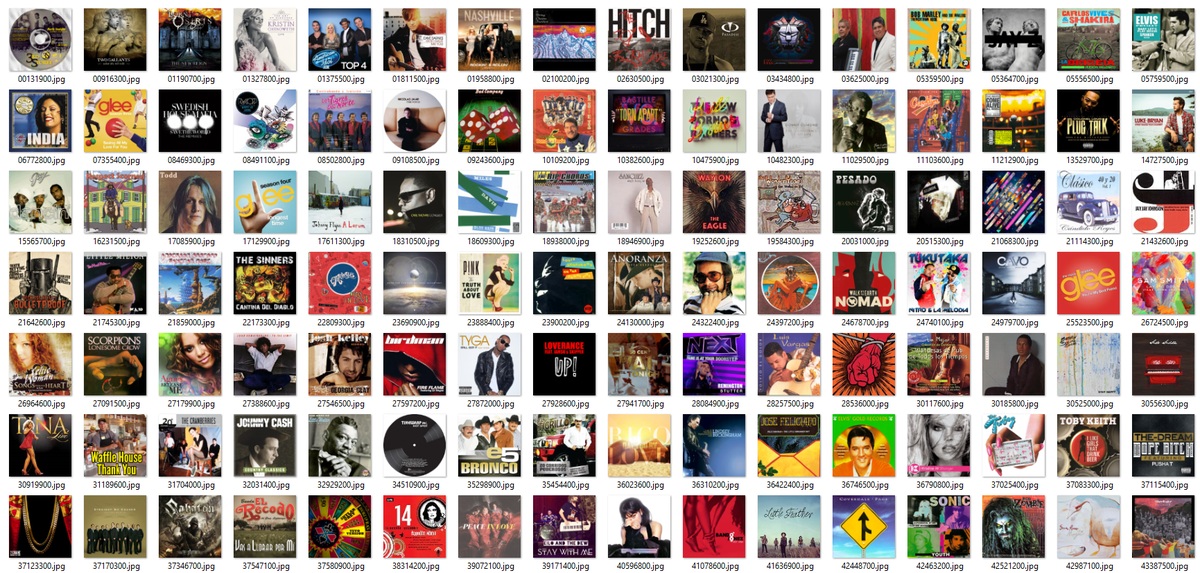
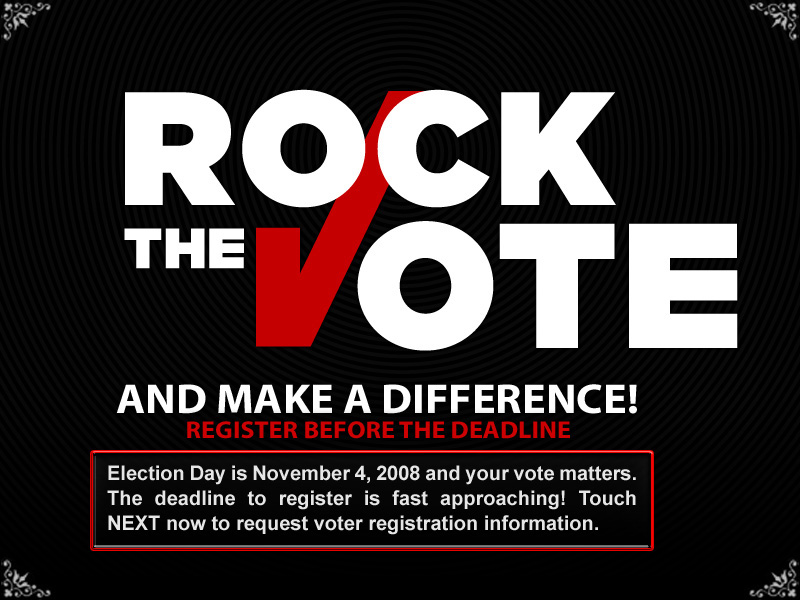
oh god I pulled a hard drive out of a weird embedded system and I thought I could just examine the partitions but it turns out it uses LVM
this just got way more complicated and/or impossible
this just got way more complicated and/or impossible
it seems to only have one single LVM physical volume on the drive which is making me think they& #39;re using LVM because it made it easier to encrypt the drive
turns out it& #39;s not encrypted.
this is the hard drive out of this thing: https://twitter.com/Foone/status/1156075485018783744">https://twitter.com/Foone/sta...
haha. I was wondering if anyone else had done any reversing on this, so I googled for the name of the LVM volume (massgaol).
I found one hit, which was someone asking about LVM commands on a mailing list back in 2006
I found one hit, which was someone asking about LVM commands on a mailing list back in 2006
I look up their name, find their linkedin, and... it turns out they worked for the company that built this device (from 2000 to 2007)
so the answer appears to be "no", no one is hacking on this except ME and THE PEOPLE WHO BUILT IT
here& #39;s an answer to the main question I had regarding this system: is it just a hard drive full of mp3s?
answer seems to be "no". The music folder has a bunch of these AE3 files, which aren& #39;t identifiable with file.
So presumably they encrypted them all
answer seems to be "no". The music folder has a bunch of these AE3 files, which aren& #39;t identifiable with file.
So presumably they encrypted them all
There& #39;s a MOTD file:
build .name = GEN3
build.revision = 3.9.20-2
build .date = 2017.10.30
build.time = 13:49:45
build.user = root
build .name = GEN3
build.revision = 3.9.20-2
build .date = 2017.10.30
build.time = 13:49:45
build.user = root
there& #39;s also an "avatars" folder which seems to be just.. random people?
huh. I didn& #39;t think this thing had any kind of social aspect so I don& #39;t know why this& #39;d be needed.
huh. I didn& #39;t think this thing had any kind of social aspect so I don& #39;t know why this& #39;d be needed.
The movies are a lot of attract videos and now playing sorts of things.
Like this one.
Like this one.
it seems it& #39;s suse-based.
so there& #39;s a bunch of scripts in /etc/ttinit which control how it boots up.
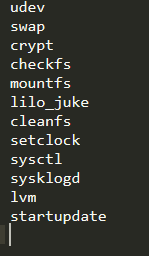
there& #39;s a file called bootorder:
there& #39;s a file called bootorder:
and a bunch of corresponding scripts in /etc/ttinit/scripts, and they just get called in that order.
some of these scripts have a linux-from-scratch header.
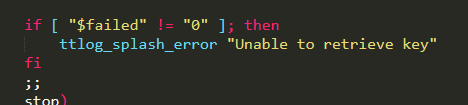
and it appears that the one called "crypt" mounts an encrypted partition (the second one), after loading some kernel modules.
Presumably they do some verification stuff...
and it appears that the one called "crypt" mounts an encrypted partition (the second one), after loading some kernel modules.
Presumably they do some verification stuff...
yeah, looks like there& #39;s a key stored in hardware or just encrypted in the kernels.
They& #39;re iButtons, which are crypto token devices.
So presumably the device originally had an iButton built into it that was could be queried and would provide the decryption keys for the second partition (and the mp3 files)
So presumably the device originally had an iButton built into it that was could be queried and would provide the decryption keys for the second partition (and the mp3 files)
There was no iButton seen in the teardown I did, so it presumably just plugged into a USB port, and vanished before the computer box got put on ebay
Interestingly, the /etc/ttinit folder has files called "splashcount" and "haltcount", presumably indicating how many times it powered on and how many times it shut down safely.
They& #39;re 13 and 6 on this machine.
They& #39;re 13 and 6 on this machine.
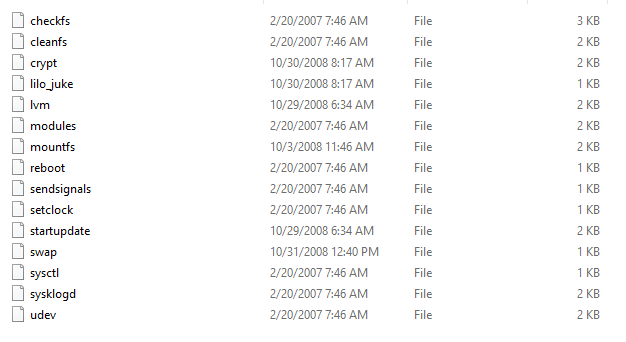
sdb1 (55mb) is basic boot stuff (kernel and the like)
sdb2 (4.7gb) is encrypted
sdb3 (133mb) is the small filesystem with the /etc/ttinit scripts
sdb5 (494mb) is a swap partition
sdb6 (144gb) is the LVM content drive
sdb2 (4.7gb) is encrypted
sdb3 (133mb) is the small filesystem with the /etc/ttinit scripts
sdb5 (494mb) is a swap partition
sdb6 (144gb) is the LVM content drive
Annoyingly I don& #39;t have enough free space on this archive machine& #39;s hard drive to fully archive the content drive, but I guess given that the mp3s are all encoded it& #39;s not like I& #39;d ever be able to do anything with them
still, it bugs me
still, it bugs me
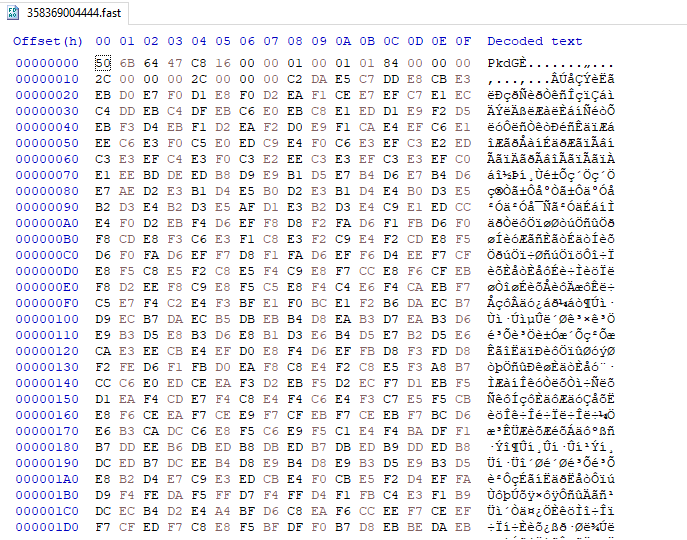
There& #39;s a bunch of ".fast" files in the jacket folder, which I think might be a kind of low-res version of an image. the format doesn& #39;t seem to be JPEG, or anything I can recognize, though.
but yeah. there& #39;s not much more I can do with this disk image, because without being able to unencrypt that sdb2 folder I have basically no binaries or databases to look into
isn& #39;t it funny that I started this thread by worrying that the LVM would be a problem or that it was encrypted, and the LVM turned out to be fine, but there was still an encrypted drive?
@mitchellmebane pointed out the .fast files are probably just serialized GdkPixbufs: https://twitter.com/mitchellmebane/status/1286851740852277248">https://twitter.com/mitchellm...

 Read on Twitter
Read on Twitter