My thoughts on current #twitterhack :
- Compromised accounts were chosen for high follower counts.
- Many of these accounts will have had 2FA enabled.
- Attackers likely have some form of administrative access.
- The above means an insider of some kind is likely involved.
- Compromised accounts were chosen for high follower counts.
- Many of these accounts will have had 2FA enabled.
- Attackers likely have some form of administrative access.
- The above means an insider of some kind is likely involved.
Continued...
- They have used a single bitcoin wallet which is something of a rookie error.
- Laundering cryptocurrency is still tricky.
- @Twitter ‘s locking of verified accounts shows a capability that we’ve never seen before.
- This could have been a whole lot worse.
- They have used a single bitcoin wallet which is something of a rookie error.
- Laundering cryptocurrency is still tricky.
- @Twitter ‘s locking of verified accounts shows a capability that we’ve never seen before.
- This could have been a whole lot worse.
And continuing on:
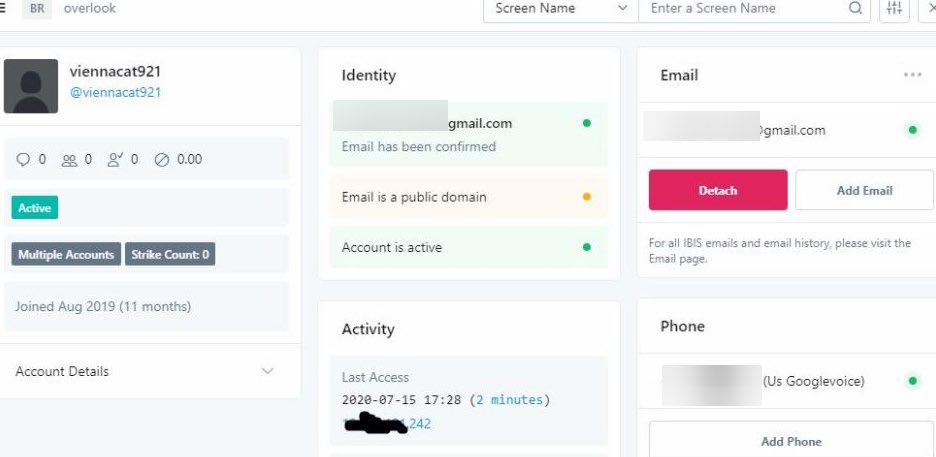
- This image has been making the rounds and purports to show the access panel used to takeover these accounts.
- Twitter has been removing this graphic which only serves to add to the chances that it’s real.
- This image has been making the rounds and purports to show the access panel used to takeover these accounts.
- Twitter has been removing this graphic which only serves to add to the chances that it’s real.
More...
- If so this is certainly another insider attack.
- That would make this the second of the year.
- Twitter has been making great steps at showing its understanding of the role and impact of its platform in the stability and security of our modern life.
- If so this is certainly another insider attack.
- That would make this the second of the year.
- Twitter has been making great steps at showing its understanding of the role and impact of its platform in the stability and security of our modern life.
And more...
- This will do a lot to undermine those good efforts.
- This hack, if it took place as evidence suggests, is not technically complex. It’s crypto bros meets script kiddies.
- By using a single Bitcoin wallet they have made it far harder to get their cash.
- This will do a lot to undermine those good efforts.
- This hack, if it took place as evidence suggests, is not technically complex. It’s crypto bros meets script kiddies.
- By using a single Bitcoin wallet they have made it far harder to get their cash.
Moving on...
- #Bitcoin https://abs.twimg.com/hashflags... draggable="false" alt=""> isn’t untraceable. Mueller taught us all that. It’s even more traceable when you pile it all up in one place.
https://abs.twimg.com/hashflags... draggable="false" alt=""> isn’t untraceable. Mueller taught us all that. It’s even more traceable when you pile it all up in one place.
- This attack was the equivalent of braking into Fort Knox and stealing the cash register... and the finding that you can’t open it.
- #Bitcoin
- This attack was the equivalent of braking into Fort Knox and stealing the cash register... and the finding that you can’t open it.
And....
- @Twitter confirms that this was an inside job. But where there employees were targeted with a coordinated social engineering hack. https://twitter.com/TwitterSupport/status/1283591846464233474?s=20">https://twitter.com/TwitterSu...
- @Twitter confirms that this was an inside job. But where there employees were targeted with a coordinated social engineering hack. https://twitter.com/TwitterSupport/status/1283591846464233474?s=20">https://twitter.com/TwitterSu...
So...
- If this is the case then there are some quick lessons that can be learned here. One, cyber-hygiene for Twitter staff needs work. Two, did the administrator tool used not require 2FA/MFA to access? Three, if not, why not. Three, if so how did the hackers gain access.
- If this is the case then there are some quick lessons that can be learned here. One, cyber-hygiene for Twitter staff needs work. Two, did the administrator tool used not require 2FA/MFA to access? Three, if not, why not. Three, if so how did the hackers gain access.
Continuing...
-If the tool did require 2FA/MFA and the hacker still gained access through social engineering then this is the best example of why education and cyber-hygiene for staff is critically important.
-If the tool did require 2FA/MFA and the hacker still gained access through social engineering then this is the best example of why education and cyber-hygiene for staff is critically important.
Still going...
- @twitter has started to adapt to this issue already. It has now blocked all tweets containing #bitcoin https://abs.twimg.com/hashflags... draggable="false" alt=""> addresses.
https://abs.twimg.com/hashflags... draggable="false" alt=""> addresses.
- This doesn& #39;t work for those posting QR codes that link to wallets.
- Unclear if this applies to other cyrptocurrency. https://bit.ly/2WkqUqr ">https://bit.ly/2WkqUqr&q...
- @twitter has started to adapt to this issue already. It has now blocked all tweets containing #bitcoin
- This doesn& #39;t work for those posting QR codes that link to wallets.
- Unclear if this applies to other cyrptocurrency. https://bit.ly/2WkqUqr ">https://bit.ly/2WkqUqr&q...
Further thoughts...
- Government inquiries loom. Sen. Josh Hawley has apparently already sent a letter to know what happened.
- A lot of analysis needs to be done as to how verified account holders responded to their accounts being blocked. News still needs to get out.
- Government inquiries loom. Sen. Josh Hawley has apparently already sent a letter to know what happened.
- A lot of analysis needs to be done as to how verified account holders responded to their accounts being blocked. News still needs to get out.
Musings...
-The & #39;blue tick& #39; proffers both elite status and legitimacy/credibility upon its bearer.
- This is bad enough when that legitimacy is misused by the authentic account holder; far worse when multiple verified accounts can be taken over at the same time.
-The & #39;blue tick& #39; proffers both elite status and legitimacy/credibility upon its bearer.
- This is bad enough when that legitimacy is misused by the authentic account holder; far worse when multiple verified accounts can be taken over at the same time.
Ideas...
- That being said, some verified accounts are more susceptible to successful manipulation than others.
- If these hackers had tried to short the market by tweeting about Tesla from @elonmusk that would be more likely to succeed. Why? Because he has a history of it....
- That being said, some verified accounts are more susceptible to successful manipulation than others.
- If these hackers had tried to short the market by tweeting about Tesla from @elonmusk that would be more likely to succeed. Why? Because he has a history of it....

 Read on Twitter
Read on Twitter