Unfortunately this large density of defects in IoT is not unexpected.
A study across 15 years and 3millon binaries showed that core security hygiene products in the base of IoT showed no trends towards improvement.
In fact, things more often got worse.
https://cyber-itl.org/2019/08/26/iot-data-writeup.html">https://cyber-itl.org/2019/08/2... https://twitter.com/largecardinal/status/1274433398141042688">https://twitter.com/largecard...
A study across 15 years and 3millon binaries showed that core security hygiene products in the base of IoT showed no trends towards improvement.
In fact, things more often got worse.
https://cyber-itl.org/2019/08/26/iot-data-writeup.html">https://cyber-itl.org/2019/08/2... https://twitter.com/largecardinal/status/1274433398141042688">https://twitter.com/largecard...
Left to their own accord vendors of embedded systems are not demonstrating that they improve basic security hygiene in their products.
There needs to be a more global incentive structure to address this issue.
There needs to be a more global incentive structure to address this issue.
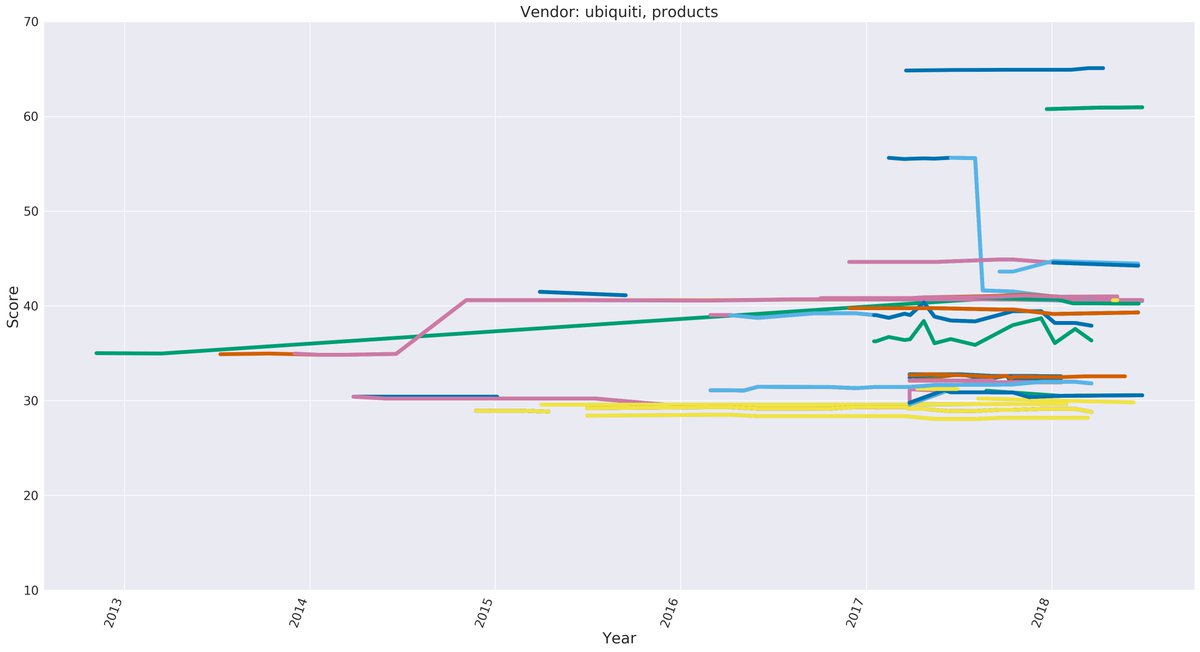
For example Ubiquity, who’s products I like, simultaneously had their best and worst hygiene product in 2018.
You can see products in their portfolio getting random improvements and products *losing* basic safety features in the dev process.
You can see products in their portfolio getting random improvements and products *losing* basic safety features in the dev process.
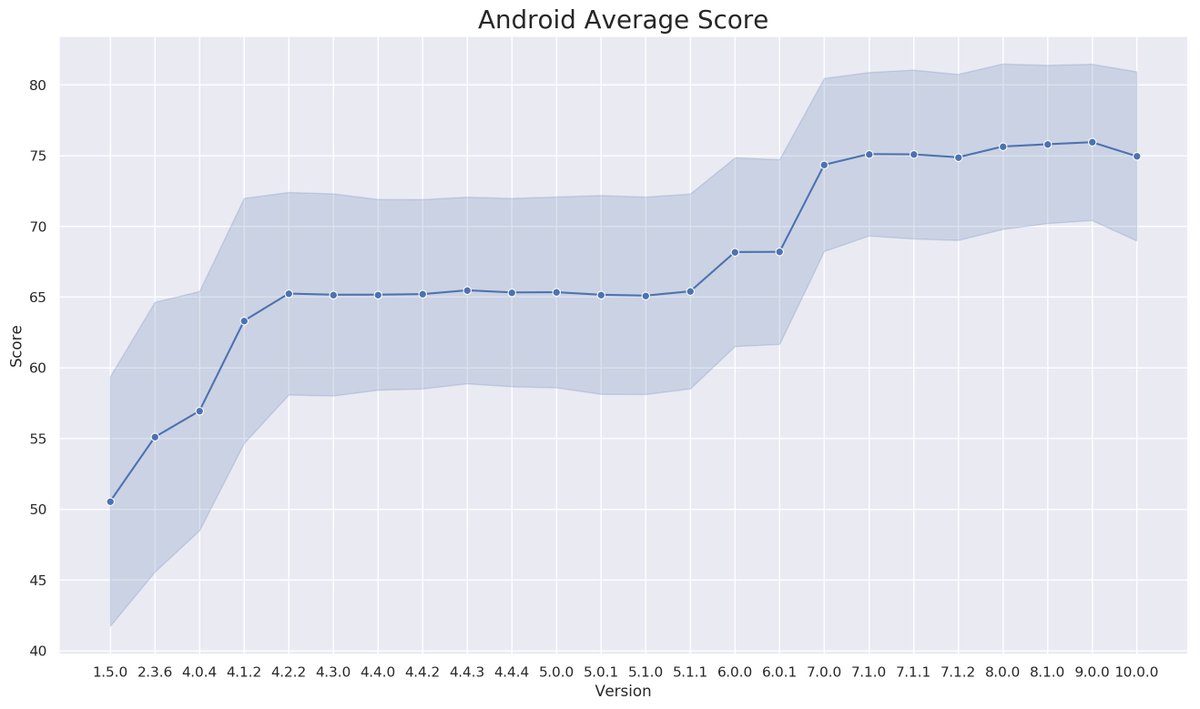
Parker, @m0thran, did observe that Google’s (non-branched) Android releases *did* show baseline improvement over time.
However Google seems to be an exception and few others have the resources or desire to improve baseline security “just because”. https://cyber-itl.org/2019/12/16/android-evolution.html">https://cyber-itl.org/2019/12/1...
However Google seems to be an exception and few others have the resources or desire to improve baseline security “just because”. https://cyber-itl.org/2019/12/16/android-evolution.html">https://cyber-itl.org/2019/12/1...
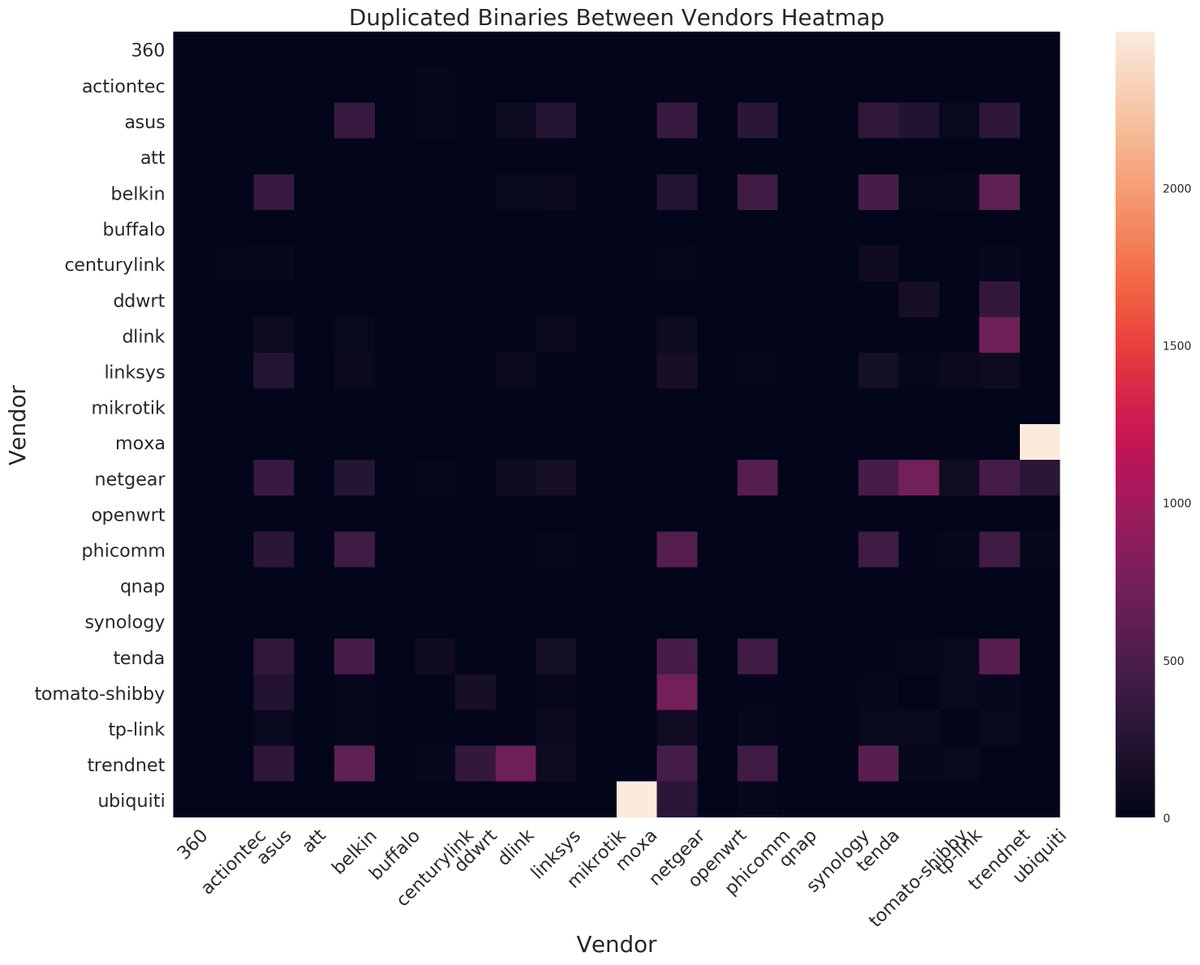
If you want to find, or fix, a vulnerability that spreads across many vendors and products I would recommend looking into the collisions identified on this heat map.
Again @m0thran did all this awesome work (in the http://Cyber-ITL.org"> http://Cyber-ITL.org blog post on embedded systems/IoT)
Again @m0thran did all this awesome work (in the http://Cyber-ITL.org"> http://Cyber-ITL.org blog post on embedded systems/IoT)
If you want to know which binaries those are, or maybe look for the sha256 of binaries from the JSOC vuln report on other products...
The http://Cyber-itl.org"> http://Cyber-itl.org dataset has s here: https://drive.google.com/file/d/1aThJ_OZXB_TX4TyiL_2WRzQmyMMETAt7/view">https://drive.google.com/file/d/1a...
The http://Cyber-itl.org"> http://Cyber-itl.org dataset has s here: https://drive.google.com/file/d/1aThJ_OZXB_TX4TyiL_2WRzQmyMMETAt7/view">https://drive.google.com/file/d/1a...
Per numerous DMs:
The description of fields in the data set, and the larger report, are here...
Please appropriately credit cyber-itl if you use it. They are a small non-profit and every bit of support helps. https://cyber-itl.org/2019/08/26/iot-data-writeup.html">https://cyber-itl.org/2019/08/2...
The description of fields in the data set, and the larger report, are here...
Please appropriately credit cyber-itl if you use it. They are a small non-profit and every bit of support helps. https://cyber-itl.org/2019/08/26/iot-data-writeup.html">https://cyber-itl.org/2019/08/2...
Additional:
The CITL dataset is Linux embedded systems / IoT variants.
CITL did not release RTOS datasets.
The CITL dataset is Linux embedded systems / IoT variants.
CITL did not release RTOS datasets.

 Read on Twitter
Read on Twitter