As a follow-up to my honeypot post from yesterday, I& #39;ve now got some interesting stats after ~36 hours of running it fully exposed to the world (A Thread)
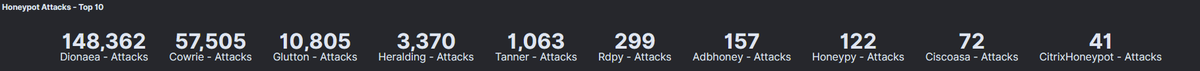
First up, the sheer number of hits on this really surprised me. Over 221k scans, exploit attempts or other hits against this was way more than I& #39;d expected in that timeframe.
The main thing I didn& #39;t expect to see from this was the overwhelming prevalence of SMB attacks. Of the 148k attacks picked up by the Dionaea honeypot, 99.67% of these were against SMB!
There was also a greater variety in the recorded countries these attacks came from than with others, but this could just be down to the sheer volume of attempts targeting this.
Suricata, an IDS/IPS engine also running as part of this stack, flags a significant number (28k) of exploit attempts for DoublePulsar ( https://www.rapid7.com/security-response/doublepulsar/)">https://www.rapid7.com/security-... - which I& #39;d honestly expected to have died down by now, suggesting it& #39;s still successful enough to keep using.
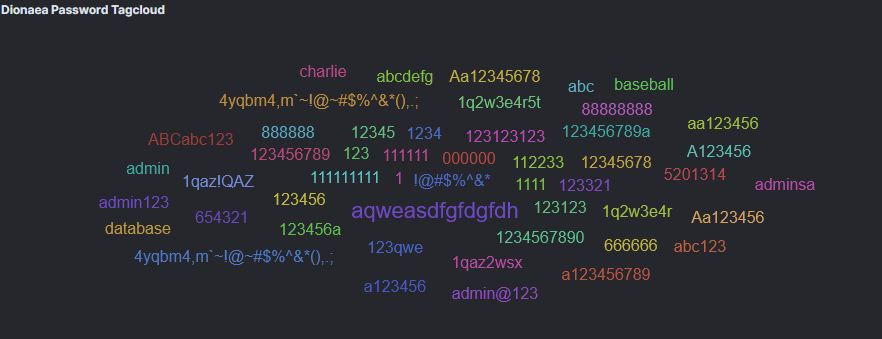
There was also a fairly weird selection of passwords attached to these attempts - "4yqbm4,m`~!@~#$%^&*(),.;" caught my eye and doesn& #39;t appear on Pwned Passwords so that one& #39;s a little unusual.
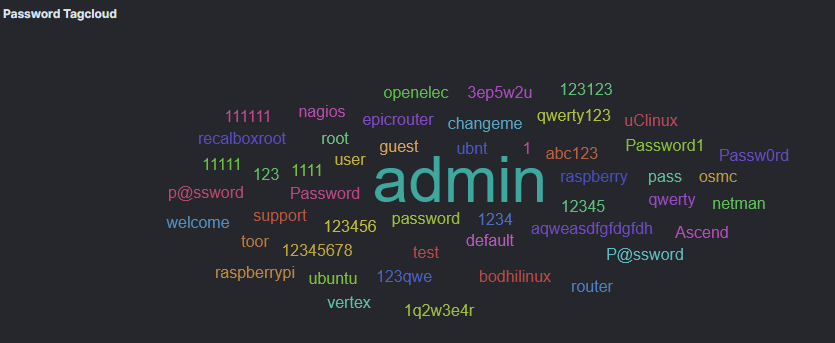
Also of some interest is the captured usernames and passwords for SSH attempts. Special shoutout to the poor bot sending its User-Agent string as a username and presumably having no success compromising anything ever.
Appearing quite frequently in that list are the default credentials for Raspbian, the OS designed for Raspberry Pis (pi:raspberry), suggesting that attackers are wise to hobbyists and less experienced folk accidentally configuring their Pi insecurely.
This is only a first pass over a single section of the data from the last day& #39;s worth of traffic, so hopefully I can revisit this a few times and provide some more interesting bits and bobs.

 Read on Twitter
Read on Twitter