THREAD: on Dec 29, 2016, day of Flynn-Kislyak calls, there was third leg to Obama statement on sanctions against Russian intel agencies and expulsion of diplomats: the release of “declassified technical information” on Russian cyber activity. https://obamawhitehouse.archives.gov/the-press-office/2016/12/29/statement-president-actions-response-russian-malicious-cyber-activity">https://obamawhitehouse.archives.gov/the-press...
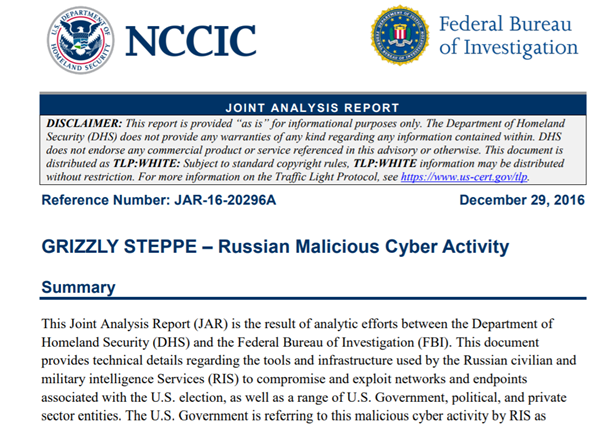
2/ The Dec 29 technical information, which was jointly published by DHS and FBI, https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296A_GRIZZLY%20STEPPE-2016-1229.pdf,">https://www.us-cert.gov/sites/def... had been expected to settle any and all skepticism by Trump and others of the intel community’s (then merely asserted) attribution of DNC hack to Russian state actors.
3/ I remember reading report in real time and being appalled its inadequacy. Indeed, its apparent incompetence led me to start looking critically and analytically at other documents. In retrospect, it& #39;s even worse than I originally thought.
4/ It contained NO evidence supporting Russian attribution of DNC hack. Attached to it was a 921-row spreadsheet https://www.us-cert.gov/sites/default/files/publications/JAR-16-20296A.csv">https://www.us-cert.gov/sites/def... of supposedly relevant malware and infrastructure - NONE of which was connected to DNC hack.
5/ Nearly all technical information (YARA rule, hashes) pertained to a single form of php malware, which was almost immedately shown https://www.wordfence.com/blog/2016/12/russia-malware-ip-hack/">https://www.wordfence.com/blog/2016... to be publicly available on internet – ironically from Ukraine, not Russia.
6/ At best, malware in the DHX-FBI report was irrelevant to DNC hack; at worst, it contradicted attribution to Russia.
If intel community/Obama admin used report in attribution, it& #39;s worrying. If they were merely trying to gull public and incoming admin with nonsense, no better
If intel community/Obama admin used report in attribution, it& #39;s worrying. If they were merely trying to gull public and incoming admin with nonsense, no better
7/ now to the narrative.
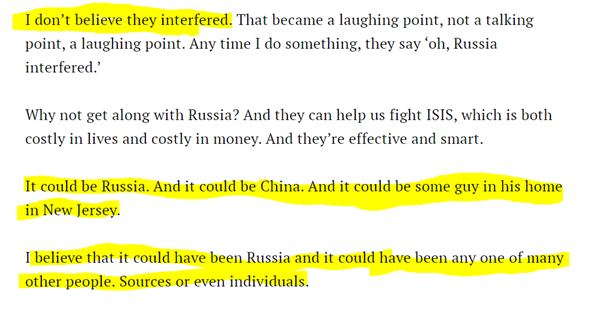
As of Nov 28, 2016, Trump remained skeptical of
https://time.com/4591183/time-person-of-the-year-2016-donald-trump-interview/">https://time.com/4591183/t... intel community& #39;s attribution of DNC hack to Russia. He admitted possibility, but wasn& #39;t convinced based on then available information. This really annoyed media.
As of Nov 28, 2016, Trump remained skeptical of
https://time.com/4591183/time-person-of-the-year-2016-donald-trump-interview/">https://time.com/4591183/t... intel community& #39;s attribution of DNC hack to Russia. He admitted possibility, but wasn& #39;t convinced based on then available information. This really annoyed media.
8/ on Dec 27, 2016, on eve of Obama policy, Adam Schiff gave an interesting interview, covering topics which were later, more or less, the terms of reference for Mueller
http://archive.is/PJhkH ">https://archive.is/PJhkH&quo...
http://archive.is/PJhkH ">https://archive.is/PJhkH&quo...
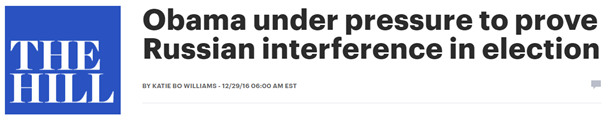
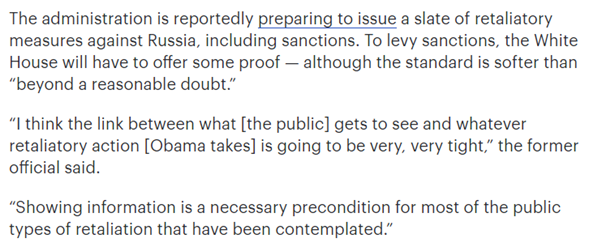
9/ leading into Dec 29 statement, The Hill http://thehill.com/policy/national-security/312049-obama-under-pressure-to-prove-russian-interference-in-election">https://thehill.com/policy/na... reported that Obama admin was “under pressure to prove Russian interference” as up till then they had “provided little documentation” to back its assessment
10/ The Hill article noted that Obama admin was reported to be preparing “retaliatory measures, including sanctions” and naively asserted that “to levy sanctions, WH will have to offer some proof”, with one official expecting link to be “very, very tight”. Uh, huh.
11/ At the time, the Trump transition team demanded that Brennan and others show their evidence, rather than just leak. Kellyanne Conway: " let& #39;s see it [the evidence]."
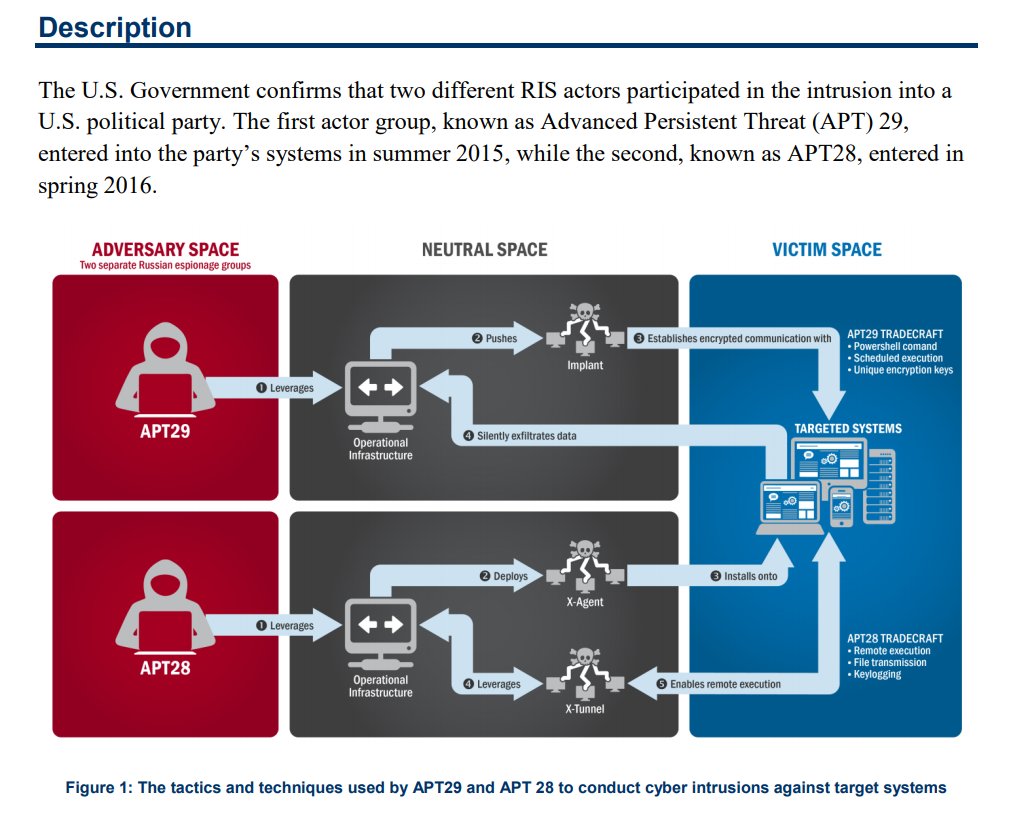
12/ but evidence supporting attribution was not what intel community provided. The text of the report https://www.us-cert.gov/sites/default/files/publications/JAR_16-20296A_GRIZZLY%20STEPPE-2016-1229.pdf">https://www.us-cert.gov/sites/def... is mostly pablum. It begins with generic cartoon of exfiltration.
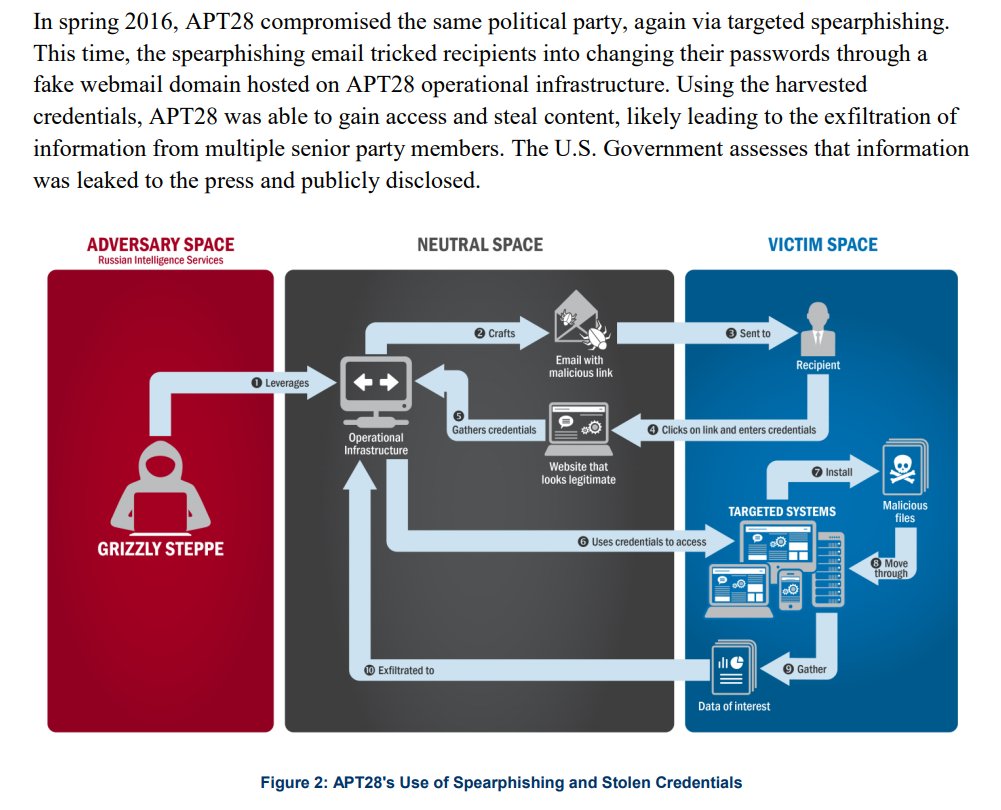
13/ it gve generic description of APT28 (Fancy Bear) hack, to which Wikileaks DNC emails were attributed, but without any information on domains, IP addresses, malware, dates or any actual technical evidence.
14/ it continued with a peculiar list entitled "Reported Russian Military and Civilian Intelligence Services (RIS)", a list which included both hypothesized APT (Advanced Persistent Theat) groups (APT28, APT29) and individual malwares (Powershell backdoor etc.)
15/ the list included multiple pseudonyms for each APT e.g. for APT28: Fancy Bear, Operation Pawn Storm, and programs attributed to each APT e.g. for APT28: Sofacy, X-Agent, Sednit, Sedkit, Sourface, ... for APT29: MiniDuke, OnionDuke, CloudDuke.....
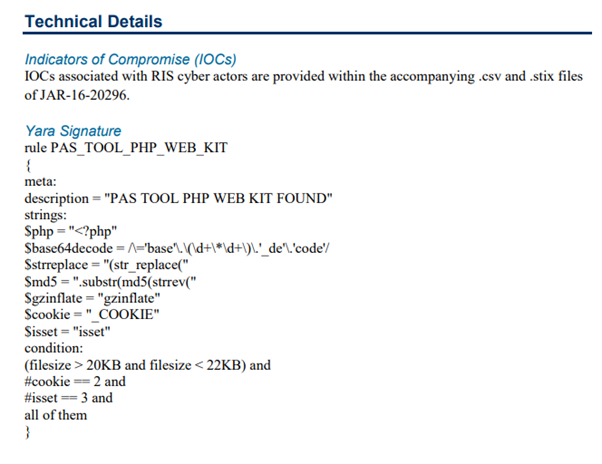
16/ the heavy lifting came in section entitled Technical Details, which stated that "IOCs associated with RIS cyber actors are provided within the accompanying .csv and .stix files" and gave YARA rule. Note "RIS cyber actors", not Ukrainian, not 400-lb man in New Jersey.
17/ I& #39;ve done new analysis of the associated csv file on "RIS cyber actors" which I& #39;ll present downthread. The YARA rule attracted immediate attention from Wordfence, which I& #39;ll also present downthread. For now, I& #39;ll finish review of document to show that there& #39;s nothing else
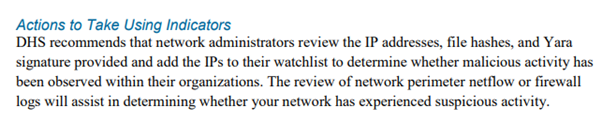
18/ DHS placed special emphasis on the IOCs in their bulletin urged that "network administrators review the IP addresses, file hashes, and Yara signature provided and add the IPs to their watchlist" to protect against "RIS cyber actors"
19/ their next sections were on Recommended Mitigations and Detailed Mitigation Strategies - both worthy activities, but unrelated to attribution of DNC hack to Russia state actors.
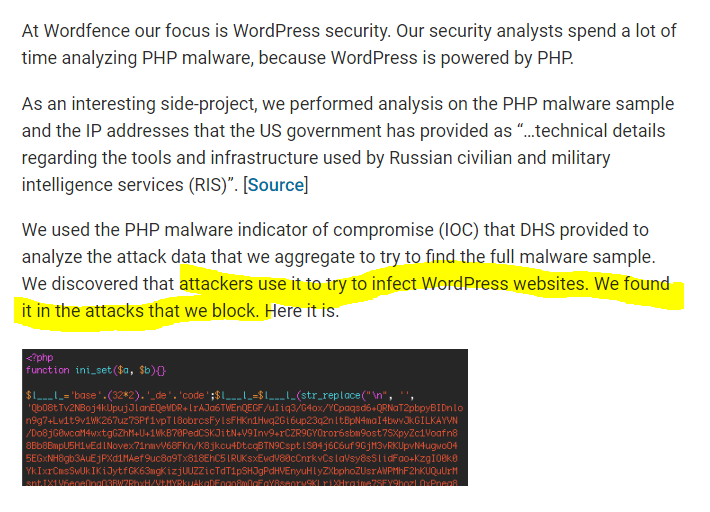
20/ the next day (Dec 30), Wordfence observed https://www.wordfence.com/blog/2016/12/russia-malware-ip-hack/">https://www.wordfence.com/blog/2016... that they had observed one of the listed PHP malware indicators in attacks on Wordpress websites.
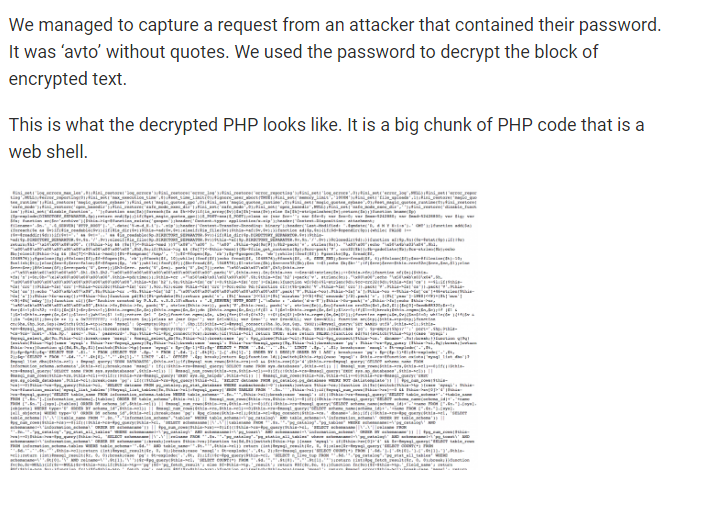
21/ Wordfence captured the password (avto) to one of these attempted intrusions and checked out the malware in a "sandbox" (separate from systems).

 Read on Twitter
Read on Twitter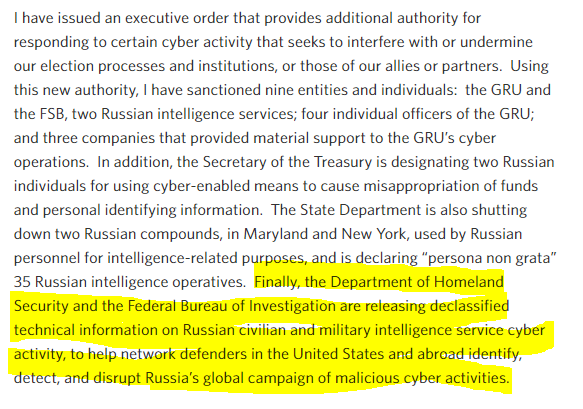

![11/ At the time, the Trump transition team demanded that Brennan and others show their evidence, rather than just leak. Kellyanne Conway: " let& #39;s see it [the evidence]." 11/ At the time, the Trump transition team demanded that Brennan and others show their evidence, rather than just leak. Kellyanne Conway: " let& #39;s see it [the evidence]."](https://pbs.twimg.com/media/EY38bf9UEAASX1r.png)