1/ Few days back a hacker claimed that he has found some serious security flaws in @SetuAarogya and 90 million user& #39;s privacy is at risk and also wrote an article on medium for explanation of the issues he found. Follow the thread to know the REALITY of so called security issues.
That is an intentional feature of the application and it provides you number of nearby users, covid-19 positive users etc and NOT their identities. Also the radius for which you can ask this data has only few values : 500m, 1Km, 2Km, 5Km, 10Km only.
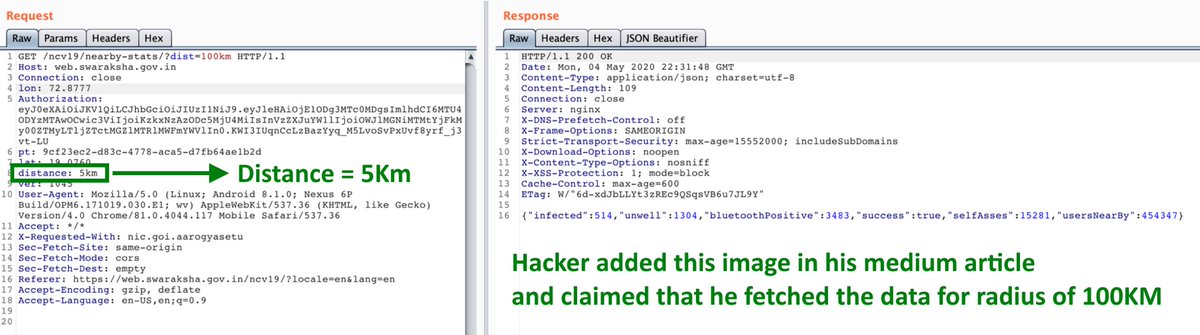
Claim by the hacker: The hacker claimed that he could fetch data for a custom radius (any radius value he likes say even 100m) which could be privacy issue as he could reduce the radius to say 50m and check if his neighbour is unwell or covid-19 positive etc.
Archive of his original article where response option is ON, where he has called that location as New Delhi (latitude, longitude in his request sent to server you can see clearly as 19.0760, 72.8777) and the authorisation token is not hidden in his image : http://archive.is/CxQFb ">https://archive.is/CxQFb&quo...
My first response to his article : https://www.facebook.com/471729996200979/posts/4146923352014940/">https://www.facebook.com/471729996... Also he blocked me just like others @hexachordanu @sunnyrockzzs @hexachordanu @Th3_N1gh7m4r3 @Sri_Hxor @virtualgh0st many more for pointing out such things.
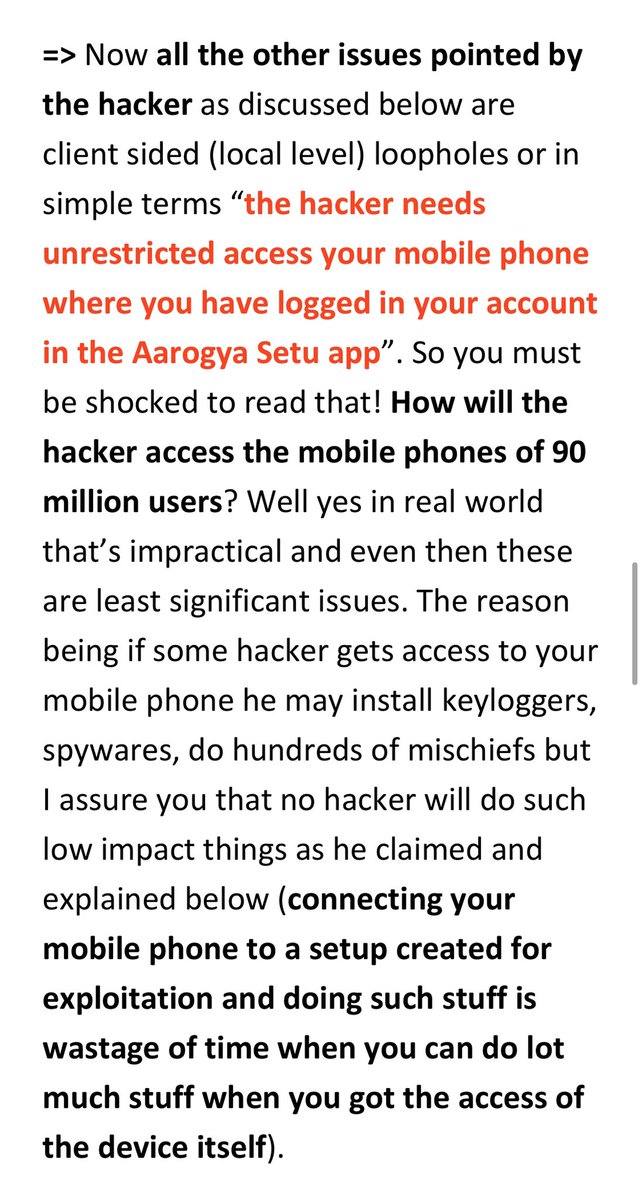
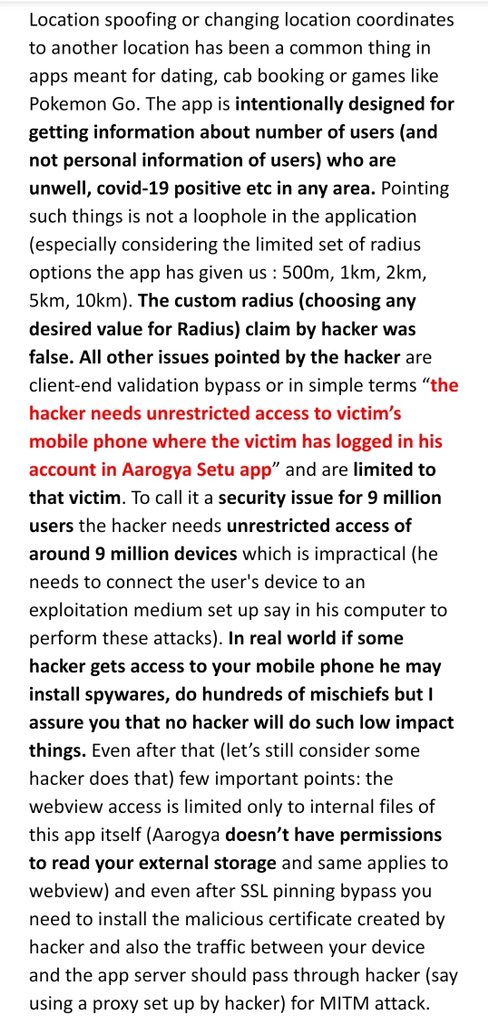
Yes! The hacker needs unrestricted access to your phone for the issues we going to talk about now. It’s not about fetching some data from server but trying to fetch from app directory or other mischiefs there). They are client-side validation bypass in an exploitation medium.
Yeah the MITM here needs all that. And this is something you can do with most of the apps you gonna find.
The app doesn’t have permissions to read your external storage and same applies to the files that can be accessed by webview. So a hacker would do such much efforts with your mobile phone (with unrestricted access) to print the internal files of that app before you?
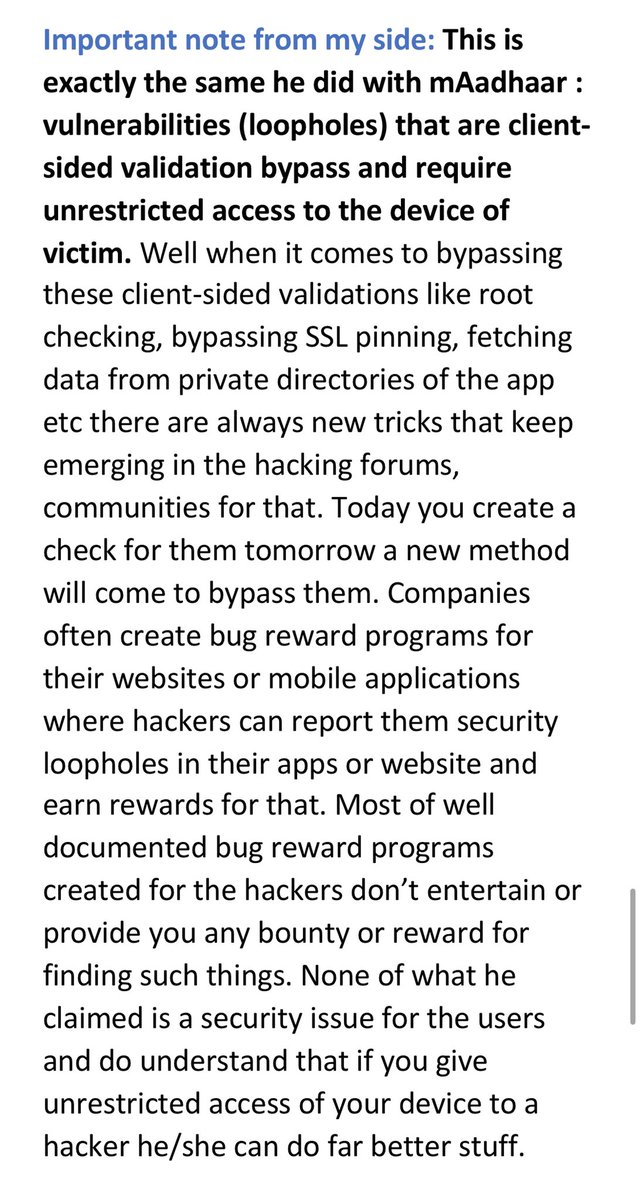
I remember the case of @UIDAI application #mAadhaar where similar issues of client-side validation bypass were pointed by him and the mainstream media highlighted that issue so much without even understanding what the actual matter is. #Aadhaar #Security
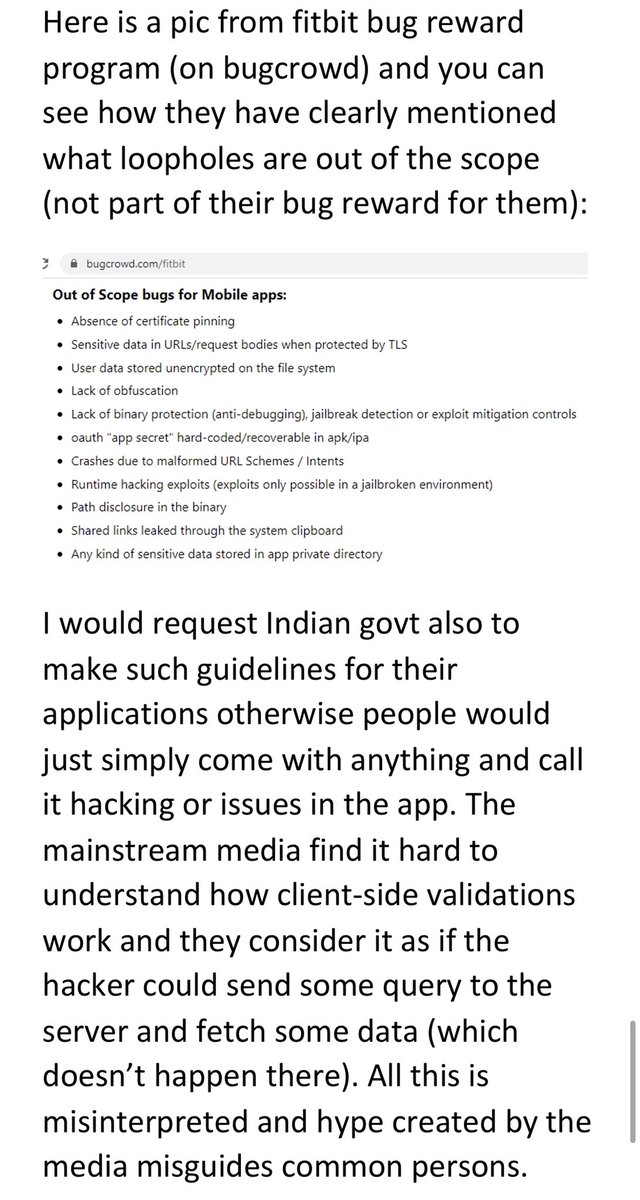
My suggestion for @UIDAI @SetuAarogya @GoI_MeitY @rsprasad @UmangOfficial_ @NPCI_BHIM @digilocker_ind @IRCTCofficial  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙏" title="Folded hands" aria-label="Emoji: Folded hands"> to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team).
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙏" title="Folded hands" aria-label="Emoji: Folded hands"> to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team).
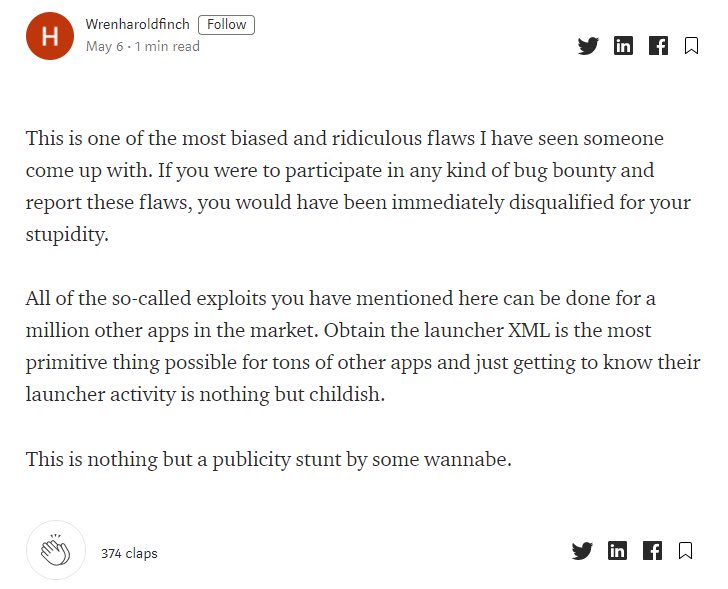
And this was the TOP response on that article made by hacker (all top responses were like this) after which he turned off response option. Here is the archives of this response: http://archive.is/7X1On ">https://archive.is/7X1On&quo... (in case needed) and the original link : https://medium.com/@wrenharoldfinch/this-is-one-of-the-most-biased-and-ridiculous-flaws-i-have-seen-someone-come-up-with-9e115013a793">https://medium.com/@wrenharo...
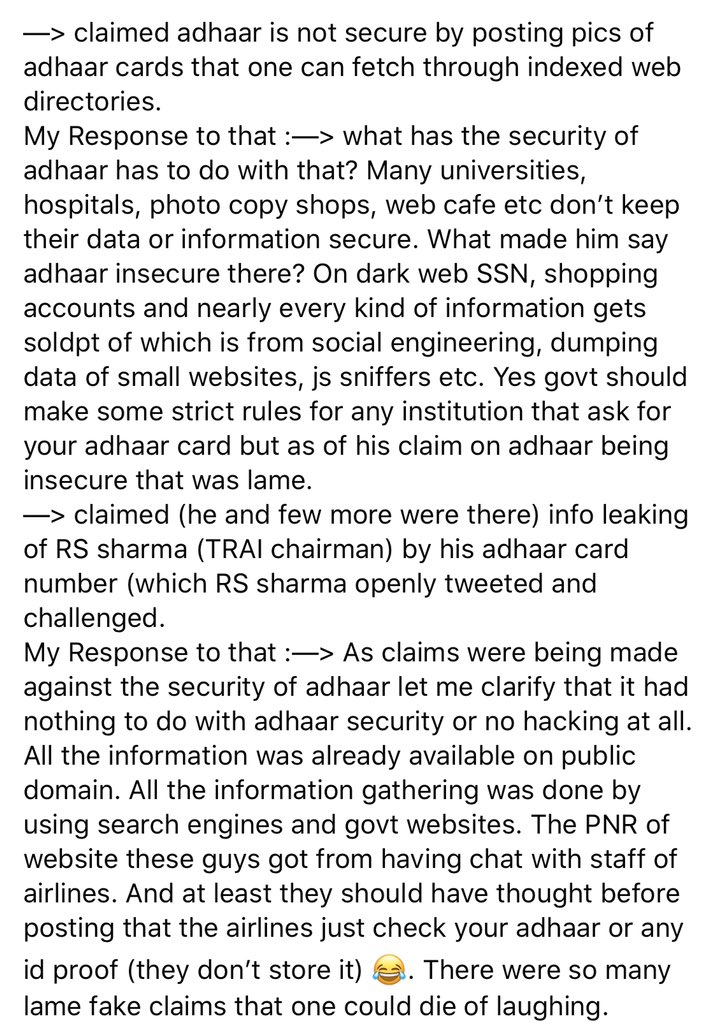
And a brief history of that hackers’s work when it comes to exposing our govt app or websites issues as he keeps claiming. When he accepted his aadhaar hacking challenge all he did was fetching information from public domain.
And when he pointed out a security breach in @BJP4India official website by pointing the encryption used there (that was CLIENT side encryption) so obviously it should be visible to clients. It’s explained well here : https://www.facebook.com/471729996200979/posts/2853679744672647/">https://www.facebook.com/471729996...
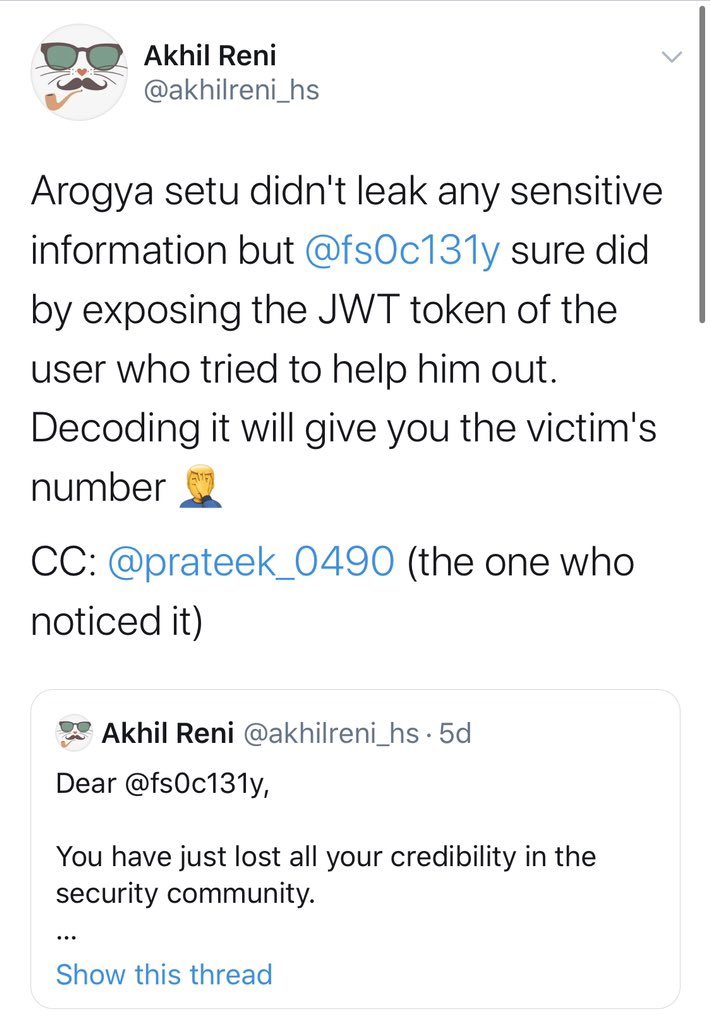
Something he needs to understand. Thanks to the person for pointing it out. Hopefully next time he will blur or hide the tokens before posting videos or pics.
If you want to go in more technical details you can go through this : https://medium.com/@N1gh7m4r3/explaining-exposing-imaginary-arogyasetu-privacy-issue-433a6dc7b76e">https://medium.com/@N1gh7m4r... and yeah getting blocked from him for asking technical things have become a standard in the mainstream hacking community. And this pic sums up that !
Also their reply is exactly what a team would reply when they receive such bug reports. The reply clearly mentions that the radius parameter is distance while in the article the hacker has taken distance as 5km (which is not a custom value). Seems he could not get what they meant
Some fellow brothers and sisters requested me to summarise the above said in brief. You can read this  https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">(in a single image as you requested for). Though to understand the points said here you may have to go through the tweets above
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">(in a single image as you requested for). Though to understand the points said here you may have to go through the tweets above https://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview
https://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">.

 Read on Twitter
Read on Twitter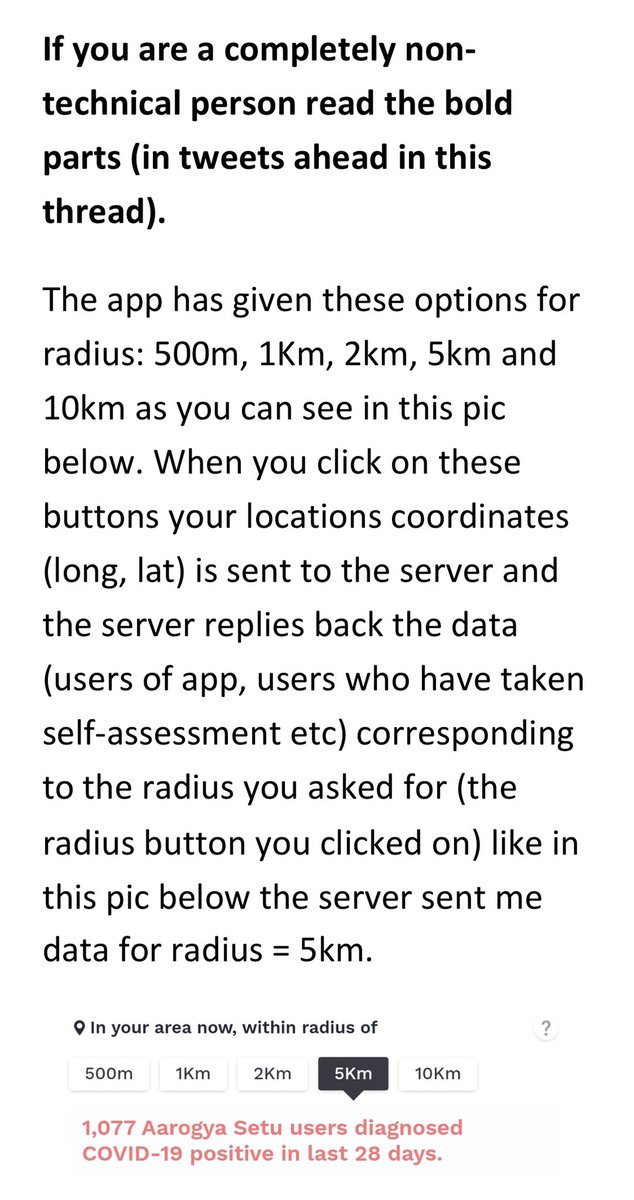





 to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team)." title="My suggestion for @UIDAI @SetuAarogya @GoI_MeitY @rsprasad @UmangOfficial_ @NPCI_BHIM @digilocker_ind @IRCTCofficial https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙏" title="Folded hands" aria-label="Emoji: Folded hands"> to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team)." class="img-responsive" style="max-width:100%;"/>
to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team)." title="My suggestion for @UIDAI @SetuAarogya @GoI_MeitY @rsprasad @UmangOfficial_ @NPCI_BHIM @digilocker_ind @IRCTCofficial https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙏" title="Folded hands" aria-label="Emoji: Folded hands"> to make few guidelines for bug hunters (those who find loopholes in websites or mobile applications and report them to responsible person or team)." class="img-responsive" style="max-width:100%;"/>

 (in a single image as you requested for). Though to understand the points said here you may have to go through the tweets abovehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face">https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">." title="Some fellow brothers and sisters requested me to summarise the above said in brief. You can read this https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">(in a single image as you requested for). Though to understand the points said here you may have to go through the tweets abovehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face">https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">." class="img-responsive" style="max-width:100%;"/>
(in a single image as you requested for). Though to understand the points said here you may have to go through the tweets abovehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face">https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">." title="Some fellow brothers and sisters requested me to summarise the above said in brief. You can read this https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">(in a single image as you requested for). Though to understand the points said here you may have to go through the tweets abovehttps://abs.twimg.com/emoji/v2/... draggable="false" alt="☝️" title="Up pointing index" aria-label="Emoji: Up pointing index">in this thread. This is in a way overview https://abs.twimg.com/emoji/v2/... draggable="false" alt="🙂" title="Slightly smiling face" aria-label="Emoji: Slightly smiling face">https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">." class="img-responsive" style="max-width:100%;"/>


