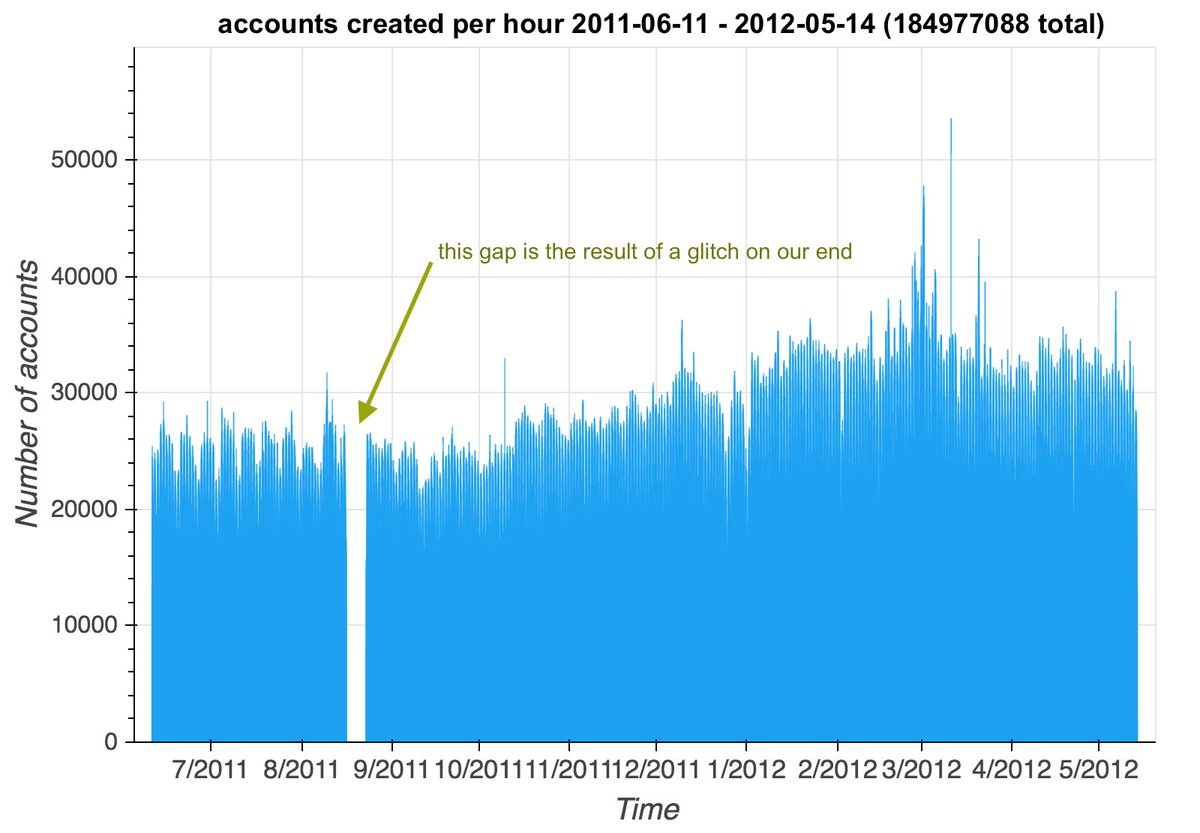
We left this ID-based profile harvesting process running after posting this thread, and checked on it today to find that we& #39;ve accumulated profile information for 184 million accounts created in 2011 and 2012. Can we pull out some botnets? #ThursdayThoughts
cc: @ZellaQuixote https://twitter.com/conspirator0/status/1236552456869470208">https://twitter.com/conspirat...
cc: @ZellaQuixote https://twitter.com/conspirator0/status/1236552456869470208">https://twitter.com/conspirat...
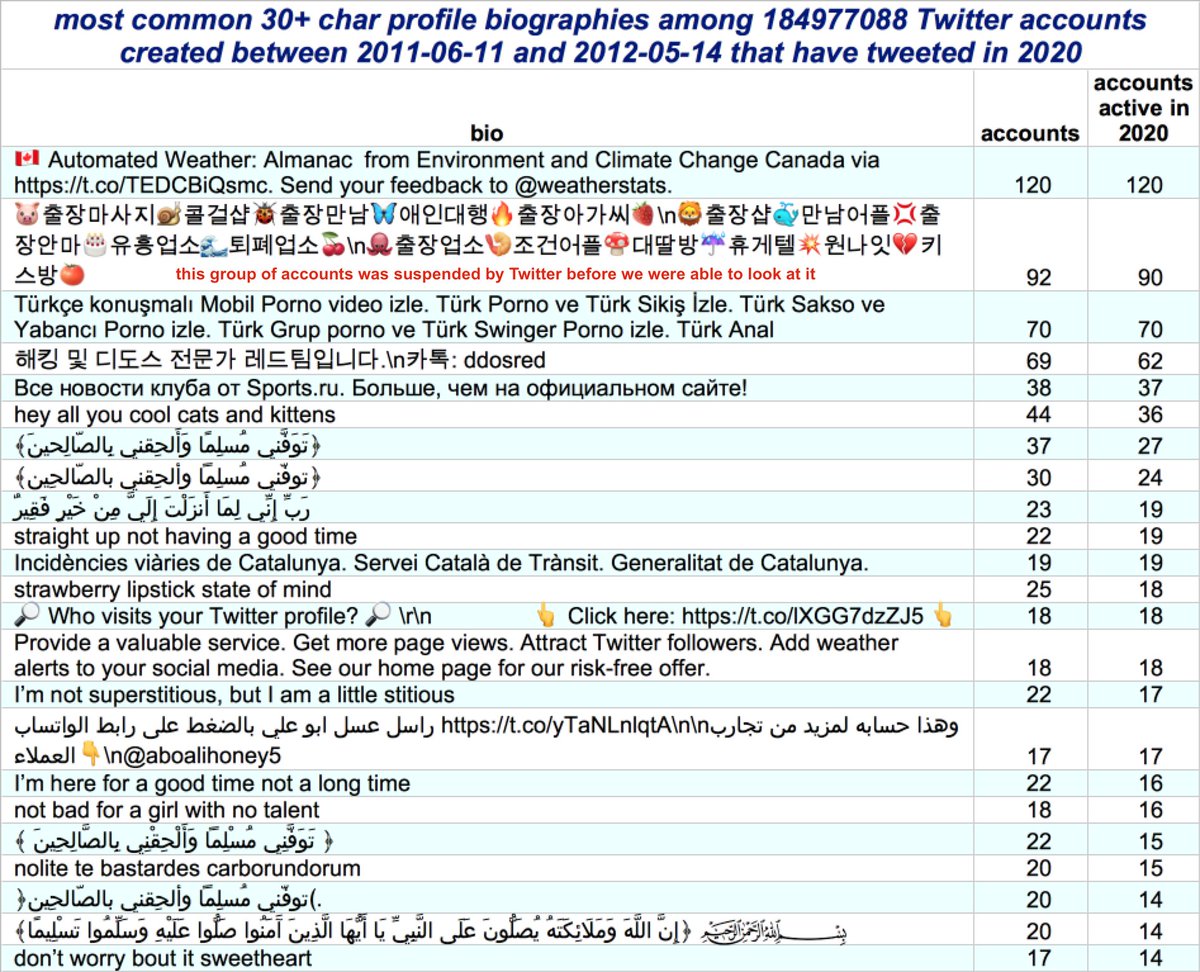
We wanted to find bot/sockpuppet networks made up of long-ago created accounts that are still active today (or have recently reactivated.) To this end, we narrowed our search to groups of accounts with identical biographies where at least 2/3 of the accounts had tweeted in 2020.
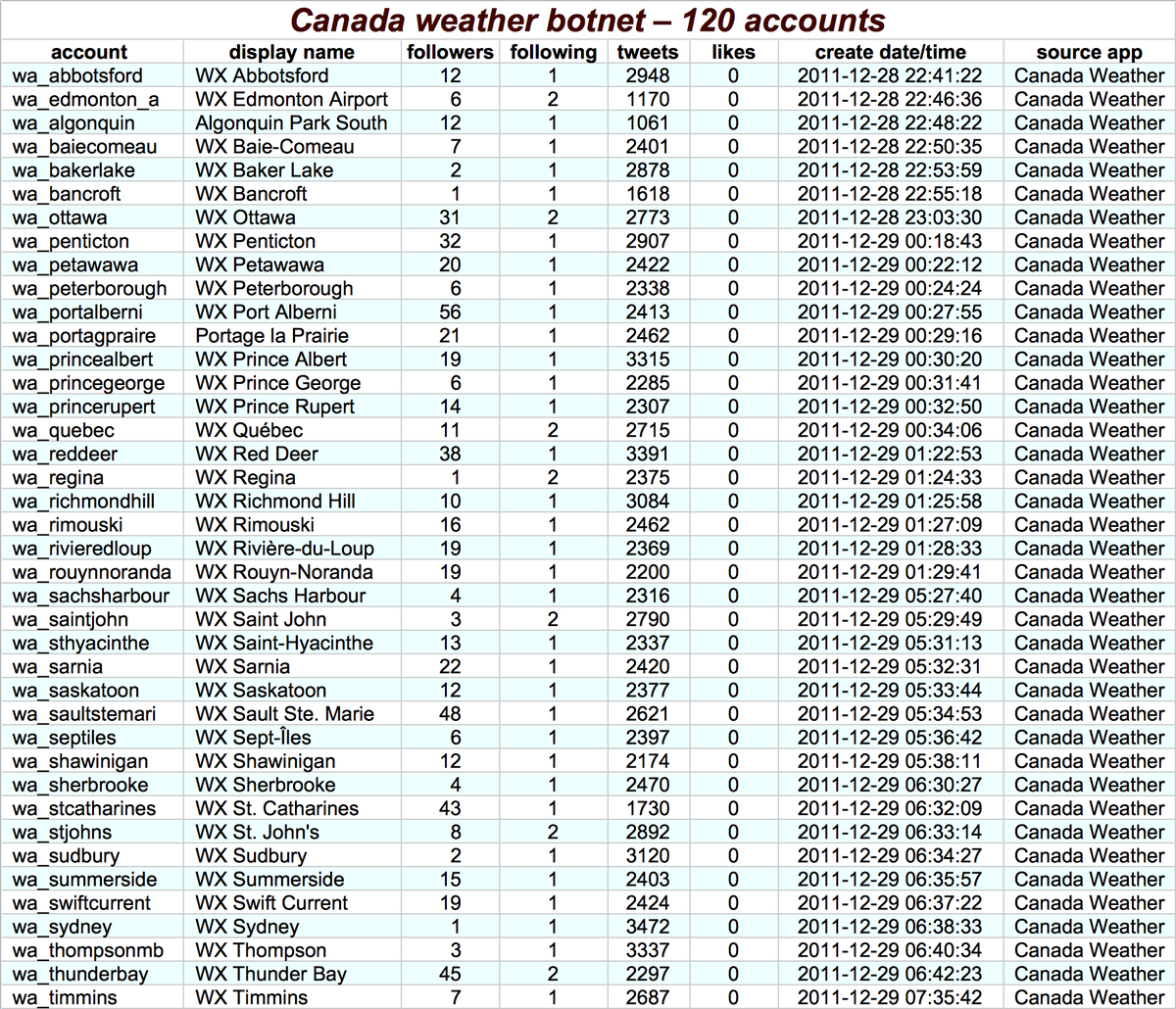
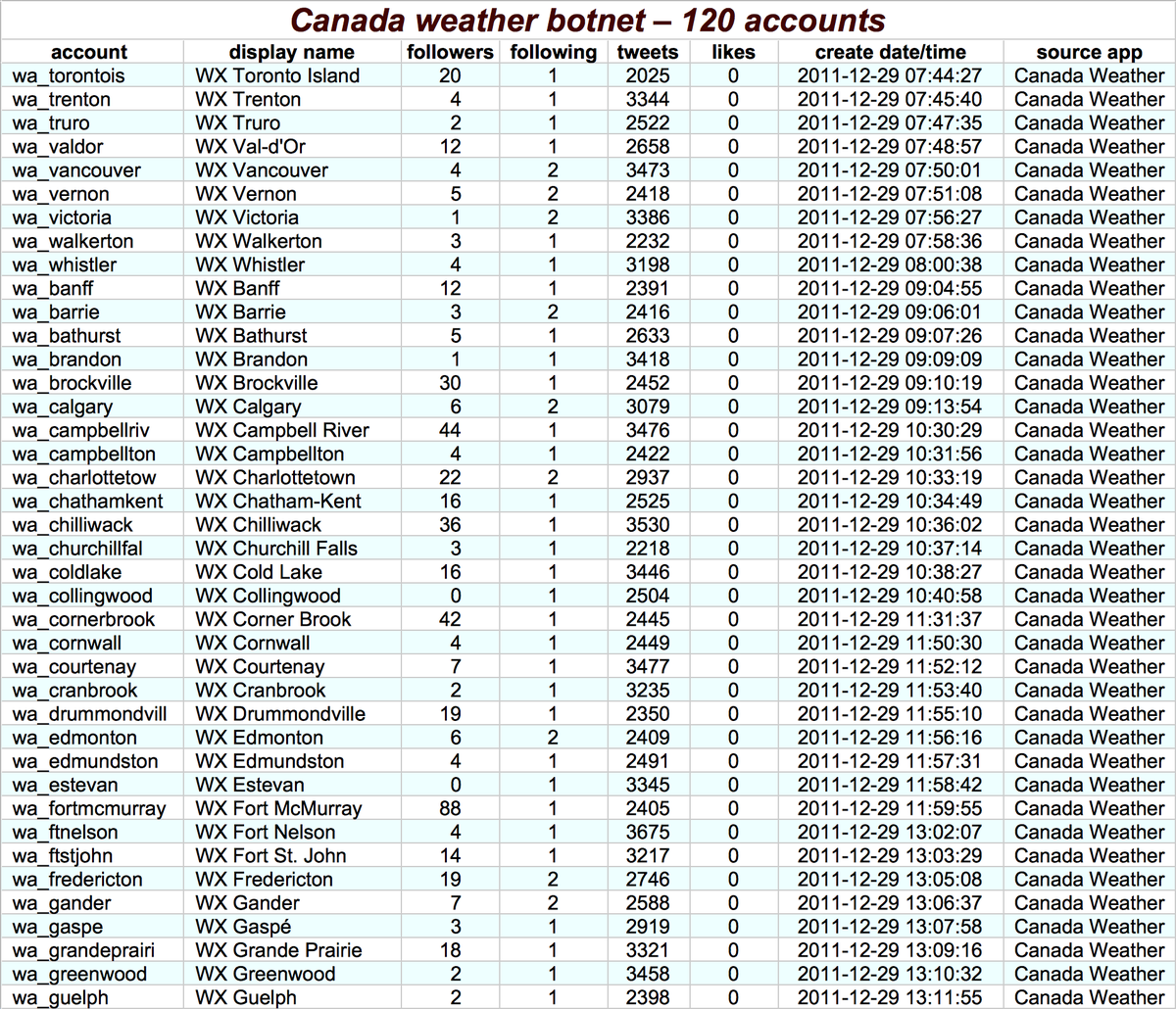
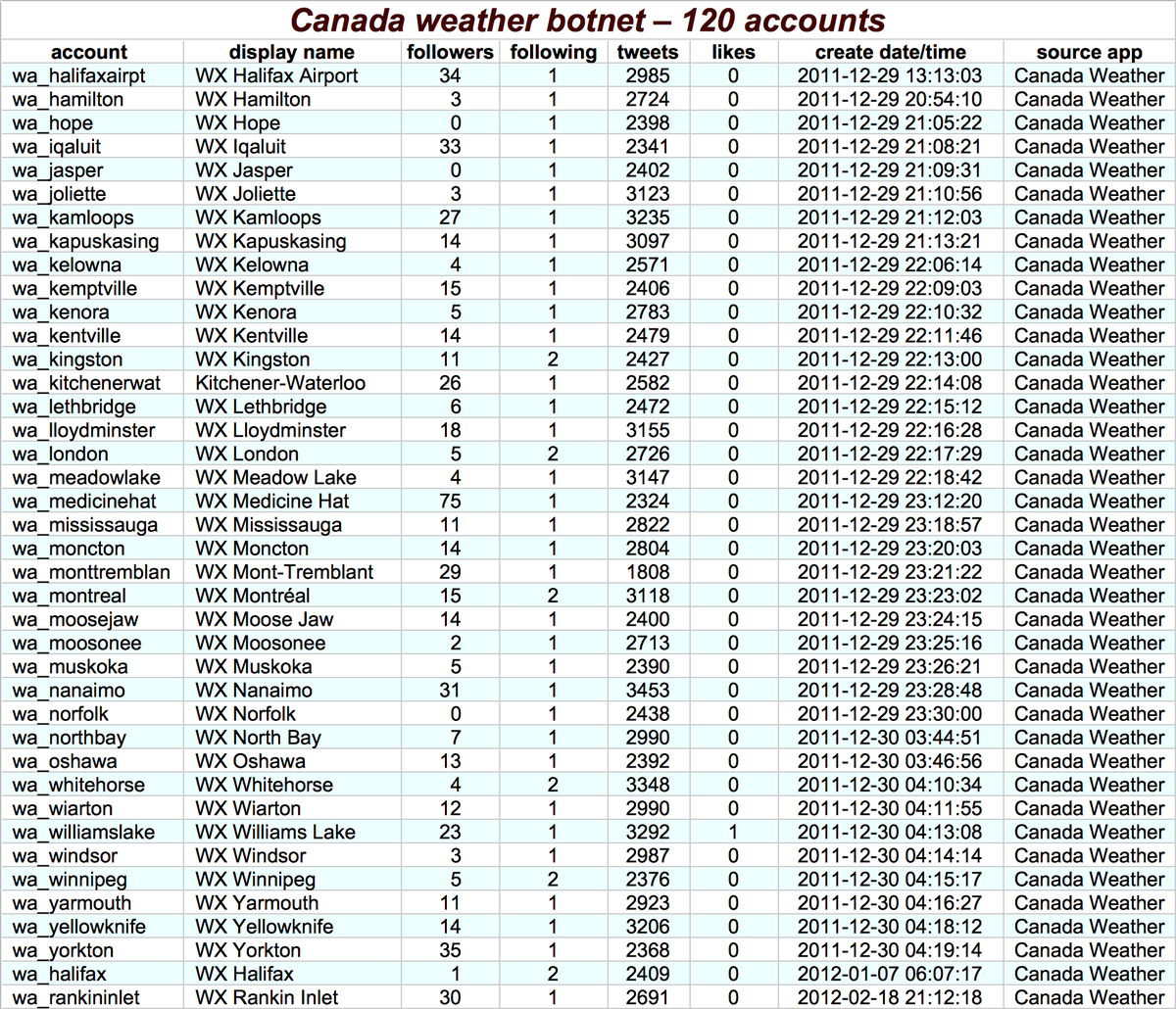
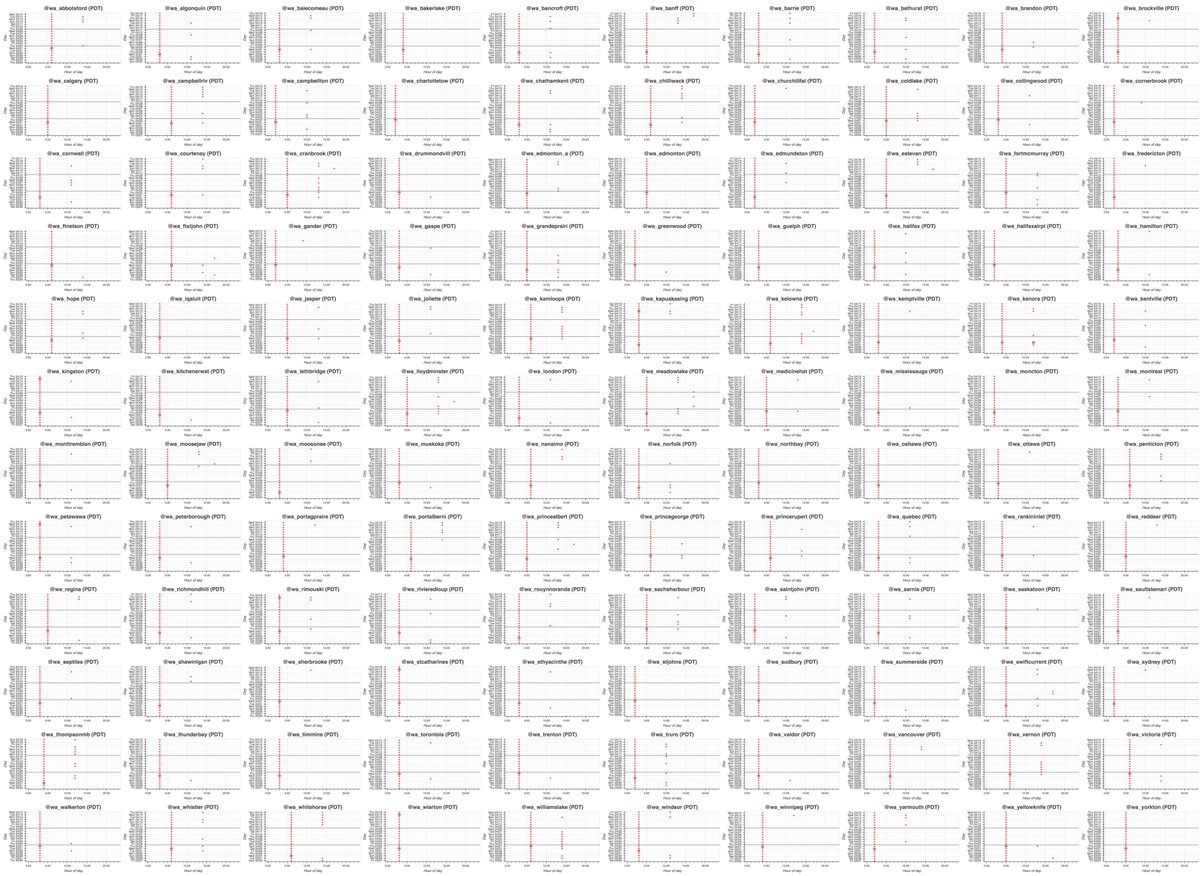
The first botnet we looked at strikes us as relatively benign. It consists of 120 automated accounts (118 created in bulk) that tweet daily weather reports for various locations in Canada once a day via an app called "Canada Weather." Moving on. . .
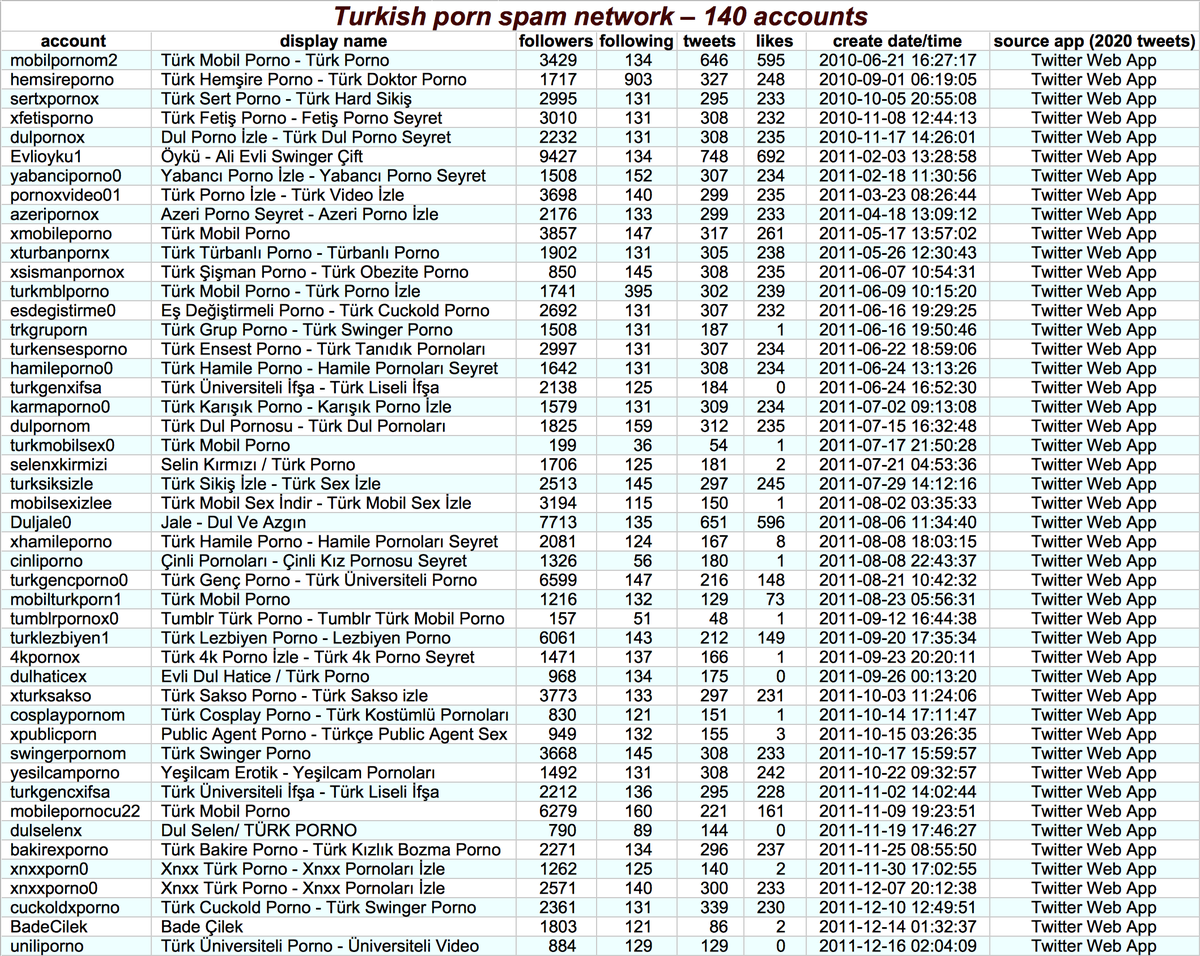
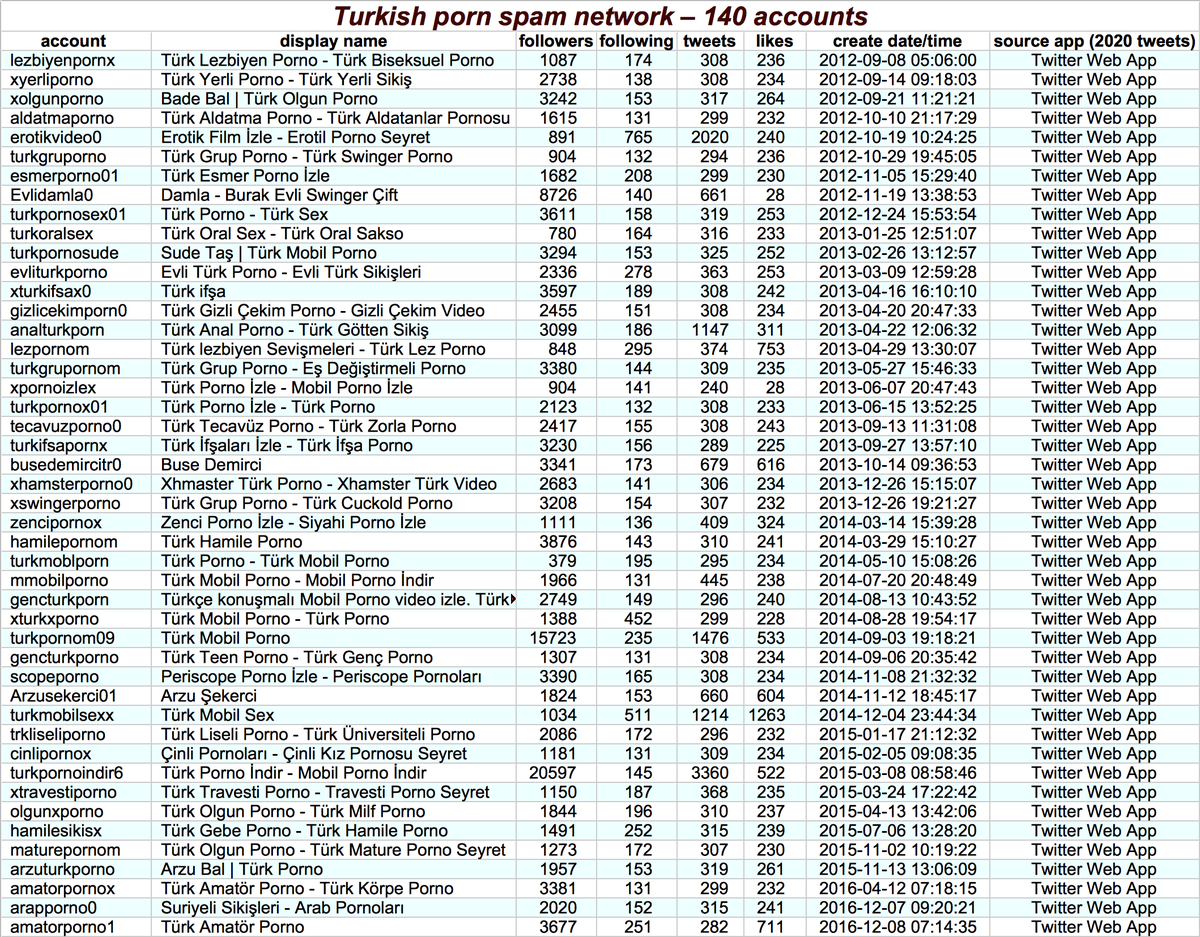
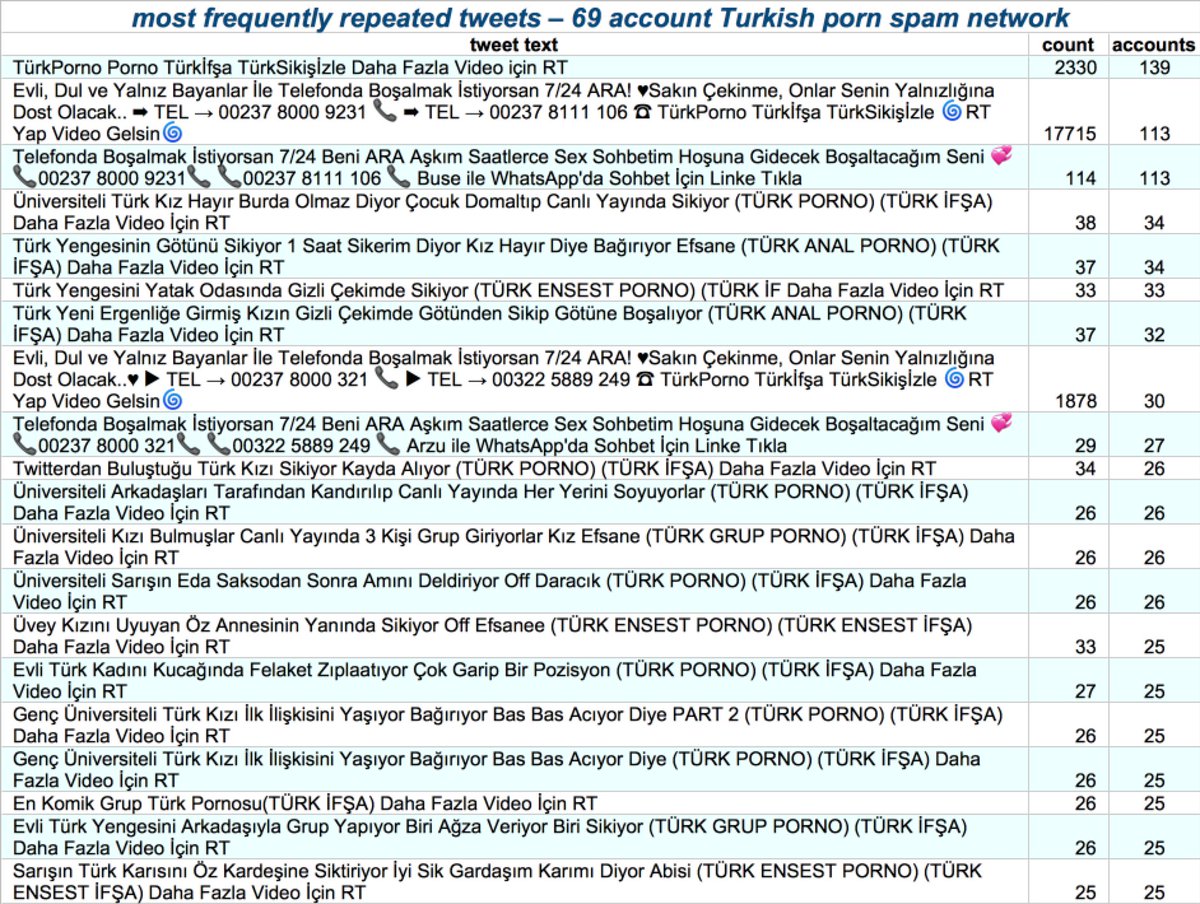
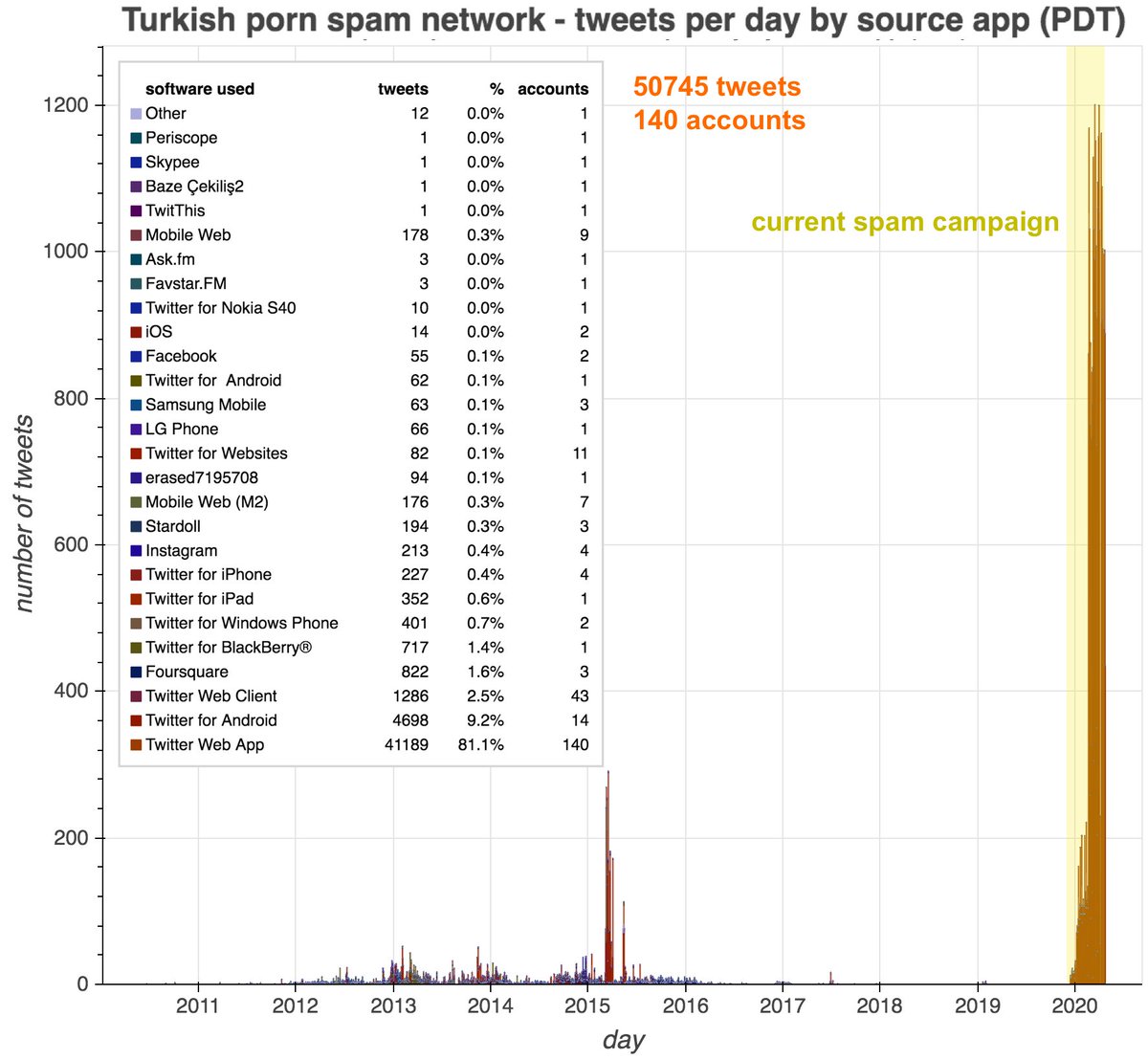
The second botnet we examined consists of 140 Turkish accounts tweeting porn spam (no tweet screenshots included because NSFW) via Twitter Web App. (The fact that all 140 accounts are tweeting via the website and none via the phone is itself a potential sign of automation.)
This network has a couple of other behaviors that indicate automation despite the accounts theoretically tweeting via the Twitter website. Firstly, they repeat tweets, both within and across accounts. . .
Secondly, the network tweets in a very mechanical fashion, continually cycling between accounts and tweeting (usually) nine times on each. It& #39;s possible this is a human doing a very boring job, but we& #39;re inclined to think it& #39;s automated as this behavior would be easy to script.
One final observation on the Turkish pornbot network: these accounts were dormant for years before their present spam campaign, and the accounts involved appear to have been not only repurposed (old content mostly doesn& #39;t look like porn) but also renamed.
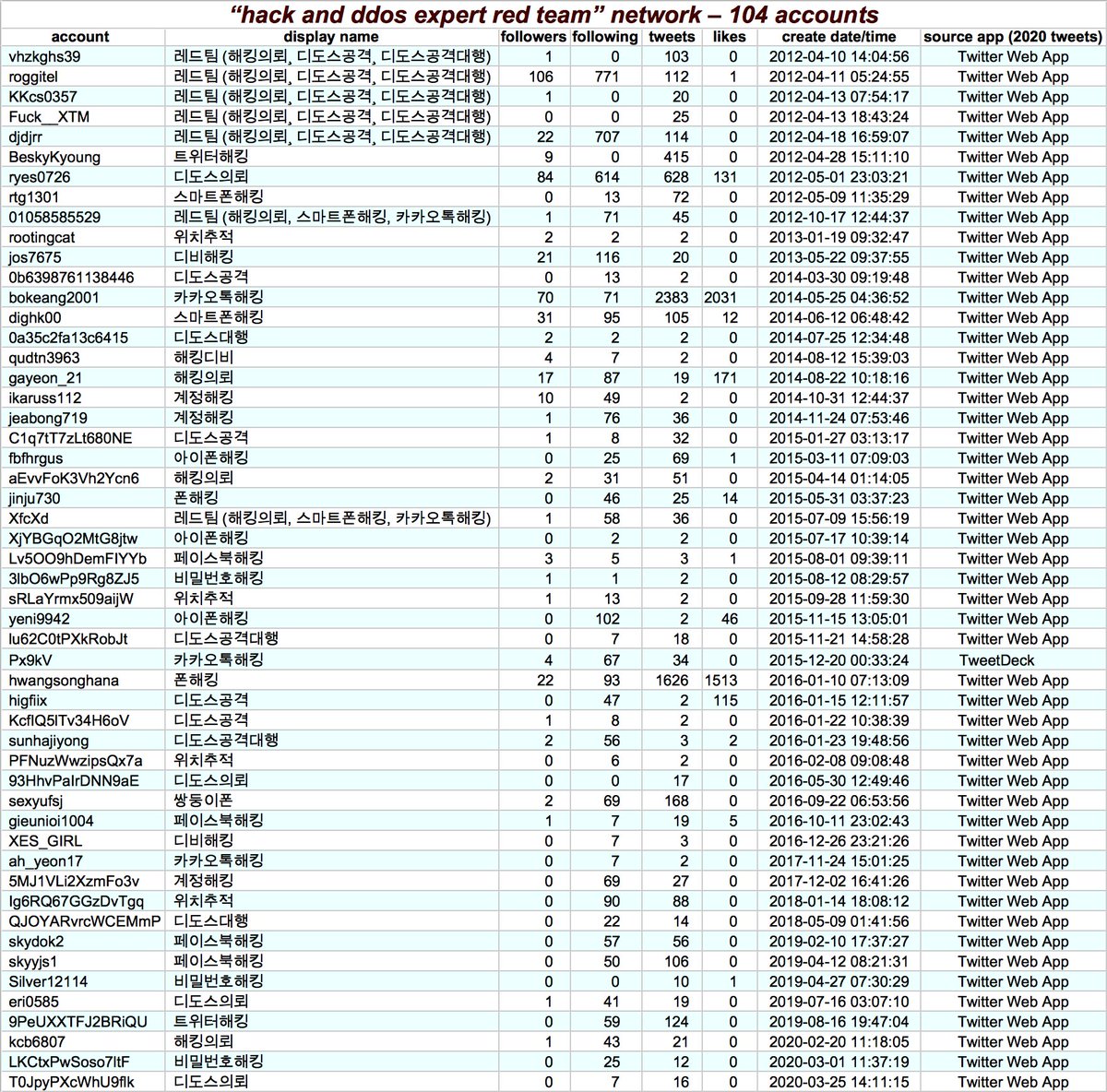
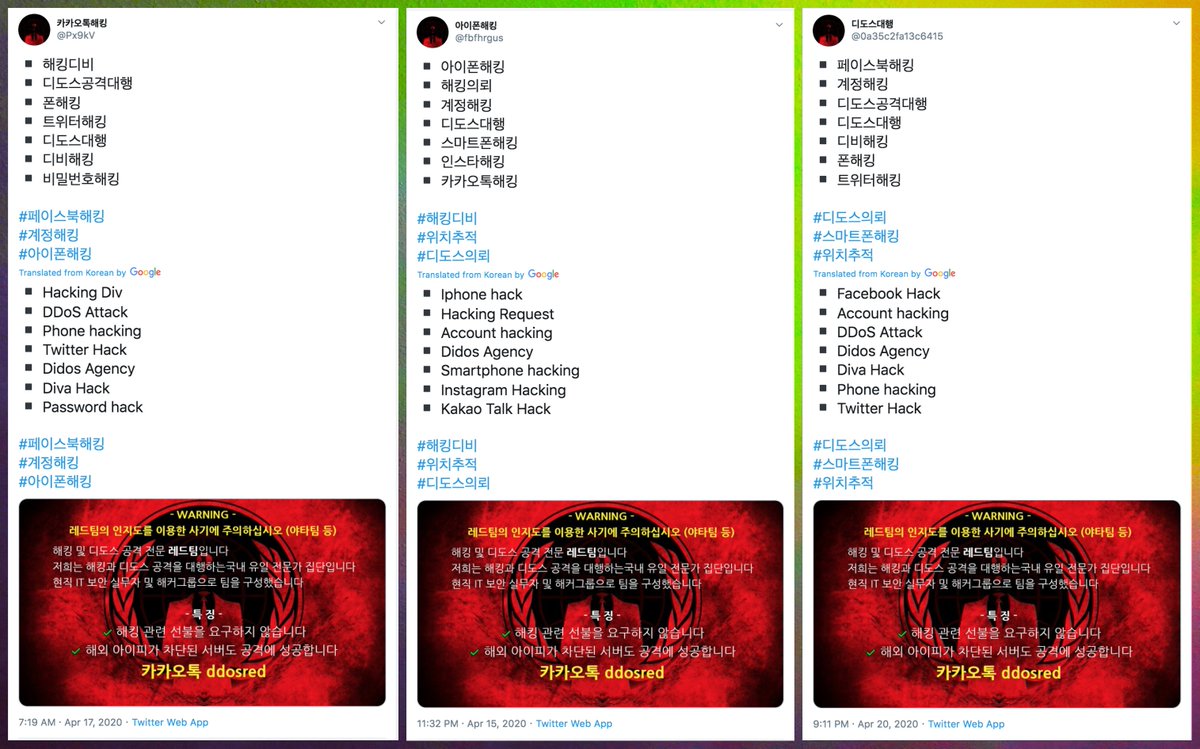
The third network we looked at is a group of 104 accounts tweeting in Korean with identical profile pics that claim to be a "hack and ddos expert red team" and appear to be advertising various hacking services.
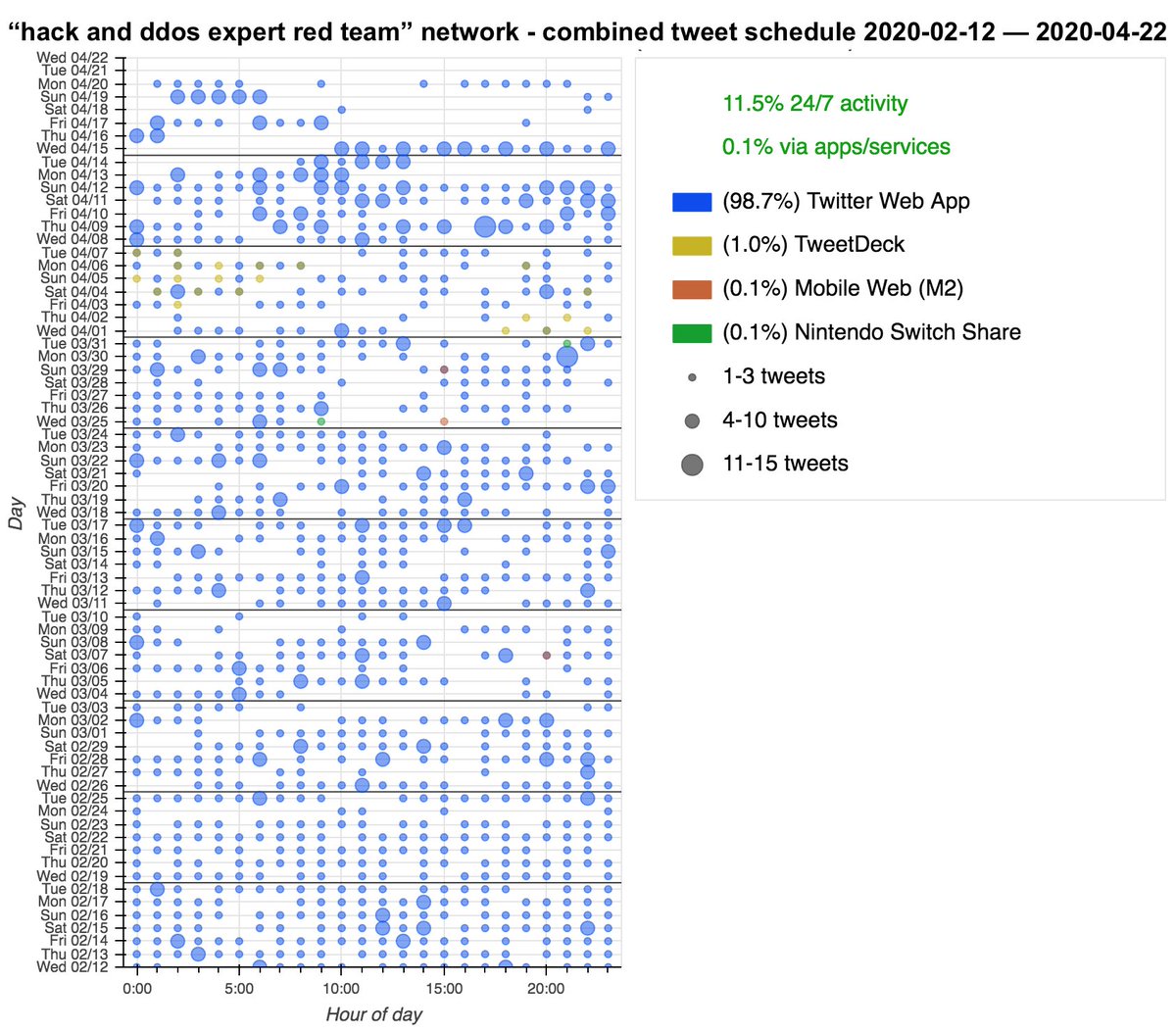
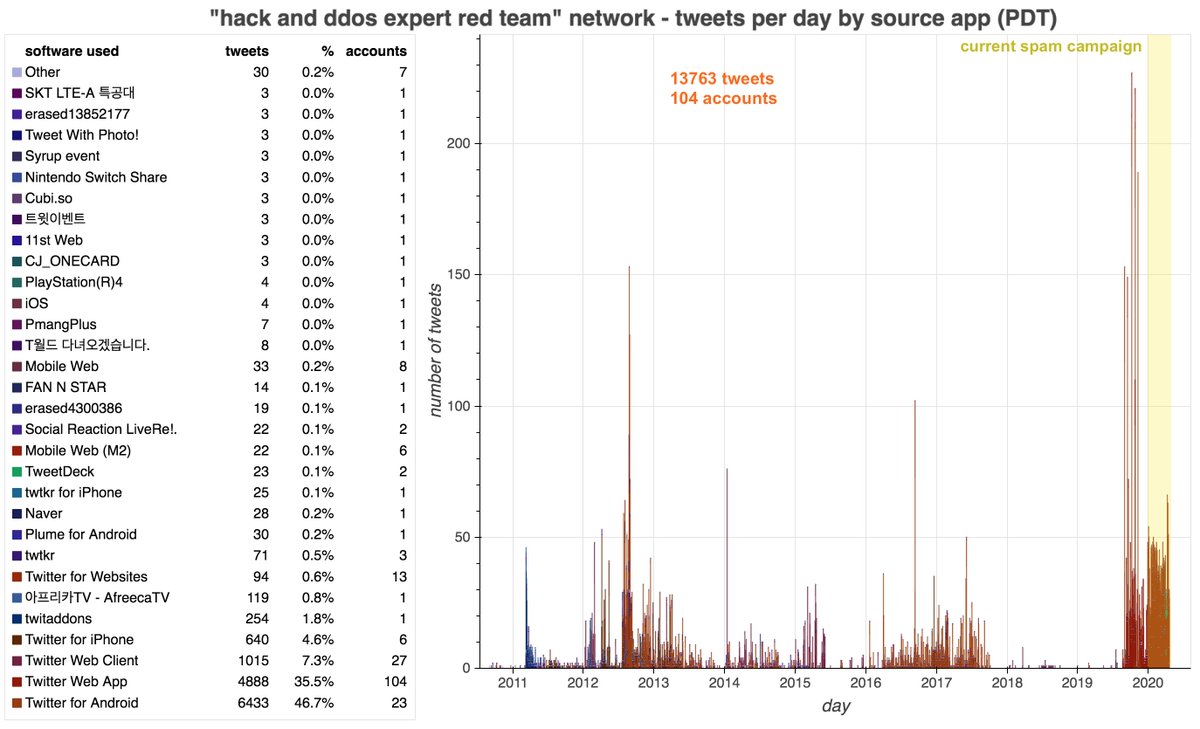
Much like the Turkish pornbots, this network currently tweets almost exclusively via Twitter Web App (again, organic large-scale activity generally involves the phone apps too.) The content is repetitive but duplicate tweets are rare as the list of services gets shuffled.
Also like the Turkish porn botnet, the Korean "hack and ddos expert red team" botnet appears to have emerged from a period of dormancy. We didn& #39;t see any signs of renames with this group, however.
We& #39;ll stop there for now, but will be looking at more of the botnets surfaced by this technique and may add those which we find sufficiently interesting.

 Read on Twitter
Read on Twitter