Bug bounty platform vendors:
Your NDAs are creating a huge amount of unnecessary friction between security researchers and the customers you are supposedly helping.
You realize that NDAs are *not* part of the ISO standards for vuln disclosure and handling, right?
Cut that out.
Your NDAs are creating a huge amount of unnecessary friction between security researchers and the customers you are supposedly helping.
You realize that NDAs are *not* part of the ISO standards for vuln disclosure and handling, right?
Cut that out.
Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.
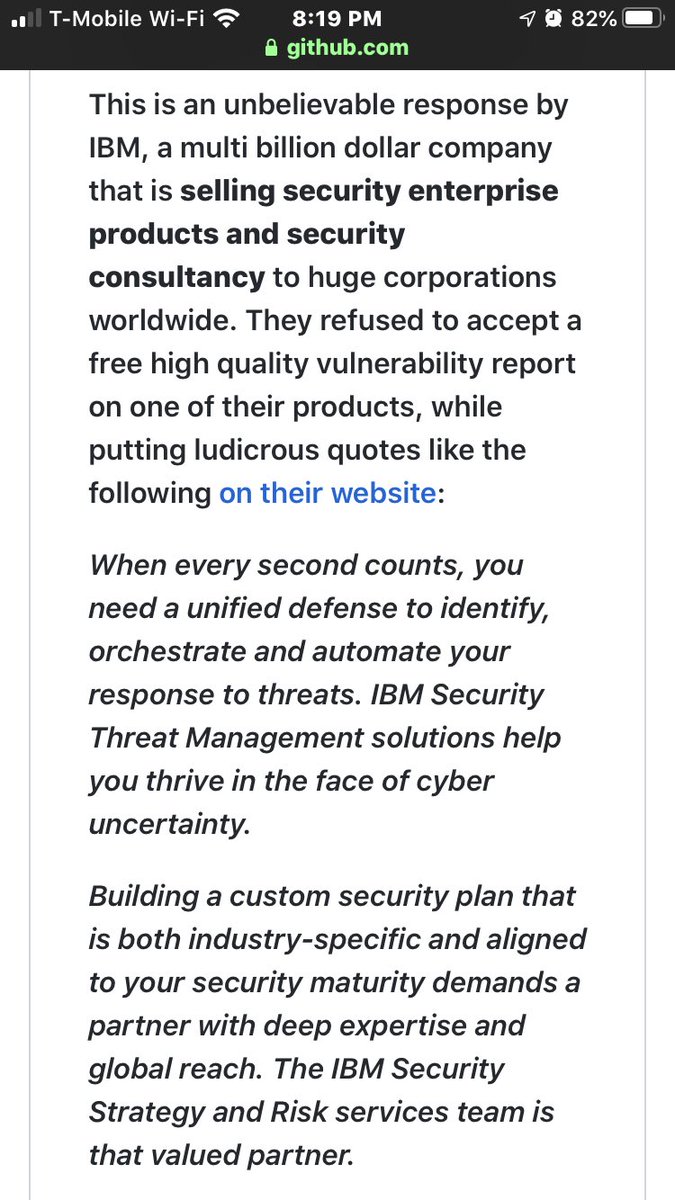
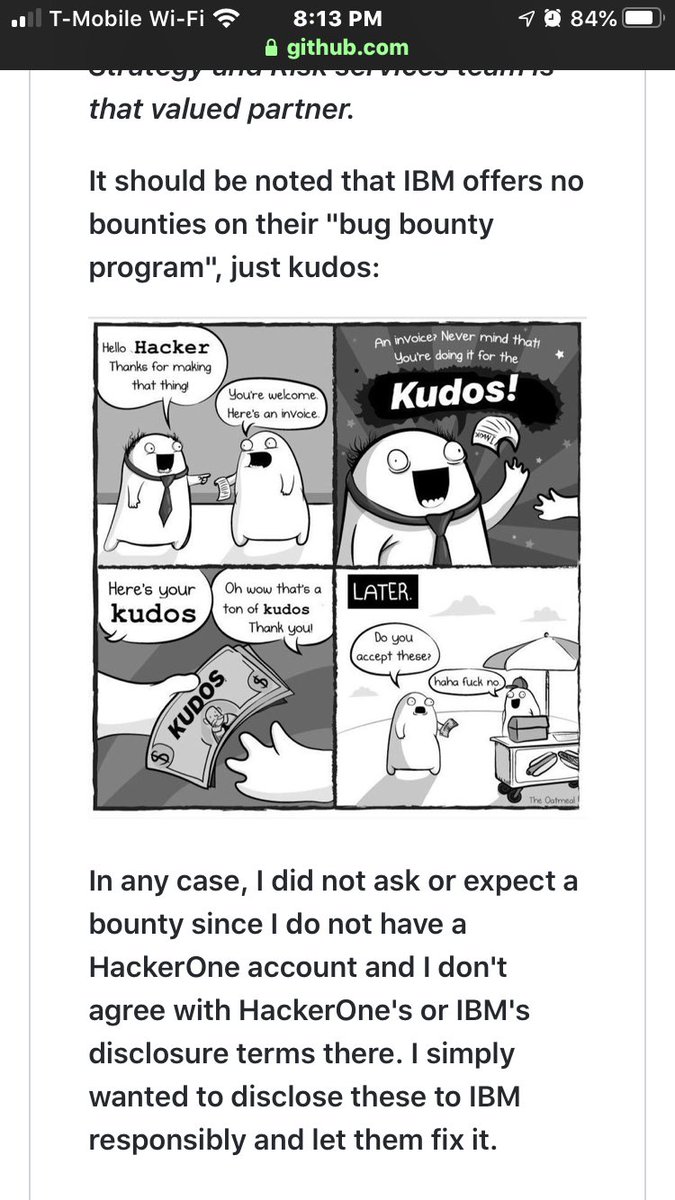
IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.
You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)">
https://github.com/pedrib/PoC/blob/master/advisories/IBM/ibm_drm/ibm_drm_rce.md
/ht">https://github.com/pedrib/Po... @tqbf
IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.
You can’t make this up.
https://github.com/pedrib/PoC/blob/master/advisories/IBM/ibm_drm/ibm_drm_rce.md
/ht">https://github.com/pedrib/Po... @tqbf
I don’t always feel like Cassandra, but when I do, it’s because I’ve been saying BB platforms’ default NDAs are ruining vuln disclosure since I worked for one.
https://twitter.com/wdormann/status/1252573192515960832?s=21">https://twitter.com/wdormann/... https://twitter.com/wdormann/status/1252573192515960832">https://twitter.com/wdormann/...
https://twitter.com/wdormann/status/1252573192515960832?s=21">https://twitter.com/wdormann/... https://twitter.com/wdormann/status/1252573192515960832">https://twitter.com/wdormann/...
Do I hear a deeper-vocal range echo in here?
I think this opinion is only unpopular among bug bounty platform vendors & the companies they truck into thinking this is normal or ok.
I think this opinion is only unpopular among bug bounty platform vendors & the companies they truck into thinking this is normal or ok.

 Read on Twitter
Read on Twitter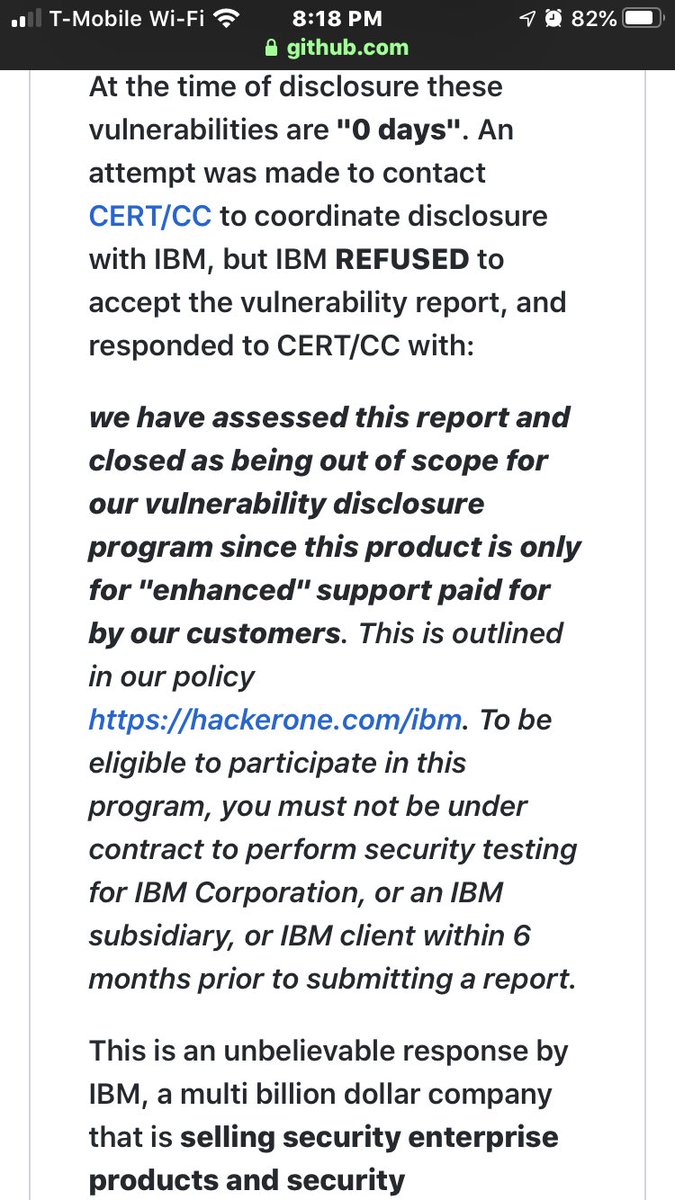 https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">
https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">
 https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">
https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">
 https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">
https://github.com/pedrib/Po... @tqbf" title="Every time I see another 0day drop because of bug bounty platform-induced NDA friction, I die a little more inside.IBM’s bug bounty platform provider rejected a CERT/CC vuln coordination attempt as OUT OF SCOPE.You can’t make this up. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🤦🏽♀️" title="Woman facepalming (medium skin tone)" aria-label="Emoji: Woman facepalming (medium skin tone)"> https://github.com/pedrib/Po... @tqbf">


