This is certainly interesting. We have two kits on this domain
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="💸" title="Money with wings" aria-label="Emoji: Money with wings"> elite bank[.]zip - AA419 scam (33.3MB)
https://abs.twimg.com/emoji/v2/... draggable="false" alt="💸" title="Money with wings" aria-label="Emoji: Money with wings"> elite bank[.]zip - AA419 scam (33.3MB)
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🎟️" title="Admission tickets" aria-label="Emoji: Admission tickets"> themeforest-ZzAltF1v-coopbank-banking-financial-credits-template.zip - Co-Op Credential Stealer kit (9MB) https://twitter.com/whale_it/status/1249598017960902657">https://twitter.com/whale_it/...
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🎟️" title="Admission tickets" aria-label="Emoji: Admission tickets"> themeforest-ZzAltF1v-coopbank-banking-financial-credits-template.zip - Co-Op Credential Stealer kit (9MB) https://twitter.com/whale_it/status/1249598017960902657">https://twitter.com/whale_it/...
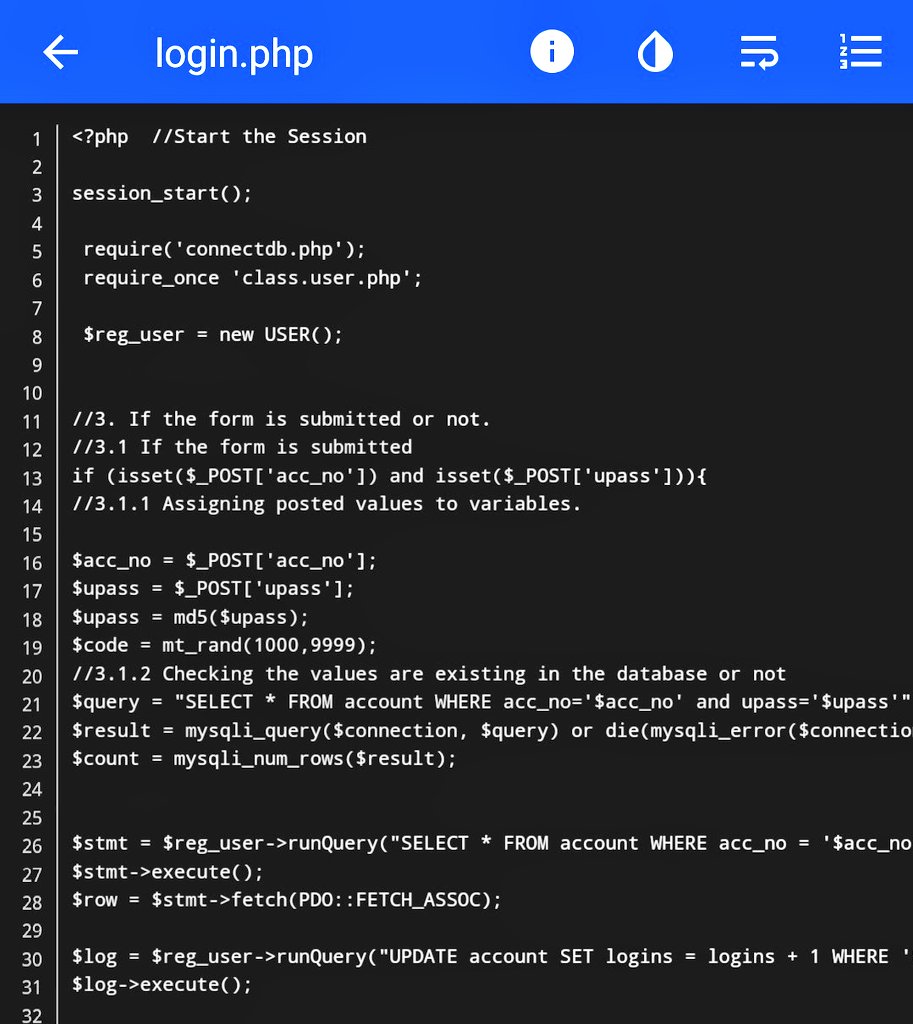
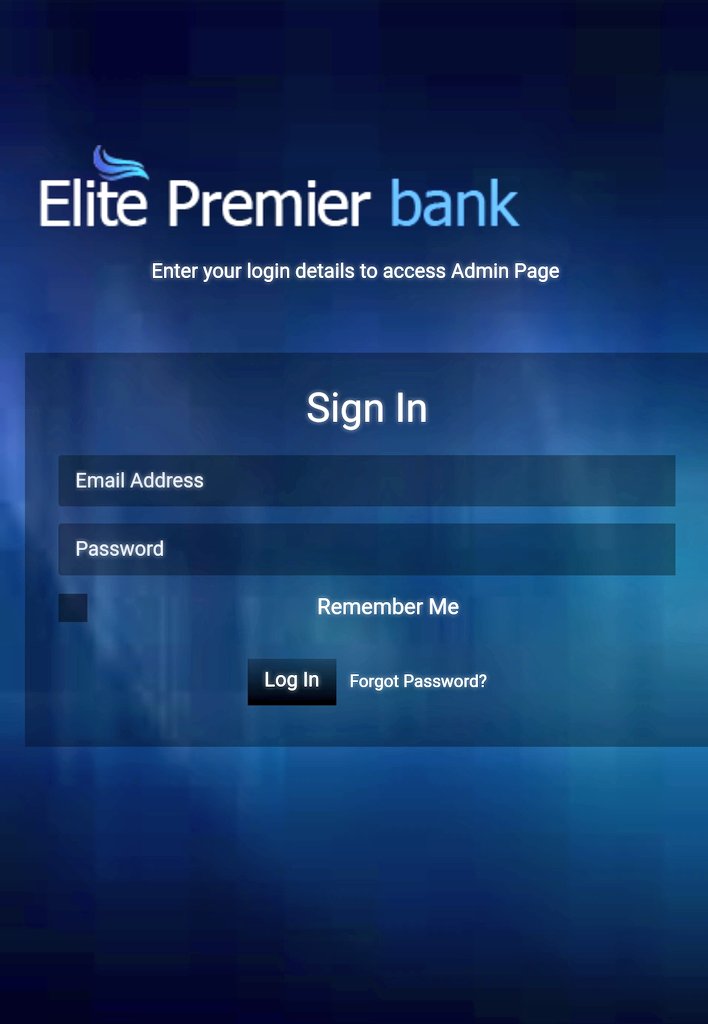
The first kit called elite bank is a fraud kit used to defraud victims by creating fake banks and interacting with targets to steal large sums of money.
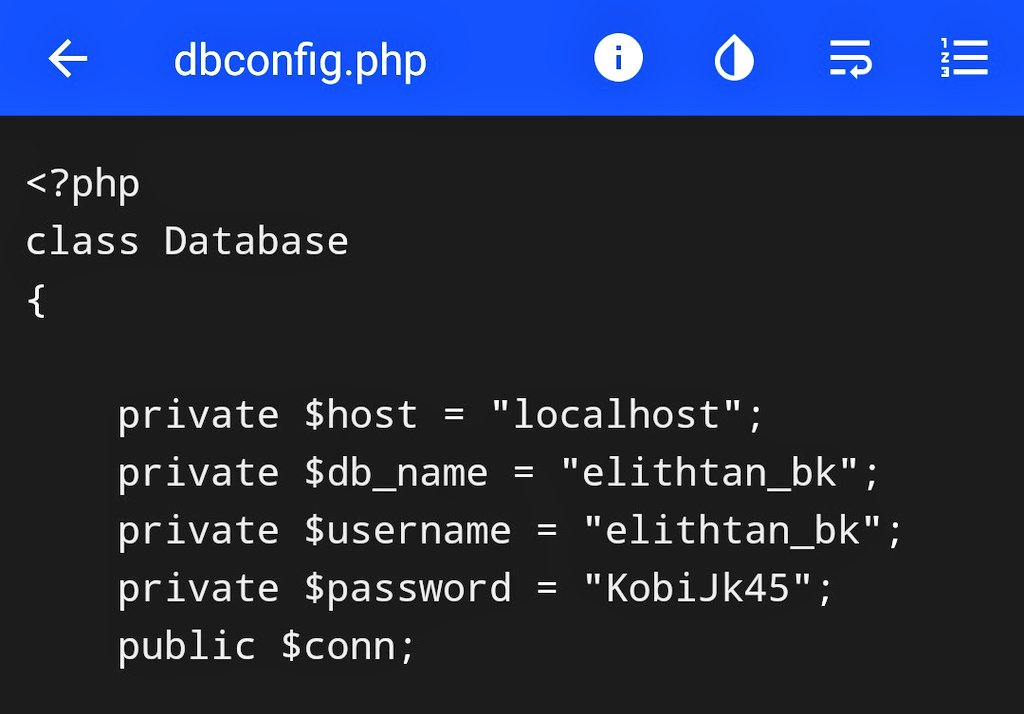
The kit is a copy and linked to
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians"> hxxps://elitepremierplc.com/index.html
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians"> hxxps://elitepremierplc.com/index.html
Screenshot attached.
The kit is a copy and linked to
Screenshot attached.
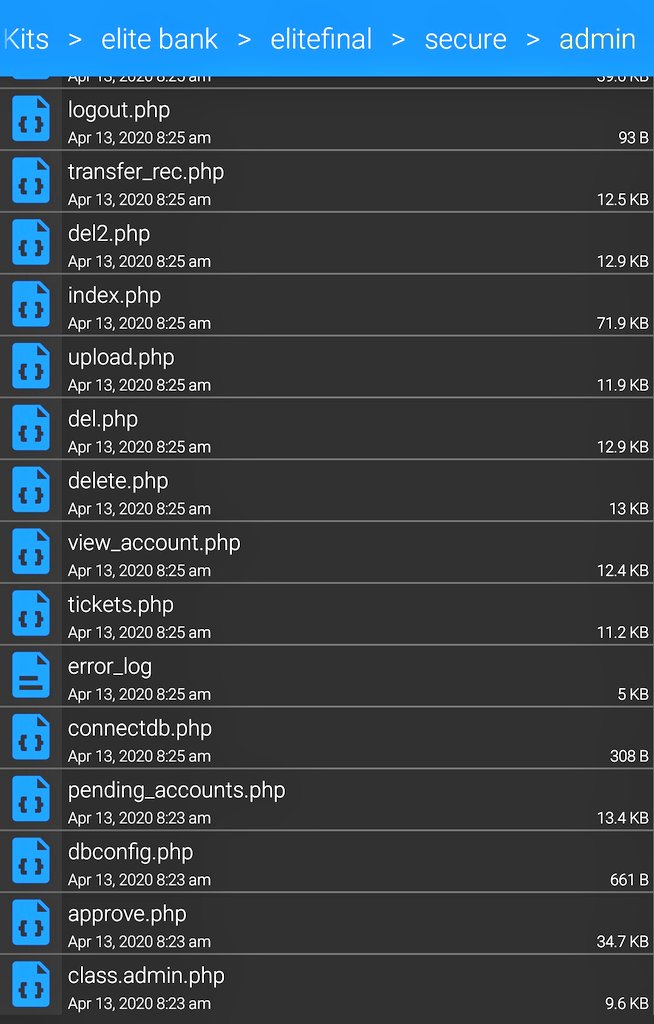
The kit is complex with many advanced features allowing for a victim to actually login to the fake website as part of the lure and many of links work on the site opposed to regular cred phishing where they usually only display a splash page.
The site also contains an admin portal for the cyber actors to access the database and view data from victims. This is not a credential stealing campaign; however, password reuse is a major concern due to victim targeting.
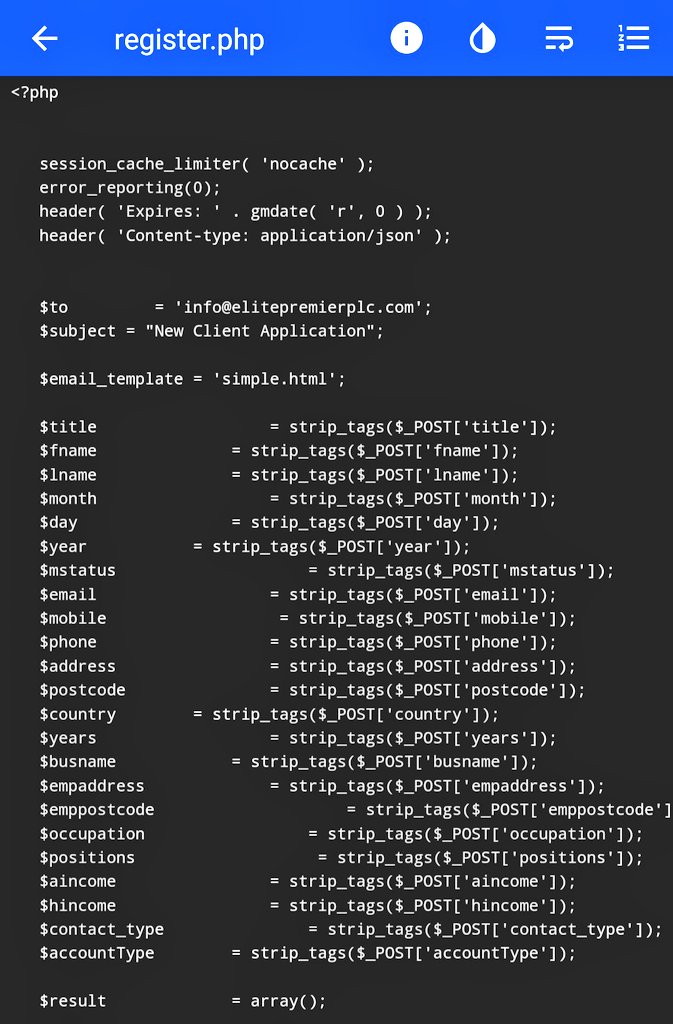
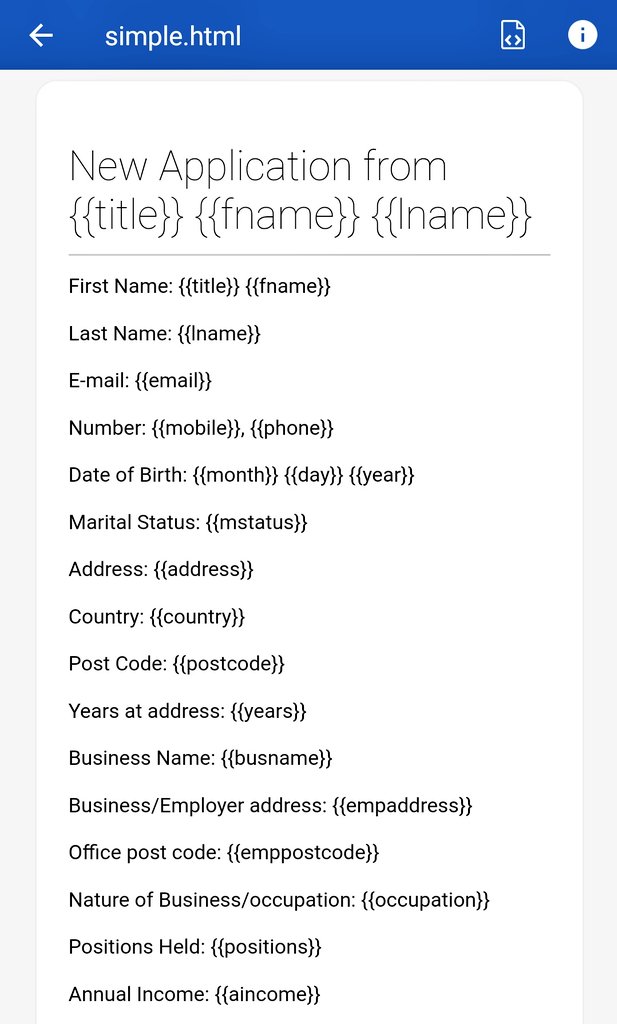
The main reason for the site is the lure victims into believing this is a real bank and the cyber actors instruct the victim to apply for a bank account by using the form. This is all part of building trust between them when, ultimately, they actor control the & #39;bank& #39;
Once a victim has an account there is a number of things they can do on the account making it appear even more legitimate. The scam can now do a number of things. Usually the cyber actors will & #39;deposit& #39; a large sum of money into the account and ask the victim to hold it for them.
The kit is well made, complex, and professional. Anyone who blames a victim for falling for these scams do not understand them. These cyber actors are scum and real world attribution will come.
This thread gets my Elite Premier Bank seal of approval
This thread gets my Elite Premier Bank seal of approval
Hosting Information:
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/elitepremierplc.com (198.54.114.241) @Namecheap
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/elitepremierplc.com (198.54.114.241) @Namecheap
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔐" title="Closed lock with key" aria-label="Emoji: Closed lock with key">TLS by @SectigoHQ
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔐" title="Closed lock with key" aria-label="Emoji: Closed lock with key">TLS by @SectigoHQ
@urlscanio Link https://urlscan.io/result/e41e7581-56a6-4b37-9dfe-56948a73eaaf">https://urlscan.io/result/e4...
@urlscanio Link https://urlscan.io/result/e41e7581-56a6-4b37-9dfe-56948a73eaaf">https://urlscan.io/result/e4...
Second domain hosting information:
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/as-samirinternationalbank.net/elitefinal (198.54.125.205) @Namecheap
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/as-samirinternationalbank.net/elitefinal (198.54.125.205) @Namecheap
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔐" title="Closed lock with key" aria-label="Emoji: Closed lock with key">TLS by @SectigoHQ
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔐" title="Closed lock with key" aria-label="Emoji: Closed lock with key">TLS by @SectigoHQ
@urlscanio link: https://urlscan.io/result/fc77101c-79fd-47f8-bd6c-be47645004ed">https://urlscan.io/result/fc...
@urlscanio link: https://urlscan.io/result/fc77101c-79fd-47f8-bd6c-be47645004ed">https://urlscan.io/result/fc...
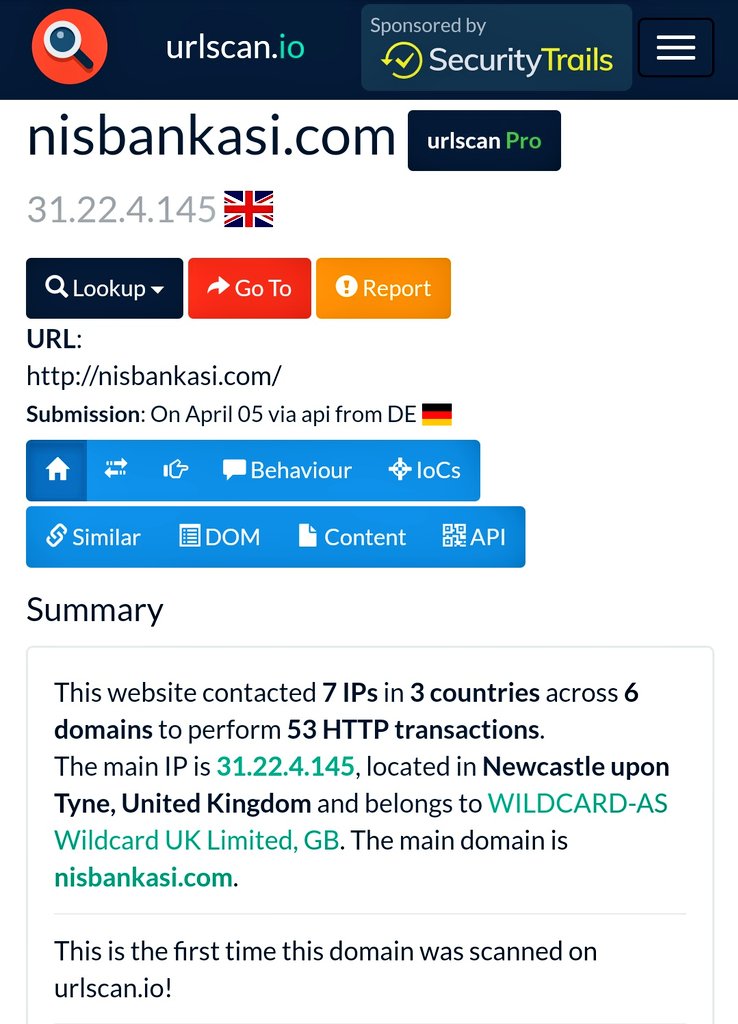
Using a page hash pivot I& #39;ve found another domain linked to the same scam
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/nisbankasi.com (31.22.4.145) @Wildcard_Net
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/nisbankasi.com (31.22.4.145) @Wildcard_Net
@urlscanio link: https://urlscan.io/result/f72a5ee0-1cf5-4c16-996f-ce4f12276f0f/">https://urlscan.io/result/f7...
@urlscanio link: https://urlscan.io/result/f72a5ee0-1cf5-4c16-996f-ce4f12276f0f/">https://urlscan.io/result/f7...
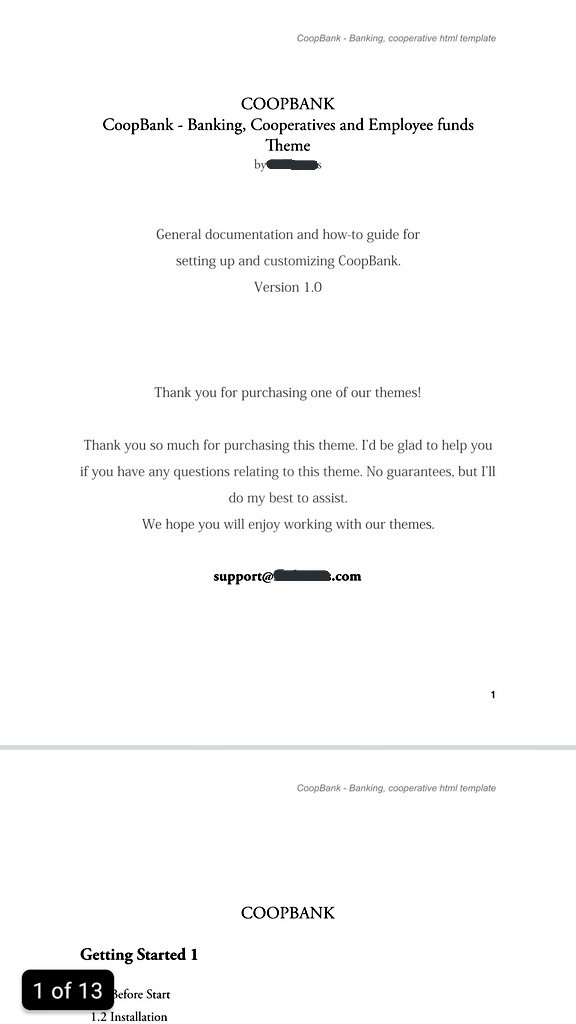
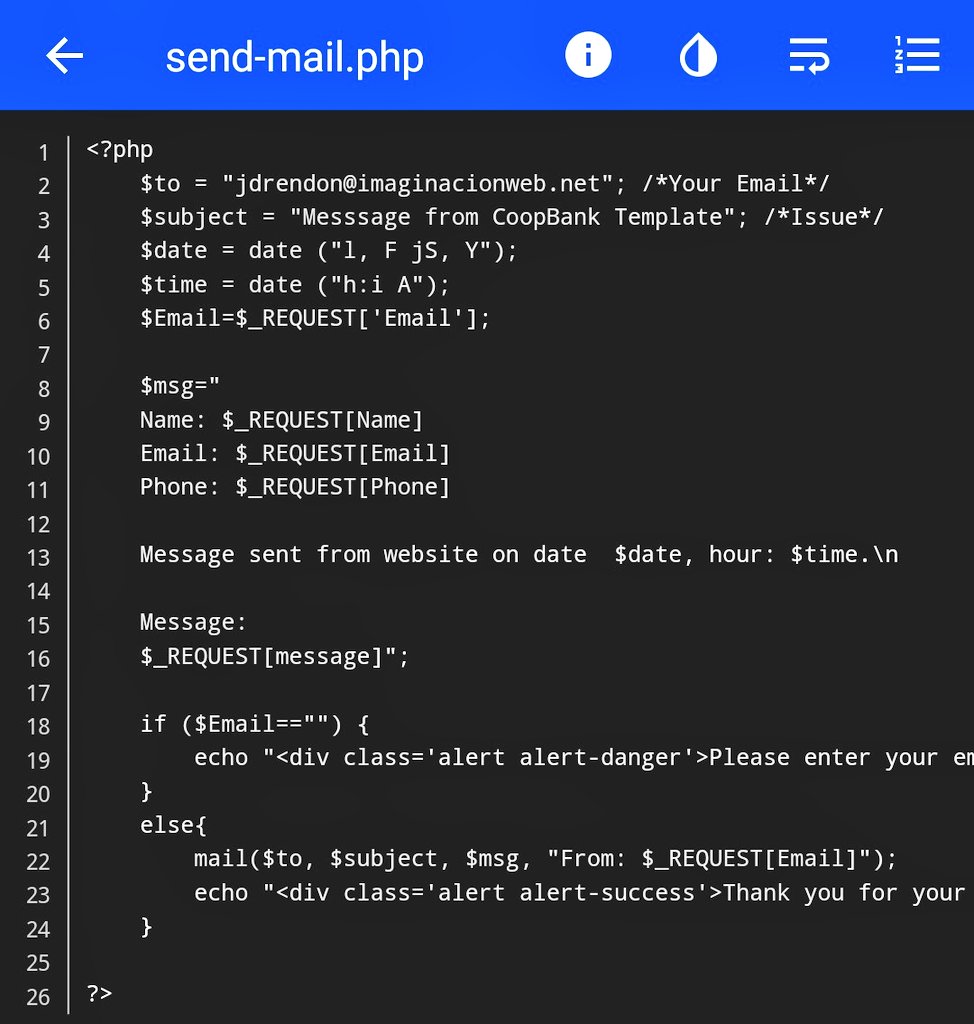
The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become.  https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">
Long thread. Might be of interest to you!
@dave_daves @James_inthe_box @JAMESWT_MHT @JRoosen @nullcookies @gcluley @thecyberwire @bad_packets @Bank_Security @unmaskparasites
@Ledtech3 @pmelson @executemalware
@Beeker51 @KB_Intel
Thanks!
@dave_daves @James_inthe_box @JAMESWT_MHT @JRoosen @nullcookies @gcluley @thecyberwire @bad_packets @Bank_Security @unmaskparasites
@Ledtech3 @pmelson @executemalware
@Beeker51 @KB_Intel
Thanks!

 Read on Twitter
Read on Twitter hxxps://elitepremierplc.com/index.htmlScreenshot attached." title="The first kit called elite bank is a fraud kit used to defraud victims by creating fake banks and interacting with targets to steal large sums of money. The kit is a copy and linked tohttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians"> hxxps://elitepremierplc.com/index.htmlScreenshot attached." class="img-responsive" style="max-width:100%;"/>
hxxps://elitepremierplc.com/index.htmlScreenshot attached." title="The first kit called elite bank is a fraud kit used to defraud victims by creating fake banks and interacting with targets to steal large sums of money. The kit is a copy and linked tohttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians"> hxxps://elitepremierplc.com/index.htmlScreenshot attached." class="img-responsive" style="max-width:100%;"/>

 /nisbankasi.com (31.22.4.145) @Wildcard_Net @urlscanio link: https://urlscan.io/result/f7..." title="Using a page hash pivot I& #39;ve found another domain linked to the same scamhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/nisbankasi.com (31.22.4.145) @Wildcard_Net @urlscanio link: https://urlscan.io/result/f7..." class="img-responsive" style="max-width:100%;"/>
/nisbankasi.com (31.22.4.145) @Wildcard_Net @urlscanio link: https://urlscan.io/result/f7..." title="Using a page hash pivot I& #39;ve found another domain linked to the same scamhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🌐" title="Globe with meridians" aria-label="Emoji: Globe with meridians">/nisbankasi.com (31.22.4.145) @Wildcard_Net @urlscanio link: https://urlscan.io/result/f7..." class="img-responsive" style="max-width:100%;"/>
 " title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">
" title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">
 " title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">
" title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">
 " title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">
" title="The second kit on the domain is a standard credential phishing kit. It even comes with a useful setup guide. This is a demonstration of how professional the phishing as a service economy has become. https://abs.twimg.com/emoji/v2/... draggable="false" alt="👎" title="Thumbs down" aria-label="Emoji: Thumbs down">">


