1/  https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">The EARN IT Act is a cynical, opportunistic attack on encryption leveraging today’s state of panic.
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">The EARN IT Act is a cynical, opportunistic attack on encryption leveraging today’s state of panic. https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light"> https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🚨" title="Police cars revolving light" aria-label="Emoji: Police cars revolving light">
My latest for @knoxcustody, which sees an attack on encryption as an attack on Bitcoin, its business, and its customers.
https://medium.com/knox-blog/privacy-isnt-free-cb5ddb98ac9">https://medium.com/knox-blog...
Thread https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Down pointing backhand index" aria-label="Emoji: Down pointing backhand index">
My latest for @knoxcustody, which sees an attack on encryption as an attack on Bitcoin, its business, and its customers.
https://medium.com/knox-blog/privacy-isnt-free-cb5ddb98ac9">https://medium.com/knox-blog...
Thread
2/ Governments have long hated consumer encryption. Leveraging a world distracted by the Coronavirus, the US Federal Government is employing the shock doctrine to try their hand once more at undermining it with the EARN IT Act.
Why? It’s about control. https://www.eff.org/deeplinks/2020/03/earn-it-act-violates-constitution">https://www.eff.org/deeplinks...
Why? It’s about control. https://www.eff.org/deeplinks/2020/03/earn-it-act-violates-constitution">https://www.eff.org/deeplinks...
3/ The EARN IT Act relies on a sleight of hand to form a law-enforcement run committee responsible for regulating online platforms, ultimately granting it the authority to unilaterally undermine encryption, while not explicitly saying this. https://www.congress.gov/bill/116th-congress/senate-bill/3398/text">https://www.congress.gov/bill/116t...
4/ Govt attacks on encryption reached crescendo with the Crypto Wars of the & #39;90s before they were forced underground w/ the clandestine operations of the NSA. But they never lost sight of the prize: a window into the activities and thoughts of everyone. https://www.wired.com/1993/02/crypto-rebels/">https://www.wired.com/1993/02/c...
5/ PGP was a high profile case that came under scrutiny for “munitions export without a license”. The answer: publish the PGP source code as a book, meaning that global distribution was protected by the First Amendment to the United States Constitution.
6/ The cypherpunks came to prominence around the Crypto Wars. Eric Hughes made the case that “privacy is necessary for an open society in the electronic age,” defending that privacy is something humans have always been able to rely on finding.
https://nakamotoinstitute.org/static/docs/cypherpunk-manifesto.txt">https://nakamotoinstitute.org/static/do...
https://nakamotoinstitute.org/static/docs/cypherpunk-manifesto.txt">https://nakamotoinstitute.org/static/do...
7/ Meanwhile, @halfin, who would go on to receive the first ever Bitcoin transaction 15 years later, identified a tendency among the cypherpunks to prematurely celebrate victory and avoid the political.
8/ It’s with Hal Finney in mind that we push back, both in principle and in regulation, against encroachments on these hard-fought liberties.
9/ Discounting privacy because you "have nothing to hide" betrays gross social negligence. What’s legal is not what’s moral; indeed, laws are often changed by the activities of people doing that which they are not supposed to be doing.
https://moxie.org/blog/we-should-all-have-something-to-hide/">https://moxie.org/blog/we-s...
https://moxie.org/blog/we-should-all-have-something-to-hide/">https://moxie.org/blog/we-s...
10/ Mass surveillance changes behavior and suppresses the human will. Some might like this, but most would see the obvious tragedy in it: for example, how would same-sex relationships become permitted if no one had ever experienced one?
11/ “I have nothing to hide” betrays an assumption of guilt. The EARN IT Act leverages this guilt and plays a positioning game w/ its name. It implies the government gives people their rights, and they must therefore earn the right to privacy, but this is the wrong way around.
12/ Privacy & secrecy are not practically separable. Some say you have a right to privacy but not secrecy. They are so compromised by the narrative that they can’t see the two are inseparable at the tech level. Online, either all the information can be snooped, or none of it.
13/ One of the strongest cases for encryption is accessible resilience in the face of tyranny. As most people sit at home, locked up w/ their liberties suspended, it should be clear how easily power might be leveraged against people despite assurances that democracy fixes this.
14/ The EARN IT Act requires that all online platforms comply with a list of undefined “best practices” that will be created by a commission of 19 people controlled by US Attorney General William Barr and law enforcement agencies. https://www.congress.gov/bill/116th-congress/senate-bill/3398/text">https://www.congress.gov/bill/116t...
15/ To those paying attention, EARN IT is transparently the latest in a slew of attacks on encryption that have ramped up dramatically in the past year. The primary indicator is to observe who, exactly, is expected to be involved in this commission. https://www.eff.org/deeplinks/2020/03/earn-it-bill-governments-not-so-secret-plan-scan-every-message-online">https://www.eff.org/deeplinks...
16/ In December, Senator @LindseyGrahamSC (co-sponsor of the current bill) threatened tech companies that “you& #39;re going to find a way to do this or we& #39;re going to do it for you,” with regards to routine surveillance. https://reason.com/2020/01/17/trump-and-comey-are-united-against-encrypted-communications/">https://reason.com/2020/01/1...
17/ US AG William Barr, who will ultimately be running the commission with the ability to approve or veto anything, has attacked encryption so consistently during his term that it’s kinda become his thing. https://www.eff.org/deeplinks/2019/07/doj-and-fbi-show-no-signs-correcting-past-untruths-their-new-attacks-encryption">https://www.eff.org/deeplinks...
18/ The VP at the NCMEC was strikingly transparent in a hearing of the Bill, saying that he wants every message sent on the Internet to be read by government-approved scanning software.
https://www.judiciary.senate.gov/imo/media/doc/Shehan%20Testimony.pdf">https://www.judiciary.senate.gov/imo/media...
https://www.judiciary.senate.gov/imo/media/doc/Shehan%20Testimony.pdf">https://www.judiciary.senate.gov/imo/media...
19/ At a pragmatic level, attacks on encryption threaten the most basic technologies people have come to rely on for the internet economy. These should be increasingly obvious for those working from home under quarantine.
20/ End-to-end encryption allows distributed teams to securely discuss sensitive topics, ensures important documents can be verified, and protects secrets from competition. That little padlock icon in your address bar confirms your connection to Twitter is secure.
21/ @Beautyon_ has even pointed out that an attack on encryption would be game theoretically stupid for America in today’s connected world, rendering only US services vulnerable and forcing the country to be recognized globally as an unsafe trade zone. https://medium.com/hackernoon/president-trumps-advisors-are-wrong-about-encryption-339fbae364be">https://medium.com/hackernoo...
22/ The practical problem with attacking encryption is that it introduces fundamental weakness in internet infrastructure that other actors will find and exploit. Even without intentionality, the pace and magnitude of exploits is already accelerating. https://blog.malwarebytes.com/privacy-2/2019/08/backdoors-are-a-security-vulnerability/">https://blog.malwarebytes.com/privacy-2...
23/ Even with a backdoor, law enforcement won’t achieve their goals. Encryption standards are open source and broadly distributed. If you need to use it, you will. The result is mass surveillance of citizens in exchange for trivial improvements to the efficacy of law enforcement.
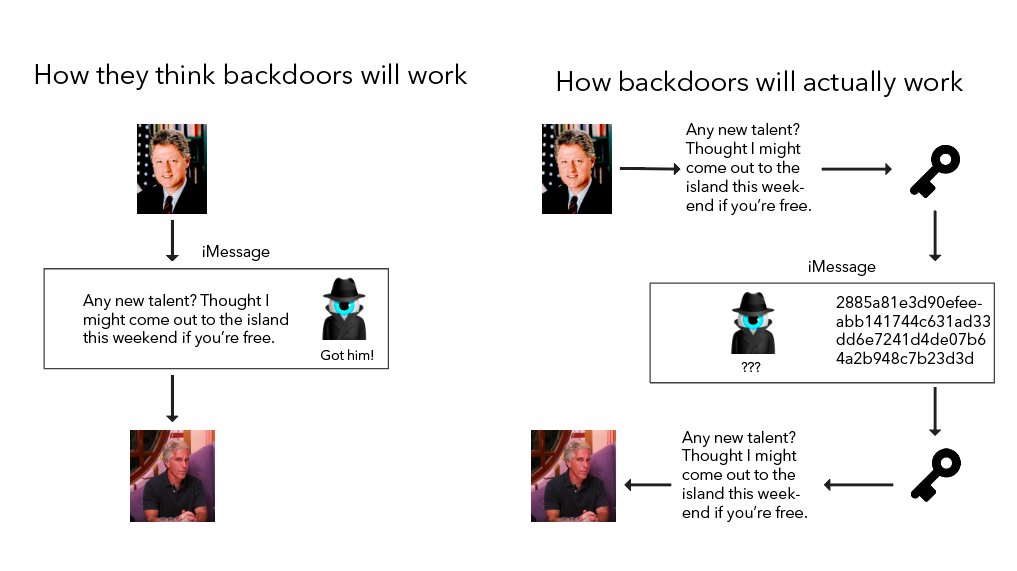
24/ A compromised iMessage can still be used for encrypted messages. It just requires a little more effort to encrypt and decrypt outside the application itself, which is then used to send what looks like a string of random characters.
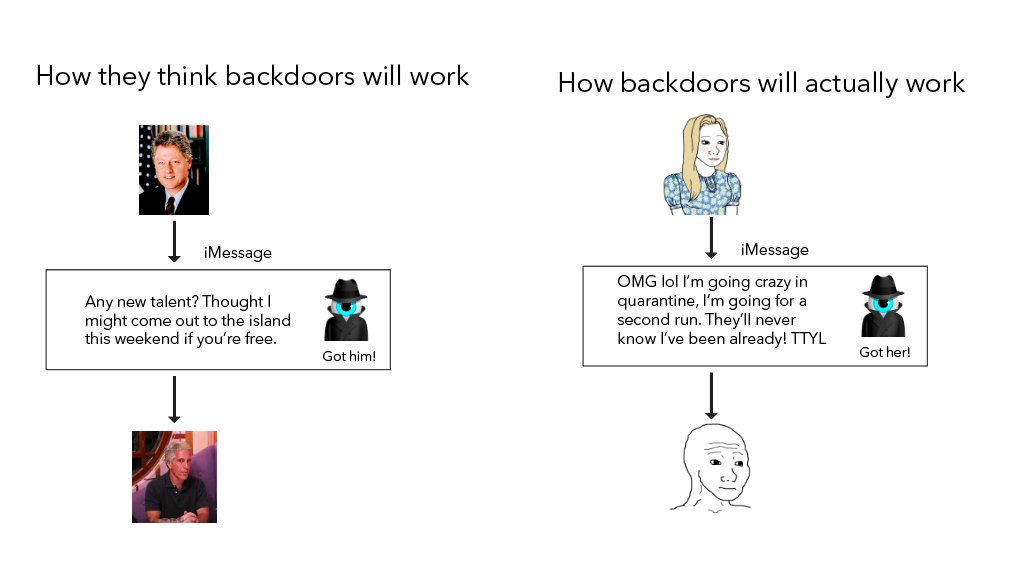
25/ If a group is sophisticated enough to run a global pedo ring, they’ll easily still use encryption. But if you communicate a second local walk in violation of your quarantine quota, you might not bother to encrypt it and soon get a knock on the door from the thought police.
26/ Security researchers often say the govt shouldn’t be in the average person’s threat model. The argument is that you’re probably not important enough for them, but if you are, then they will always get you anyway––so what’s the point? This argument is defeatist and incorrect.
27/ Attempted abuses of individual liberties, and the government& #39;s role in feeding the problems they profess to solve, demonstrates that the government should be the centerpiece of everyone’s threat model.
28/ Maybe stories of child abuse can pull at your heartstrings, but the same tools in the hands of a principled, independent investigator can be harnessed to expose the child abuse rampant among the world’s most powerful people themselves (Epstein & friends).
29/ Maybe the specter of terrorism scares you. But without encryption, @wikileaks mightn& #39;t have pulled off the clandestine operations to expose the Obama admin’s role in arming ISIS. If terrorism is such a threat, best to understand who’s involved. https://www.democracynow.org/2016/7/25/assange_why_i_created_wikileaks_searchable">https://www.democracynow.org/2016/7/25...
30/ Encryption is antifragile. Encroachments will only strengthen its need and assurances. But it would be nice if everyone could use it by default. Encourage the use of free and open source software like @signalapp. Fight for your right to privacy.
END/ Thanks to @daskalov, @thibm_, @hodlonaut, @FriarHass, @HillebrandMax and @matt_odell for their help with this article. If you have any thoughts or want to hear more about our principled approach to Bitcoin key custody @knoxcustody, hit us up! https://www.knoxcustody.com/demo ">https://www.knoxcustody.com/demo"...

 Read on Twitter
Read on Twitter