Lazy as I am, I will do the & #39;report& #39; on Stopp Corona App in english on twitter (german will be a blogpost). I will focus on cryptography, security and privacy.
So follow this thread, if you& #39;re interested in technical details.
So follow this thread, if you& #39;re interested in technical details.
First - what is it? Well, you can track your physical contacts via "digital handshakes" and it should be anonymous (or at least pseudonymous). If one of your contacts confirms an infection you will be notified. And they did an interesting job.
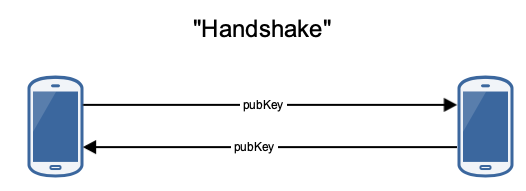
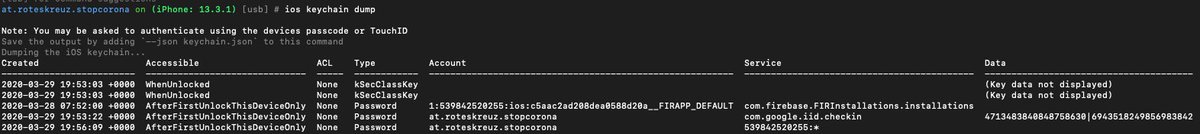
First, the handshake is done manually and based on Google Nearby (BTLE+Sound+Location+GoogleApis). No UUID is exchanged, only a publicKey. But what publickey? How did they do the notification? What data is exchanged, where and how is it stored?
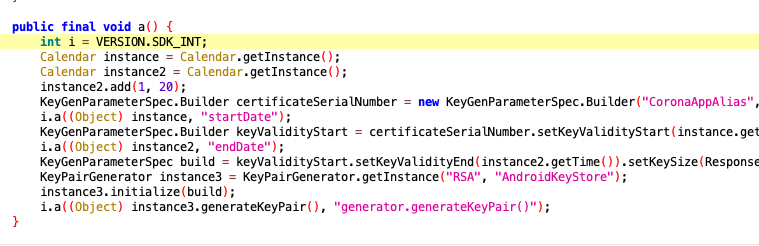
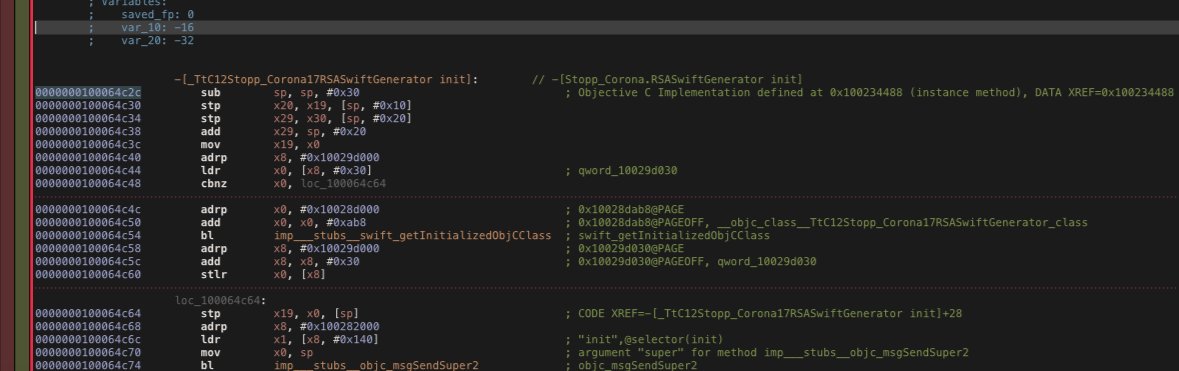
The publicKey is a RSA 1024 Bit key, that is generated in both android and iOS at first start of the app. We can see it in the source or the march-bin:
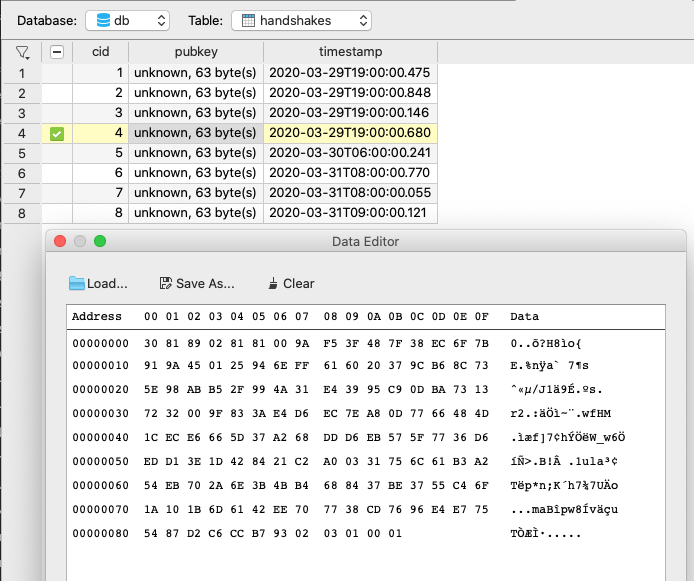
Encounters will be stored in a sqlite containing the publicKey, together with an incremental id and a timestamp. That is pretty nice.
But here& #39;s a minor con: The pubkey won& #39;t change - ever. Since they are still stored locally, this is atm only a minor drawback. Also: The handshake isn& #39;t signed - so you may just use any of your collected keys. Attack scenario is limited, just for fun?
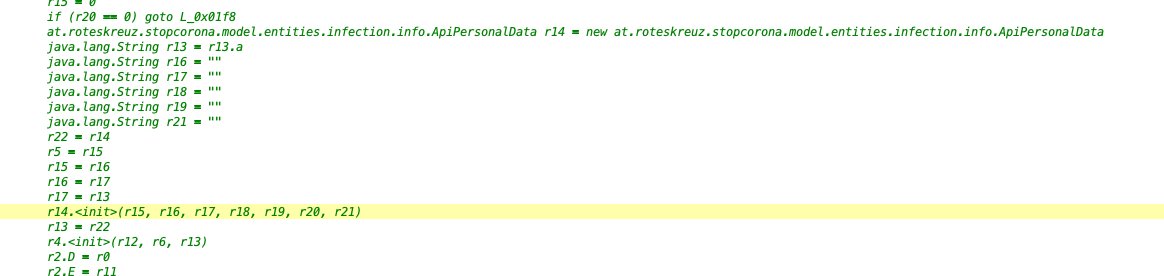
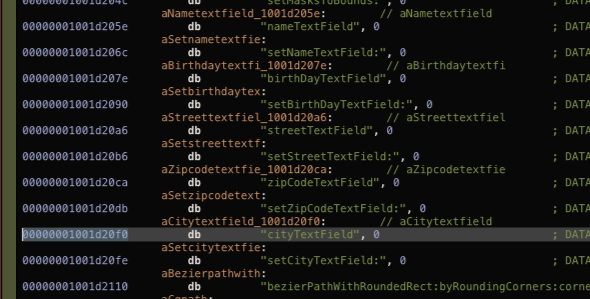
More interestingly, there is a prepared data for "name, dob, city, zip" even though it isn& #39;t used. This might be a generated artifact from a data scheme, but it does not fit to "anonymous". Nevertheless it is never used - but rather filled with empty strings.
So, what happens in case of an infected encounter? The app generates a *random* UUID and encrypts it with all stored pubKeys from the last 2 days.
Since I didn& #39;t want to trigger that function, I aborted it in BURP. The used scheme is "RSA/None/PKCS1Padding".
Since I didn& #39;t want to trigger that function, I aborted it in BURP. The used scheme is "RSA/None/PKCS1Padding".
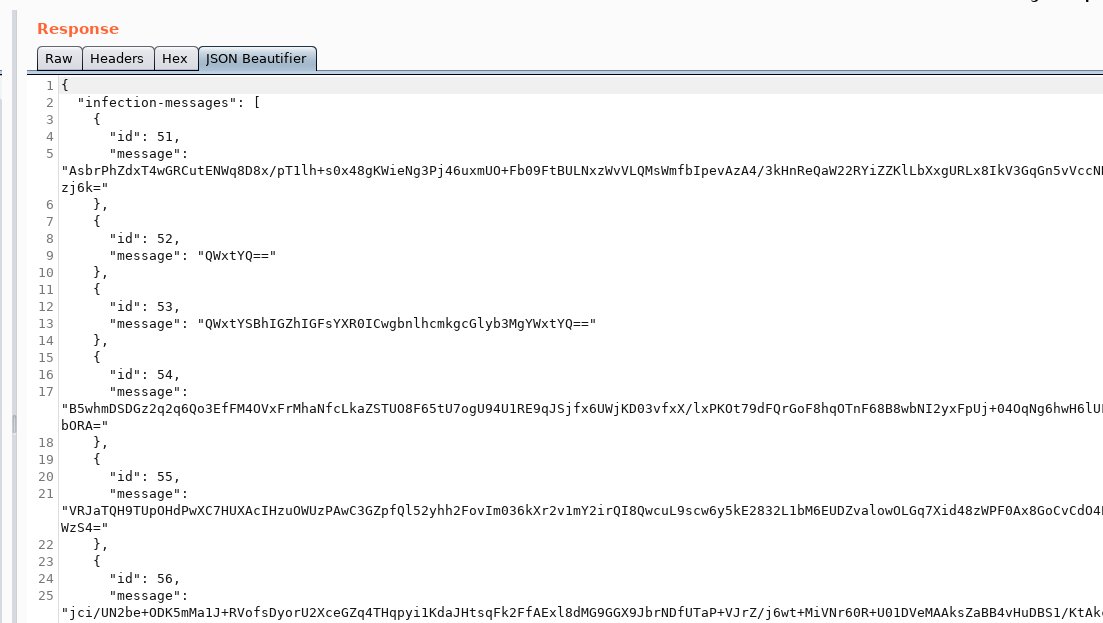
All infection messages are distributed to all clients, every client tries do decipher it using its private key. If your client is able to do so, that is & #39;proof& #39; that you encountered an infected person.
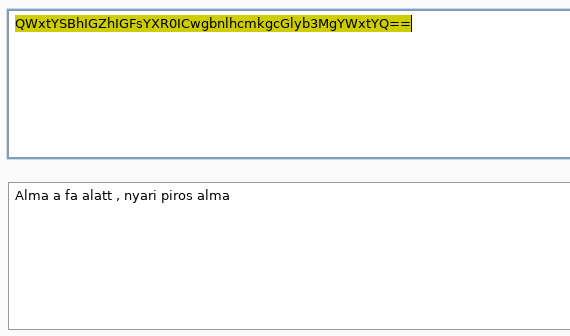
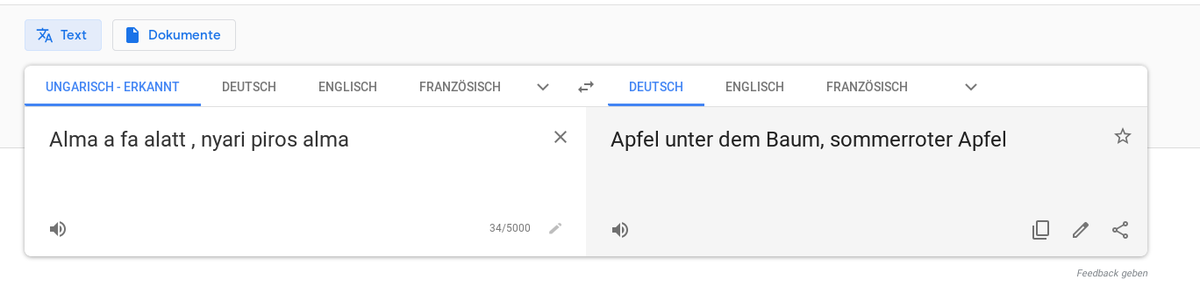
There is some proof, that the content is not decrypted nor inspected on server side, as someone already put a hungarian "I was here" message there.
Once you had an encounter the backend will be informed, that you had one, but not which handshake exactly. So what& #39;s left to say?
- Unsigned handshake -> You can use any publickey
(could& #39;ve been solved with w.g. RSA blinded signature)
- Public Key doesn& #39;t change
- Unsigned handshake -> You can use any publickey
(could& #39;ve been solved with w.g. RSA blinded signature)
- Public Key doesn& #39;t change
- there are some questionable artifacts (street/name/zip/dob...)
- Someone left already a message there
- You will disclose some data, but it is interesting
CC @fs0c131y
- Someone left already a message there
- You will disclose some data, but it is interesting
CC @fs0c131y

 Read on Twitter
Read on Twitter