We& #39;ve all received emails with no attachment and assume it& #39;s "safe" to open in a mail client (as long as we don& #39;t explicitly click on any URLs). Right?
Not so much...
Not so much...
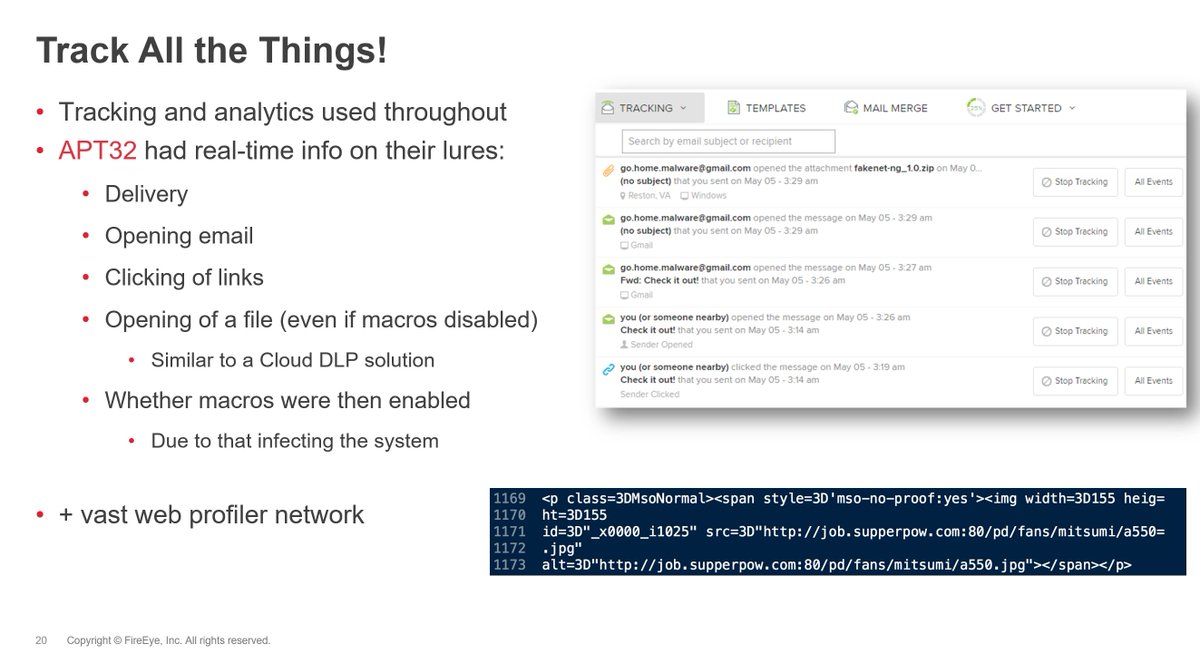
Let& #39;s talk about email tracking pixels for a minute and how sales/marketing (as well as real threat actor& #39;s) can use them to evaluate the success of an email marketing (or phishing) campaign...or for information gathering before sending a follow-up payload.
#DFIR #APT32
#DFIR #APT32
Let& #39;s start with the basics of tracking pixels.
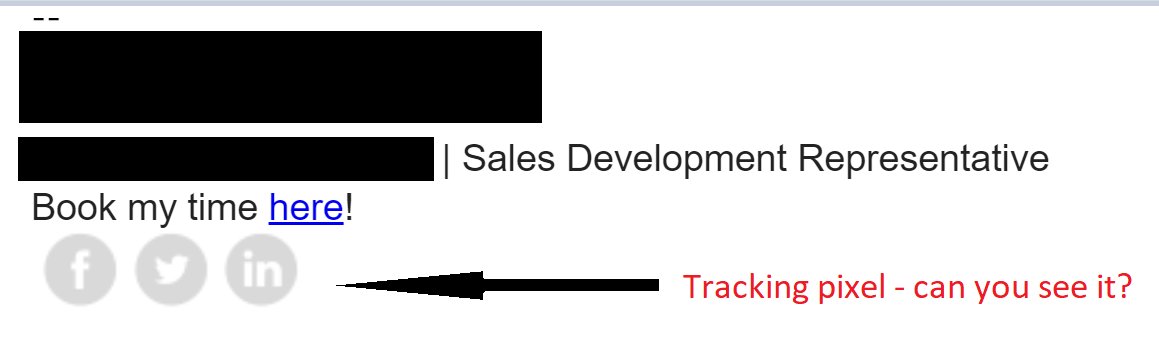
I& #39;m not attending @RSAConference - but I get marketing emails like this one. If you use the Outlook client - have you ever noticed the "to help protect your privacy; Outlook prevented automatic download of some pictures."?
I& #39;m not attending @RSAConference - but I get marketing emails like this one. If you use the Outlook client - have you ever noticed the "to help protect your privacy; Outlook prevented automatic download of some pictures."?
The email has a number of image attachments - one of which is called a tracking pixel. Here& #39;s what it looks like when the images haven& #39;t been downloaded.
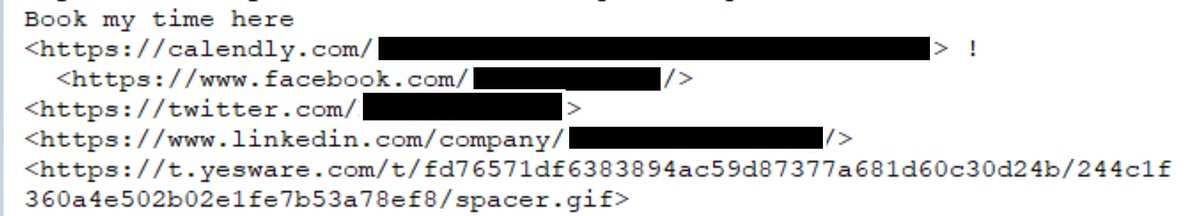
If you take a look at the raw email message you& #39;ll notice multiple URLs including ones from well known social media companies and a lesser known one called yesware
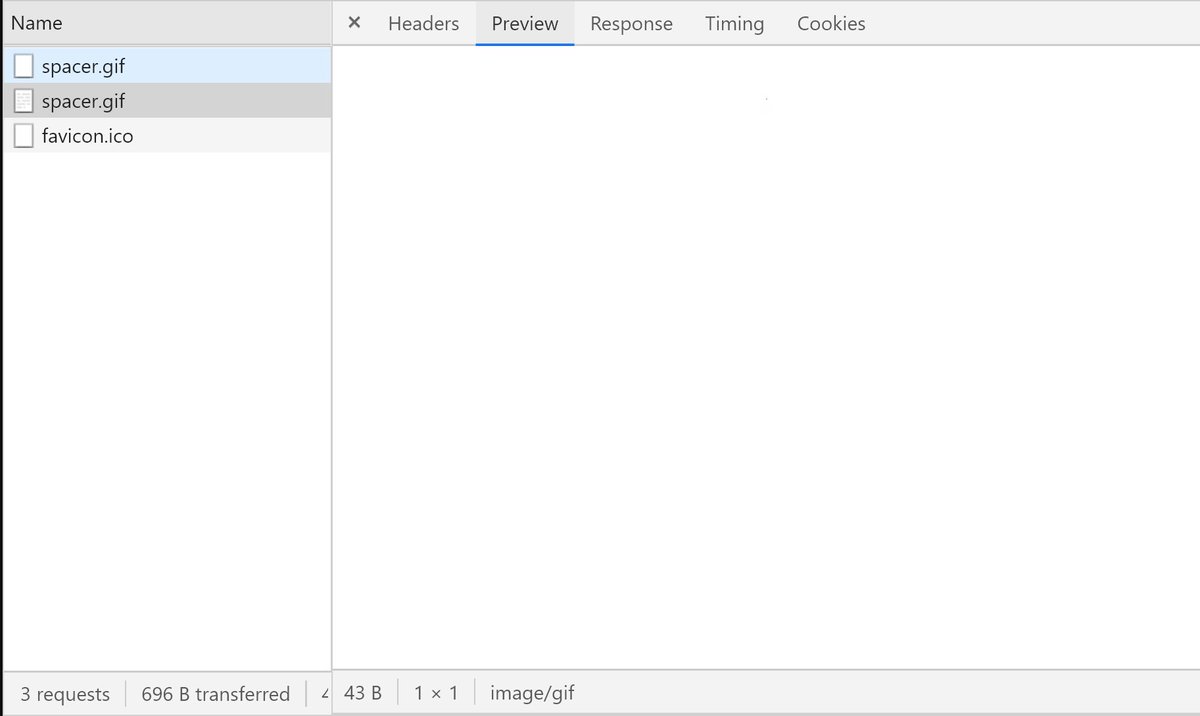
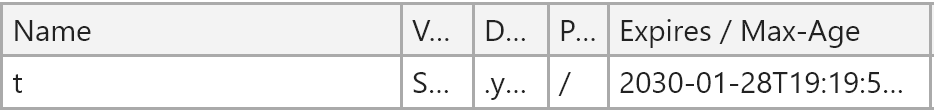
Let& #39;s take a look at spacer.gif. According to Chrome developer tools - it& #39;s a 1 pixel by 1 pixel, white image and also saves a cookie called "t" that expires in 10 years.
In my limited testing I& #39;ve found that each mail client chooses to handle these tracking pixels differently.
Outlook thick client (blocked by default)
Office365 in a web browser (pixel autoloaded)
iPhone mail client (pixel autoloaded)
Android mail client (pixel autoloaded)
Outlook thick client (blocked by default)
Office365 in a web browser (pixel autoloaded)
iPhone mail client (pixel autoloaded)
Android mail client (pixel autoloaded)
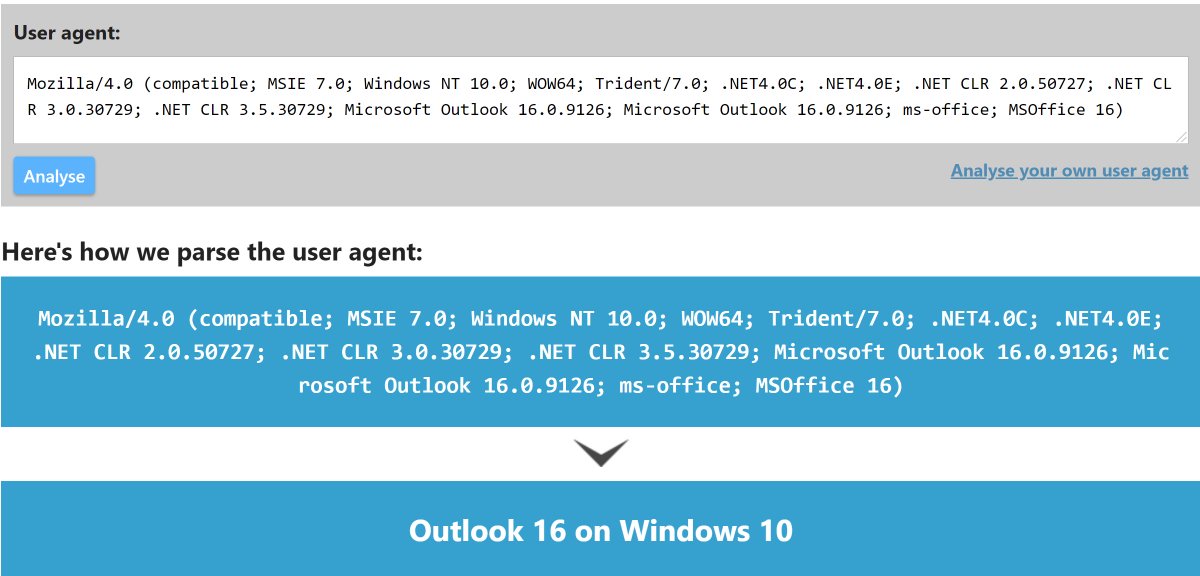
If you open an email in a mail client that autoloads a tracking pixel - you divulge your IP address, OS version and mail client version and the date/time of each time you opened the email.
Moral of the story is - opening an email in certain mail clients can leak information about your system b/c your mail client autoloads a tracking pixel. And although it might be a company hosting a hot @RSAConference party - it could also be someone less "friendly"
#DFIR #APT32
#DFIR #APT32
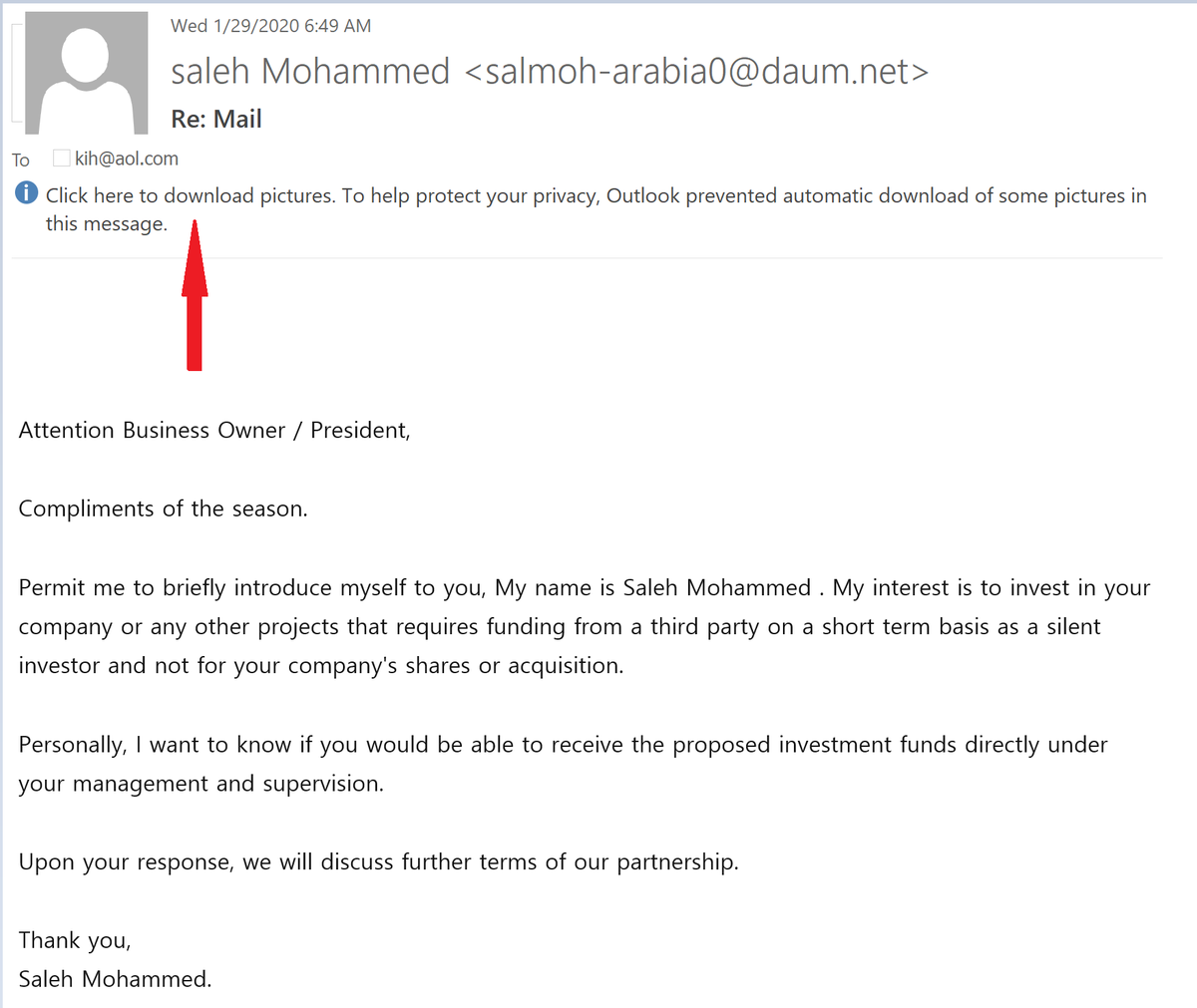
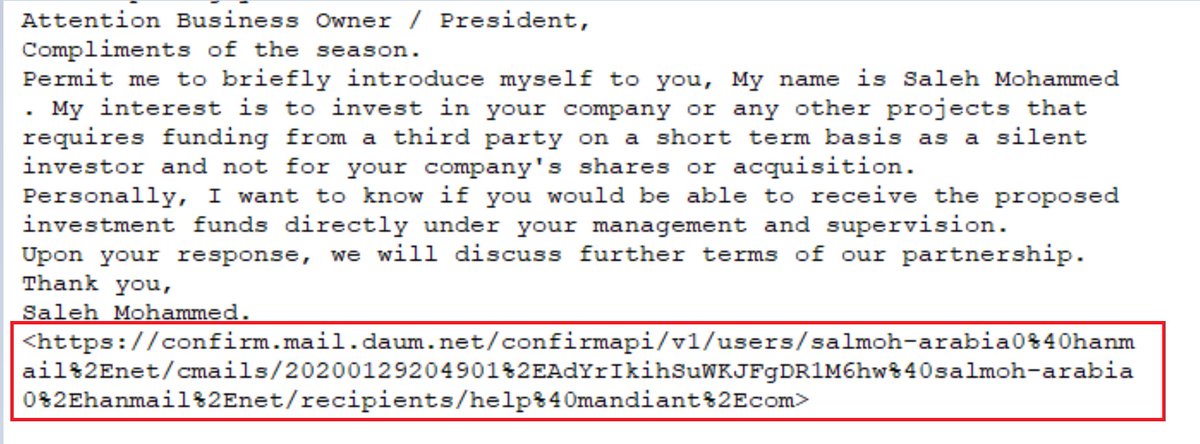
Even scammers leverage tracking pixels to gauge the success of their campaigns.
I could really use a silent investor - you think I should reach out to Mr. Mohammed?
I could really use a silent investor - you think I should reach out to Mr. Mohammed?

 Read on Twitter
Read on Twitter