Tracking devices and strategic places via NMEA sentences
#osint #hacking #maritime #ics #scada #cybersecurity #shodan #shodansafari
[THREAD]
#osint #hacking #maritime #ics #scada #cybersecurity #shodan #shodansafari
[THREAD]
NMEA is a protocol established by National Marine Electronics Association and is used in communication between marine electronics such as echo sounder, sonars, anemometer, gyrocompass, autopilot, GPS receivers and many other types of instruments https://www.gpsinformation.org/dale/nmea.htm ">https://www.gpsinformation.org/dale/nmea...
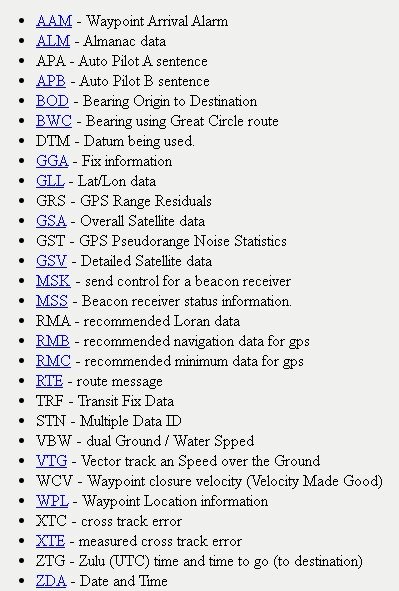
NMEA consists of sentences that describe geographic position, date & time, satellites in view, routes and much more, full list with all sentence codes you can find here http://aprs.gids.nl/nmea/ ">https://aprs.gids.nl/nmea/&quo...
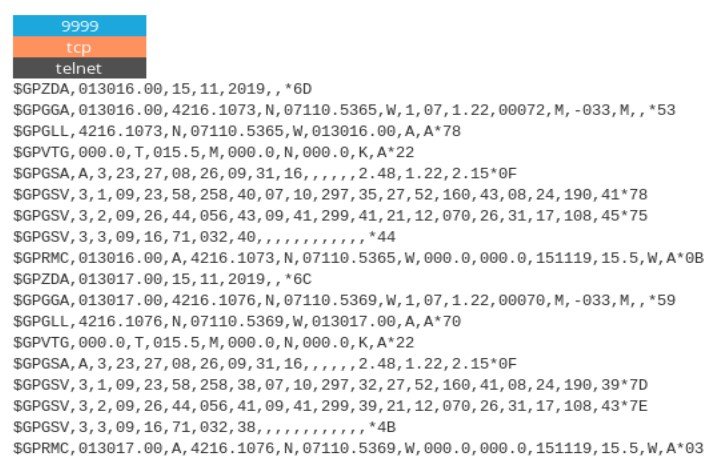
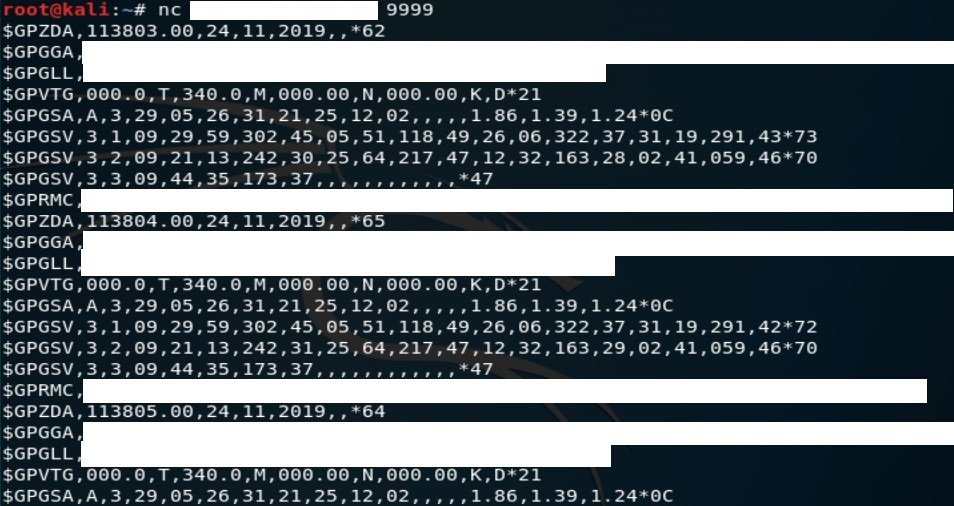
Typical NMEA response includes "$GPGGA" code which is called "Global Positioning System Fix Data" and gives exact coordinates and timestamp.
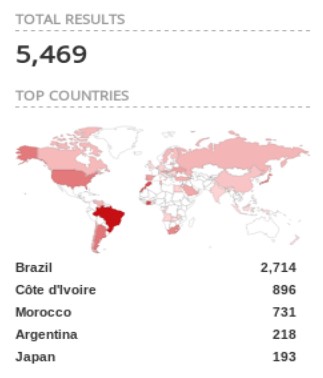
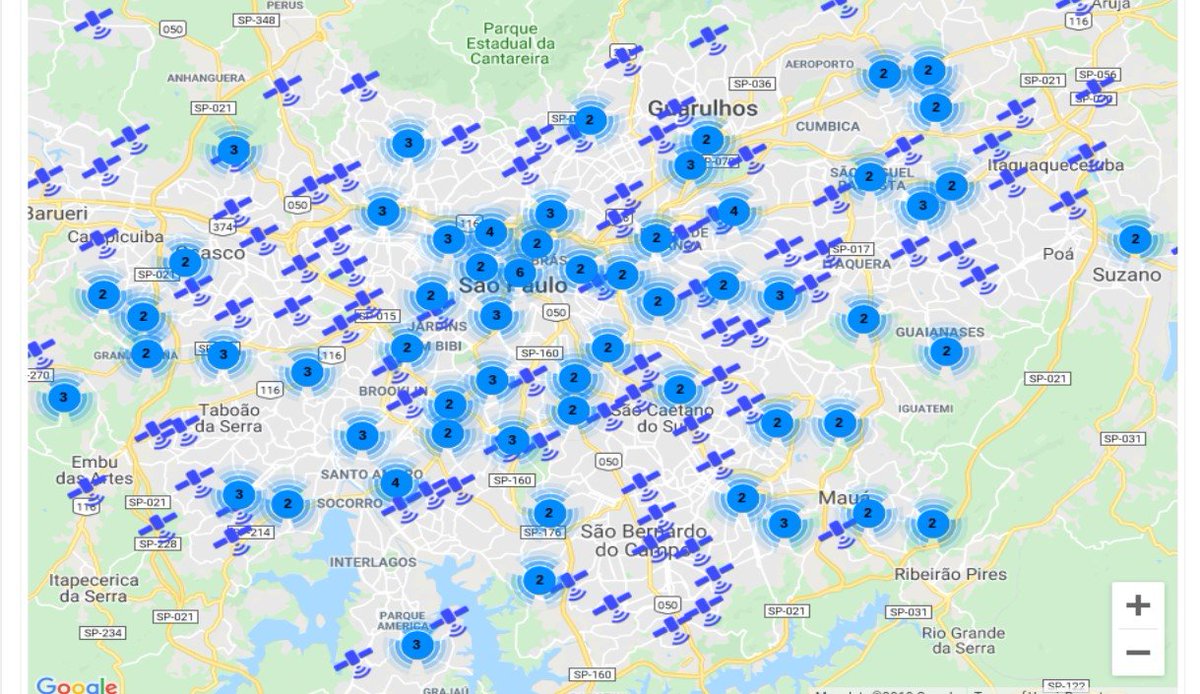
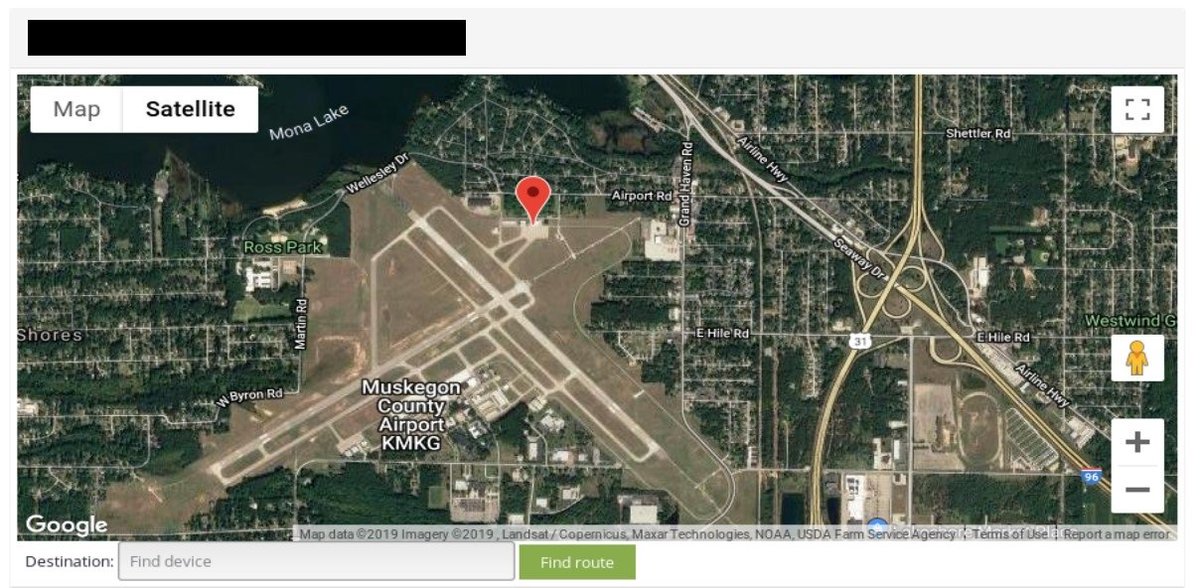
Thanks to @Shodan query "$GPGGA" and new ꓘamerka update, you can map these devices. They are most popular in Brazil, Côte d& #39;Ivoire, Morocco, Argentina and Japan
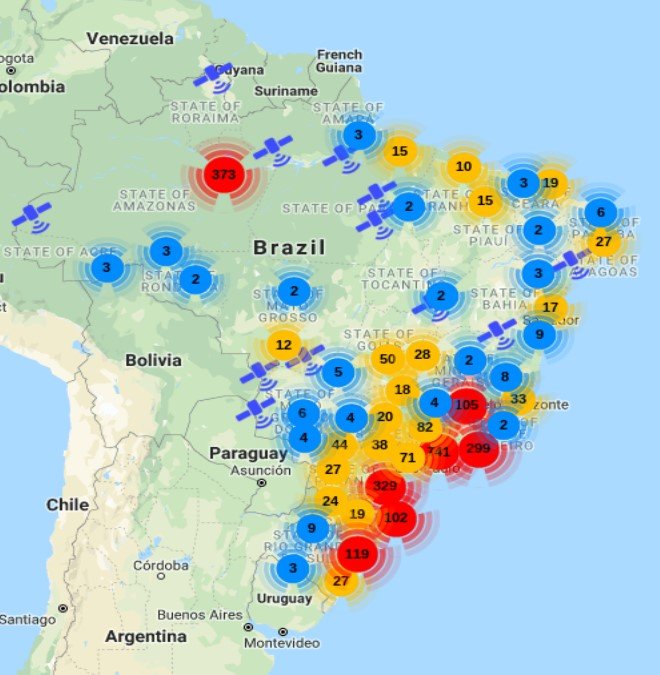
I visualized every place that NMEA sentences point to for whole Brazil. Location is not IP based but it& #39;s established by parsing NMEA response from device. Second screenshot is for Sao Paolo.
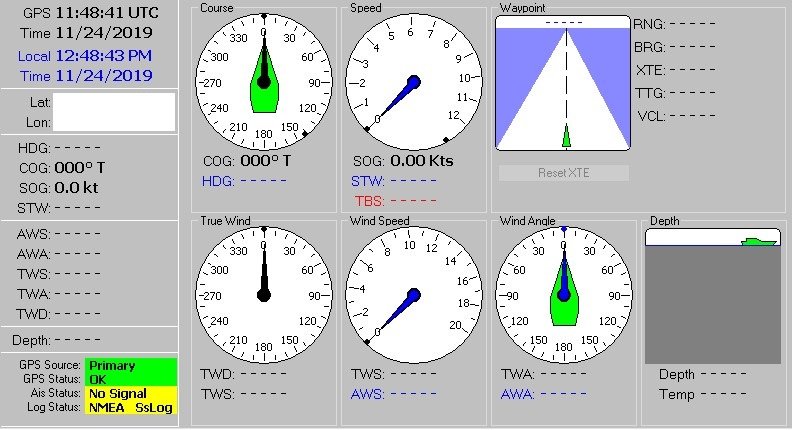
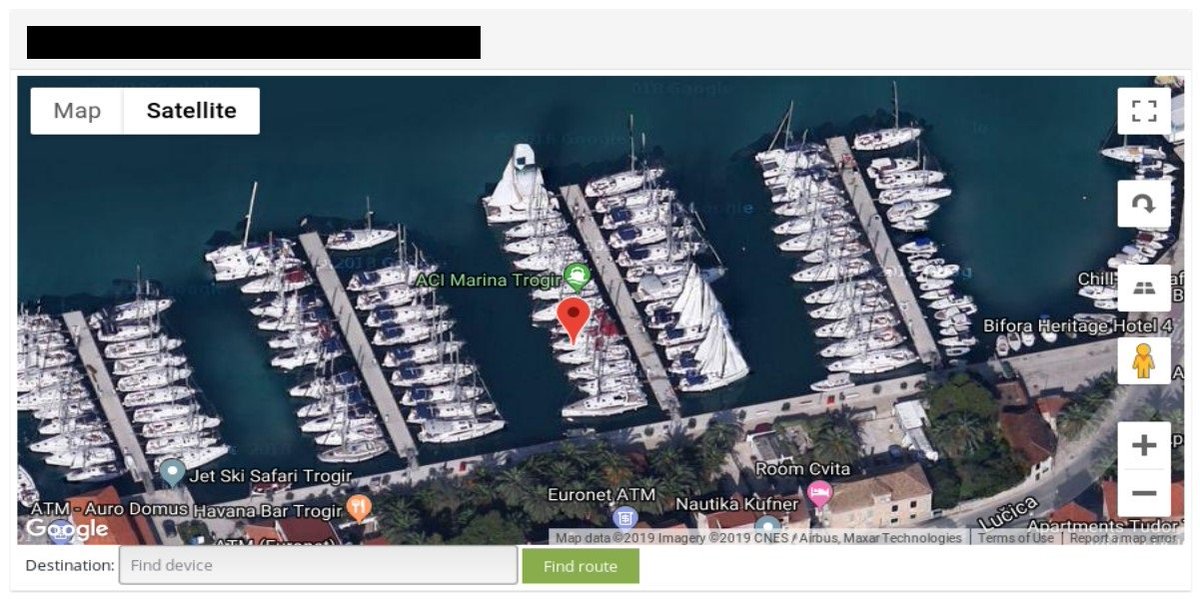
Directly connecting to the device will give you real time data so you know if it points only on one place or if it& #39;s moving. NMEA is often use in maritime and with NavMon you can monitor exposed ships in real time.
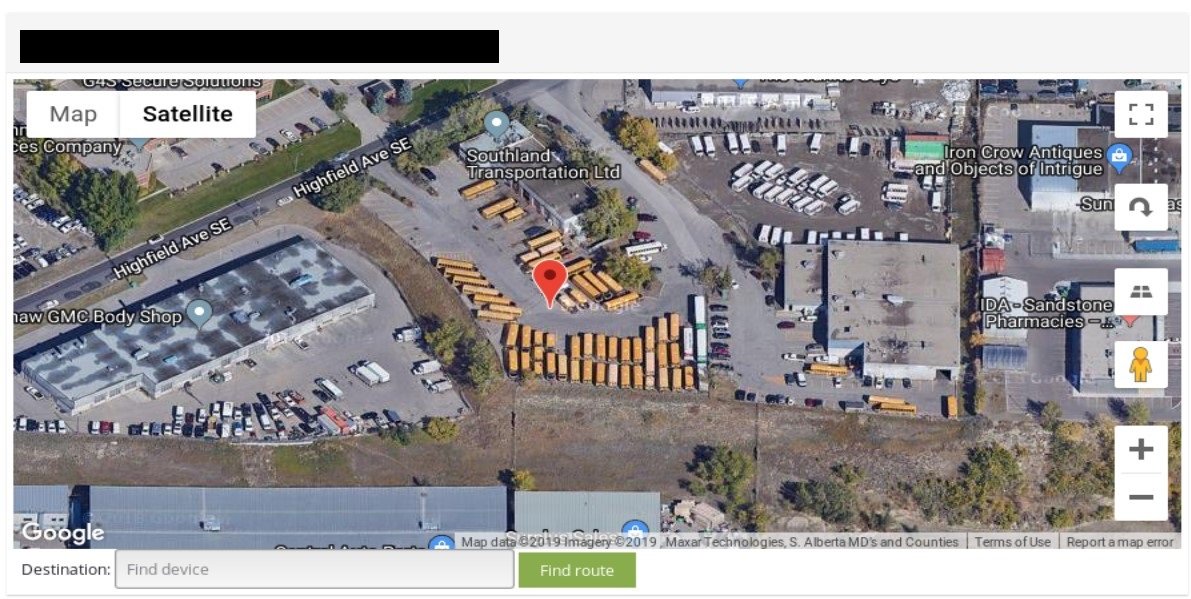
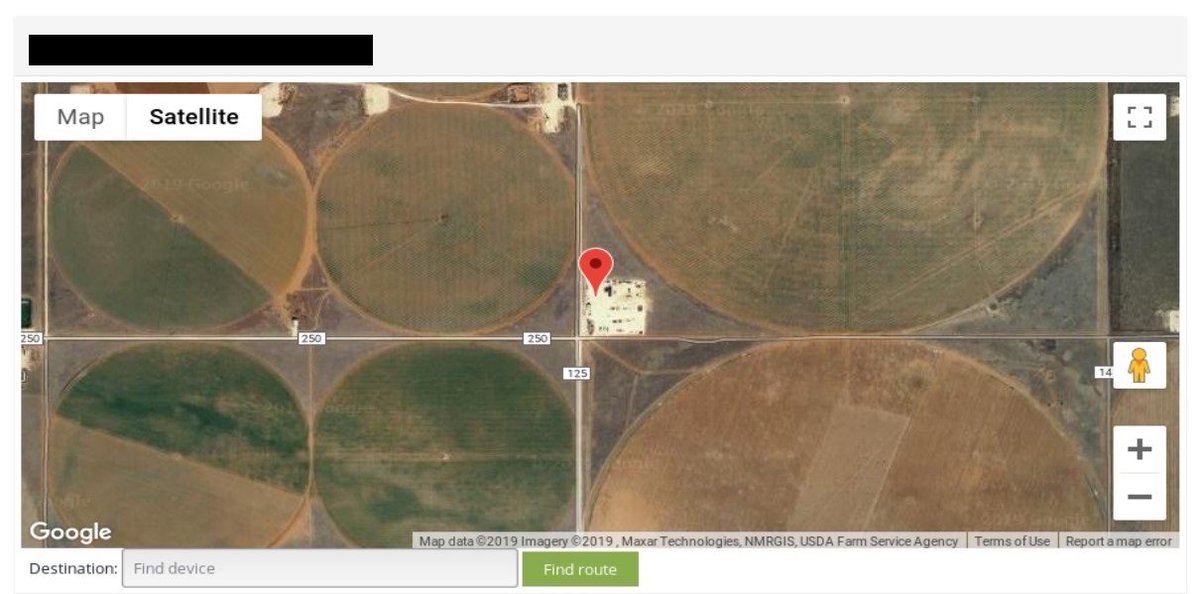
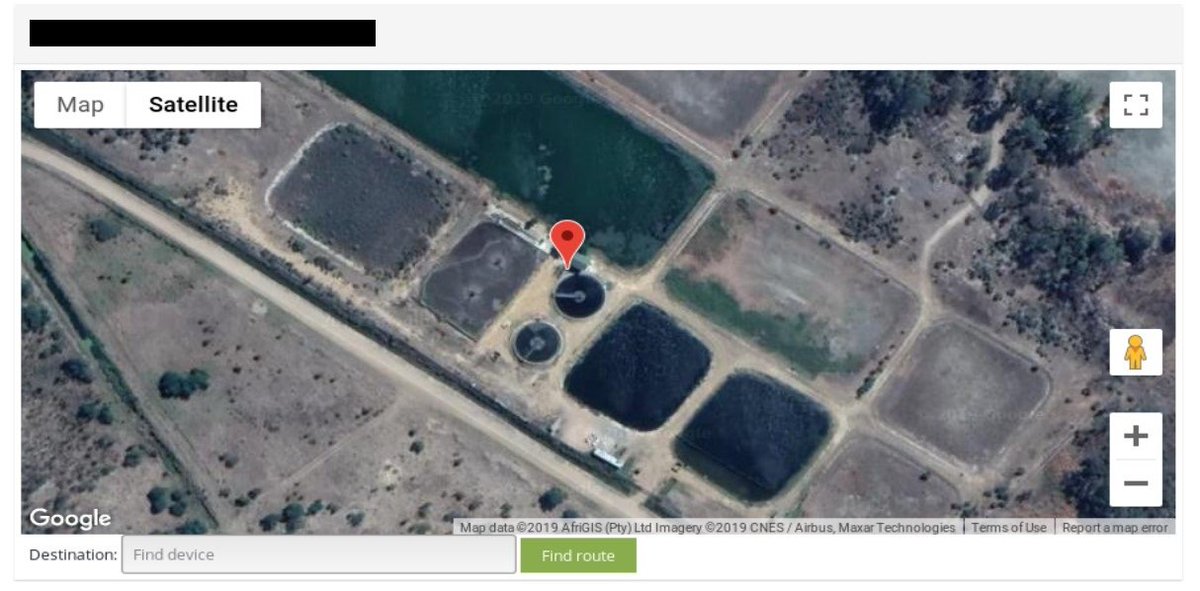
Among mentioned findings you can came across places like airports, waste water treatment plants, yachts, locations important from logistics point of view and other facilities.
Moreover, NMEA supports input mode in some cases, so someone can take over device and overwrite data like way point, destination, satellites or even autopilot.
More about NMEA https://www.gpsworld.com/what-exactly-is-gps-nmea-data/">https://www.gpsworld.com/what-exac... and it’s security https://www.kaspersky.com/blog/yachts-vulnerabilities/21576/">https://www.kaspersky.com/blog/yach... https://www.pentestpartners.com/security-blog/crashing-ships-by-hacking-nmea-sentences/">https://www.pentestpartners.com/security-...
ꓘamerka here --> https://github.com/woj-ciech/Kamerka-GUI">https://github.com/woj-ciech...

 Read on Twitter
Read on Twitter