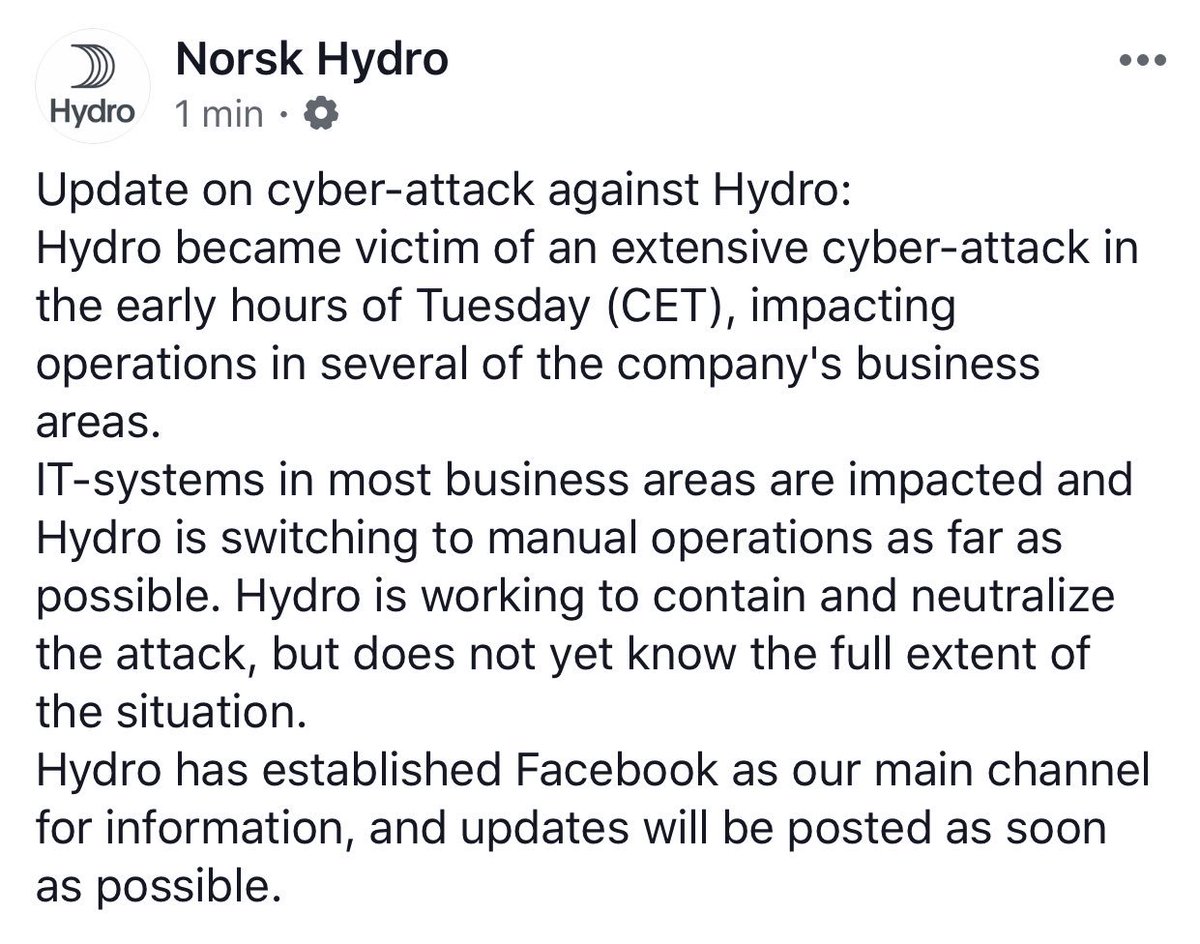
https://www.hydro.com/ ">https://www.hydro.com/">... https://twitter.com/NorskHydroASA/status/1107925735048646656">https://twitter.com/NorskHydr...
They’ve informed stock market they’ve gone to manual operations. Anybody know what the deal is?
Tis about 35k employees. I’m going to guess ransomware.
BBC News has some more details, sounds like their ICS systems may be offline. https://www.bbc.co.uk/news/technology-47624207">https://www.bbc.co.uk/news/tech...
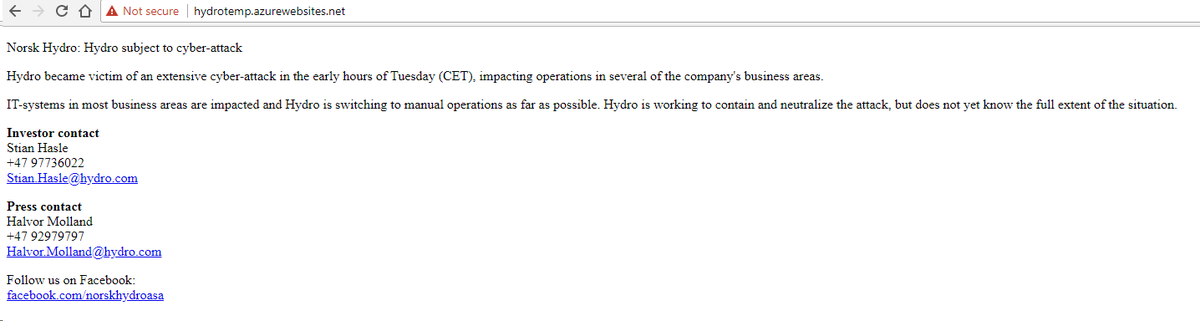
They have redirected their website to an Azure temporary hosting area. http://hydrotemp.azurewebsites.net/ ">https://hydrotemp.azurewebsites.net/">...
According to Reuters Hydro plants in Qatar and Brazil are also impacted.
This is a notice one of their offices, it says "do not connect your PC to the network". It appears they have been ransomware& #39;d by a crime group.
Norwegian state media reporting LockerGoga ransomware, which I covered here a few weeks ago with @malwrhunterteam - keeps getting signed with same certificate that CA won& #39;t revoke, very little AV detection each time https://twitter.com/GossiTheDog/status/1104089245344583680?s=20">https://twitter.com/GossiTheD...
"A certificate was explicitly revoked by its issuer."
sign from another office https://www.nrk.no/norge/skreddersydd-dobbeltangrep-mot-hydro-1.14480202">https://www.nrk.no/norge/skr...
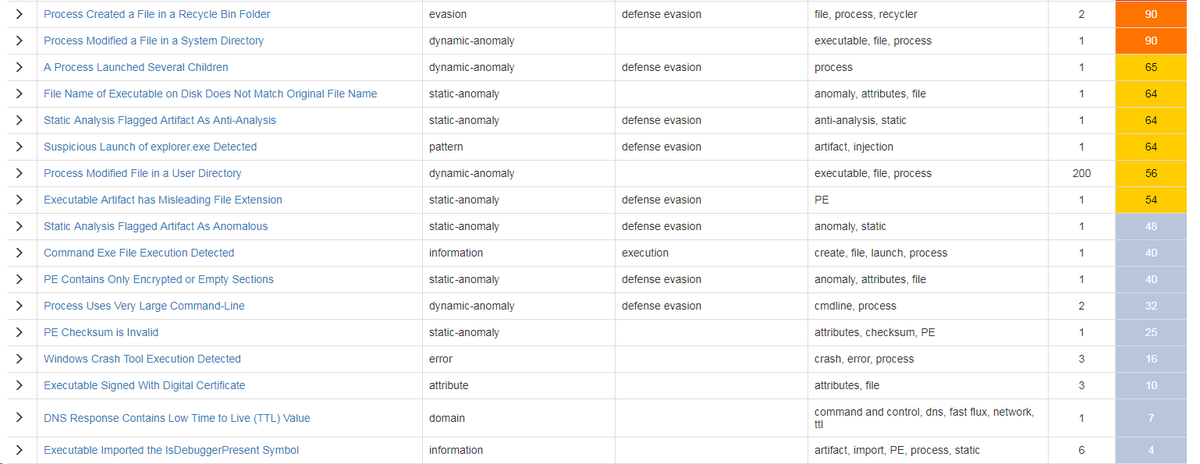
LockerGaga ransomware analysis - it uses no network traffic, no DNS, no C2. Endpoint detection poor, I can give multiple samples without real world detection still. It .locker& #39;s files in Recycle Bin, which is one to detect heuristically.
*LockerGoga. Note that a few of those events are wrong (my fault), e.g. executable name is me renaming it.
Note that the payload does not spread, for sure. It is very likely companies getting pwned are having it delivered by Active Directory Group Policy, e.g. scheduled tasks etc.
LockerGoga hit @Altran back in January. As an attacker - if you have domain admins, put the .exe in Netlogon folder, it automatically propagates to every Domain Controller, then make a GPO to run on each PC and server at top level. Most orgs firewall accept Active Directory.
Here& #39;s the latest statement. They will be live streaming a briefing on the attack in 10 minutes from this tweet at the following link: http://webtv.hegnar.no/presentation.php?webcastId=97819442">https://webtv.hegnar.no/presentat...
I will live tweet anything interesting. Feel really bad for Hydro, the scenario is nightmare fuel. It is the CEO& #39;s 2nd day on the job.
Hydro are incredibly good at incident response and public relations, at least externally facing. They& #39;ve got an alternative website spun up in Azure, they& #39;re being transparent, doing live streams etc.
Hydro& #39;s recovery plan is to restore from backups. They believe they have good backup data still.
Gotta say Hydro& #39;s public facing response has been incredibly good - open, quick, transparent with customers (and public & employees), seniors on camera talking about issues. Wishing them a speedy recovery. I& #39;m in this BBC News piece: https://www.bbc.co.uk/news/technology-47624207">https://www.bbc.co.uk/news/tech...
At 5am this morning UTC somebody from Norway uploaded a signed copy of LockerGoga ransomware. It uses the same certificate me and @malwrhunterteam team identified several weeks ago, which the CA has now revoked.
Hydro moved all their email to Office365 cloud hosting a while back, which has enabled them to direct staff to mobile phones and tablets to keep communication going. Which is a pretty good cloud first endorsement, btw.
Norwegian media with NorCERT are reporting LockerGoga ransomware deployed by Active Directory, which backs up this thread theory.
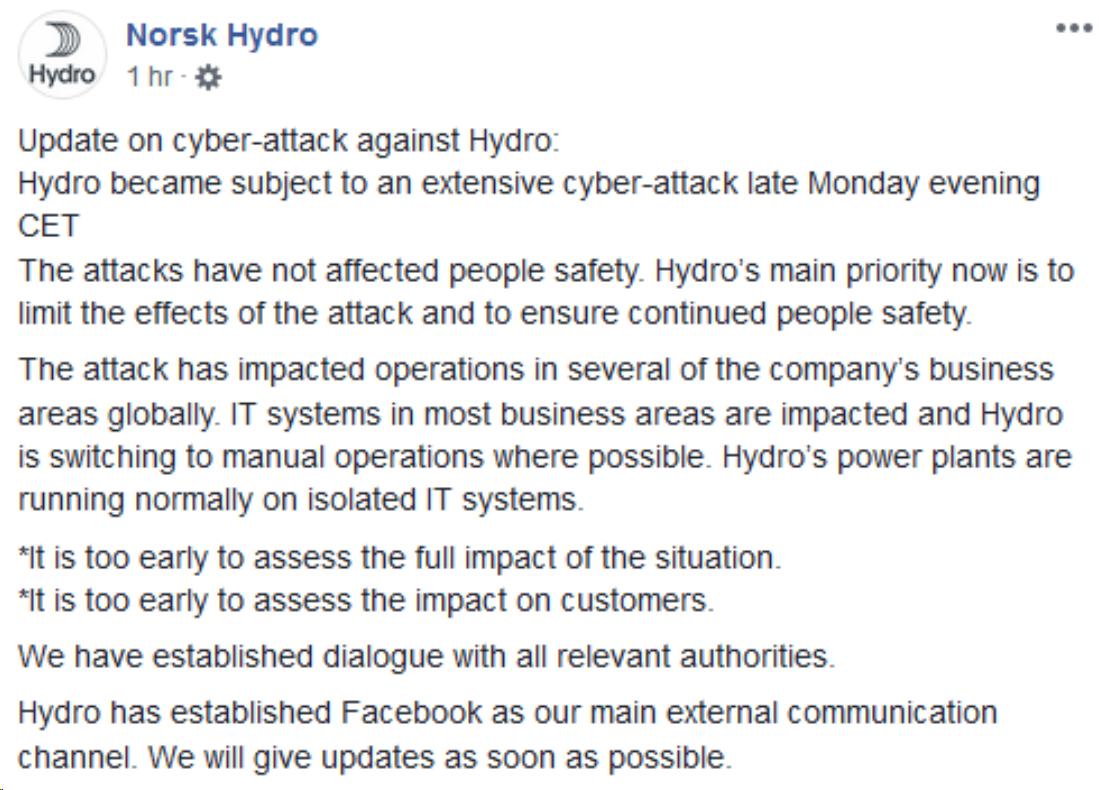
Here’s the latest update from Norsk Hydro. They’re basically running manufacturing production (where possible) from pre-printed order lists.
I should amalgamate my other tweets on this here:
- LockerGoga is only used in limited targeted attacks.
- It does not have a ‘spreader’, it’s not like WannaCry or NotPetya. It has to be deployed by an attacker who already has admin access.
- LockerGoga is only used in limited targeted attacks.
- It does not have a ‘spreader’, it’s not like WannaCry or NotPetya. It has to be deployed by an attacker who already has admin access.
- The ransom note is very similar to Ryuk, however the actual malware is different.
- The attackers at Altran and Hydro know what they are doing. It’s well organised extortion.
- The attackers at Altran and Hydro know what they are doing. It’s well organised extortion.
Note that despite being extremely open about the scale of the issues with public and media and putting execs in front of streams talking about an “extreme” situation, Norsk Hydro’s share price is fine. Compare that to where companies have hidden and minimised things.
Hydro have another webcast in 30 minutes from this tweet about their restoration efforts, at the following link http://webtv.hegnar.no/presentation.php?webcastId=97841296">https://webtv.hegnar.no/presentat...
It& #39;s a newer version of LockerGoga, having a quick look at lunch in ThreatGrid. Spawns lots of executables (one for each file?), very quick to encrypt, logs out console user when finished, you get ransom note on login. It encrypts DLL files which really breaks some applications.
Hydro& #39;s website is back online: https://www.hydro.com/en/media/news/2019/update-on-the-cyber-attack-on-hydro/">https://www.hydro.com/en/media/...
A very important point re LockerGoga - each payload .exe is unique. It is targeted per company with a uniquely generated payload. Just in reference to some of the sales traffic being generated by it.
Another fun one - Norsk Hydro& #39;s share price has actually gone up and continues to go up since this began. Having a global operational outage of manufacturing IT systems is actually a really big deal to a company (way more important than a data breach).
Behind the scenes they may well be having some pretty robust conversations about backups/restoration of systems etc (it& #39;s a big company, 40 locations), but they& #39;ve managed external comms like.. well, like a company arguably should.
Hydro have another update: https://www.hydro.com/en-GB/media/news/2019/update-on-cyber-attacks-march-21/
Key">https://www.hydro.com/en-GB/med... takeaways:
- They& #39;ve flown in staff from Microsoft and other unnamed firms to help with restoration.
- "Although progressing from day to day, it is still not clear how long it might take restore stable IT operations."
Key">https://www.hydro.com/en-GB/med... takeaways:
- They& #39;ve flown in staff from Microsoft and other unnamed firms to help with restoration.
- "Although progressing from day to day, it is still not clear how long it might take restore stable IT operations."
Further update from Hydro, it sounds like they are having great challenges getting things back online including having challenges around payroll and such https://www.hydro.com/en/media/news/2019/update-on-cyber-attack-march-22/">https://www.hydro.com/en/media/...
"Any encrypted PC or server will be rebuilt based on back-ups." Latest update from Hydro on their cyber security incident https://www.hydro.com/en/media/news/2019/update-on-cyber-attack-march-25/">https://www.hydro.com/en/media/...
Hydro& #39;s website says they are looking at around $40m USD in damages caused by cyberattack, says they have insurance through AIG, their Building Systems unit operations "remain almost at a standstill", in recovery phase for other areas of org https://www.hydro.com/en/media/news/2019/update-on-cyber-attack-march-26/">https://www.hydro.com/en/media/...
The ~$40m damages estimate is only for the last week, it doesn& #39;t include ongoing costs.
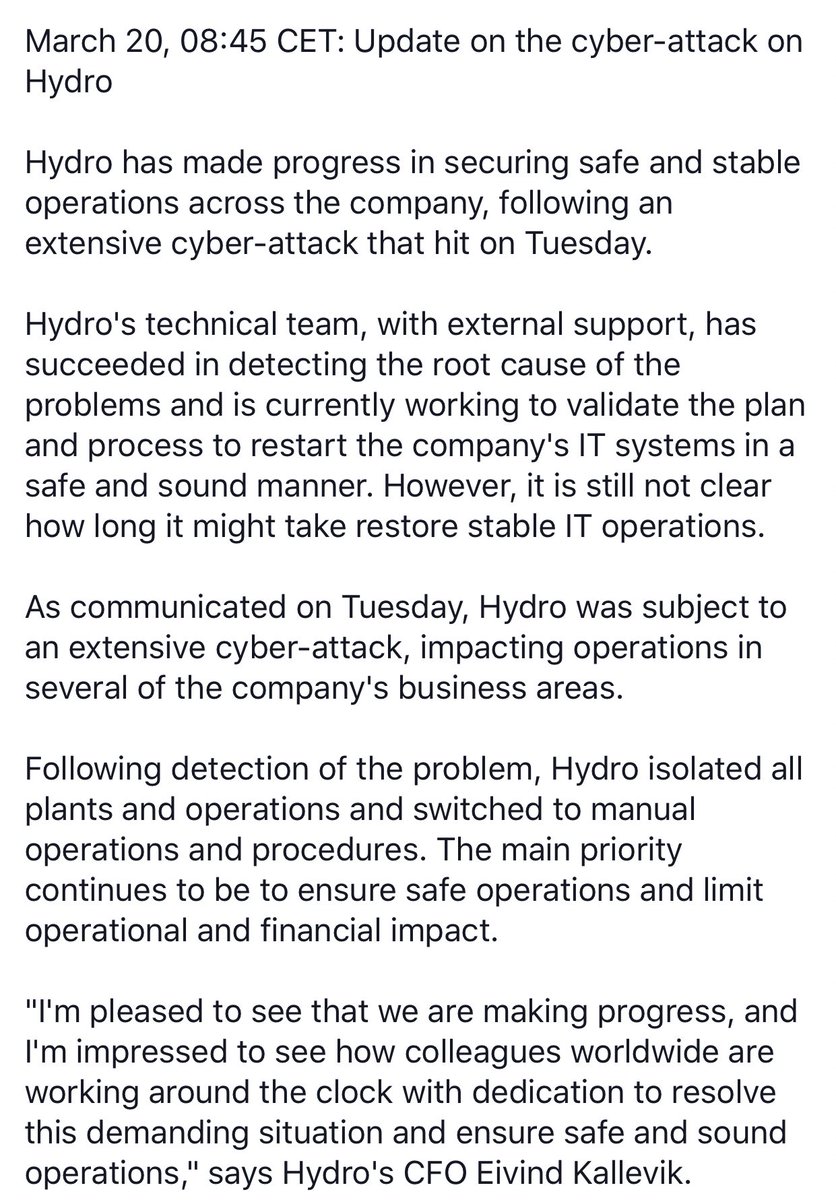
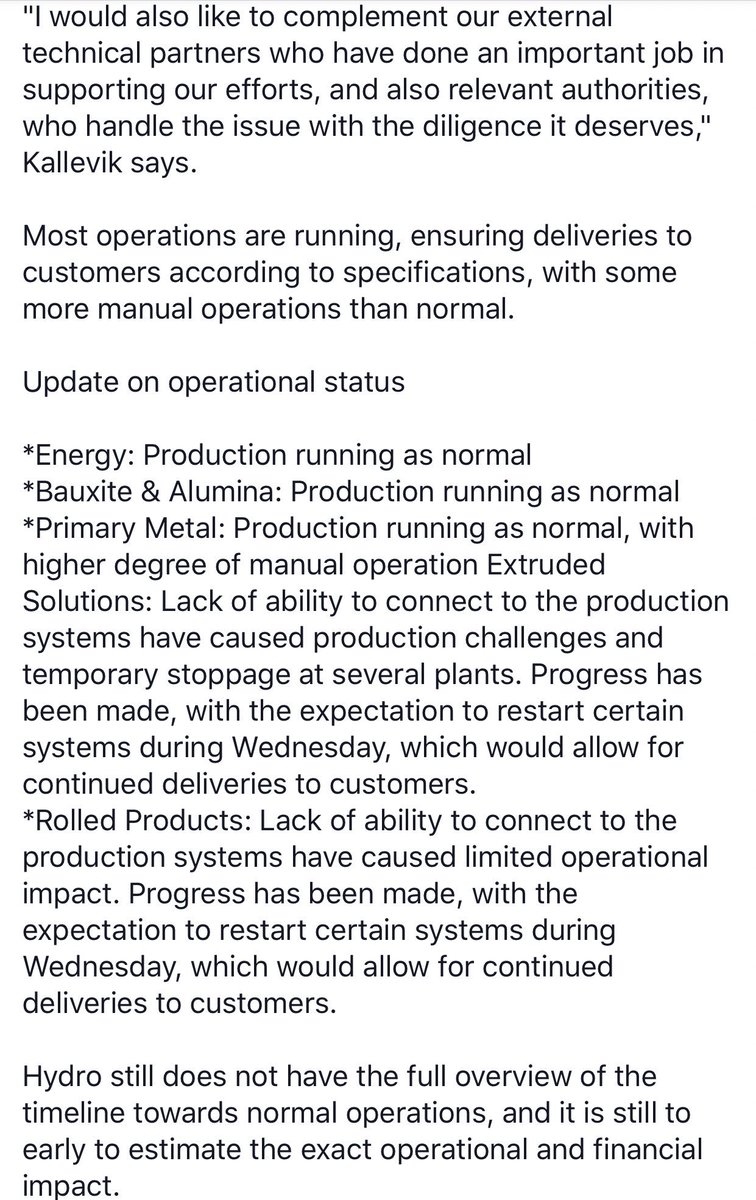
Hydro& #39;s biggest impacted business units are below, the primary production impact is their aluminium businesses (about 100 sites) - Extrusions they have down as 70-80% operational some with manual processes, Building Systems at "almost a standstill". 50/50 JV they acquired in 2017
Reuters have more on what is happening now here: https://uk.reuters.com/article/us-norway-cyber/norsk-hydros-initial-loss-from-cyber-attack-may-exceed-40-million-idUKKCN1R71X9">https://uk.reuters.com/article/u... - effectively they& #39;re estimating a ~$40m cost for last week, with full restoration taking "weeks or longer", and they have a cyber insurance claim cap. It& #39;s impacting share price, although not much so far.
Hydro say they have Building Systems production back online, currently operating at 20% volume. Unclear how long full operation will take to restore at those facilities.
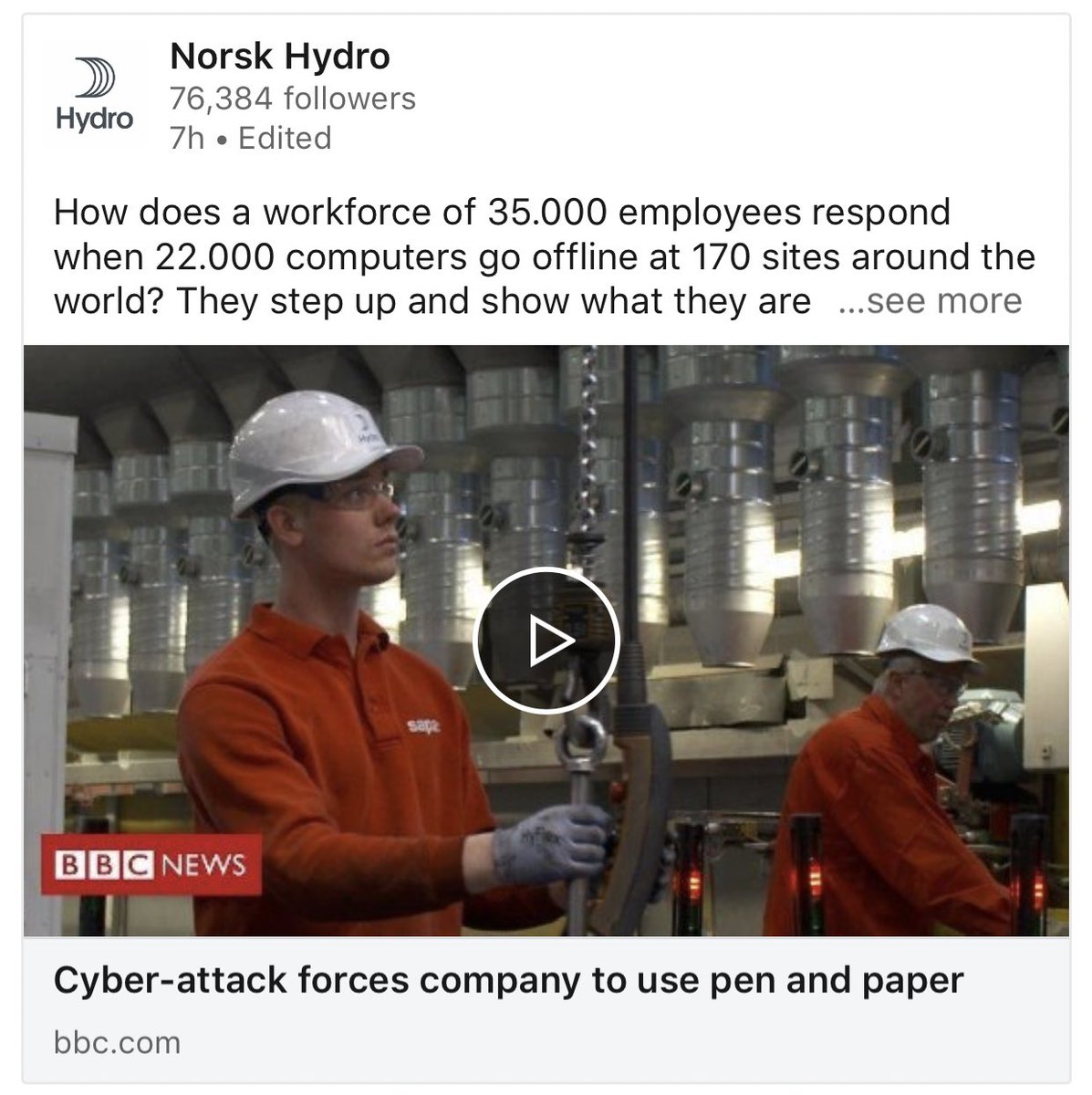
Hydro’s latest update is 4 of 5 business units are producing at normal speeds but using “manual workarounds”. Building Systems is 40-50% operational. They are working to restore “internal administrative processes, such as systems for payroll, treasury and reporting”. Some photos.
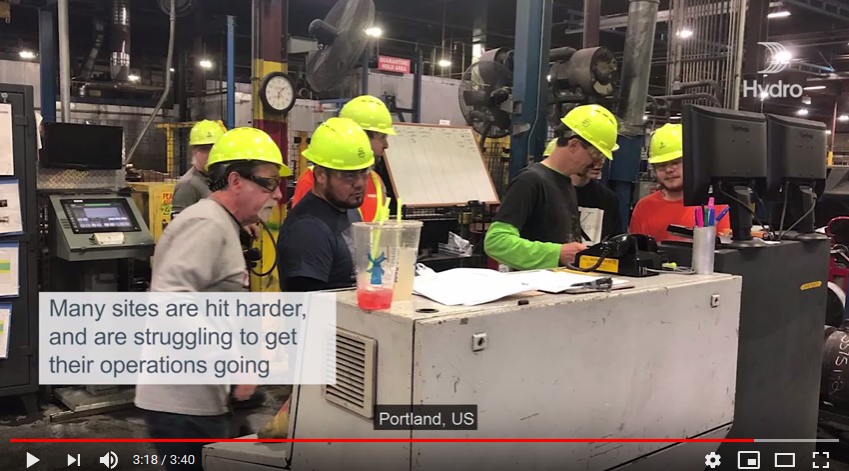
Okay so this is pretty incredible, @NorskHydroASA Hydro have released a 4 minute video on YouTube shot on the ground, talking to production managers etc about their cyber attack and what is happening https://www.youtube.com/watch?v=S-ZlVuM0we0&feature=youtu.be">https://www.youtube.com/watch... https://www.youtube.com/watch...
In the video you see plant managers operating from paper to keep production going, recreating documentation by hand etc.
Anyhow an incredible effort is ongoing to get Hydro back up and running by the staff, they have hundreds of manufacturing locations and lots of business units so a huge beast to wrangle. Their communication has been A++, they must be really glad they moved comms to O365 recently
17 days since Hydro cyber attack, checking in:
- delays to certain administrative processes incl reporting, billing and invoicing.
- Energy and Bauxite & Alumina running as normal.
- Primary Metal and Rolled Products some manual operation.
- Building Systems @ 75% production.
- delays to certain administrative processes incl reporting, billing and invoicing.
- Energy and Bauxite & Alumina running as normal.
- Primary Metal and Rolled Products some manual operation.
- Building Systems @ 75% production.
Hydro have delayed their Q1 reports to market due to cyber attack, sounds like they are having problems producing the reporting.
“35k employees, operations in 40 countries on all continents and several thousand servers in the company, full recovery is a complex and time-consuming process. We are well on our way, but it will take time before we are fully back to normal IT operations” https://www.hydro.com/en-GB/media/news/2019/update-on-cyber-attack-april-12/">https://www.hydro.com/en-GB/med...
https://www.hydro.com/Document/Index?name=General%20cyber-attack%20presentation%20April%2012.pdf&id=28255">https://www.hydro.com/Document/...
NRK have a feature inside Norsk Hydro’s cyberattack.
Key points:
- Confirms LockerGoga with Active Directory.
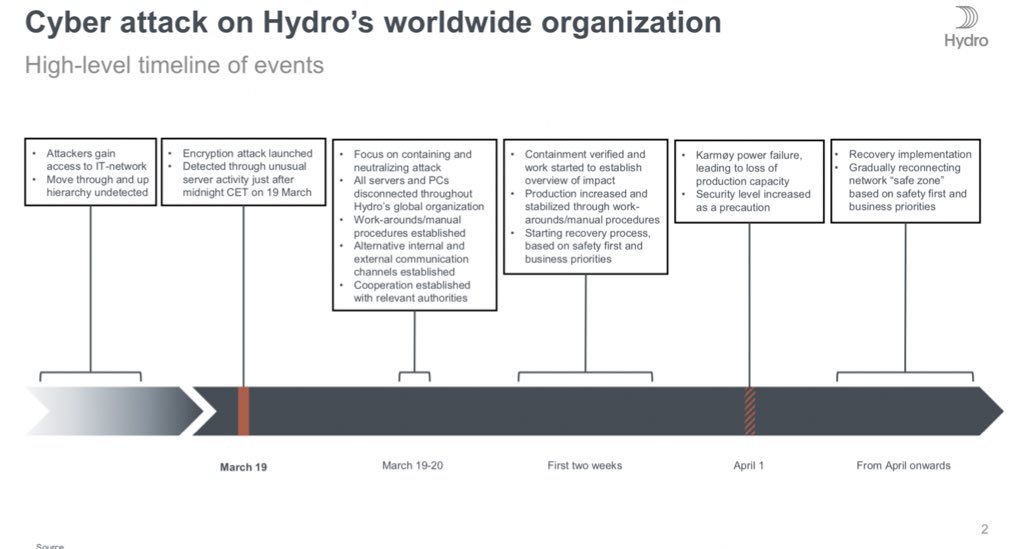
- They believe attackers had access around 2-3 weeks.
- Will take months to get back to normal.
- Microsoft doing IR.
https://www.nrk.no/norge/it-sjefen-i-hydro-om-dataangrepet_-_-man-tror-krisen-blir-stor_-sa-blir-den-enda-verre-1.14515043">https://www.nrk.no/norge/it-...
Key points:
- Confirms LockerGoga with Active Directory.
- They believe attackers had access around 2-3 weeks.
- Will take months to get back to normal.
- Microsoft doing IR.
https://www.nrk.no/norge/it-sjefen-i-hydro-om-dataangrepet_-_-man-tror-krisen-blir-stor_-sa-blir-den-enda-verre-1.14515043">https://www.nrk.no/norge/it-...
Another video update from the ground at Hydro. https://www.youtube.com/watch?v=o6eEN0mUakM">https://www.youtube.com/watch...
That video is well worth a watch if you’re in manufacturing IT btw. That factory had complete ICS failure due to ransomware, and had to find out how to operate manually by.. not having IT any more.
Examples of things Hydro staff are doing to keep production going. https://www.hydro.com/en-NO/about-hydro/stories-by-hydro/employees-find-creative-solutions-in-response-to-cyber-attack/">https://www.hydro.com/en-NO/abo...
Norsk Hydro have further delayed their Q1 results to June 5th due to cyberattack, may be delayed further https://www.hydro.com/Document/Index?name=Hydro%20Q1-2019%20Update&id=42133">https://www.hydro.com/Document/... - “The revised date is conditional upon the planned timeline for restoring operational and reporting systems”
Norsk Hydro have issued their Q1 results, raising financial hit from ~$40m to ~$69m for ransomware incident by spreading cost over two quarters (so far). They expect insurance to cover. https://www.hydro.com/Document/Index?name=Report%20Q1%202019.pdf&id=71833">https://www.hydro.com/Document/...
Really good 5 minute video report from BBC News on the ground at Norsk Hydro, showing for the first time the ransomware message - and how other companies are in secret paying ransomware https://www.bbc.co.uk/news/av/technology-48707033/ransomware-cyber-attacks-are-targeting-large-companies-and-demanding-huge-payments">https://www.bbc.co.uk/news/av/t...
Norsk Hydro have recorded another ~£27m loss in Q2 2019 financial results due to ongoing ransomware incident, this figure is in addition to prior reported numbers. https://www.hydro.com/en/media/news/2019/second-quarter-2019-results-down-on-lower-realized-prices/">https://www.hydro.com/en/media/...
Norsk Hydro says their ransomware incident costs up to about £55m, only about £2m has been recovered from cyber insurance so far https://www.cyberscoop.com/cyber-insurance-norsk-hydro-lockergoga-attack/">https://www.cyberscoop.com/cyber-ins...
Almost 9 months post attack, Norsk Hydro reveal they called in Microsoft to aid response. There’s a TON of information in this, I think cybersecurity history will look back at Norsk as a bellwether for good crisis management. https://news.microsoft.com/transform/hackers-hit-norsk-hydro-ransomware-company-responded-transparency/">https://news.microsoft.com/transform...

 Read on Twitter
Read on Twitter